How can I configure LDAP authentication for SSLVPN users?
Description
This article outlines all necessary steps to configure LDAP authentication for SSL-VPN users.
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
SSL-VPN Address Object
- Navigate to Object | Match Objects | Addresses and click on Add.
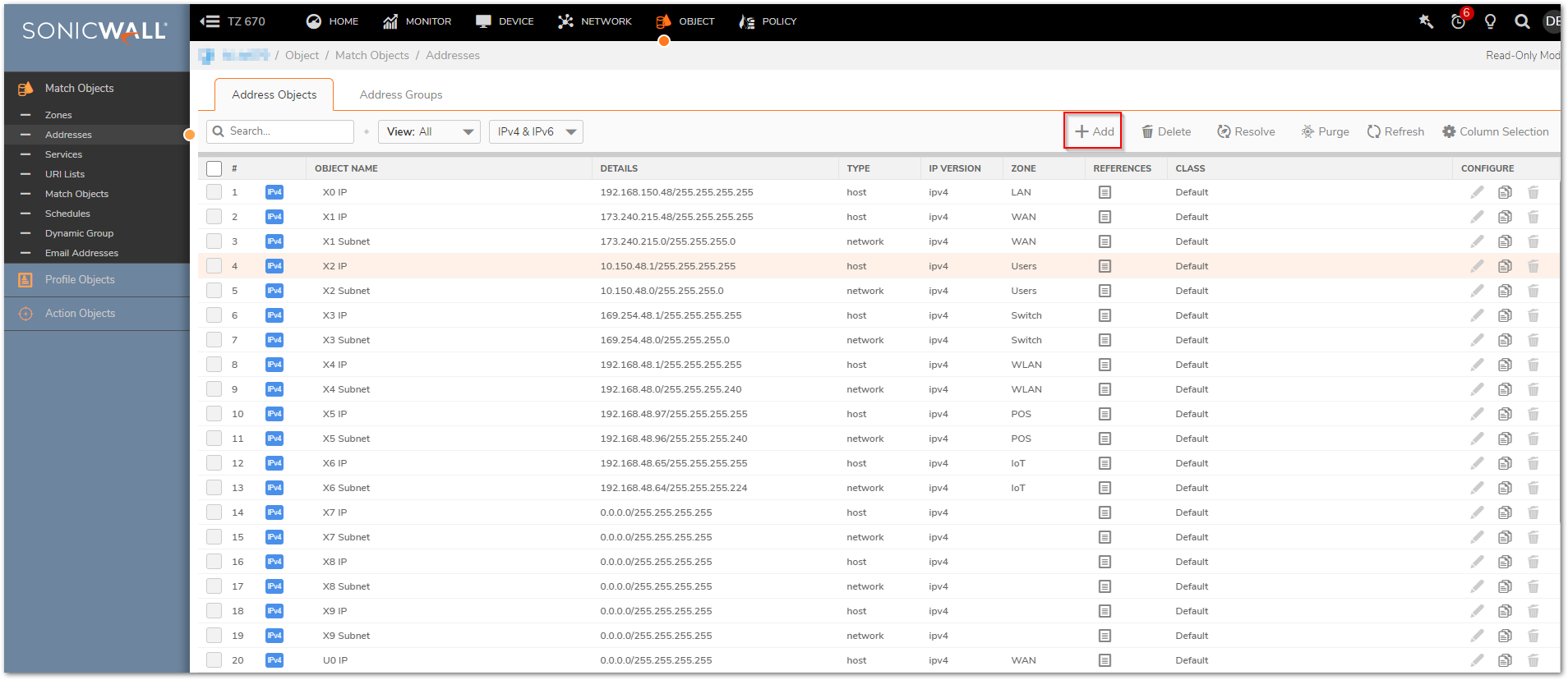
- In the pop-up window, enter the information for your SSL VPN Range. An example Range is included below:
- Name: SSL VPN Range
 TIP: This is only a Friendly Name used for Administration.
TIP: This is only a Friendly Name used for Administration. - Zone: SSLVPN
- Type : Range
 NOTE: You can use a Network or Host as well.
NOTE: You can use a Network or Host as well. - Starting IP Address: 192.168.168.100
- Ending IP Address: 192.168.168.110

- Name: SSL VPN Range
SSLVPN Configuration
- Navigate to Network | SSL VPN | Server Settings.
- Enable or disable SSL-VPN access by toggling the zone. Here we will be enabling SSL-VPN for WAN.
- Set the SSL VPN Port, and Domain as desired.
 NOTE: The SSLVPN port will be needed when connecting using Mobile Connect and NetExtender unless the port number is 443. Port 443 can only be used if the management port of the firewall is not 443.The Domain is used during the user login process.
NOTE: The SSLVPN port will be needed when connecting using Mobile Connect and NetExtender unless the port number is 443. Port 443 can only be used if the management port of the firewall is not 443.The Domain is used during the user login process. TIP: If you want to be able to manage the firewall via GUI or SSH over SSLVPN these features can be enabled separately here as well.
