Configuring Active Directory/LDAP over TLS (Certificate)
Description
This article explains how to integrate SonicWall appliance with an LDAP directory service, such as Windows Active Directory, using SSL/TLS.
- Install a server certificate on the LDAP server.
- Install a Certificate Authority (CA) certificate for the issuing CA on your SonicWall appliance.
- Configure the SonicWall appliance for LDAP over SSL/TLS
A prerequisite is configuring the Domain Controller (DC) server for certificate management so that it can establish SSL/TLS sessions with the SonicWall appliance. To achieve this, one has to install the certificate, e.g, mycert.pfx on the DC. Such a file has both the private key and public key certificate. While one can purchase a certificate from a public Certificate Authority (CA), self-signed certificates can be created on a CA in Active Directory Certificate Services or OpenSSL and used for this purpose.
Next, you should configure the SonicWall appliance for LDAP over SSL/TLS. Additionally, you may consider exporting the public key certificate from the DC and import it to the SonicWall Appliance.
Resolution
 NOTE: In this article we have used Windows 2003 server for Certificate Authority and Active Directory. If you are using windows server other than 2003 please check Microsoft site for configuring CA and Active directory, however the steps on the SonicOS Enhanced remains the same.
NOTE: In this article we have used Windows 2003 server for Certificate Authority and Active Directory. If you are using windows server other than 2003 please check Microsoft site for configuring CA and Active directory, however the steps on the SonicOS Enhanced remains the same.
The following procedures describe how to Configure LDAP over TLS.
Configuring the CA on the Active Directory (Windows 2003 Server)
To configure the CA on the Active Directory server (skip the first five steps if Certificate Services are already installed)
- Navigate to Start | Settings | Control Panel | Add/Remove Programs.
- Select Add/Remove Windows components.
- Select Certificate Services.
- Select Enterprise Root CA when prompted.
- Enter the requested information. For information about certificates on Windows systems, see http://support.microsoft.com/kb/931125.
Exporting the CA Certificate from the Active Directory Server
To export the CA certificate from the AD server
- Launch the Certification Authority application: Start | Run | certsrv.msc.
- Right click on the CA you created and select Properties.
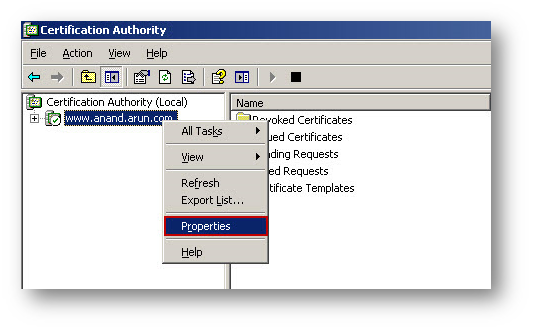
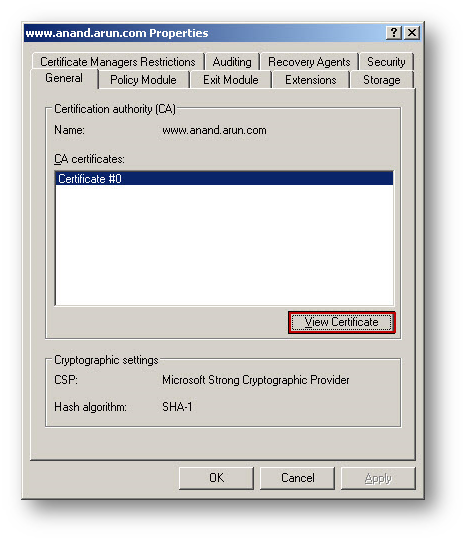
- On the General tab, click View Certificate .
- On the Details tab, select Copy to File.
