MedusaLocker is Sweeping Its Gaze

Overview
This week, the Sonicwall Capture Labs threat research team investigated a sample of MedusaLocker Ransomware. This ransomware-as-a-service (RaaS), in regular operation since 2021, has recently seen a resurgence as noted in this recent CISA alert. The variant analyzed here uses Bcdedit to perform modifications to the boot loader, remote shell commands to escalate from 32- to 64-bit prompts to bypass security, and aggressively kills all backup services while files are encrypted.
Infection Cycle
The main infector is not packed or encrypted and a majority of the data is unencoded during static analysis.
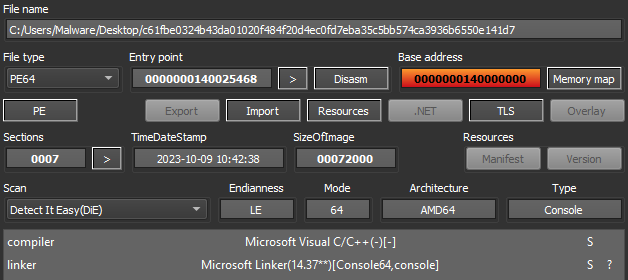
The first item that differs from a regular executable is the section labeled “_RDATA”, along with strings for a debug file named ‘D:\Education\locker\bin\stub_win_x64_encrypter.pdb’. Additional and previously noted strings are “PUTINHUILLO1337” and the directory item “SOFTWARE/PAIDMEMES”, which may or may not be created during runtime.
When the program is launched, checks are performed for locale, system time, and running processes. There are also environmental checks for virtual environments such as VMWare, and any debugging software. Then, the following actions are taken while the system files are encrypted using AES-256:
- bcdedit.exe is run to change boot settings and prevent Safe Mode using the following commands:
- C:\Windows\SysWOW64\cmd.exe \\?\C:\Windows\SysWOW64\cmd.exe /c %windir%\sysnative\cmd.exe /c bcdedit.exe /set {default} recoverynabled No
- C:\Windows\SysWOW64\cmd.exe \\?\C:\Windows\SysWOW64\cmd.exe /c %windir%\sysnative\cmd.exe /c bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures
- Shadow Copies are removed using vssadmin:
- C:\Windows\SysWOW64\cmd.exe \\?\C:\Windows\SysWOW64\cmd.exe /c %windir%\sysnative\cmd.exe /c vssadmin.exe Delete Shadows /All /Quiet
- A registry key is created for persistence:
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\BabyLockerKZ
- taskkill.exe is used to terminate the following processes:
- sqlserv.exe
- sqlbrowser.exe
- sqlwriter.exe
- sqlagent.exe
- msmdsrv.exe
- msdtssrvr.exe
- sqlceip.exe
- fdlauncher.exe
- ssms.exe
- fdhost.exe
- msftesql.exe
- pg_ctl.exe
- postgres.exe
- Elevated commands are used to stop additional services:
- C:\Windows\SysWOW64\cmd.exe \\?\C:\Windows\SysWOW64\cmd.exe /c %windir%\sysnative\cmd.exe /c net stop {MSSQLServerADHelper100, MSSQL$ISARS, MSSQL$MSFW, SQLAgent$ISARS, SQLAgent$MSFW, SQLBrowser, ReportServer$ISARS, SQLWriter}
- Uses WMIC to query system information:
- IWbemServices::CreateInstanceEnum - root\cimv2 : Win32_BIOS
- IWbemServices::CreateInstanceEnum - root\cimv2 : Win32_ComputerSystem

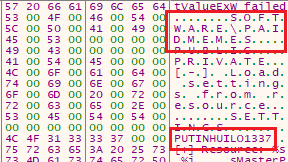
Windows Restart Manager is loaded to unlock files in use for encryption. An internet connectivity check is performed by querying ‘google.com’ over DNS. Keystrokes are hooked using ‘GetAsyncKeyState’, though no traffic or logging of keystrokes was detected during runtime.
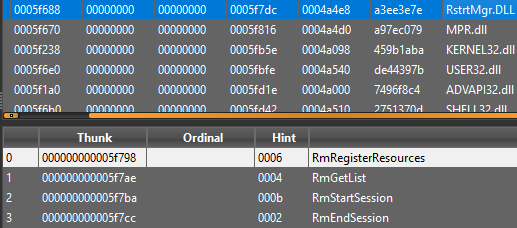
Once the encryption has started, a ransom note called ‘How_to_back_files.html’ is written to every directory.
The listed addresses to contact are ithelp01@securitymy.name and ithelp01@yousheltered.com.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this malware, this and other variants of MedusaLocker are detected and stopped by RTDMI.
IOCs
c61fbe0324b43da01020f484f20d4ec0fd7eba35c5bb574ca3936b6550e141d7
Share This Article

An Article By
An Article By
Security News
Security News