TIP: If you want to be able to manage the firewall via GUI or SSH over SSLVPN these features can be enabled separately here as well.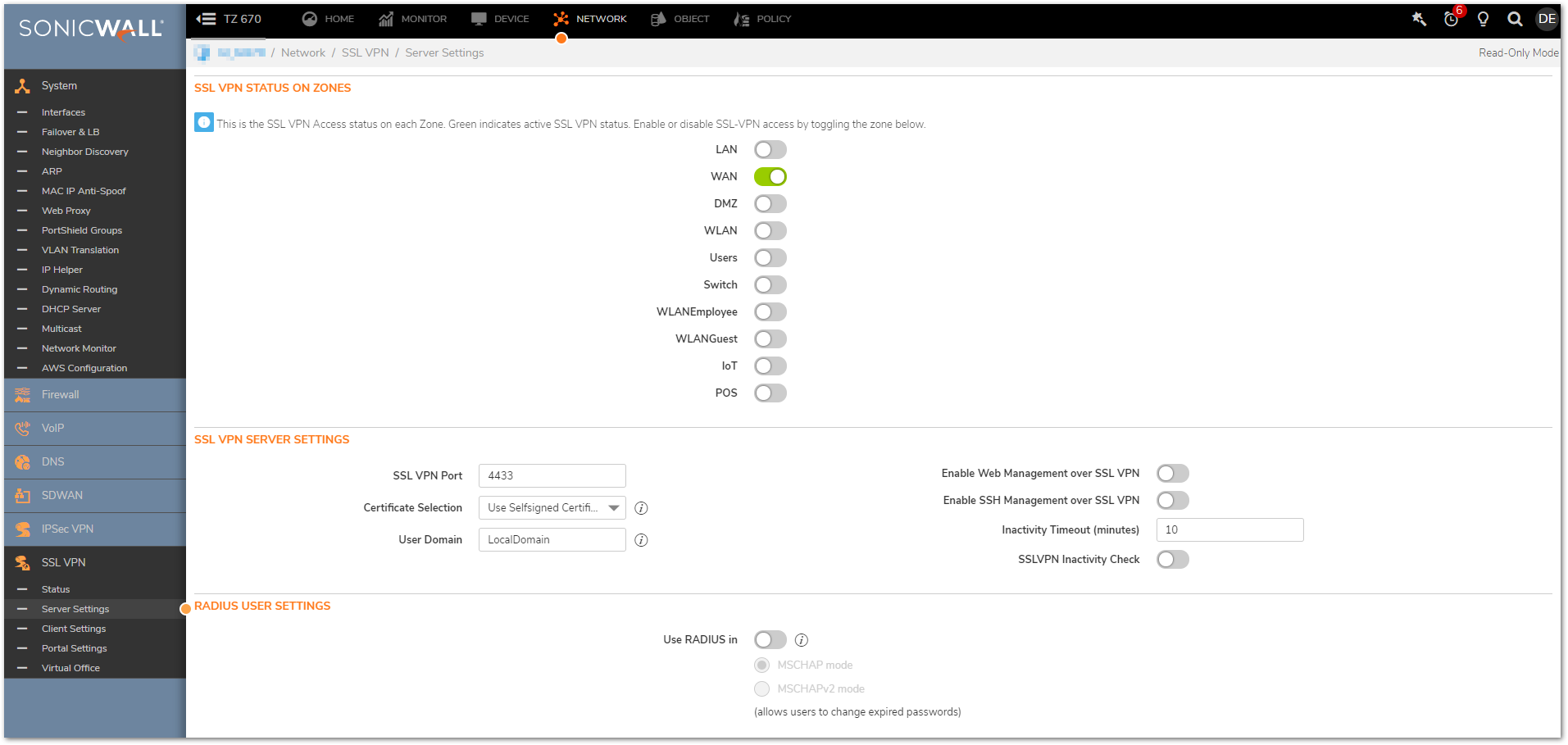
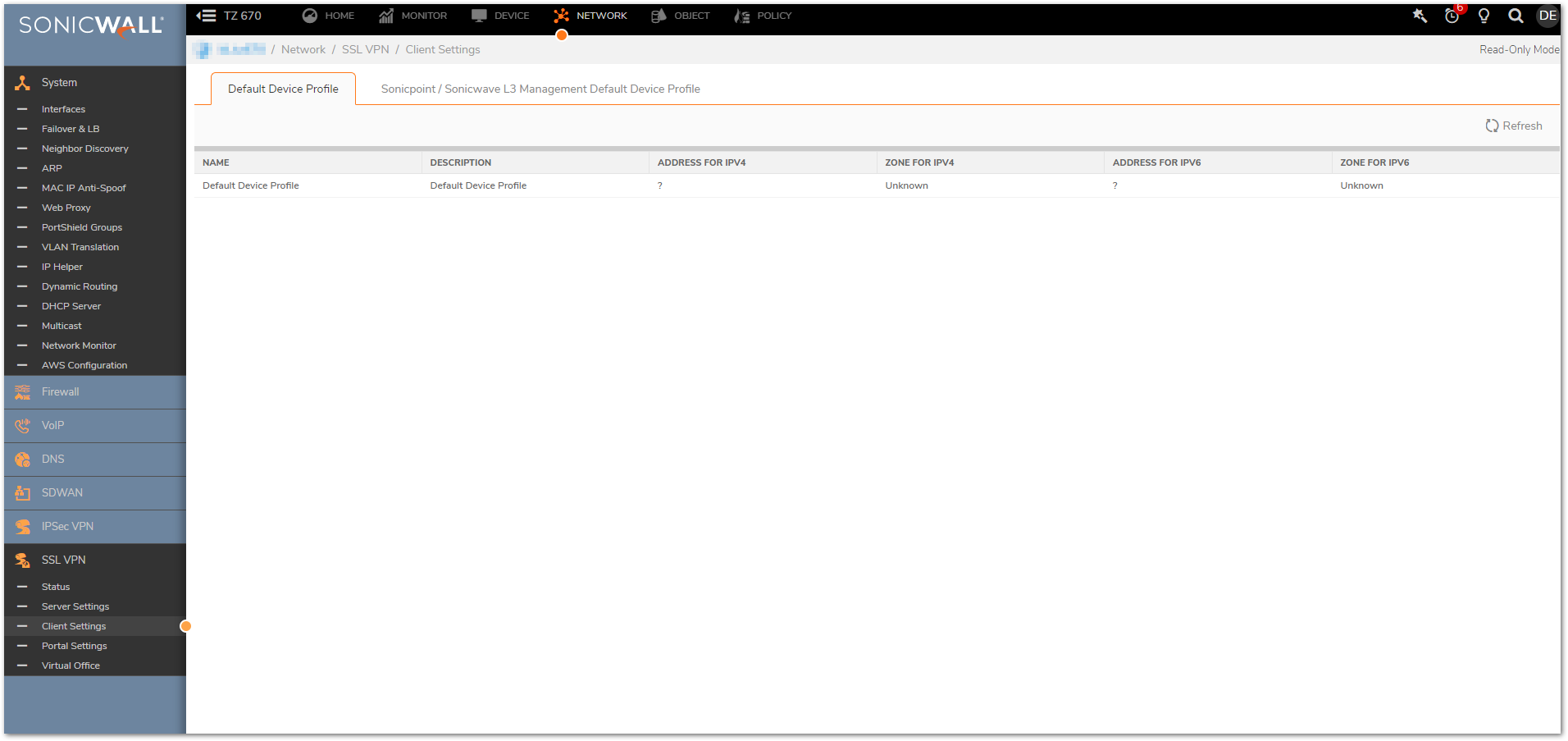
- Navigate to Network | SSL VPN | Client Settings page. The SSL VPN | Client Settings page allows the administrator to configure the client address range information and NetExtender client settings, the most important being where the SSL-VPN will terminate (e.g. on the LAN in this case) and which IPs will be given to connecting clients.
 CAUTION: NetExtender cannot be terminated on an Interface that is paired to another Interface using Layer 2 Bridge Mode. This includes Interfaces bridged with a WLAN Interface. Interfaces that are configured with Layer 2 Bridge Mode are not listed in the "SSLVPN Client Address Range" Interface drop-down menu. For NetExtender termination, an Interface should be configured as a LAN, DMZ, WLAN, or a custom Trusted, Public, or Wireless zone, and also configured with the IP Assignment of Static.