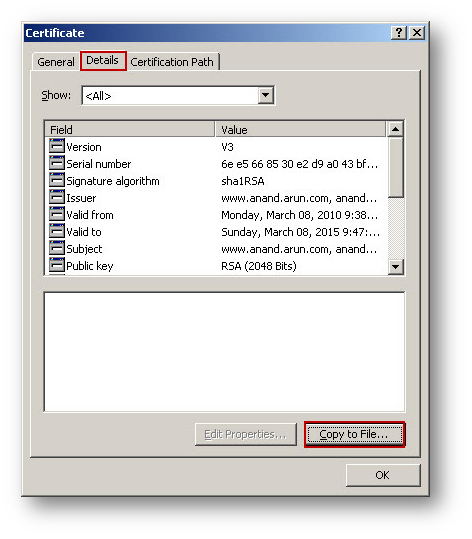
- Follow through the wizard, and select the DER Encoded binary X.509 (.cer) format.
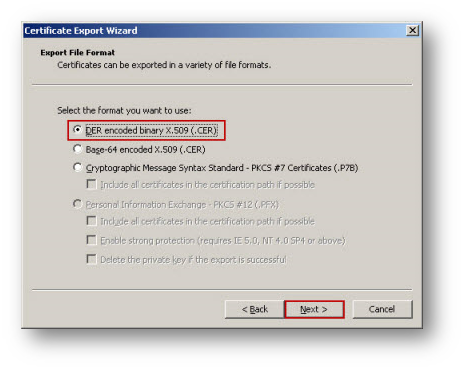
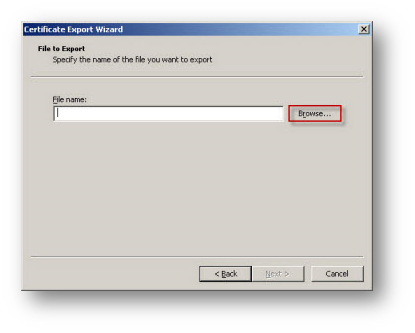
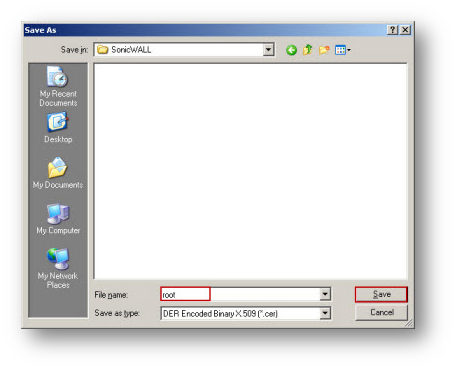
- Click browse and Specify a path and filename to which to save the certificate.
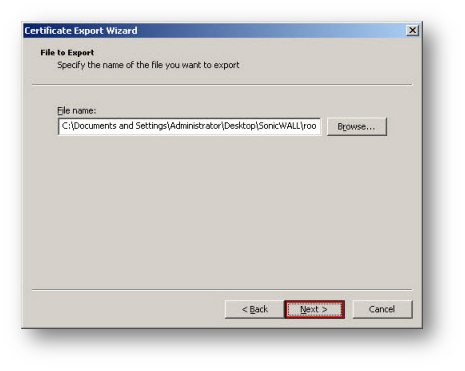
- Click Next button and click Finish.
