MSS FW Best Practices: Security Services
Description
 CAUTION: These documents are intended to provide partners with firewall configuration recommendations ONLY. They contain examples and caution should be exercised when making changes to your firewall as unplanned changed could result in downtime based on the complexity of the environment and/or configuration.
CAUTION: These documents are intended to provide partners with firewall configuration recommendations ONLY. They contain examples and caution should be exercised when making changes to your firewall as unplanned changed could result in downtime based on the complexity of the environment and/or configuration.
MSS Recomended SonicWall Firewall Best Practices Index
Excluding Devices from Security Services
- Each security service has a spot to specify an “Exclusion Group”.
- There are 2 ways to exclude local devices from Security Services:
- Create a “Security Exclusion Group” and exclude it from all security services.
- Create an “Address Object Exclusion Group” for each security service and exclude them from the applicable security service. (This is recommended as it’s more secure and retains the most control)
- Only exclude devices if absolutely necessary.
- Excluded devices will NOT be protected.
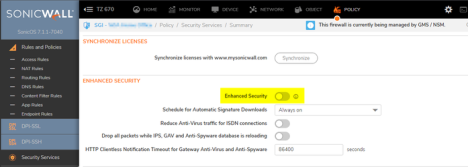
Security Services Enhanced Security Setting
All generation 7 firewalls come set to Performance Optimized by default which is the recommended setting.
- To enable what was formally known in Gen 6/6.5 as Maximum Security, enable Enhanced Security (Not recommended).
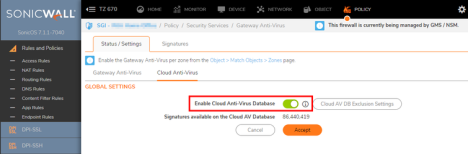
Gateway Anti-Virus (GAV)
GAV best practices and recommended configuration
- Under the Gateway Anti-Virus tab:
- Enable all options.
- Note on TCP Stream: If you do not enable, DPI will only scan listed protocols (HTTP, FTP, SMTP, etc.) on default port(s)

- Under the Cloud Anti-Virus tab:
- Enable Cloud Anti-Virus Database
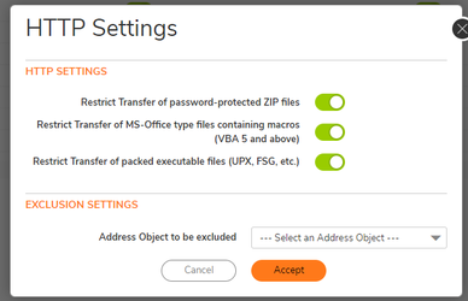
- Click Configure for each protocol (HTTP, FTP, etc.):
- Enable: Restrict Transfer of password-protected ZIP files
- Enable: Restrict Transfer of MS-Office type files containing macros (VBA 5 and above)
- Enable: Restrict Transfer of packed executable files (UPX, FSG, etc.)
- Keep in mind this might cause challenges or inconveniences for users.
To report False Positives to SonicWall: How can I report false positives or Virus/Trojan/Malware samples to the Gateway AntiVirus team? | SonicWall
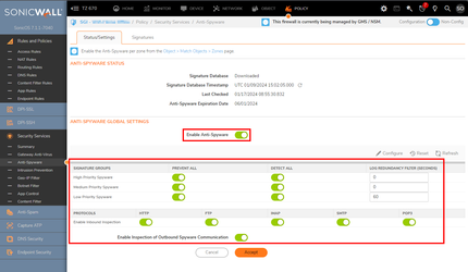
Anti-Spyware
Anti-Spyware best practices and recommended configuration
- Enable all options.
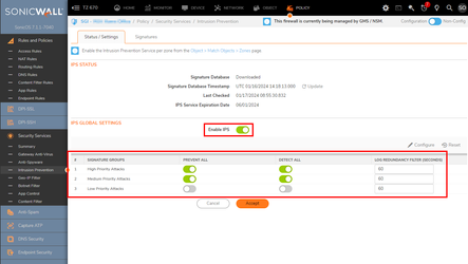
Intrusion Prevention Service (IPS)
IPS best practices and recommended configuration
- For High & Medium Priority Attacks
- Enable Prevent + Detect boxes.
- For Low Priority Attacks
- Don’t enable either..
