Russian Threat Group CryptoBytes is Still Active in the Wild with UxCryptor

The SonicWall Capture Labs threat research team has recently been analyzing malware from the CryptoBytes hacker group. UxCryptor is a ransomware strain associated with the CryptoBytes group, a financially motivated Russian cybercriminal organization. It has been active since at least 2023. The group is known for leveraging leaked ransomware builders to create and distribute their malware.
UxCryptor is part of a broader trend of ransomware families that use leaked builders, making it accessible to less technically skilled malware operators. It is often delivered alongside other malware types, such as Remote Access Trojans (RATs) or information stealers, to maximize the impact of an attack. The malware is designed to encrypt files on the victim's system, demanding payment in cryptocurrency for decryption.
UxCryptor has seen consistent activity since its emergence, with its usage peaking in 2024. Although the sample analyzed here appears to be an early version, it is still active in the wild.
Infection Cycle
Upon execution of the malware, the following three screens are displayed in quick succession:
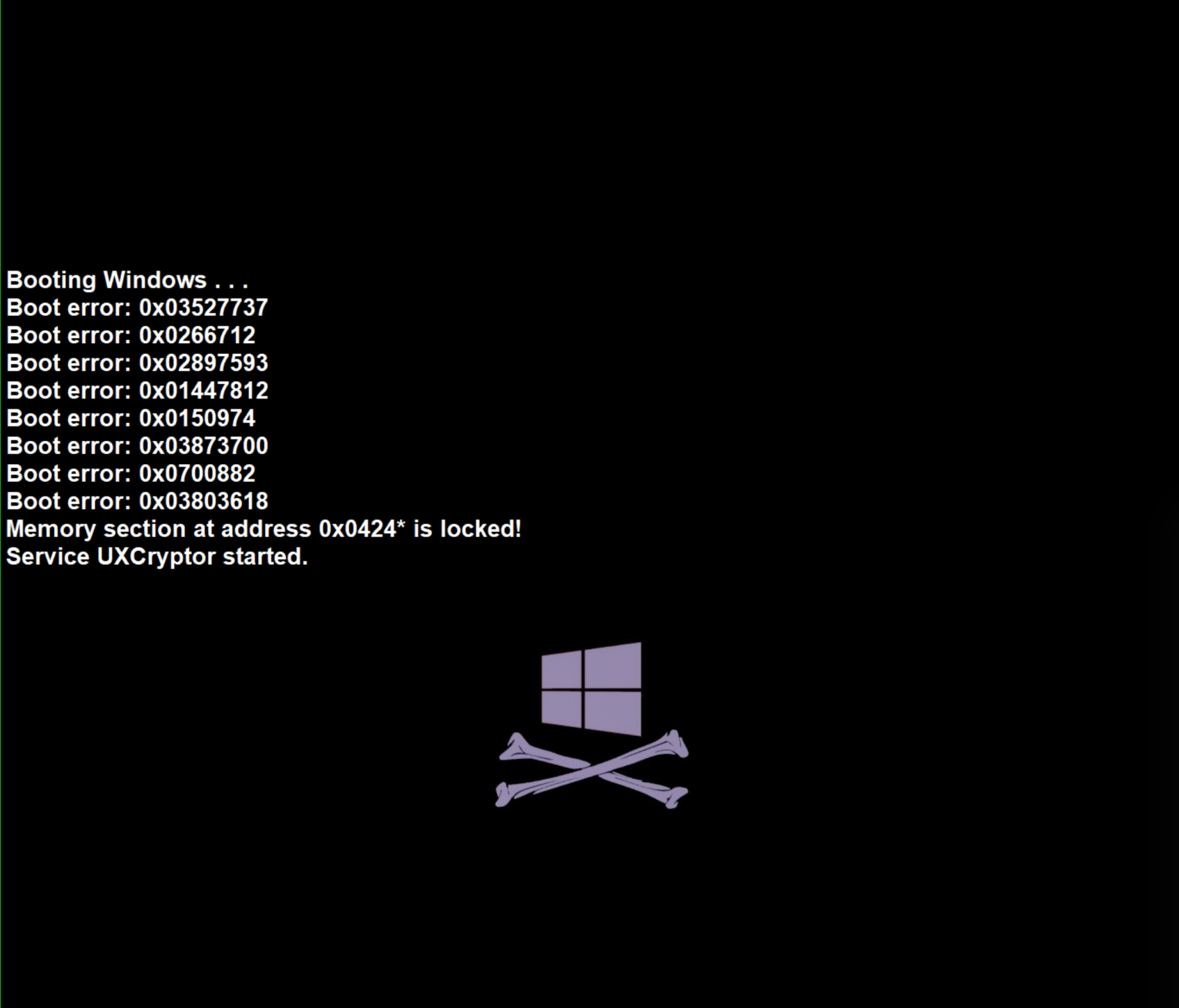
