GCleaner is Packed and Ready to Go

Overview
This week, the SonicWall Capture Labs threat research team investigated a sample of GCleaner, a Themida-packed malware variant that downloads and drops additional malware, has C2, heavy anti-analysis/anti-VM, and evasion capabilities. GCleaner will also attempt to infect removable drives by encryption or to spread to other systems.
Infection Cycle
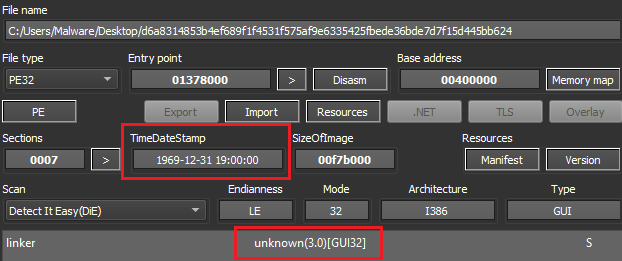
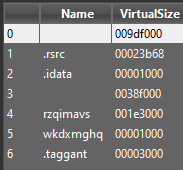
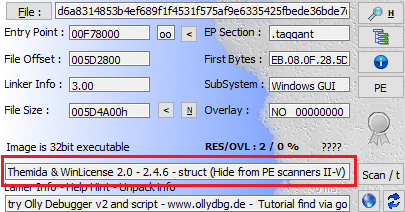
The main executable has a variety of markers to illustrate it is not a typical file. Depending on the file detector used, it will show up as either ‘unknown’ or ‘Themida-Packed’. The timestamp marks the creation date as 12-31-1969, and the file sections are misnamed or missing.
Through dynamic analysis, the main executable runs and performs checks for the following programs and processes, while sending network requests every three seconds:
Programs
- OllyDbg
- Process Monitor
- File Monitor
- Registry Monitor
Debugging
- DebugPort
- IsDebuggerPresent
- IsProcessorFeaturePresent
- Rdtsc (for time measurements)
- OutputDebugStringA
- HideFromDebugger
- GetProcessHeap
- GetLastError
Checks are also performed to ensure the malware isn’t running on a virtual machine by querying the following registry keys:
- HKEY_CURRENT_USER\Software\Wine
- HKEY_LOCAL_MACHINE\HARDWARE\ACPI\DSDT\VBOX__
- HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System name: SystemBiosVersion
- HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System name: VideoBiosVersion
- HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\TenantRestrictions\Payload
This API call for GetLastError is used against multiple threads that are created and the checks require the appropriate error codes from each thread; attempting to bypass results in the program immediately closing. Once checks complete, multiple files are dropped onto the system with one being run immediately:
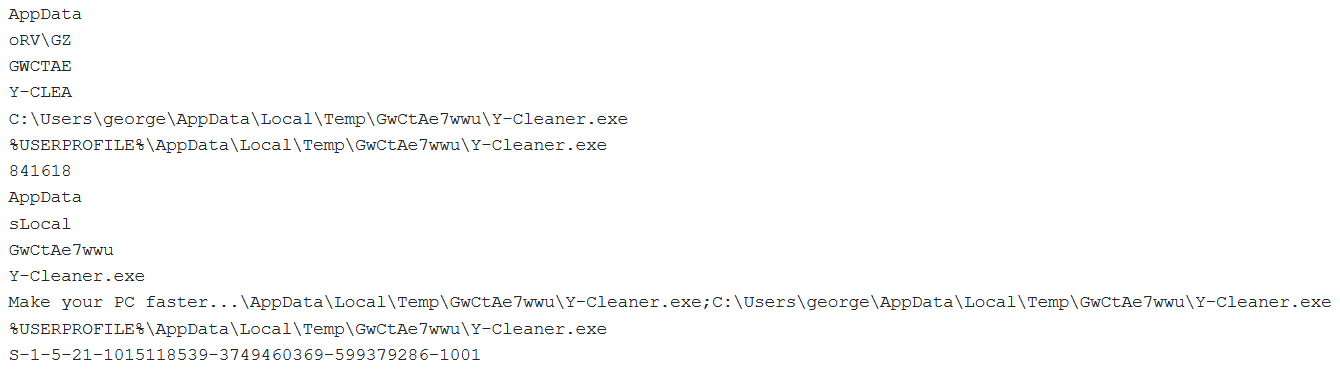
- BitLockerToGo.exe (run)
- Y-Cleaner.exe (dropped as soft[1])
- Cleaner.lnk
- key(1).txt (also drops as key[1].htm)
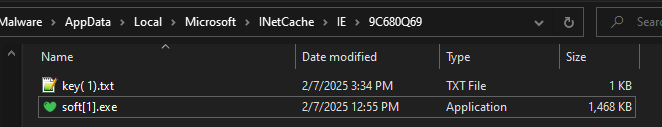
Cleaner.lnk is created using IShellLink to act as a shell script to run Y-Cleaner.
- key(1).txt or key[1].htm contents:
- 9tKiK3bsYm4fMuK47Pk3s
A TCP connection is made to ‘185.56.73.23/add?substr=mixfour&s=three&sub=emp’ to establish C2 comms and download another file named ‘fuckingdllENCR[1].dll; this IP is located in Russia. This file is completely encoded and did not run during testing; it also has no detection signature and appears to require additional code or a decryption operation before becoming usable.

SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this malware, the following signatures have been released:
- GCleaner.Downloader
- GCleaner.YCleaner
IOCs
- D6a8314853b4ef689f1f4531f575af9e6335425fbede36bde7d7f15d445bb624
- 7533c0c4547741bc6533cf4ac7e590e97be5039555938c993534a5ded4323374
- 614a0362ab87cee48d0935b5bb957d539be1d94c6fdeb3fe42fac4fbe182c10c
- 15ee76cd7ecf55a261b421d506b9174002fc731d94af09c144f63c5d97743637
- d6cc7713c7c8fad193556372d8473be748e9c24381ebff50b10072de20239911
- e29a4fd2cb1f367a743ea7cfd356dbd19aeb271523bbae49d4f53257c3b0a78d
Share This Article

An Article By
An Article By
Security News
Security News