- Ensure Log Redundancy Filter is set for 60 Seconds for each signature group.
Botnet Filter
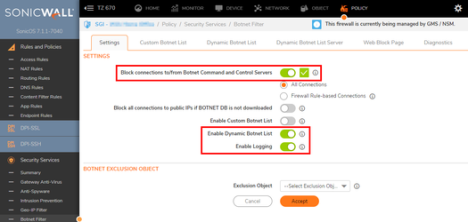
Botnet Filter best practices and recommended configuration
- DO NOT use the “Default GEO IP & Botnet Filter Exclusion Group”! Always create your own!
- Enable “Block connections to/from Botnet Command and Control Servers”
- Enable “Dynamic Botnet List”
- Enable “Logging”
App Control
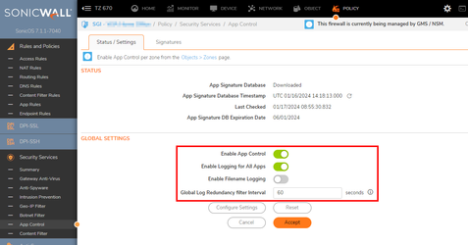
App Control best practices and recommended configuration
- Enable “App Control”
- Enable “Logging for all Apps”
- Ensure that the Global Log Redundancy Filter Interval is set to 60.
- Block & Disable Logging for MSS Recommended App Signatures below:
| Category | MSS Recommendation |
| APP-UPDATE | Nothing |
| BACKUP-APPS | Log |
| BROWSING-PRIVACY | Log |
| BUSINESS-APPS | Log |
| DATABASE-APPS | Log |
| DOWNLOAD-APPS | Log |
| EMAIL-APPS | Log |
| FILETYPE-DETECTION | Log |
| GAMING | Block & Log |
| IM | Log |
| INFRASTRUCTURE | Nothing |
| IoT-APPS | Log |
| MINERS | Block & Log |
| MISC-APPS | Log |
| MOBILE-APPS | Log |
| MULTIMEDIA | Log |
| P2P | Block & Log |
| P2P\ Non-SSL traffic over SSL port | Nothing |
| PROTOCOLS | Nothing |
| PROXY-ACCESS | Block & Log |
| PROXY-ACCESS\ Encrypted Key Exchange | Nothing |
| REMOTE-ACCESS | Log |
| REMOTE-DEBUG | Log |
| SCADA-APPS | Log |
| SOCIAL-NETWORKING | Block & Log |
| SRC-CTRL-APPS | Log |
| STOCK-TRADING | Log |
| VoIP-APPS | Log |
| VPN | Log |
| WEB-BROWSER | Nothing |
| WEB-CONFERENCING | Log |
| WEBMAIL | Log |
Content Filtering (CFS)
CFS best practices and recommended configuration
To view SonicWall’s rating for a URL: SonicWALL Content-Filter Website Rating Review
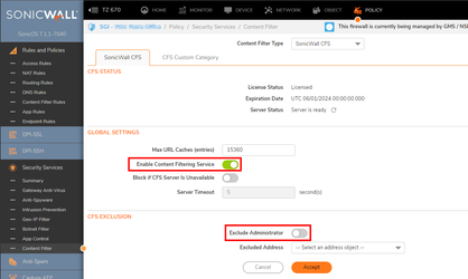
On the Content Filter page under the “Security Service” page:
Enable Content Filtering Service
Disable Exclude Administrator
Below are Best Practices/Recommendations when it comes to configuring your individual CFS policies on the Content Filter page under the “Profile Objects” page:
| Security Risk | Block All |
| Entertainment | Allow All |
| Keyloggers and Monitoring | Block | Arts/Entertainment | Allow | |
| Malware | Block | Multimedia | Allow | |
| Phishing and Other Frauds | Block | P2P | Allow | |
| Proxy Avoidance and Anonymizers | Block | Games | Block | |
| Spyware and Adware | Block | Music | Allow | |
| Bot Nets | Block | Lifestyle | Allow All | |
| SPAM URLs | Block | Travel | Allow | |
| Open HTTP Proxies | Block | Home and Garden | Allow | |
| Human Resource Protections | Block All | Religion | Allow | |
| Drugs/Illegal Drugs | Block | Hunting and Fishing | Allow | |
| Pornography | Block | Society and Lifestyle | Allow | |
| Sex Education | Block | Sports | Allow | |
| Intimate Apparel/Swimsuit | Block | Fashion and Beauty | Allow | |
| Gross | Block | Recreation and Hobbies | Allow | |
| Nudism | Block | Humor/Jokes | Allow | |
| Alcohol/Tobacco | Block | Business/Government/Services | Allow All | |