CAUTION: NetExtender cannot be terminated on an Interface that is paired to another Interface using Layer 2 Bridge Mode. This includes Interfaces bridged with a WLAN Interface. Interfaces that are configured with Layer 2 Bridge Mode are not listed in the "SSLVPN Client Address Range" Interface drop-down menu. For NetExtender termination, an Interface should be configured as a LAN, DMZ, WLAN, or a custom Trusted, Public, or Wireless zone, and also configured with the IP Assignment of Static. - Click Configure for the Default Device Profile.
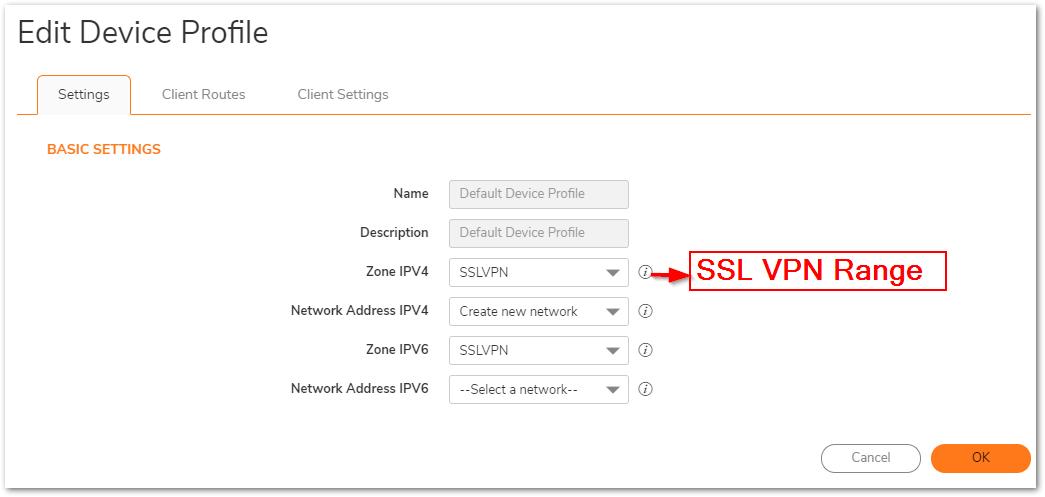
- Set the Zone IP V4 as SSLVPN. Set Network Address IP V4 as the Address Object you created earlier (SSLVPN Range).
- The Client Routes tab allows the administrator to control what network access SSL VPN Users are allowed. The NetExtender client routes are passed to all NetExtender clients and are used to govern which networks and resources remote users can access via the SSL VPN connection.
 CAUTION: All SSL VPN Users can see these routes but without appropriate VPN Access on their User or Group they will not be able to access everything shown in the routes. Please make sure to set VPN Access appropriately.
CAUTION: All SSL VPN Users can see these routes but without appropriate VPN Access on their User or Group they will not be able to access everything shown in the routes. Please make sure to set VPN Access appropriately.
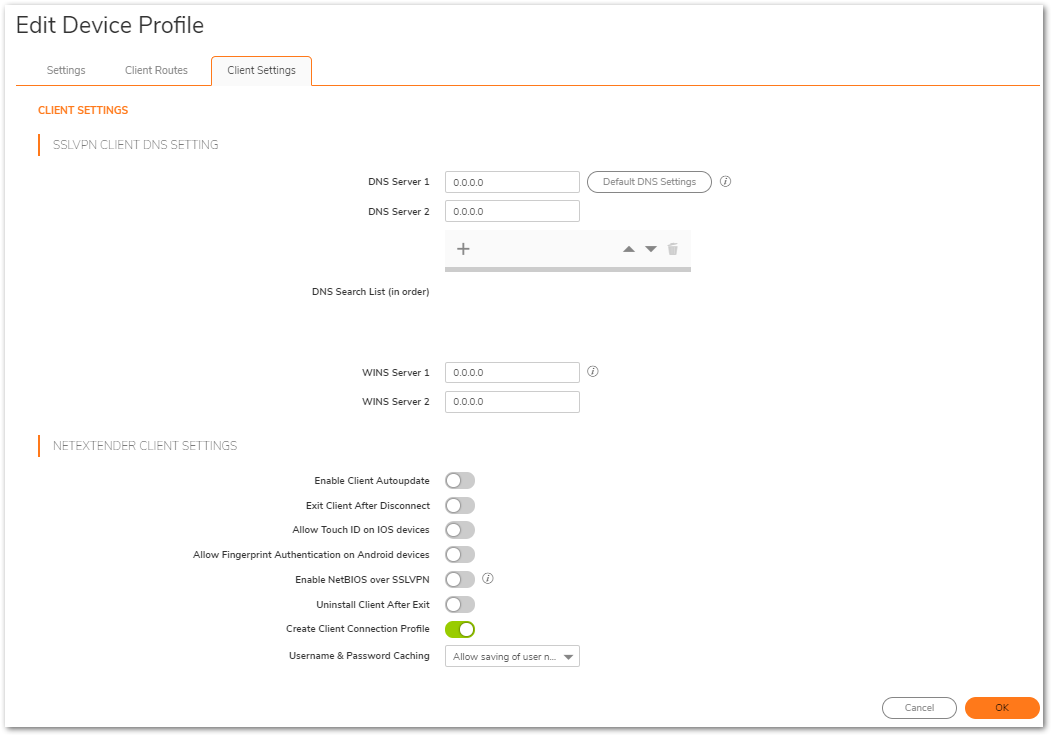
- The Client Settings tab allows the administrator to input DNS, WINS, and Suffix information while also controlling the caching of passwords, user names, and the behavior of the NetExtender client.
- Input the necessary DNS/WINS information and a DNS Suffix if SSL VPN Users need to find Domain resources by name.
- Enable Create Client Connection Profile - The NetExtender client will create a connection profile recording the SSL VPN Server name, the Domain name and optionally the username and password.
