How do I configure 2FA for SSL VPN with TOTP?
Description
This article provides information on how to configure Multi-Factor Authentication (MFA) for SSL VPN using a 3rd-party TOTP App such as Google Authenticator, Microsoft Authenticator, Duo, Free-OTP, etc
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Create a new user or group:
- Log into the SonicWall appliance, navigate to Device | Users | Local Users & Groups
- Click on Add option
- Under the Settings tab, from the drop-down list beside the One-time password method, select TOTP
 NOTE: This applies to both LDAP or Local Users.
NOTE: This applies to both LDAP or Local Users.
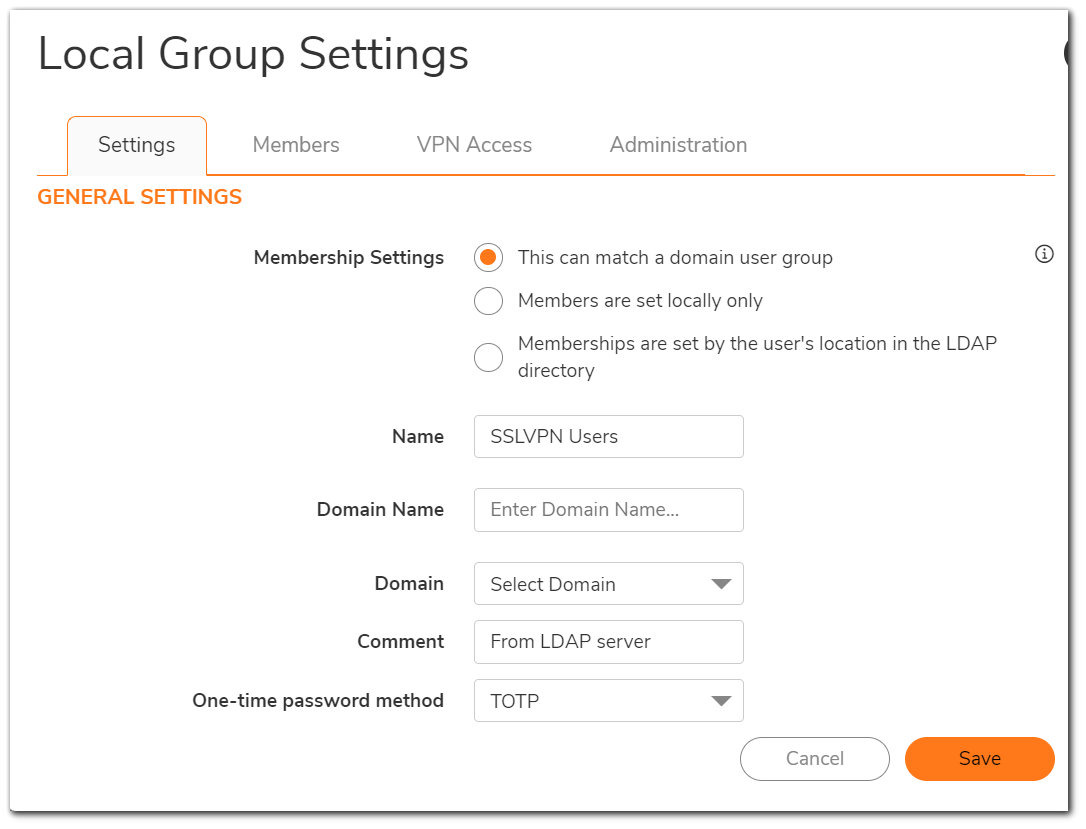
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Create a new user or group:
- Log into the SonicWall appliance, navigate to Users | Local Users & Groups (The screenshots shown in this KB article are from Classic Navigation mode)
- Click on Add option
- Under the Settings tab, from the drop-down list beside the One-time password method, select TOTP
 NOTE: This applies to both LDAP or Local Users.
NOTE: This applies to both LDAP or Local Users.