| Adult/Mature Content | Block | Real Estate | Allow | |
| Personals and Dating | Block | Computer and Internet Security | Allow | |
| Internet Watch Foundation CAIC | Block | Online Banking | Allow | |
| Questionable/Legal | Block All | Business and Economy | Allow | |
| Cult/Occult | Block | Information Technology/Computers | Allow | |
| Gambling | Block | Military | Allow | |
| Marijuana | Block | Online Brokerage and Trading | Allow | |
| Hacking | Block | Training and Tools | Allow | |
| Weapons | Block | Online Personal Storage | Allow | |
| Pay to Surf Sites | Block | Government | Allow | |
| Questionable | Block | Content Delivery Networks | Allow | |
| Hate and Racism | Block | Vehicles | Allow | |
| Violence | Block | Web Hosting | Allow | |
| Cheating | Block | Restaurants and Dining | Allow | |
| Illegal Skills/Questionable Skills | Block | General Information | Allow All | |
| Abortion/Advocacy Groups | Block | Legal | Allow | |
| Radicalization and Extremism | Block | Local Information | Allow | |
| Social Media/Internet Communication | Allow All | Job Search | Allow | |
| Social Networking | Allow | Translation | Allow | |
| Personal Sites and Blogs | Allow | Reference | Allow | |
| Online Greeting Cards | Allow | Political/Advocacy Groups | Allow | |
| Search Engines and Portals | Allow | Education | Allow | |
| Advertisement | Allow | Kid Friendly | Allow | |
| | Allow | News and Media | Allow | |
| Web Communications | Allow | Health | Allow | |
| Dynamic Content | Allow | Image and Video Search | Allow | |
| Chat/Instant Messaging (IM) | Allow | Cultural Institutions | Allow | |
| Usenet News Groups | Allow | Other | Allow | |
| Shopping | Allow All | Uncategorized | Allow All | |
| Internet Auctions | Allow | Not Rated | Allow | |
| Shopping | Allow | Dead Sites | Allow | |
| Freeware/Software Downloads | Allow | Parked Domains | Allow | |
|
|
| Private IP Addresses | Allow |
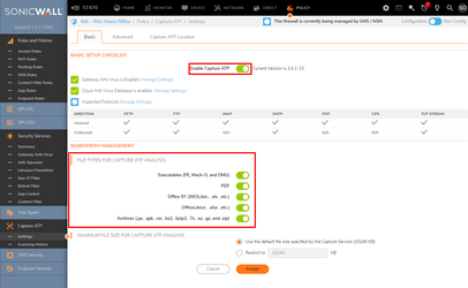
Capture ATP (If purchased):
CATP best practices and recommended configuration
Under the Basic tab:
Enable Capture ATP
Select all under FILE TYPES FOR CAPTURE ATP ANALYSIS
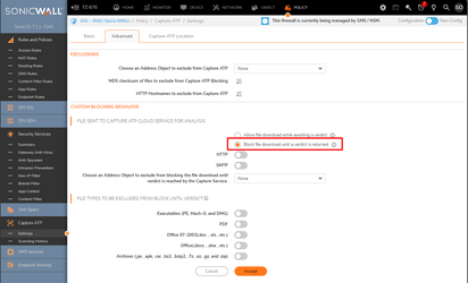
Under the Advanced tab:
Select “Block file download until a verdict is returned”
This may cause delays in download times for my users and may require users to retry the download.
DNS Security (If purchased):
Introducing the latest enhancement to SonicOS – centralized DNS management powered by DNS proxy, featuring advanced DNS security functionalities such as DNS Filtering, DNS Sinkhole service, and DNS Tunnel Detection. While bearing a resemblance to the Content Filtering Service (CFS), it's important to note that CFS relies on the completion of the full firewall inspection process before taking action. In contrast, DNS Security operates at the DNS layer, intercepting and halting malicious domains even before they reach the firewall, let alone undergo inspection.