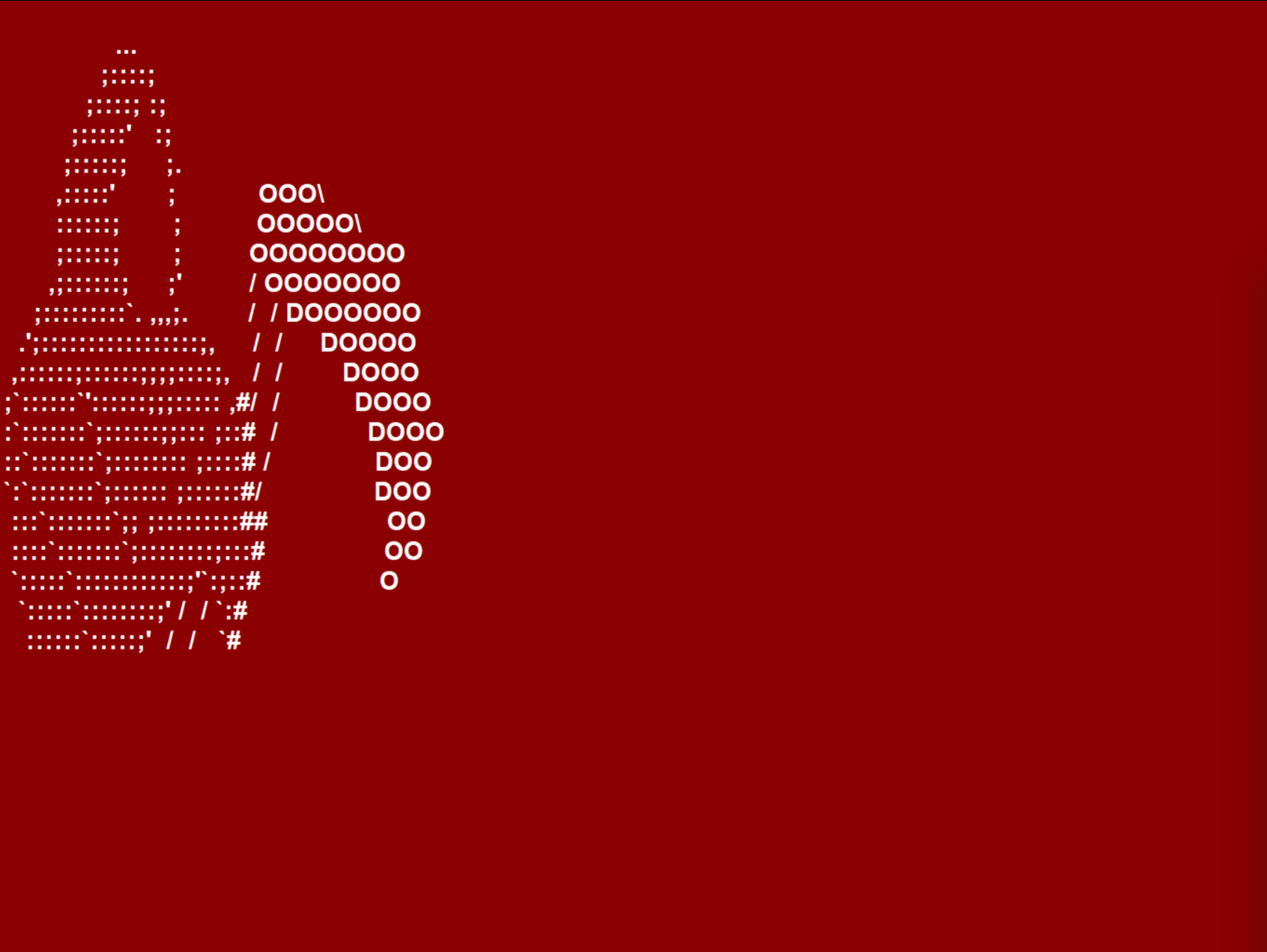
A ransom note in Russian is displayed:
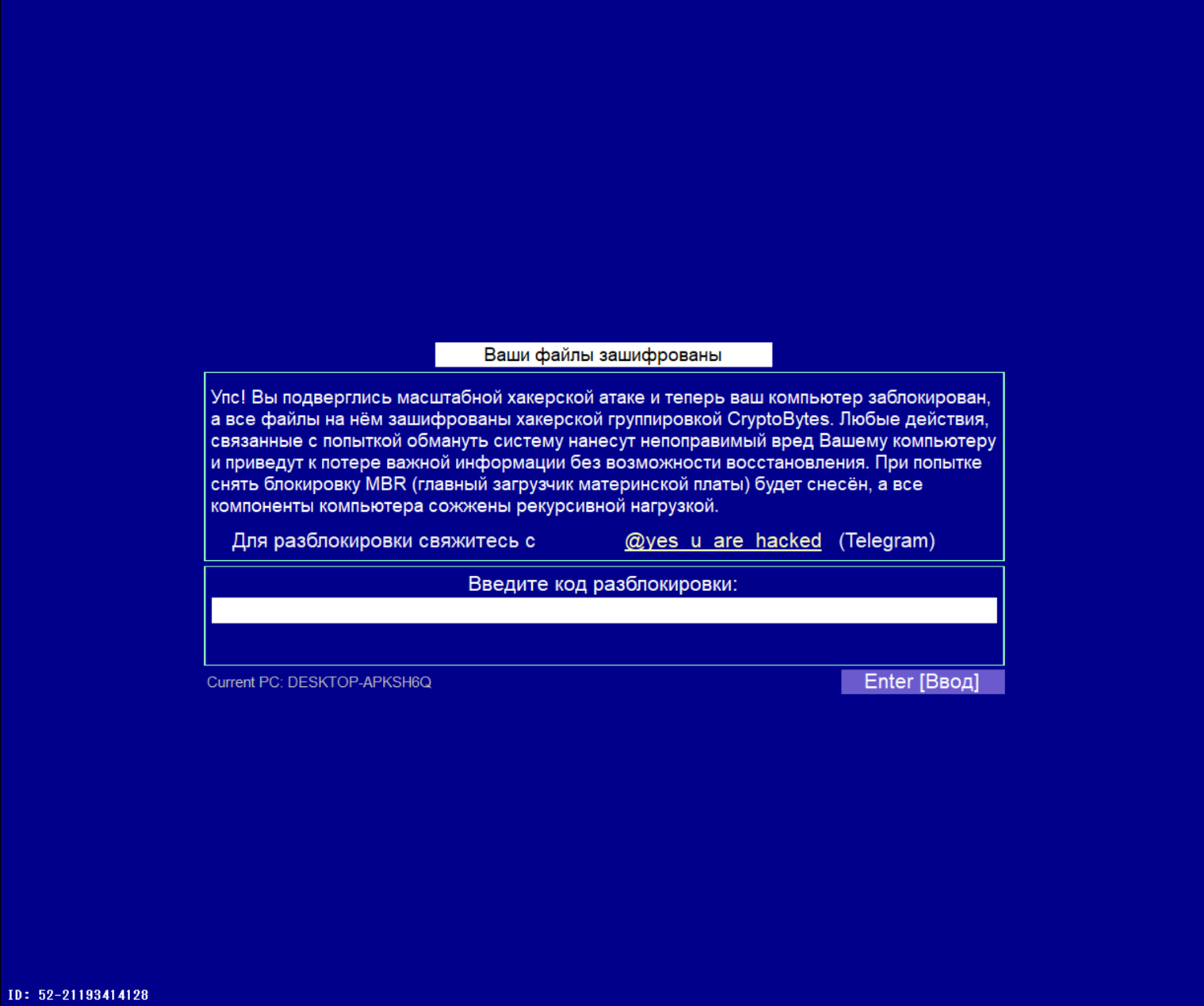
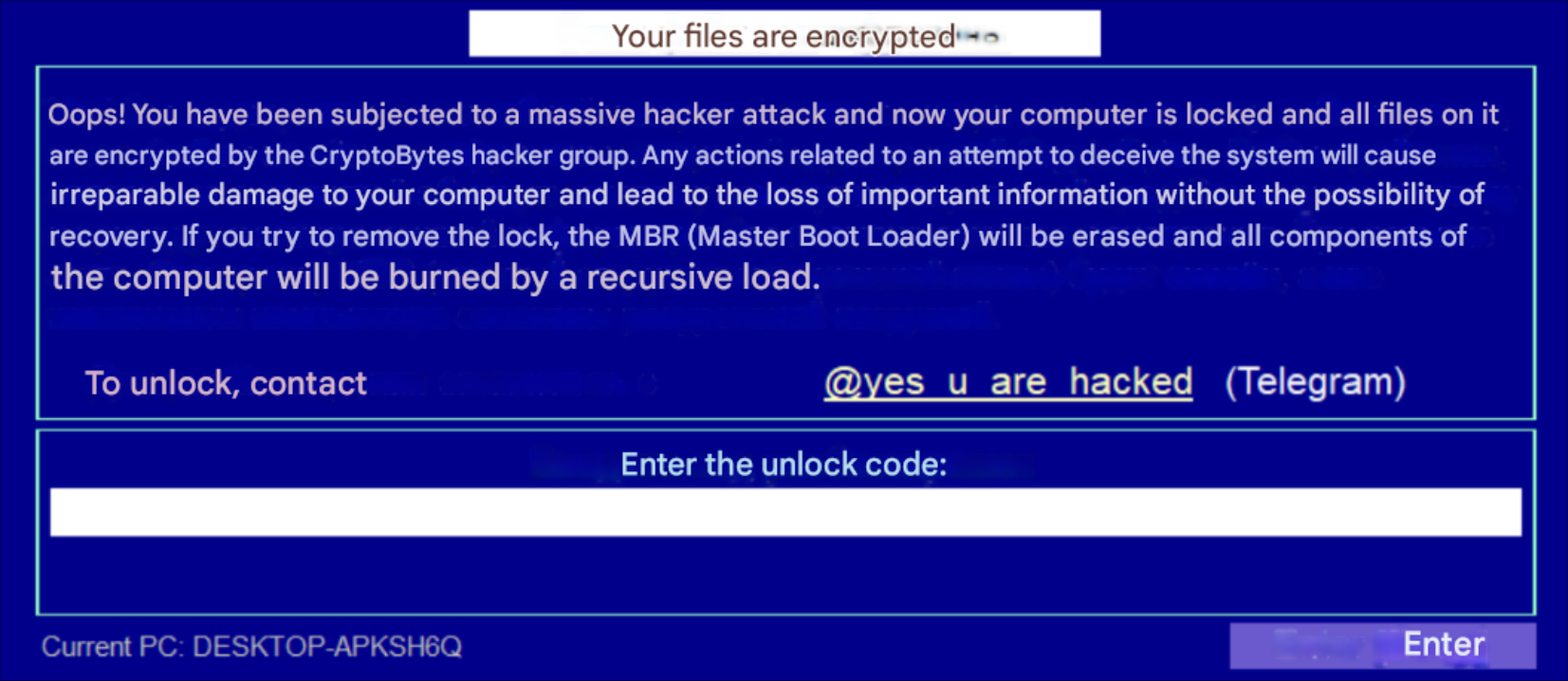
An additional ransom note is written to %USERPROFILE%\AppData\Local\Temp\$unlocker_id.ux-cryptobytes. It contains the following message:

The malware is written in .NET. Decompiling the code reveals a variety of anti-analysis methods.