LDAP Settings
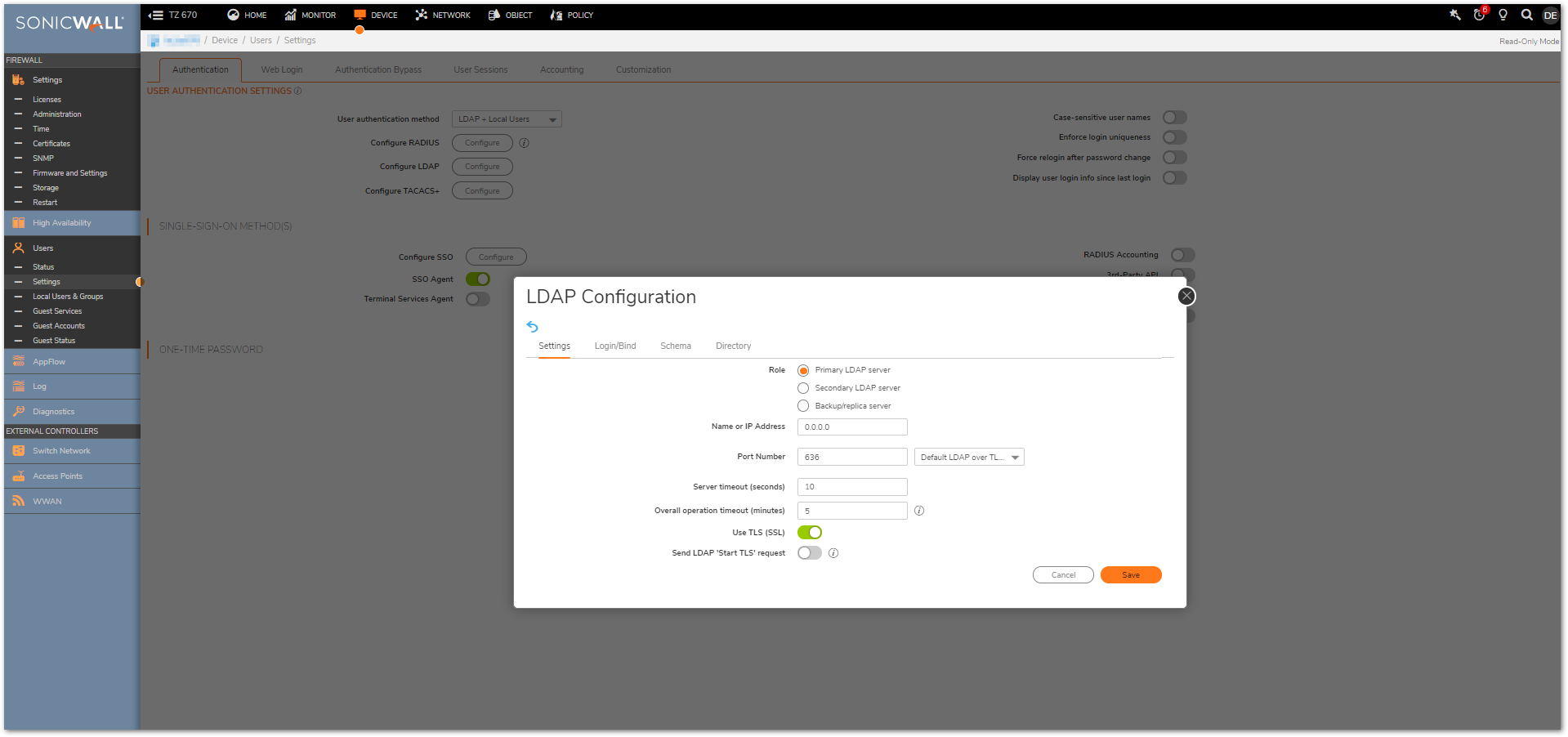
- Navigate to Device | Users | Settings.
- Select LDAP (or LDAP + Local Users) as authentication method.
- Click Configure LDAP.
- Click Add to add a new LDAP server.
- Enter the Name or IP address, Port Number, and indicate if you wish to Use TLS (SSL). Additionally, you will need to choose if this is the Primary, Secondary or a Backup/replica server.
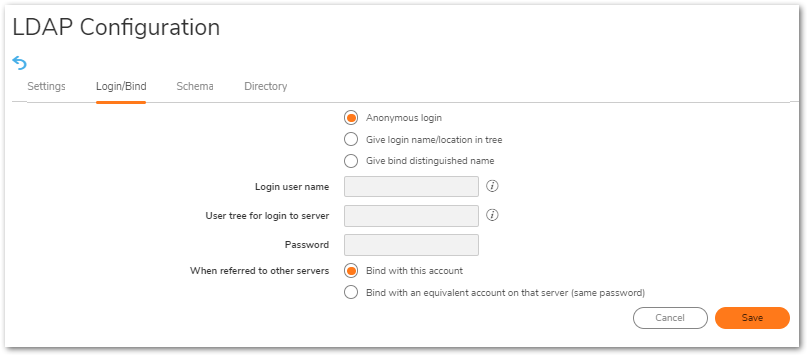
- On the Login/Bind tab, Select the login type (Anonymous, login name in tree or bind distinguished name) and enter the Login user name, User tree for login to server and Password if applicable.
- On the Directory tab, Make the necessary adjustments to the Trees containing users and the Trees containing user groups or use the AUTO-CONFIGURE button as appropriate.

- Click SAVE.
- In the LDAP configuration window, access the Users & Groups Tab and click Import Users.
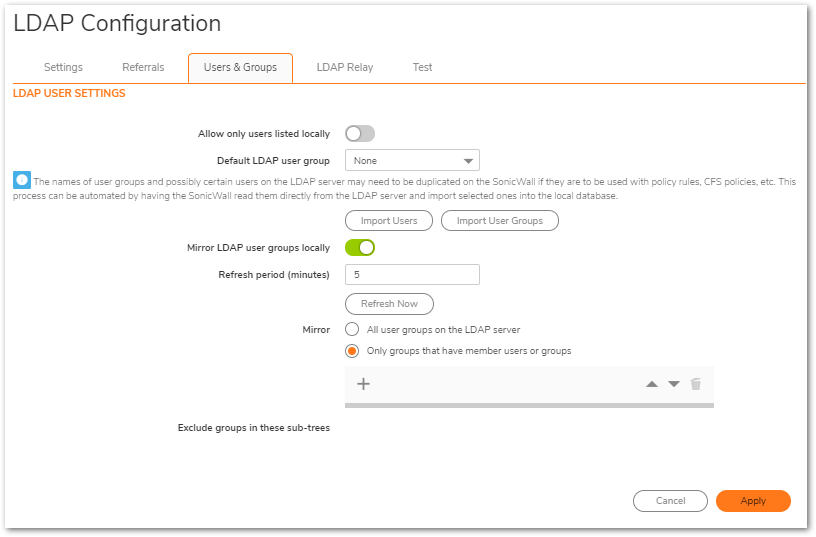
- Select the appropriate LDAP server to import from along with the appropriate domain(s) to include.
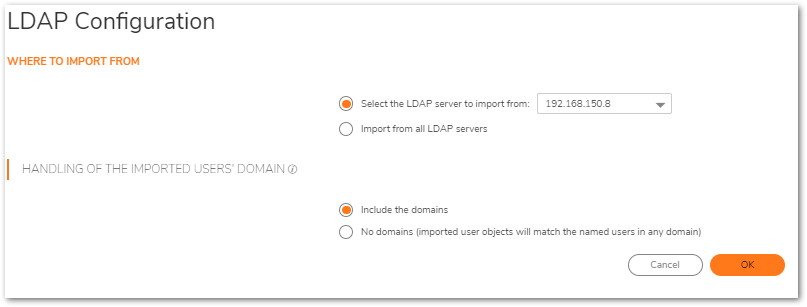
- Choose the way in which you prefer user names to display.