A key distinction lies in the frequency of database updates – CFS databases are refreshed every 12-24 hours, whereas DNS updates occur every few minutes. This real-time update advantage positions DNS filtering as a proactive measure against potential risks. Acting as a critical shield, it intercepts users' DNS requests, cross-referencing them with a database of known malicious domains. This preemptive approach effectively blocks users from accessing suspicious websites, ensuring protection from potential harm.
Furthermore, DNS filtering delivers a positive impact on network performance. By preventing access to unnecessary or undesirable websites, it reduces bandwidth consumption and optimizes internet speeds. This proves particularly advantageous in corporate environments where inadvertent access to sites can compromise both network performance and security.
In conclusion, supported by robust SonicWall capabilities, DNS filtering emerges as a cornerstone in maintaining a secure and productive online environment. Its role in safeguarding against malicious websites, filtering inappropriate content, and enhancing network performance positions DNS filtering as a valuable asset for individuals and organizations alike.
DNS Filtering
Neustar is a public DNS Server which has intelligence of domain name categorization. By integrating Neustar DNS service with SonicWall firewall, we obtain domain categorization service along with DNS for SonicWall customers. SonicWall support profiles to take different actions on different categories, then the DNS Packet will process according to the action. Neustar support 19 pre-defined categories and SonicWall support 4 actions. For more information, see: About DNS Filtering
It is important to note that this feature requires you to point network client’s DNS server to the firewall. The firewall will act as the network’s DNS server in this case.
DNS Filtering best practices and recommended configuration:
Prerequisite
To use DNS Filtering, user has to do the following configurations:
Ensure DNS Filtering is licensed under Gateway Services in the license page
Add/Edit/Delete DNS policy manually in the Policy > Rules and Polices > DNS Rules. For more information on adding DNS policy, refer to the SonicOS Rules and Policies guide
Add/Edit/Delete DNS Profile in the Object > Profile Objects> DNS Filtering. For more information on adding DNS policy, refer to the SonicOS Objects guide
Set the DHCP DNS Server Lease Scopes interface as the interface IP of firewall in the Dynamic Range Configuration. For more information on adding Dynamic, refer to the SonicOS system guide
Enable Enforce DNS Proxy For All DNS Requests at DNS Proxy settings in the Network > DNS > DNS Proxy
To configure Global settings
Navigate to POLICY | DNS Security > Settings.
Hover over to the DNS Filtering tab.
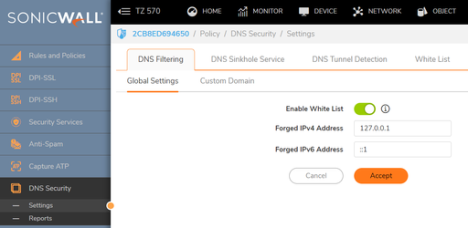
Click the Global Settings tab. Enable the option Enable White List.
White List can be used for both DNS Sinkhole Service and DNS Filtering.
Configure both Forged IPv4 Address and Forged IPv6 Address.
Click Accept.
To configure Custom Domain
Navigate to POLICY | DNS Security > Settings.
Hover over to the DNS Filtering tab.
Click the Custom Domain tab.
Under Category Information, you can find the different type of categories and the categories explanation.
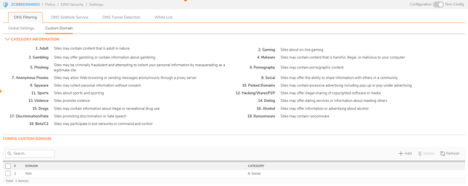
For each domain name you want to add as a custom domain name under the Config Custom Domain section:
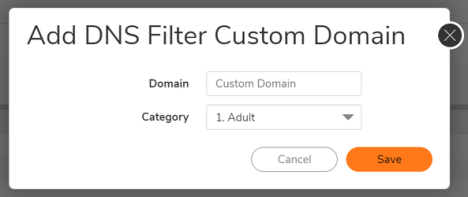
Click +Add. The Add DNS filter Custom Domain dialog displays.
Enter the custom domain name in the Domain Name field.
Select the category type from the drop-down in the Category field.
Click Save.
DNS Sinkhole Service
A DNS sinkhole also known as a sinkhole server, Internet sinkhole, or Blackhole DNS — is a DNS server that gives out false information to prevent the use of the domain names it represents. DNS sinkholes are effective at detecting and blocking malicious traffic, and used to combat bots and other unwanted traffic.