Importing the CA Certificate onto the SonicWall
To import the CA certificate onto the SonicWall:
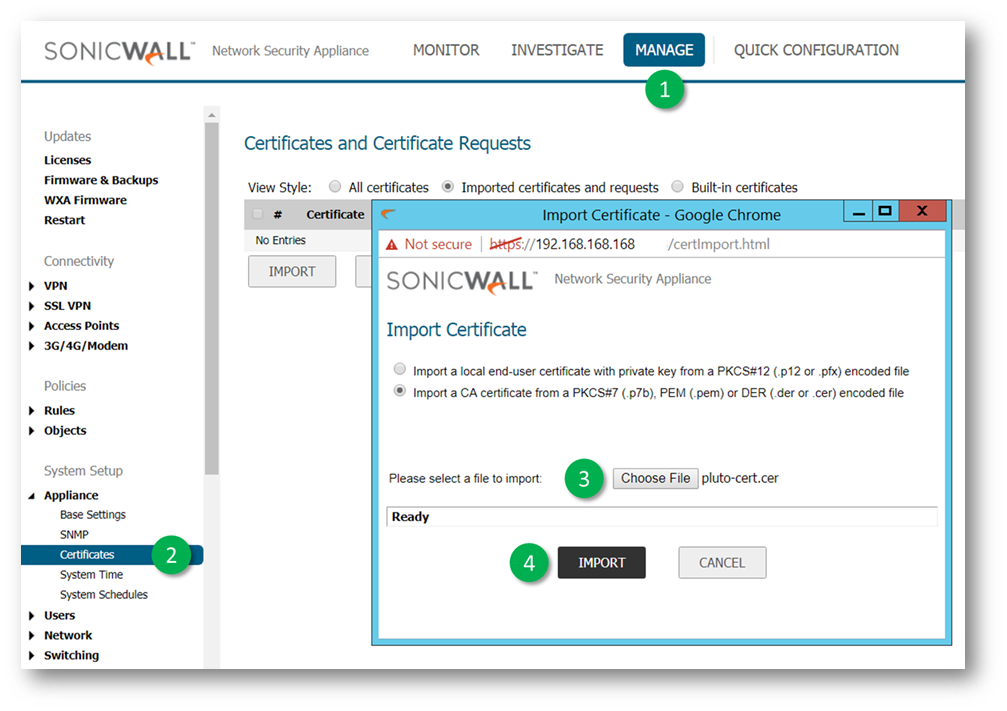
- Navigate to Manage | System Setup | Appliance | Certificates.
- Select Import a CA certificate from a PKCS#7 (.p7b), PEM (.pem) or DER (.der or .cer) encoded file.
- Choose the certificate File,
 EXAMPLE: pluto-cert.cer below.
EXAMPLE: pluto-cert.cer below. - Click Import.
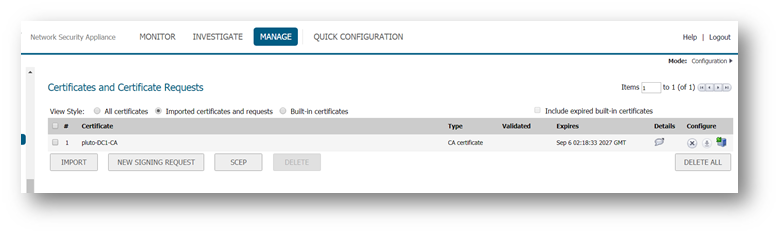
- Once the CA root certificate is imported, it will be listed under Manage | System Setup | Appliance | Certificates | Imported Certificates.
Configuring LDAP settings on SonicWall Appliance
- Navigate to Manage | System Setup | Users | Settings . In the User authentication method from the drop-down list, select LDAP + Local Users and click Configure LDAP.
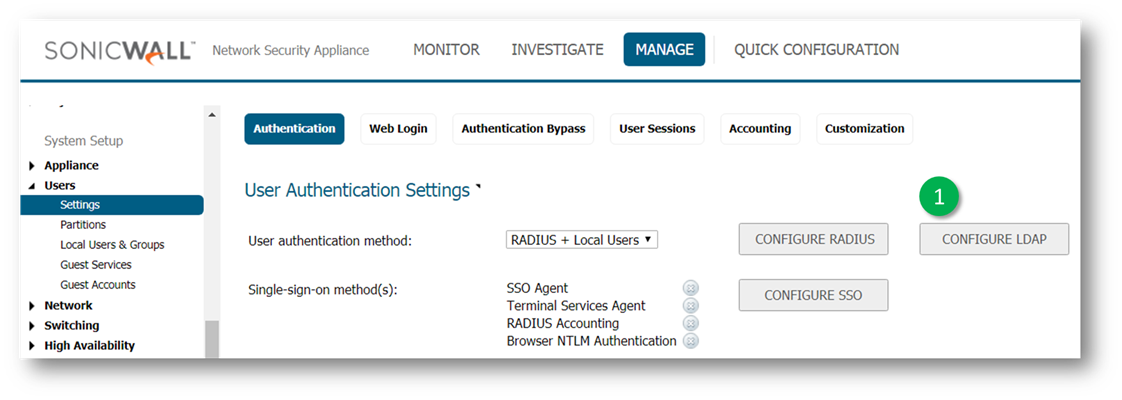
- On the LDAP Configuration window that opened, click ADD to set up a new LDAP server.