 NOTE: This is a personal preference and does not affect.
NOTE: This is a personal preference and does not affect.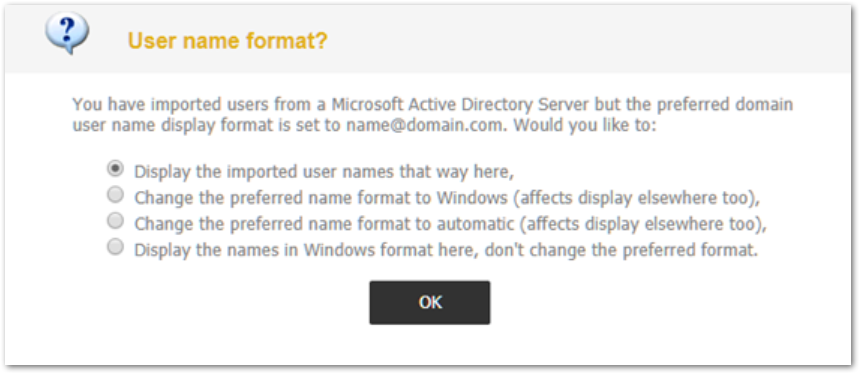
- Select the appropriate users you wish to import and click Save Selected.
 NOTE: Make a note of which users or groups that are being imported as you will need to make adjustments to them in the next section of this article.
NOTE: Make a note of which users or groups that are being imported as you will need to make adjustments to them in the next section of this article. 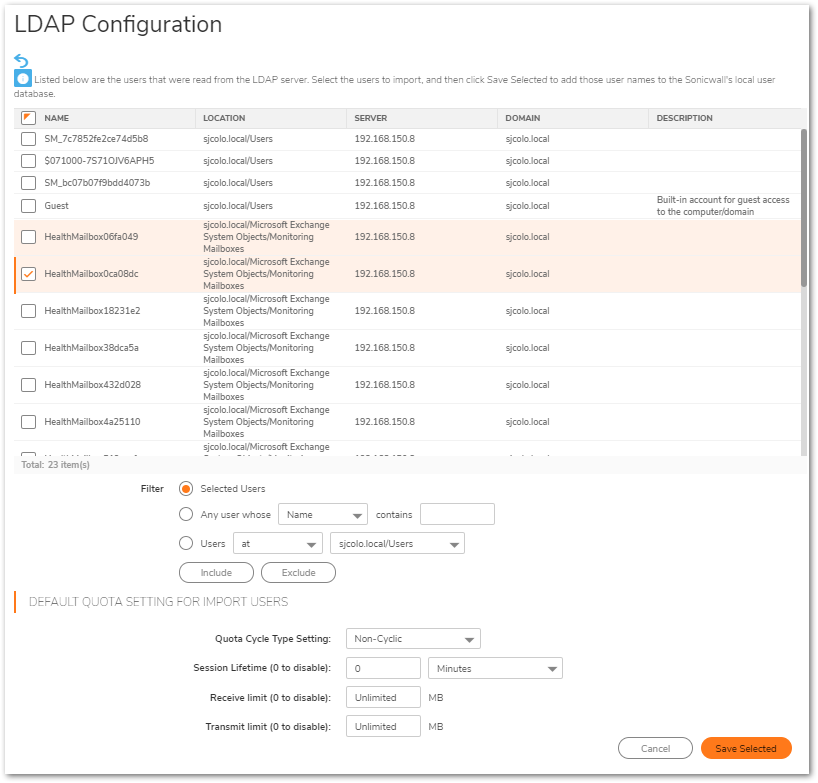
- Click Save Selected.
User Settings
- Navigate to the Device | Users | Local Users & Groups page.
- On the appropriate Local User or Local Groups Tab, Click configure on the newly imported LDAP User or Group.
 NOTE: This is dependant on the User or Group you imported in the steps above. If you imported a user, you will configure the imported user, if you have imported a group, you will access the Local Groups tab and configure the imported group.
NOTE: This is dependant on the User or Group you imported in the steps above. If you imported a user, you will configure the imported user, if you have imported a group, you will access the Local Groups tab and configure the imported group. - Under VPN Access tab select the appropriate address objects/groups that your LDAP User or LDAP Group will need access to and click the right arrow to Add Network to Access List.

- Click Save .
- To make your User or Group a member of the SSLVPN Services group for access to SSLVPN, access the Local Groups tab and click Configure on SSLVPN Services.
- On the Members tab, Add your Imported user or group as to the Member Users and Groups.
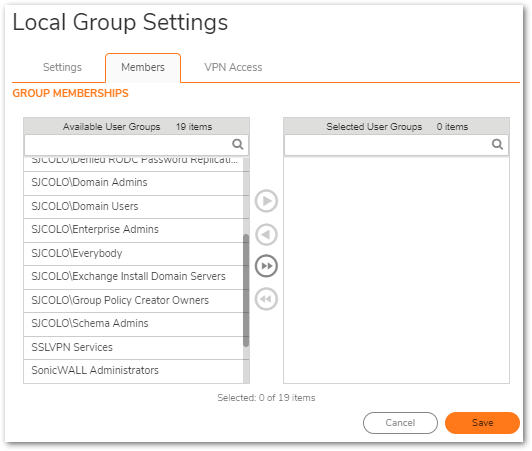
- Click Save.
- As per the above configuration, only members of the Group will be able to connect to SSL-VPN.
 TIP: Inorder for the LDAP users to be able to change their AD password via Netextender, make sure "ALL LDAP Users" group is added to the "SSLVPN Services" group.
TIP: Inorder for the LDAP users to be able to change their AD password via Netextender, make sure "ALL LDAP Users" group is added to the "SSLVPN Services" group.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
SSL-VPN Address Object
- Login to the SonicWall management GUI.
- Click Manage in the top navigation menu
- Navigate to Objects | Address Objects and click Add at the top of the pane.