Steps to be followed on client machine :
1. Download and install Google Authenticator App or any other App that supports TOTP such as Microsoft Authenticator, Duo or Free-OTP from your mobile phone.
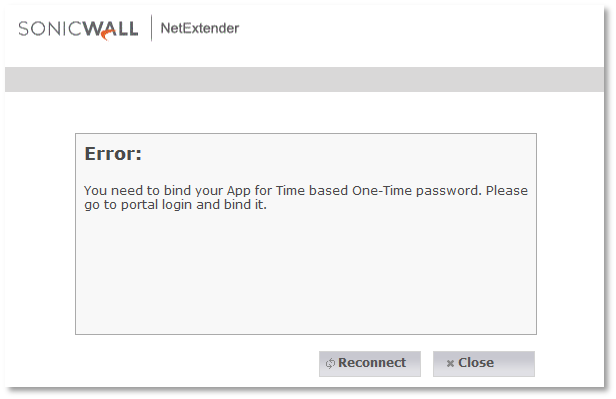
 NOTE: Trying to log in with SSL VPN client, NetExtender, would result in an error: "You need to bind your App for Time based One-Time password. Please go to the portal to login and bind it." This is referring to the SSLVPN Virtual Office Portal (explained in the next step)
NOTE: Trying to log in with SSL VPN client, NetExtender, would result in an error: "You need to bind your App for Time based One-Time password. Please go to the portal to login and bind it." This is referring to the SSLVPN Virtual Office Portal (explained in the next step)
2. Log into SSL VPN portal, aka. the Virtual Office. Remote clients have to login to the virtual office portal by typing firewall public IP followed by port number 4433 in the browser URL (https://myfirewall:4433), to bind the Google Authenticator App
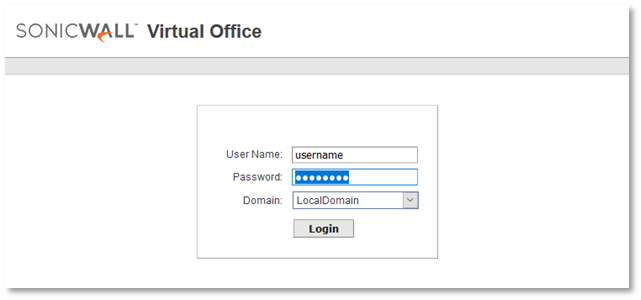
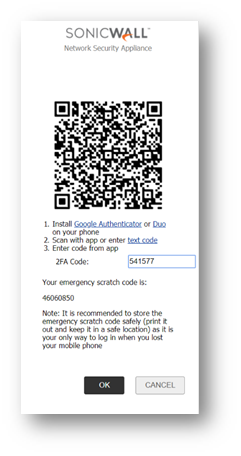
3. Post entering their username & password, they will be prompted with a QR code and an Emergency Scratch code

 NOTE: Please store the Emergency Scratch Code as it is the only way to login if the mobile device is lost or reset.
NOTE: Please store the Emergency Scratch Code as it is the only way to login if the mobile device is lost or reset.
4. Open the Google Authenticator App or Duo on the Mobile phone, then click on Begin

5. Select Scan a barcode to scan QR code

6. Once the QR code is scanned, the App will provide a 6-digit One-Time Password (OTP), then click Add Account. SNWL is added

7. Enter the OTP beside the 2FA Code option on the pop-up window with the QR code
8. Open NetExtender
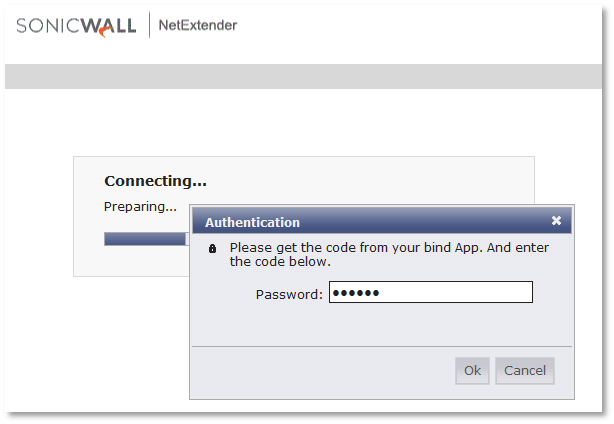
- Enter Active Directory credentials. Then, a window will pop up asking to enter an authentication code (password)
- On mobile phone, open Google Authenticator, and go to SNWL account to get one-time password (OTP)
- On the Authentication window, enter OTP in the Password field, and click OK to establish the SSL VPN connection