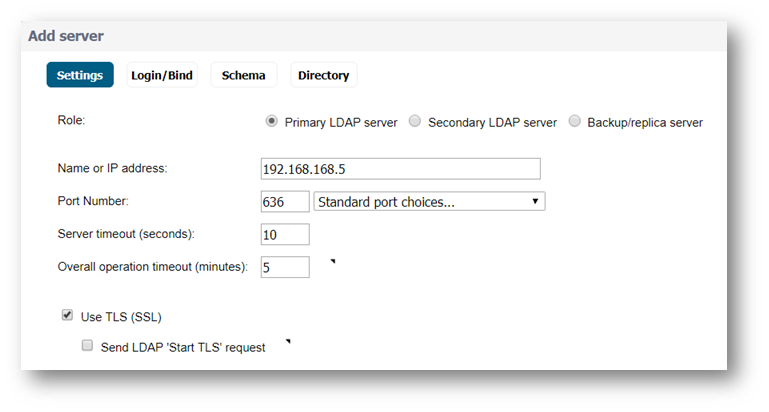
- Name or IP address: The FQDN or IP address of the LDAP server against which you wish to authenticate. When using an FQDN name, be certain that it can be resolved by your DNS server.(Recommended to use the name of the server).
- Port Number: The default LDAP over TLS port number is TCP 636.
- Server timeout (seconds): The amount of time, in seconds, that the SonicWall will wait for a response from the LDAP server before timing out. Allowable ranges are 1 to 99999, with a default of 10 seconds.
- Overall operation timeout (minutes): 5(Default).
- Use TL(SSL) : Use Transport Layer Security (SSL) to log in to the LDAP server. It is strongly recommended that TLS be used to protect the username and password information that will be sent across the network (as shown in the diagram below). Most modern implementations of LDAP server, including Active Directory, support TLS. Deselecting this default setting will display an alert that you must accept to proceed.
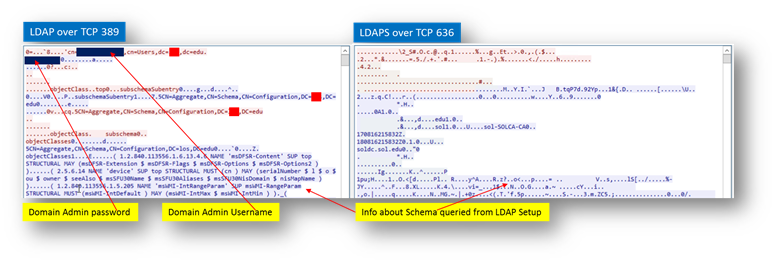
- Send LDAP Start TLS Request Some LDAP server implementations support the Start TLS directive rather than using native LDAP over TLS. This allows the LDAP server to listen on one port (normally 389) for LDAP connections, and to switch to TLS as directed by the client. Active Directory does not use this option, and it should only be selected if required by your LDAP server. Require valid certificate from server Validates the certificate presented by the server during the TLS exchange, matching the name specified above to the name on the certificate. Deselecting this default option will present an alert, but exchanges between the SonicWall and the LDAP server will still use TLS only without issuance validation.