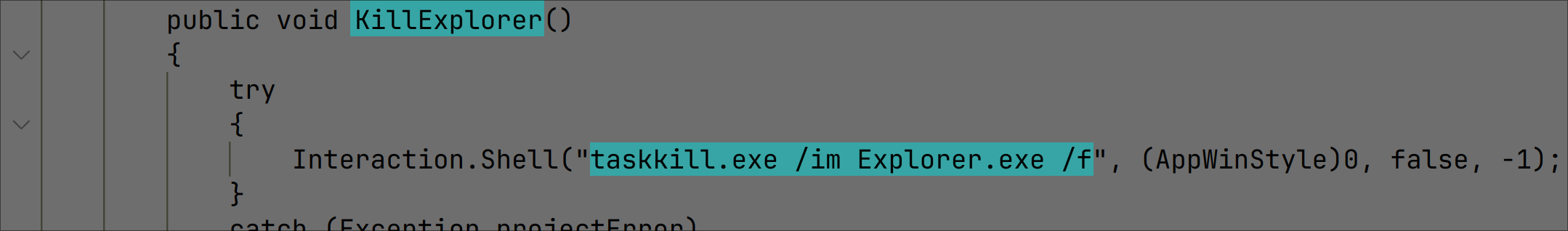
It first attempts to kill explorer.exe:
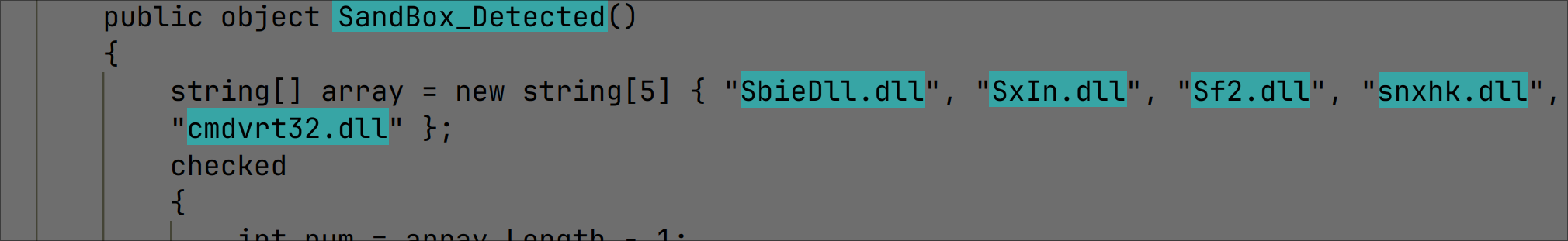
It checks to see if it is running in Sandboxes such as Sandboxie, Avast and Qihoo360:
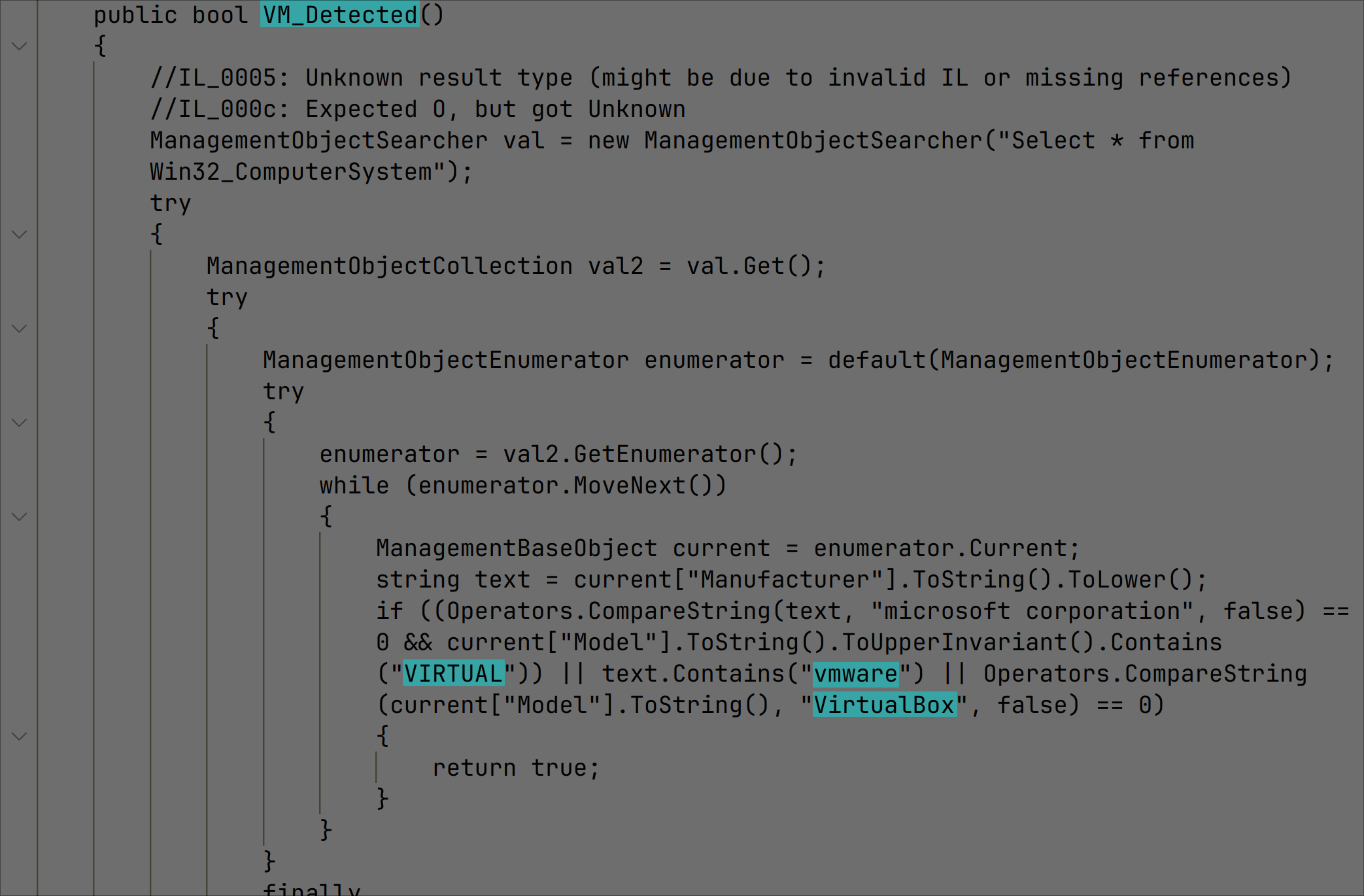
The code contains VMWare and VirtualBox VM detection:
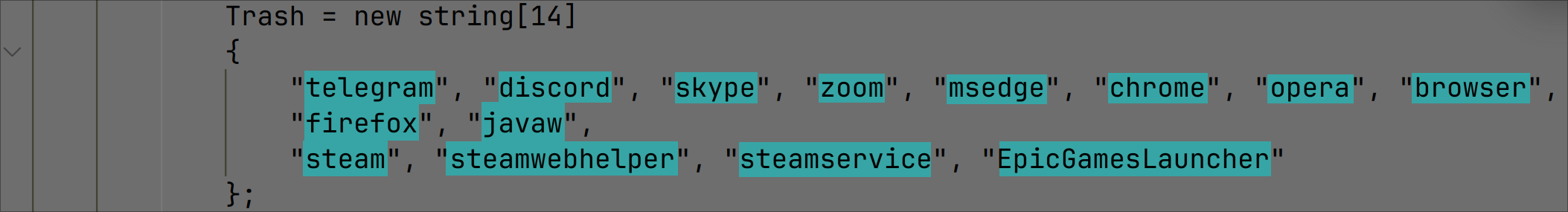
Various programs such as Discord, Skype, Zoom and any browsers are killed if they are found to be running:
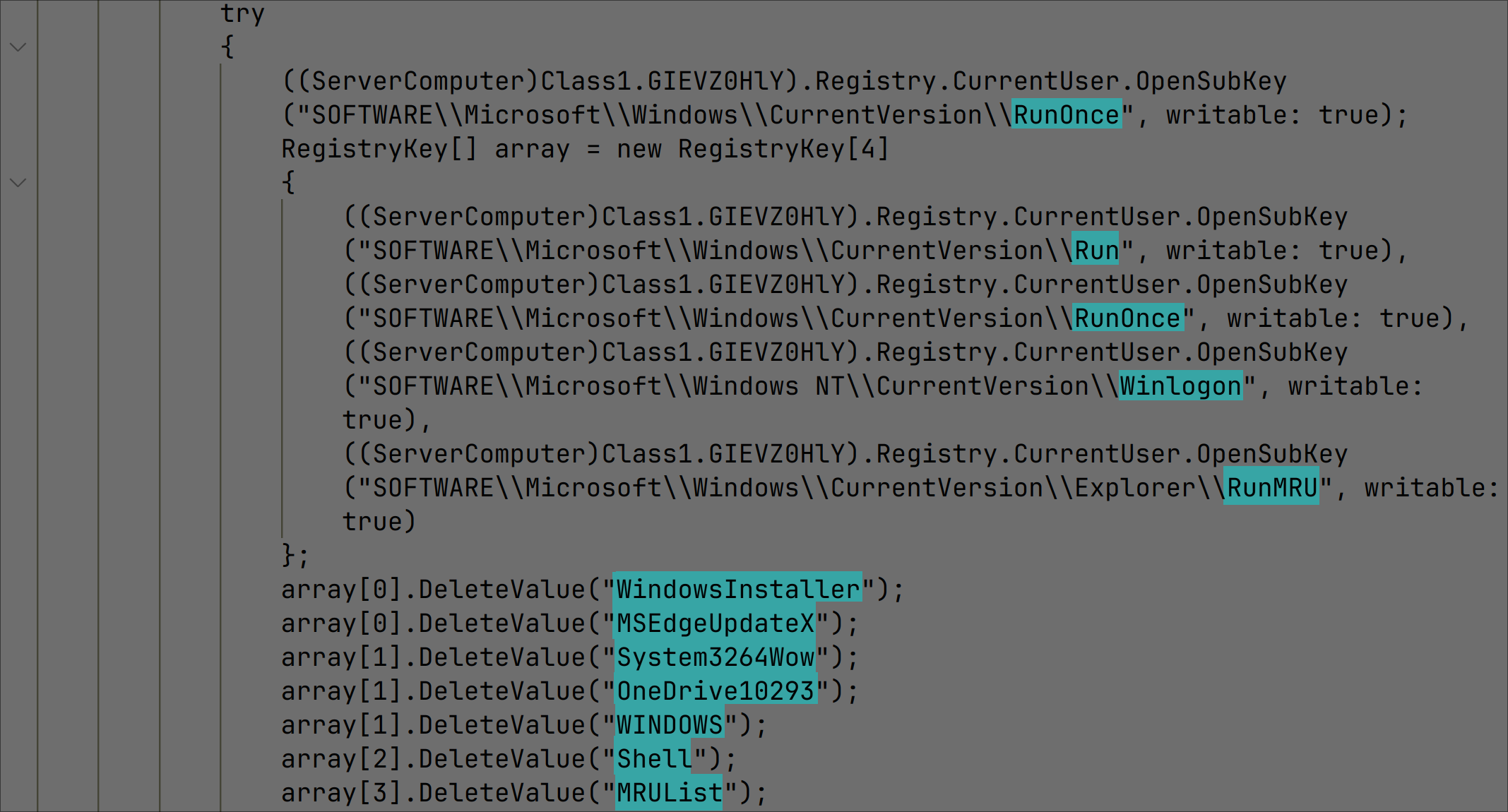
Various Windows system applications are prevented from starting up after login by deleting their corresponding registry keys:
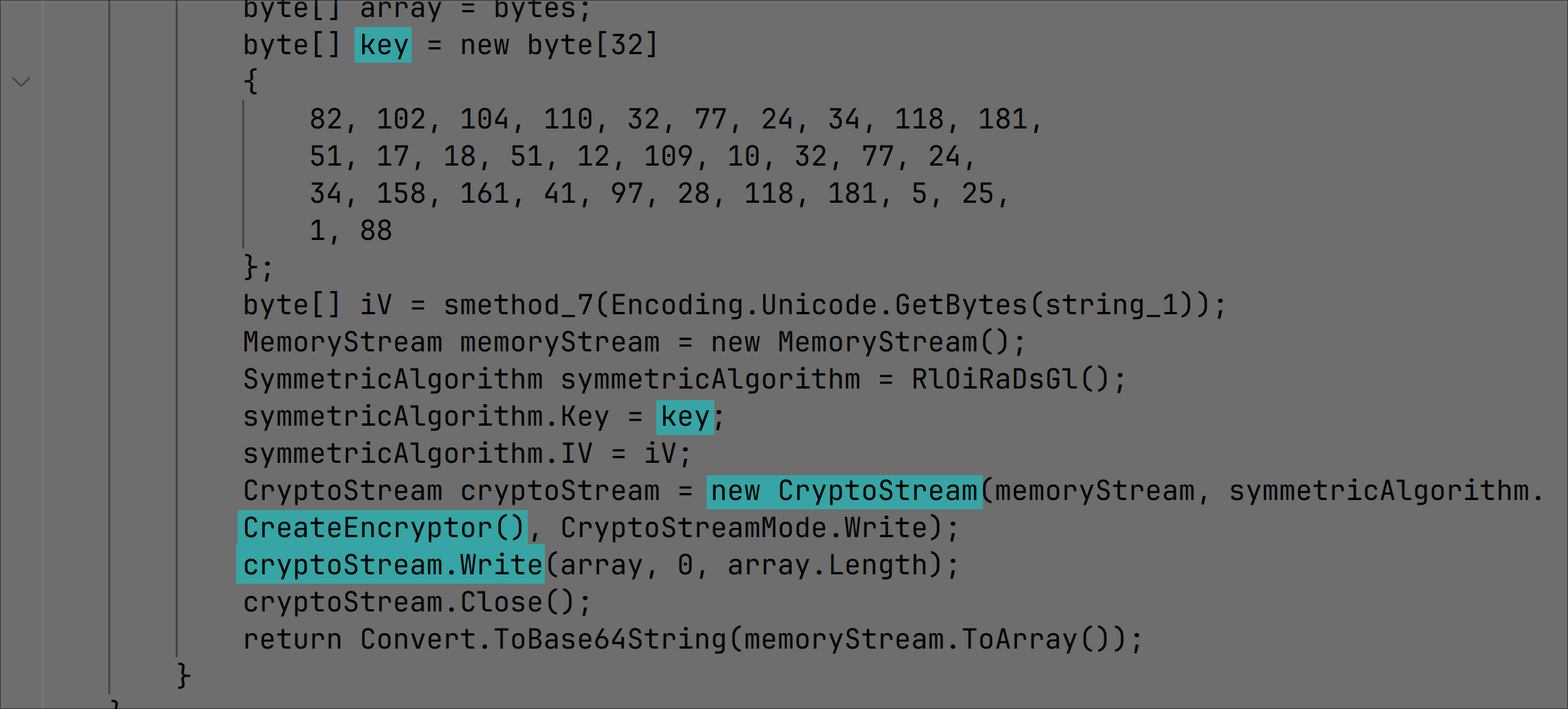
In this early version of the software, no files were actually encrypted during our analysis. However, the functionality is present:
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: UXCryptor.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News