SonicOS provides the ability to configure a sinkhole with black- and whitelists.
DNS Sinkhole Service best practices and recommended configuration:
To configure DNS Sinkhole settings
Navigate to POLICY | DNS Security > Settings.
Hover over to the DNS Sinkhole Service tab.
Select Enable DNS Sinkhole Service under the Settings tab. This option is not selected by default.
Click the Global Settings tab. Enable the option Enable White List.
From the Action drop-down menu, select what the service should do:
Dropping with Logs
Dropping with Negative DNS reply to Source
Dropping with DNS reply of Forged IP
Ensure the IPv4 address and IPv6 address, Current Detection, and Malicious Domain in the fields.
Click Accept.
To configure Custom Malicious Domain Name List
Navigate to POLICY | DNS Security > Settings.
Hover over to the DNS Sinkhole Service tab.
Click the Custom Malicious Domain Name tab.
For each domain name you want to add as a malicious domain name:
Click +Add. The Add One Domain Name dialog displays.
Enter the malicious domain name in the Domain Name field.
Click Save.
Deleting Entries in the Custom Malicious Domain Name List
Navigate to POLICY | DNS Security > Settings.
Hover over to the DNS Sinkhole Service tab.
Click the Custom Malicious Domain Name tab.
Select an entry to delete or select the top checkbox next to the Domain Name column to select all of the items in the list.
Click Delete.
DNS Tunnel Detection
DNS tunneling is a method of bypassing security controls and exfiltrating data from a targeted organization. A DNS tunnel can be used as a full remote-control channel for a compromised internal host. Capabilities include Operating System (OS) commands, file transfers, or even a full IP tunnel.
SonicOS provides the ability to detect DNS tunneling attacks, displays suspicious clients, and allows you to create white lists for DNS tunnel detection.
When DNS tunneling detection is enabled, SonicOS logs whenever suspicious DNS packets are dropped.
DNS Tunneling settings can be made at the group or unit level.
DNS Tunnel Detection best practices and recommended configuration:
To configure DNS tunnel detection
Navigate to POLICY | DNS Security > Settings.
Click the DNS Tunnel Detection tab.
Under Settings, select Enable DNS Tunnel Detection to enable DNS tunnel detection.
To block all the DNS traffic from the detected clients, select Block All the Clients DNS Traffic.
Click Accept.
Detected Suspicious Client Information
SonicOS displays information about all hosts that have established a DNS tunnel in the Detected Suspicious Clients Info table.
Navigate to POLICY | DNS Security > Settings.
Hover over to the DNS Tunnel Detection tab.
Click on the Detected Suspicious Clients Info tab.
This table is populated only if DNS tunnel detection is enabled. Hosts are dropped only if blocking clients DNS traffic is enabled.
| IP Address | IP address of the suspicious client |
| MAC Address | MAC address of the suspicious client |
| Detection Method | DNS type used to detect suspicious clients:
|
| Interface | Interface on which the host establishing the DNS tunnel was detected. |
| Block | Indicates whether the host was blocked. |
Creating White list for DNS Tunnel Detection
You can create white lists for IP address you consider safe. If a detected DNS tunnel IP address matches an address in the white list, DNS tunnel detection is bypassed.
Navigate to POLICY | DNS Security > Settings.
Hover over to the DNS Tunnel Detection tab.
Click on the White List for DNS Tunnel Detection tab.
For each IP address you want to add to the white list:
Click +Add. The Add One White Entry dialog displays.
In the IP Address field, enter the IP address of the domain to be added to the whitelist.
Click Save.
Deleting White List Entries for DNS Tunnel Detection
Navigate to POLICY | DNS Security > Settings.
Hover over to the DNS Tunnel Detection tab.
Click on the White List for DNS Tunnel Detection tab.
Select an entry to delete or select the top checkbox next to the IP Address column to select all of the items.
Click Delete.
White List
DNS Security White List best practices and recommended configuration:
You can create white lists for IP address you consider safe.
The default URLs on White List is deleted by design. Now it displays No data as default.
To create a white list
Navigate to POLICY | DNS Security > Settings.
Click the White List tab.
For each domain name you want to add to the white list:
Click +Add. The Domain Name dialog displays.
In the Domain Name field, enter the white list domain name.