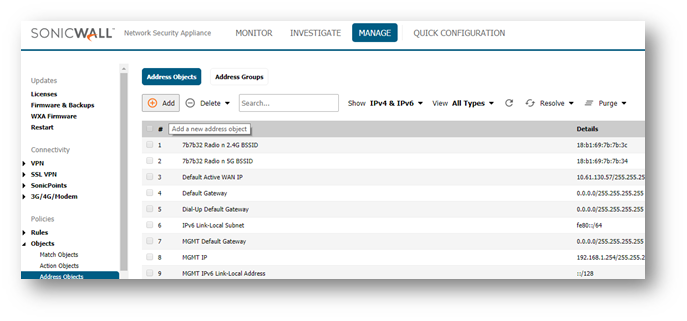
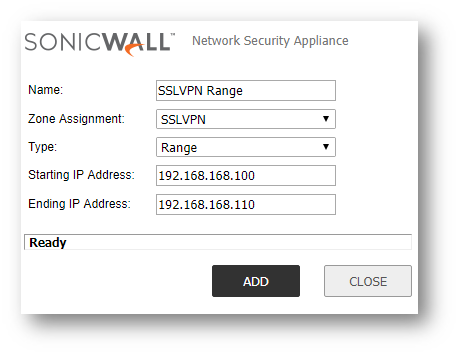
- In the pop-up window, enter the information for your SSL VPN Range. An example Range is included below:
- Name: SSL VPN Range
 TIP: This is only a Friendly Name used for Administration.
TIP: This is only a Friendly Name used for Administration. - Zone: SSLVPN
- Type : Range
 NOTE: You can use a Network or Host as well.
NOTE: You can use a Network or Host as well. - Starting IP Address: 192.168.168.100
- Ending IP Address: 192.168.168.110
SSLVPN Configuration
- Navigate to SSL-VPN | Server Settings page.
- Click Red Bubble for WAN, it should become Green. This indicates that SSL VPN Connections will be allowed on the WAN Zone.
- Set the SSL VPN Port, and Domain as desired.
NOTE: The SSLVPN port will be needed when connecting using Mobile Connect and NetExtender unless the port number is 443. Port 443 can only be used if the management port of the firewall is not 443.The Domain is used during the user login process.
TIP: If you want to be able to manage the firewall via GUI or SSH over SSLVPN these features can be enabled separately here as well.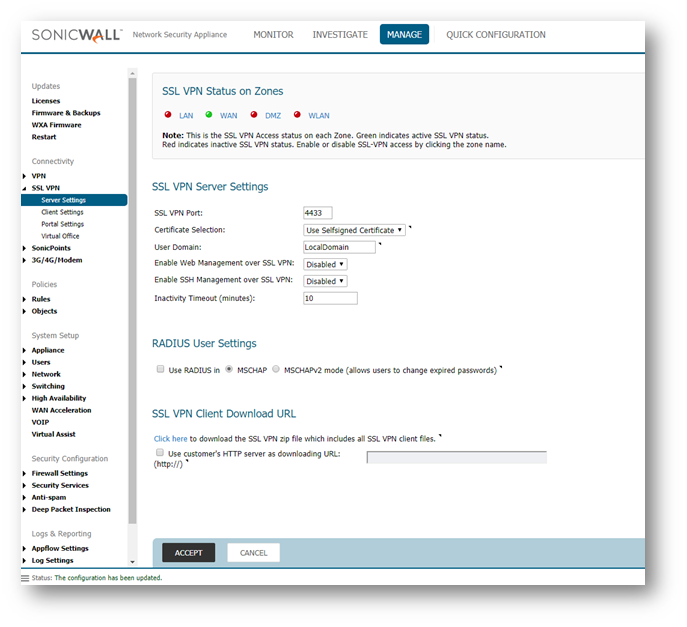
- Navigate to SSL VPN | Client Settings page.The SSL VPN | Client Settings page allows the administrator to configure the client address range information and NetExtender client settings, the most important being where the SSL-VPN will terminate (e.g. on the LAN in this case) and which IPs will be given to connecting clients
 CAUTION: NetExtender cannot be terminated on an Interface that is paired to another Interface using Layer 2 Bridge Mode. This includes Interfaces bridged with a WLAN Interface. Interfaces that are configured with Layer 2 Bridge Mode are not listed in the "SSLVPN Client Address Range" Interface drop-down menu. For NetExtender termination, an Interface should be configured as a LAN, DMZ, WLAN, or a custom Trusted, Public, or Wireless zone, and also configured with the IP Assignment of Static.
CAUTION: NetExtender cannot be terminated on an Interface that is paired to another Interface using Layer 2 Bridge Mode. This includes Interfaces bridged with a WLAN Interface. Interfaces that are configured with Layer 2 Bridge Mode are not listed in the "SSLVPN Client Address Range" Interface drop-down menu. For NetExtender termination, an Interface should be configured as a LAN, DMZ, WLAN, or a custom Trusted, Public, or Wireless zone, and also configured with the IP Assignment of Static. - Click Configure for the Default Device Profile.
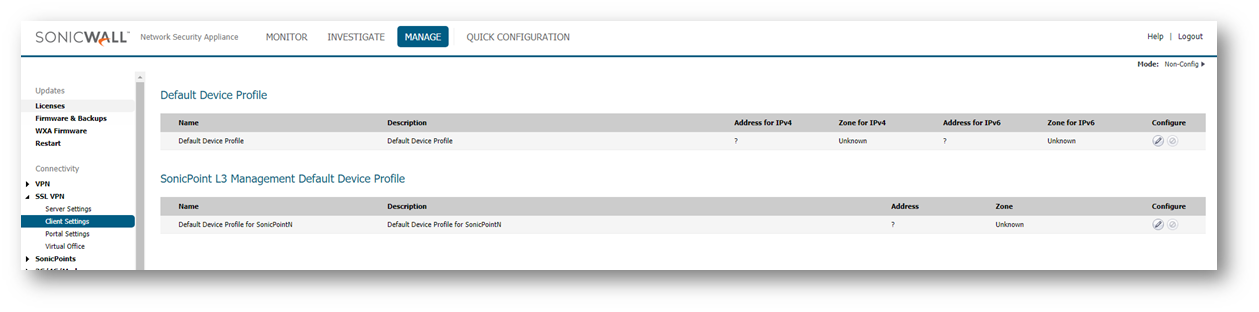
- Set the Zone IP V4 as SSLVPN. Set Network Address IP V4 as the Address Object you created earlier (SSLVPN Range).

- The Client Routes tab allows the administrator to control what network access SSL VPN Users are allowed. The NetExtender client routes are passed to all NetExtender clients and are used to govern which networks and resources remote users can access via the SSL VPN connection.
 CAUTION: All SSL VPN Users can see these routes but without appropriate VPN Access on their User or Group they will not be able to access everything shown in the routes. Please make sure to set VPN Access appropriately.
CAUTION: All SSL VPN Users can see these routes but without appropriate VPN Access on their User or Group they will not be able to access everything shown in the routes. Please make sure to set VPN Access appropriately.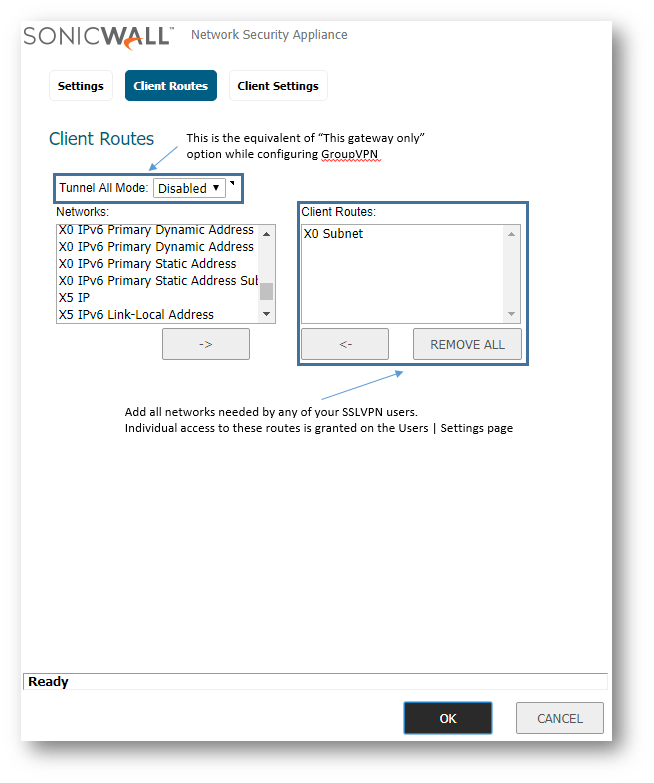
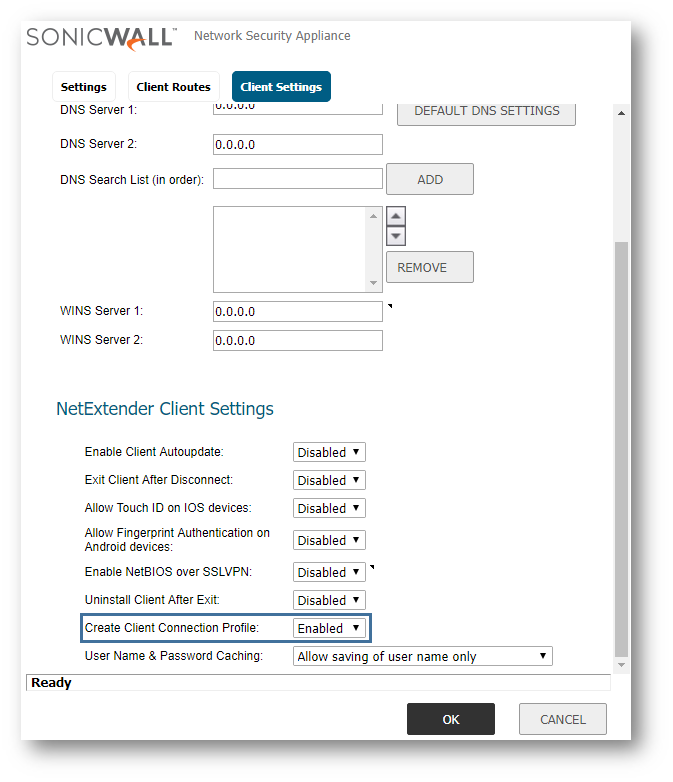
- The Client Settings tab allows the administrator to input DNS, WINS, and Suffix information while also controlling the caching of passwords, user names, and the behavior of the NetExtender client.
- Input the necessary DNS/WINS information and a DNS Suffix if SSL VPN Users need to find Domain resources by name.
- Enable Create Client Connection Profile - The NetExtender client will create a connection profile recording the SSL VPN Server name, the Domain name and optionally the username and password.

LDAP Settings
- Navigate to Users | Settings page.
- Select LDAP (or LDAP + Local Users) as authentication method and click Configure LDAP.
- Click Add to add a new LDAP server.
- Enter the Name or IP address, Port Number, and indicate if you wish to Use TLS (SSL). Additionally, you will need to choose if this is the Primary, Secondary or a Backup/replica server.
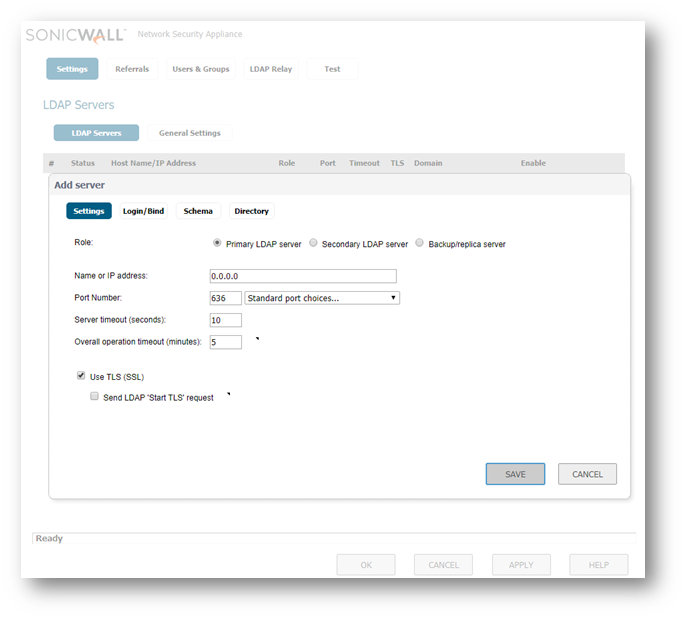
- On the Login/Bind tab, Select the login type (Anonymous, login name in tree or bind distinguished name) and enter the Login user name, User tree for login to server and Password if applicable.

- On the Directory tab, Make the necessary adjustments to the Trees containing users and the Trees containing user groups or use the AUTO-CONFIGURE button as appropriate.

- Click SAVE.
- In the LDAP configuration window, access the Users & Groups Tab and click Import Users.
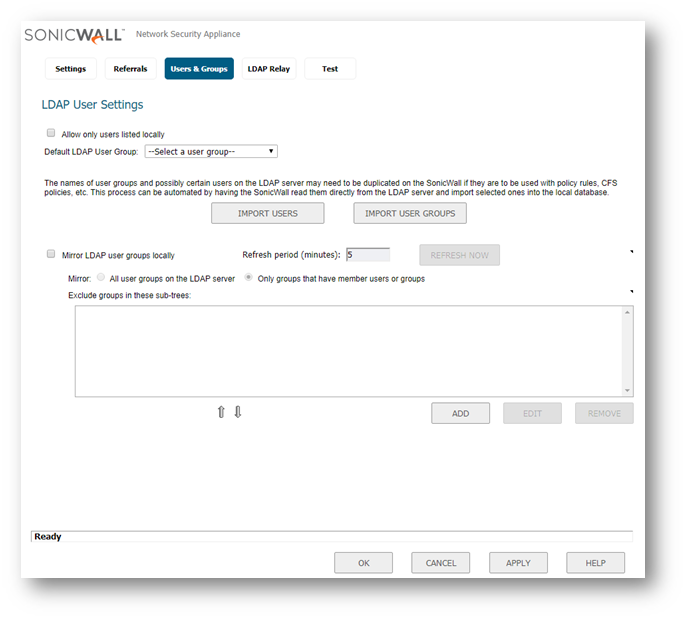
- Select the appropriate LDAP server to import from along with the appropriate domain(s) to include.

- Choose the way in which you prefer user names to display.
NOTE: This is a personal preference and does not affect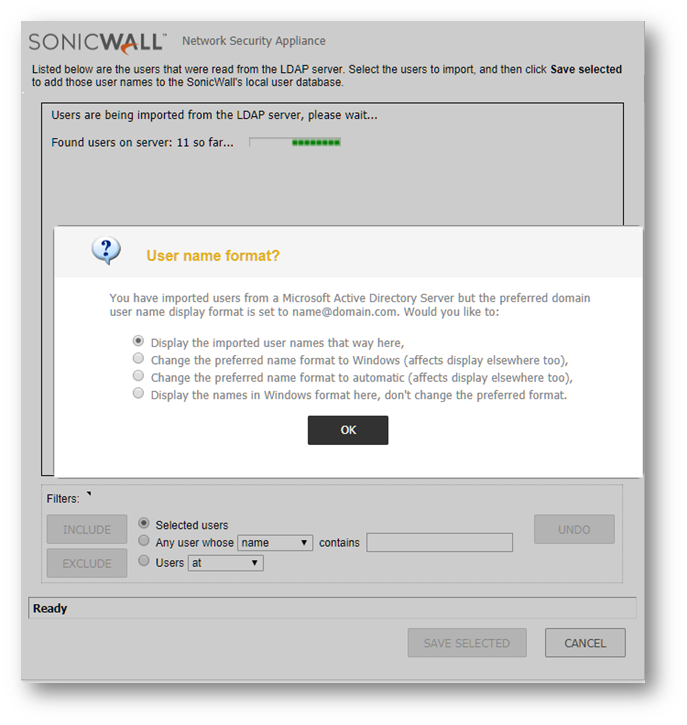
- Select the appropriate users you wish to import and click Save Selected.
 NOTE: Make a note of which users or groups that are being imported as you will need to make adjustments to them in the next section of this article.
NOTE: Make a note of which users or groups that are being imported as you will need to make adjustments to them in the next section of this article.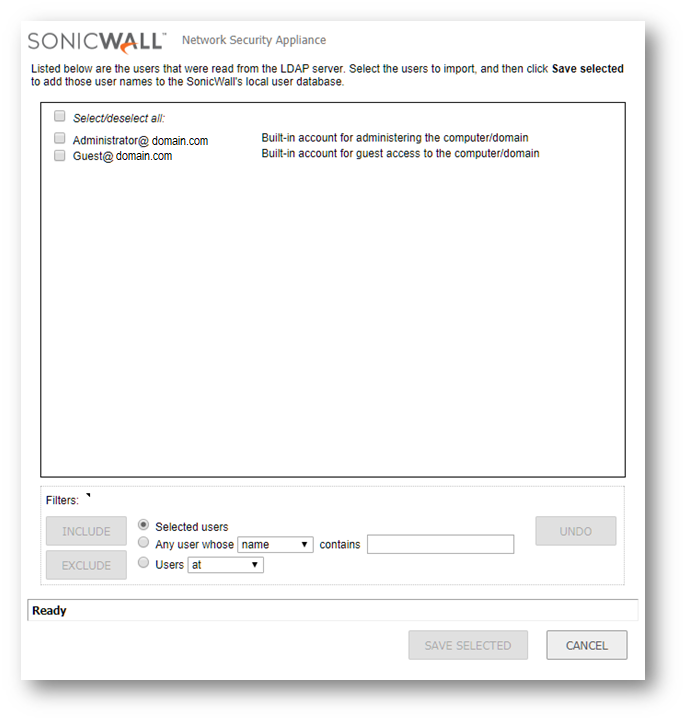
- Click OK.
User Settings
- Navigate to the Users | Local Users & Groups page.
- On the appropriate Local User or Local Groups Tab, Click configure on the newly imported LDAP User or Group.
 NOTE: This is dependant on the User or Group you imported in the steps above. If you imported a user, you will configure the imported user, if you have imported a group, you will access the Local Groups tab and configure the imported group.
NOTE: This is dependant on the User or Group you imported in the steps above. If you imported a user, you will configure the imported user, if you have imported a group, you will access the Local Groups tab and configure the imported group. - Under VPN Access tab select the appropriate address objects/groups that your LDAP User or LDAP Group will need access to and click the right arrow to Add Network to Access List.
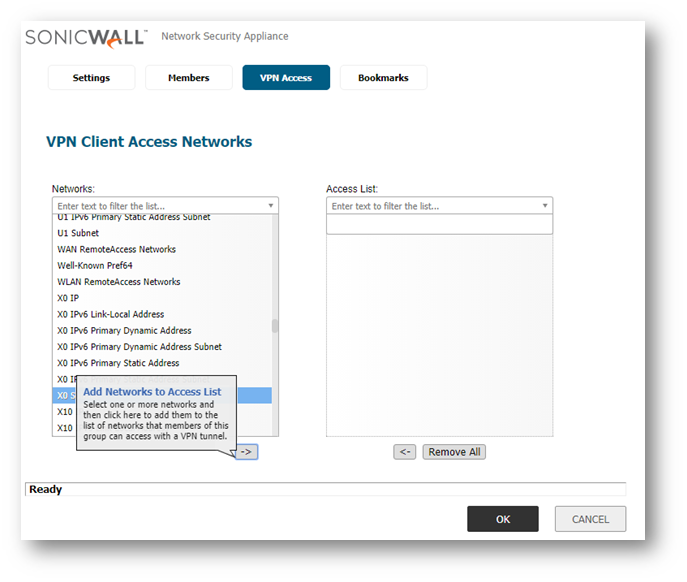
- Click OK .
- To make your User or Group a member of the SSLVPN Services group for access to SSLVPN, access the Local Groups tab and click Configure on SSLVPN Services.
- On the Members tab, Add your Imported user or group as to the Member Users and Groups.

- Click OK save the settings and close the window.
- As per the above configuration, only members of the Group will be able to connect to SSL-VPN.
 TIP: Inorder for the LDAP users to be able to change their AD password via Netextender, make sure "ALL LDAP Users" group is added to the "SSLVPN Services" group.
TIP: Inorder for the LDAP users to be able to change their AD password via Netextender, make sure "ALL LDAP Users" group is added to the "SSLVPN Services" group.