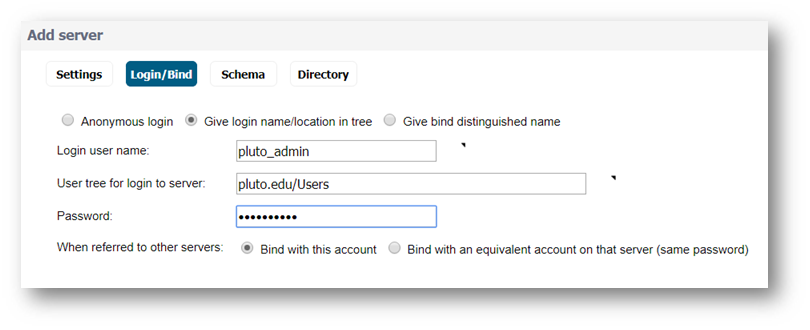
- Anonymous Login: Some LDAP servers allow for the tree to be accessed anonymously. If your server supports this (Active Directory generally does not), then you may select this option.
- Give login name/location in tree: Specify a user name that has rights to log in to the LDAP directory, any account with LDAP read privileges. The login name will automatically be presented to the LDAP server in full dn notation. Administrative privileges are not required.
 NOTE: That this is the user's display name, not their login ID.
NOTE: That this is the user's display name, not their login ID. - Give bind distinguished name: one can get the full user DN.
 EXAMPLE: CN=pluto_admin admin,CN=Users,DC=pluto,DC=edu.
EXAMPLE: CN=pluto_admin admin,CN=Users,DC=pluto,DC=edu. - Password The password for the user account specified above.
- Select Bind with this account.
On the Schema tab
- Select the LDAP schema
 EXAMPLE: Microsoft Active Directory. Additionally, one might consider updating the schema by clicking READ FROM SERVER followed by Automatically update the server's schema configuration .
EXAMPLE: Microsoft Active Directory. Additionally, one might consider updating the schema by clicking READ FROM SERVER followed by Automatically update the server's schema configuration .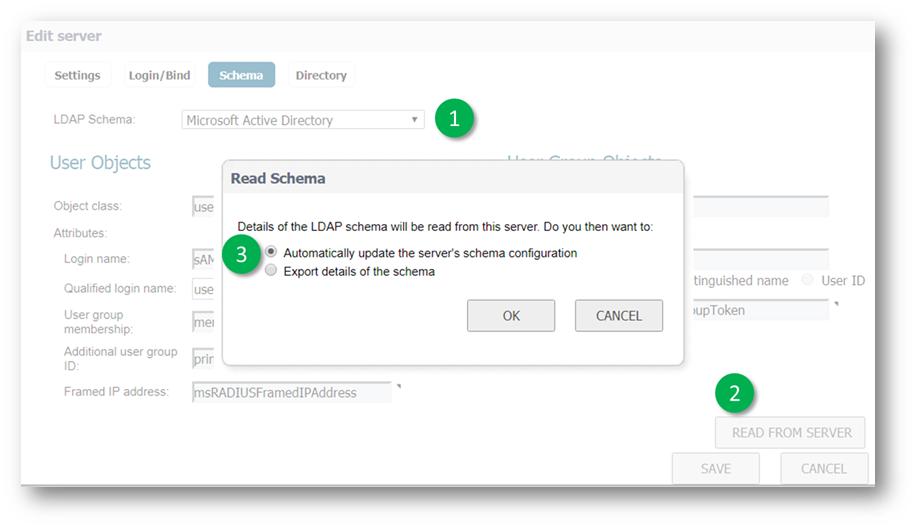
On the Directory tab
- Primary domain: The domain used by your LDAP implementation.
- Trees containing users: click AUTO-CONFIGURE followed by Replace Existing trees and START (in the pop-up windows). This will update the user treetree for login to server.
 NOTE: If you want your previous tree to be appended please choose so in the last option.