Click Save.
To delete all white list
Navigate to POLICY | DNS Security > Settings.
Click the White List tab.
Select an entry to delete or select the top checkbox next to the IP Address column to select all of the items.
Click Delete.
Geo IP
Geo-IP best practices and recommended configuration
- DO NOT use the “Default GEO IP & Botnet Filter Exclusion Group”! Always create your own!
- If you need to exclude local hosts (private IPs behind the firewall) from Geo-IP, see the following SonicWall KB: How can I exclude hosts behind SonicWall from Geo-IP Filter using firewall access rules? | SonicWall
- Enable “Block connections to/from countries selected in the Countries tab”
- Enable “Logging”
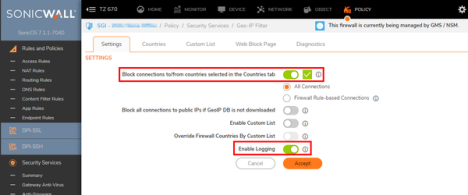
- In the Countries tab:
- Enable “Block all Unknown countries”
- Block MSS Recommended Countries below:
| Country | MSS Recommendation |
| Afghanistan | Block |
| Aland Islands | Block |
| Albania | Block |
| Algeria | Block |
| American Samoa | Block |
| Andorra | Block |
| Angola | Block |
| Anguilla | Block |
| Anonymous Proxy/Private IP | Block |
| Antarctica | Block |
| Antigua and Barbuda | Block |
| Argentina | Block |
| Armenia | Block |
| Aruba | Block |
| Asia/Pacific Region | Block |
| Australia | Allow |
| Austria | Allow |
| Azerbaijan | Block |
| Bahamas | Block |
| Bahrain | Block |
| Bangladesh | Block |
| Barbados | Block |
| Belarus | Block |
| Belgium | Block |
| Belize | Block |
| Benin | Block |
| Bermuda | Block |
| Bhutan | Block |
| Bolivia | Block |
| Bonaire, Saint Eustatius and Sa | Block |
| Bosnia and Herzegovina | Block |
| Botswana | Block |
| Bouvet Island | Block |
| Brazil | Block |
| British Indian Ocean Territory | Block |
| Brunei Darussalam | Block |
| Bulgaria | Block |
| Burkina Faso | Block |
| Burundi | Block |
| Cambodia | Block |
| Cameroon | Block |
| Canada | Allow |
| Cape Verde | Block |
| Cayman Islands | Block |
| Central African Republic | Block |
| Chad | Block |
| Chile | Block |
| China | Block |
| Christmas Island | Block |
| Cocos (Keeling) Islands | Block |
| Colombia | Block |
| Comoros | Block |
| Congo | Block |
| Congo, The Democratic Republic | Block |
| Cook Islands | Block |
| Costa Rica | Block |
| Cote d'Ivoire | Block |
| Croatia | Block |
| Cuba | Block |
| Curacao | Block |
| Cyprus | Block |
| Czech Republic | Block |
| Denmark | Block |
| Djibouti | Block |
| Dominica | Block |
| Dominican Republic | Block |
| Ecuador | Block |
| Egypt | Block |
| El Salvador | Block |
| Equatorial Guinea | Block |
| Eritrea | Block |
| Estonia | Block |
| Ethiopia | Block |
| Europe | Allow |
| Falkland Islands (Malvinas) | Block |
| Faroe Islands | Block |
| Fiji | Block |
| Finland | Block |
| France | Allow |
| French Guiana | Block |
| French Polynesia | Block |
| French Southern Territories | Block |
| Gabon | Block |
| Gambia | Block |
| Georgia | Block |
| Germany | Allow |
| Ghana | Block |
| Gibraltar | Block |
| Greece | Block |
| Greenland | Block |
| Grenada | Block |
| Guadeloupe | Block |
| Guam | Block |
| Guatemala | Block |
| Guernsey | Block |
| Guinea | Block |
| Guinea-Bissau | Block |
| Guyana | Block |
| Haiti | Block |
| Heard Island and McDonald Islan | Block |
| Holy See (Vatican City State) | Block |
| Honduras | Block |
| Hong Kong | Block |
| Hungary | Block |
| Iceland | Block |
| India | Block |
| Indonesia | Block |
| Iran, Islamic Republic of | Block |
| Iraq | Block |
