Critical Wazuh RCE Vulnerability (CVE-2025-24016): Risks, Exploits and Remediation

Overview
SonicWall Capture Labs threat research team has become aware of a critical remote code execution (RCE) vulnerability in Wazuh Server (CVE-2025-24016) and has implemented mitigating measures. Wazuh is an open-source security platform used for threat detection, incident response, and compliance monitoring. This vulnerability affects Wazuh versions 4.4.0 through 4.9.0 and is caused by an unsafe deserialization flaw in the DistributedAPI component. Attackers with API access can inject malicious JSON payloads to execute arbitrary Python code remotely. This flaw has been assigned a CVSS score of 9.9 and is patched in Wazuh version 4.9.1. Organizations running affected versions should update immediately to mitigate exploitation risks. A Proof-of-Concept (PoC) exploit has been publicly disclosed, increasing the risk of active exploitation in the wild.
Technical Overview
The vulnerability resides in how Wazuh handles DistributedAPI parameters, which are serialized as JSON and later deserialized using the function ‘as_wazuh_object’ in ‘framework/wazuh/core/cluster/common.py’, which can be seen in Figure 1. An attacker can manipulate the API by injecting a dictionary into a DAPI request or response, allowing them to forge an unhandled exception (__unhandled_exc__) that evaluates arbitrary Python code. Since ‘as_wazuh_object’ blindly accepts input without sanitization, malicious JSON payloads that result in remote code execution can be crafted. The issue was fixed using PR #25705, as seen in Figure 1.
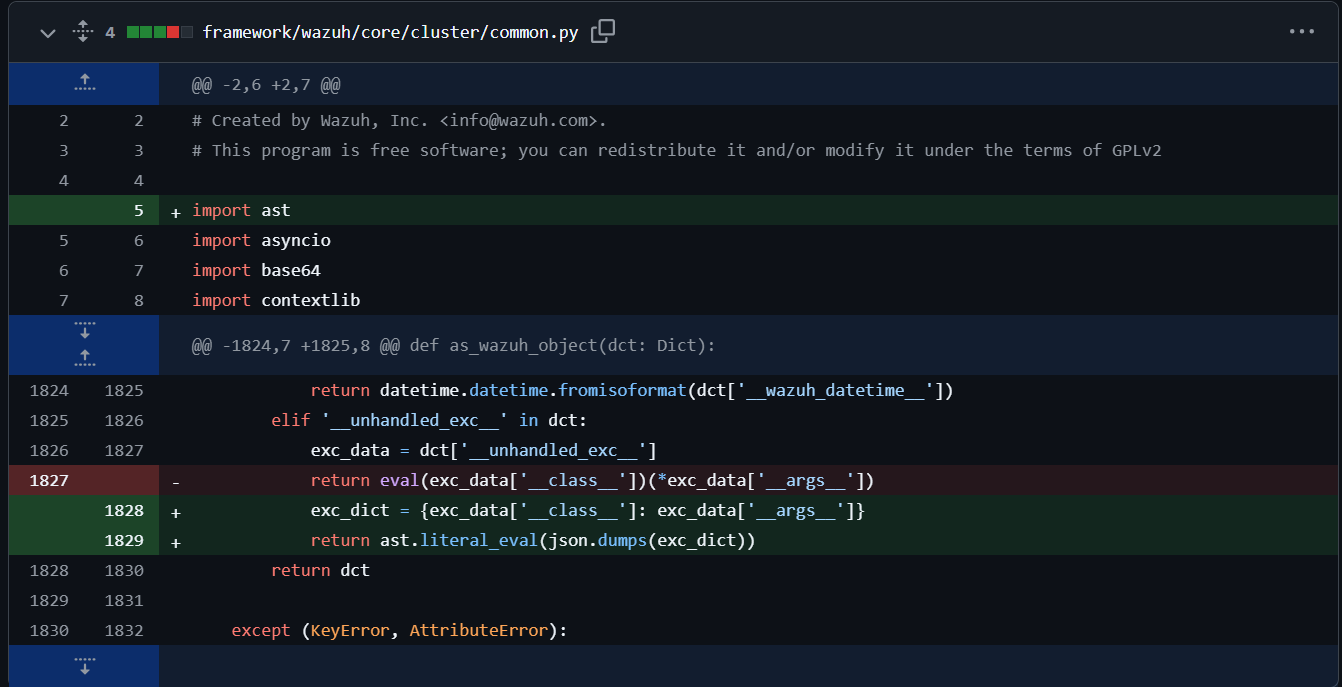
Triggering the Vulnerability
An attacker with API access can trigger this flaw by sending a specially crafted JSON payload to a Wazuh worker server. If the request is relayed to the master server, it may result in arbitrary code execution. Additionally, an attacker can leverage a compromised Wazuh agent to exploit the vulnerability in specific configurations. A compromised agent can manipulate a getconfig request by injecting a malicious JSON object containing a serialized unhandled exception. If a getconfig request is initiated through a server API call to /agents/{agent_id}/config/{component}/{configuration}, and the targeted agent is managed by a different server than the one making the request, the unsafe deserialization process will occur on the receiving server, potentially leading to the execution of malicious code.
Exploitation
An attacker would need to take the following steps to exploit this vulnerability:
Obtain API Credentials - The attacker must first acquire the username and password of a valid Wazuh API user. Without these credentials, exploitation is not possible.
Craft a Malicious Payload - The attacker prepares a JSON payload that includes a dictionary that contains an “__unhandled_exc__” primitive and Python code to be executed.
Send the Malicious Request - The crafted payload is sent using API credentials through a run_as request or another API endpoint that accepts user-controlled data.
Trigger Remote Code Execution - If the request is directed at a Wazuh worker server, it may be forwarded to the master server, resulting in arbitrary code execution.
SonicWall Protections
To ensure SonicWall customers are protected against CVE-2025-24016, the following security signatures have been released:
IPS: 20732 - Wazuh Insecure Deserialization
Remediation Recommendations
Upgrading to Wazuh 4.9.1 or later is the best way to address this issue since it includes the patch that addresses the vulnerability. In addition, limiting API access to only essential and trusted clients can help minimize risks. Keeping an eye on logs for any unusual getconfig requests or suspicious API activity can also help catch potential threats early. An open-source script has been made available to help test if an instance of Wazuh is vulnerable to this attack.
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News