NOTE: If you want your previous tree to be appended please choose so in the last option.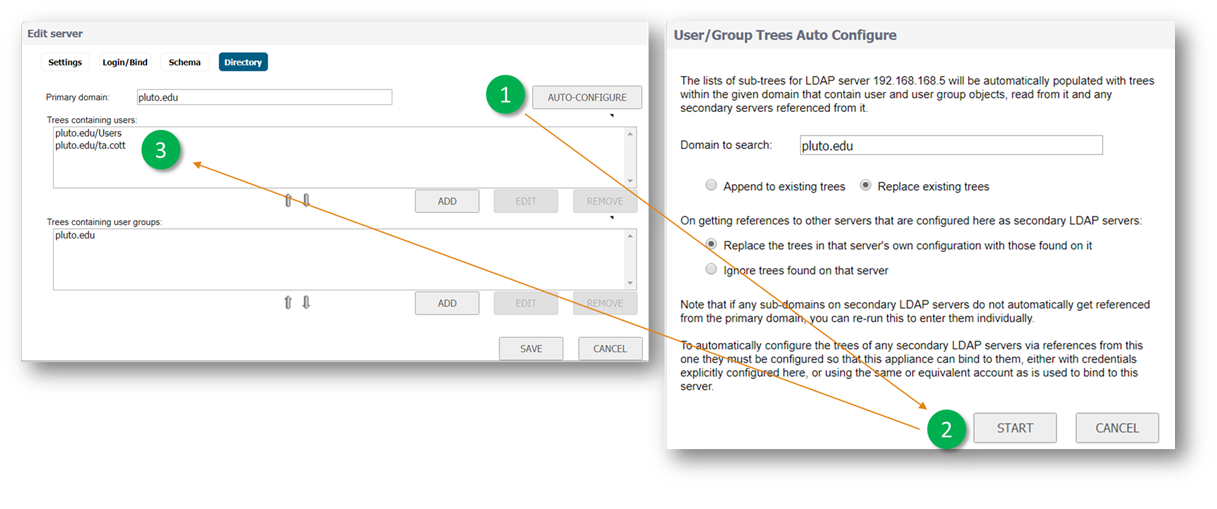
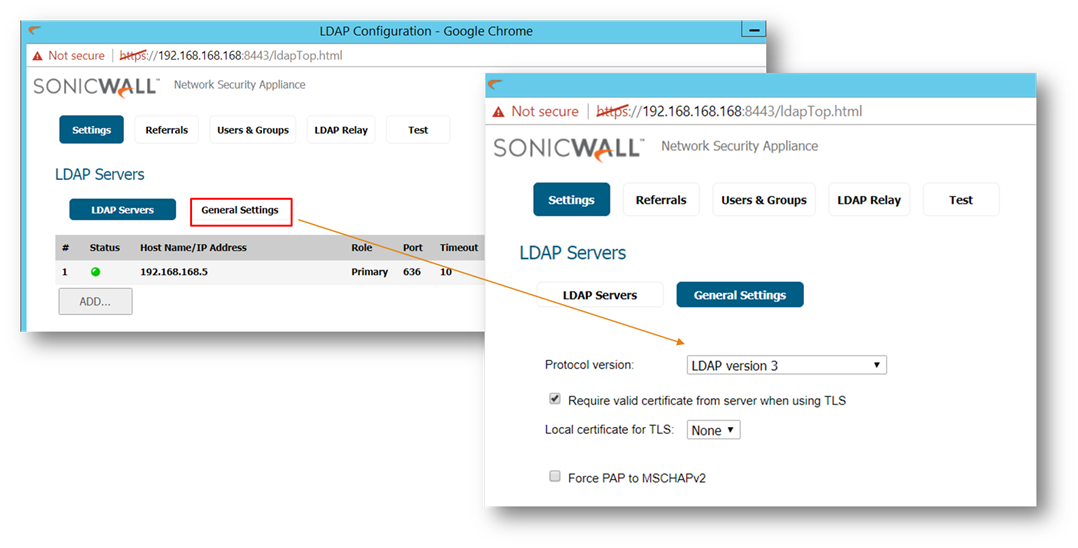
In the Genera Settings tab of LDAP Configuration window: select
- Protocol version: LDAP version 3.