| Ireland | Allow |
| Isle of Man | Block |
| Israel | Block |
| Italy | Block |
| Jamaica | Block |
| Japan | Block |
| Jersey | Block |
| Jordan | Block |
| Kazakhstan | Block |
| Kenya | Block |
| Kiribati | Block |
| Korea, Democratic People's Repu | Block |
| Korea, Republic of | Block |
| Kuwait | Block |
| Kyrgyzstan | Block |
| Lao People's Democratic Republi | Block |
| Latvia | Block |
| Lebanon | Block |
| Lesotho | Block |
| Liberia | Block |
| Libyan Arab Jamahiriya | Block |
| Liechtenstein | Block |
| Lithuania | Block |
| Luxembourg | Block |
| Macao | Block |
| Macedonia | Block |
| Madagascar | Block |
| Malawi | Block |
| Malaysia | Block |
| Maldives | Block |
| Mali | Block |
| Malta | Block |
| Marshall Islands | Block |
| Martinique | Block |
| Mauritania | Block |
| Mauritius | Block |
| Mayotte | Block |
| Mexico | Block |
| Micronesia, Federated States of | Block |
| Moldova, Republic of | Block |
| Monaco | Block |
| Mongolia | Block |
| Montenegro | Block |
| Montserrat | Block |
| Morocco | Block |
| Mozambique | Block |
| Myanmar | Block |
| Namibia | Block |
| Nauru | Block |
| Nepal | Block |
| Netherlands | Block |
| Netherlands Antilles | Block |
| New Caledonia | Block |
| New Zealand | Block |
| Nicaragua | Block |
| Niger | Block |
| Nigeria | Block |
| Niue | Block |
| Norfolk Island | Block |
| Northern Mariana Islands | Block |
| Norway | Block |
| Oman | Block |
| Other Country | Block |
| Pakistan | Block |
| Palau | Block |
| Palestinian Territory | Block |
| Panama | Block |
| Papua New Guinea | Block |
| Paraguay | Block |
| Peru | Block |
| Philippines | Block |
| Pitcairn | Block |
| Poland | Block |
| Portugal | Block |
| Puerto Rico | Block |
| Qatar | Block |
| Reunion | Block |
| Romania | Block |
| Russian Federation | Block |
| Rwanda | Block |
| Saint Helena | Block |
| Saint Kitts and Nevis | Block |
| Saint Lucia | Block |
| Saint Martin | Block |
| Saint Pierre and Miquelon | Block |
| Saint Vincent and the Grenadine | Block |
| Samoa | Block |
| San Marino | Block |
| Sao Tome and Principe | Block |
| Satellite Provider | Block |
| Saudi Arabia | Block |
| Senegal | Block |
| Serbia | Block |
| Seychelles | Block |
| Sierra Leone | Block |
| Singapore | Block |
| Sint Maarten | Block |
| Slovakia | Block |
| Slovenia | Block |
| Solomon Islands | Block |
| Somalia | Block |
| South Africa | Block |
| South Georgia and the South San | Block |
| Spain | Block |
| Sri Lanka | Block |
| Sudan | Block |
| Suriname | Block |
| Svalbard and Jan Mayen | Block |
| Swaziland | Block |
| Sweden | Allow |
| Switzerland | Allow |
| Syrian Arab Republic | Block |
| Taiwan | Block |
| Tajikistan | Block |
| Tanzania, United Republic of | Block |
| Thailand | Block |
| Timor-Leste | Block |
| Togo | Block |
| Tokelau | Block |
| Tonga | Block |
| Trinidad and Tobago | Block |
| Tunisia | Block |
| Turkey | Block |
| Turkmenistan | Block |
| Turks and Caicos Islands | Block |
| Tuvalu | Block |
| Uganda | Block |
| Ukraine | Block |
| United Arab Emirates | Block |
| United Kingdom | Allow |
| United States | Allow |
| United States Minor Outlying Is | Allow |
| Uruguay | Block |
| Uzbekistan | Block |
| Vanuatu | Block |
| Venezuela | Block |
| Vietnam | Block |
| Virgin Islands, British | Block |
| Virgin Islands, U.S. | Block |
| Wallis and Futuna | Block |
| Western Sahara | Block |
| Yemen | Block |
| Zambia | Block |
| Zimbabwe | Block |