- Select Require valid certificate from the server when using TLS.
- Local certificate for TLS : Optional, to be used only if the LDAP server requires a client certificate for connections. Useful for LDAP server implementations that return passwords to ensure the identity of the LDAP client (Active Directory does not return passwords). This setting is not required for Active Directory. Leave this option to None.
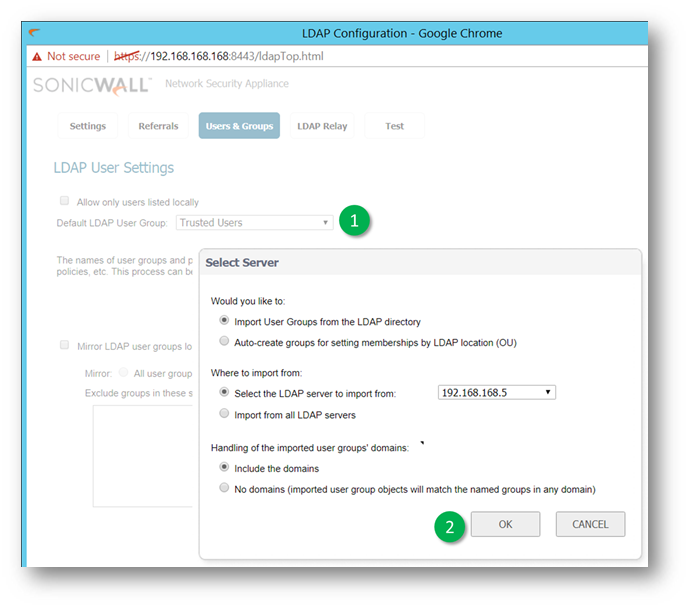
On the Users & Groups tab
- Default LDAP User Group : Trusted Group
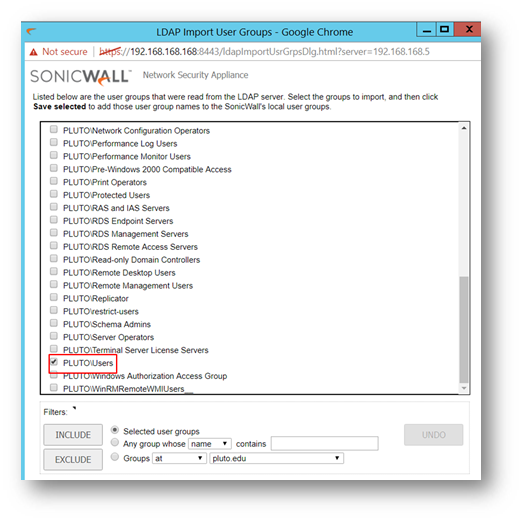
- Click OK which will open an window where you an choose which groups import.
Test
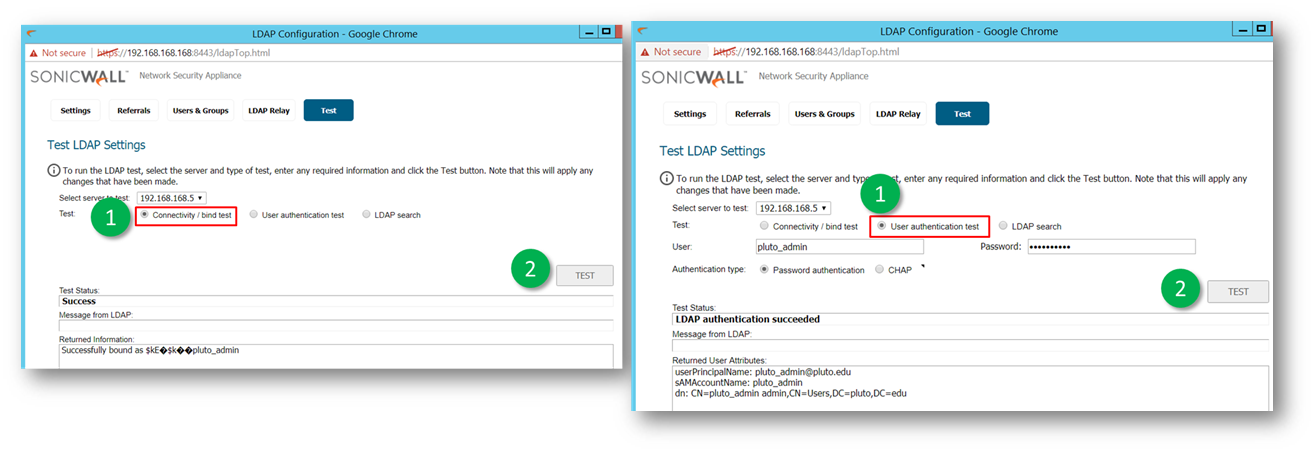
- The LDAP Configuration window allows one to test LDAP users as summarized below.
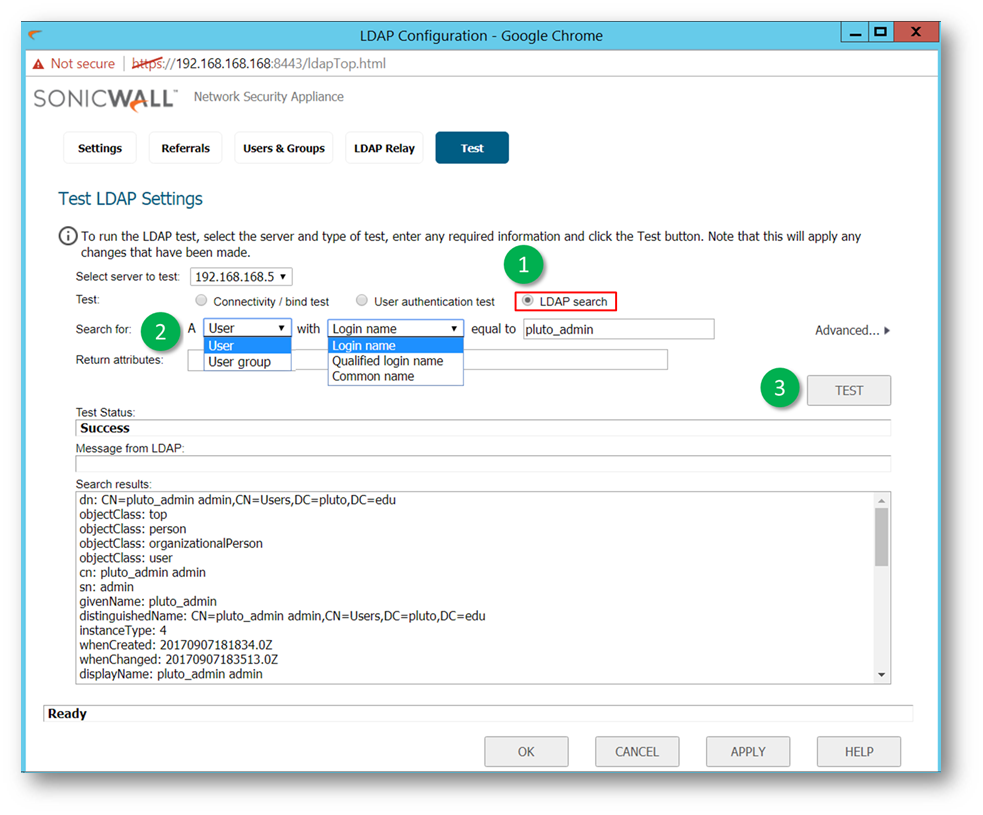
- SonicOS 6.5 LDAP Test has a newer feature where one can do an LDAP search for a user or usergroup as summarized below.
Further Reading: