Integration of LDAP Groups or Local Groups and Content Filtering without Single Sign On
Description
To watch a video tutorial on this topic, click here.
This article explains about how to integrate Premium Content Filtering Service with LDAP, while not using the Single-Sign On service. In order for the SonicWall to know what Content Filtering Policies to apply for a session it either needs to have the policy set by IP address or have a user authenticate against it. This can be a Local User or an LDAP User, for this article we'll be examining LDAP Users.
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Enabling HTTPS Login for LAN Interface
 TIP: This step can be used for any Zone, not just the LAN. Make sure to Enable HTTPS Login for every Zone that you need Users to Authenticate from!
TIP: This step can be used for any Zone, not just the LAN. Make sure to Enable HTTPS Login for every Zone that you need Users to Authenticate from!
 CAUTION: It is possible to follow this setup using HTTP but this is highly insecure, not recommended, and thus not explicitly detailed in this article. 
CAUTION: It is possible to follow this setup using HTTP but this is highly insecure, not recommended, and thus not explicitly detailed in this article. 
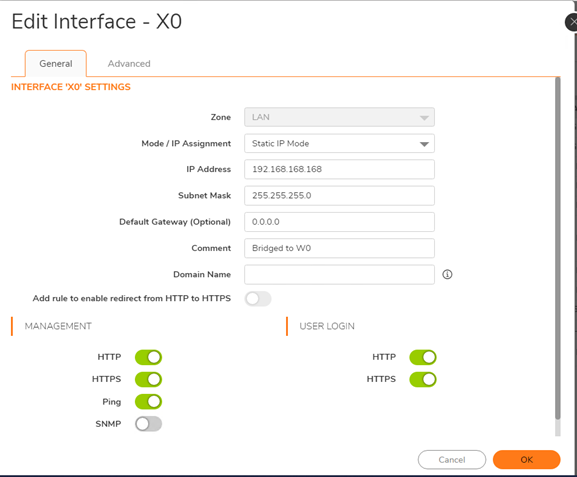
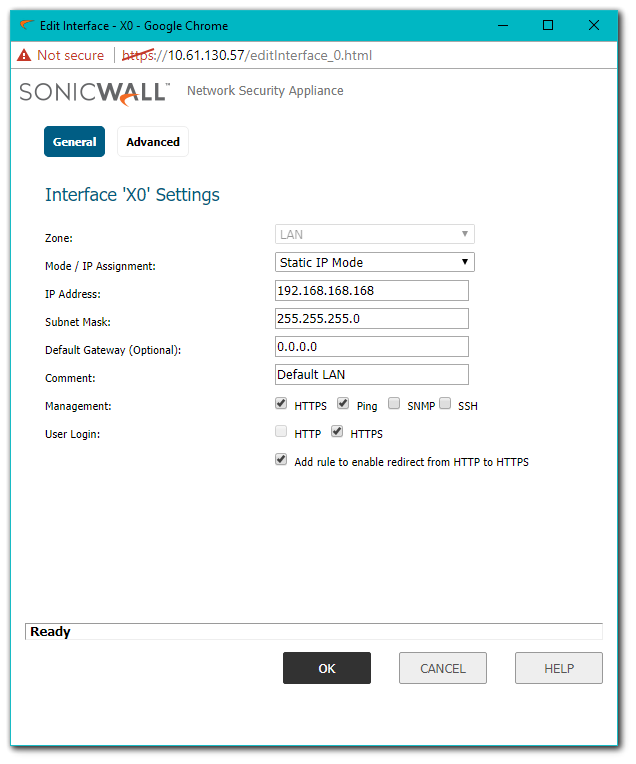
- Log in to SonicWall and navigate to Network | Interfaces | X0 then click configure.
- Select HTTPS under User Login.
Configuring LDAP on SonicWall (If You're Using Local Groups Only Skip This Step)
· For Details on this process please follow: Integrating LDAP/Active Directory with SonicWall UTM Appliance.
Configuring the Local/LDAP Groups
- Navigate to Device |Local users & groups | Local Groups. From here you can click Add and choose either Import Groups from LDAP or create Local Groups which reside on the SonicWall.
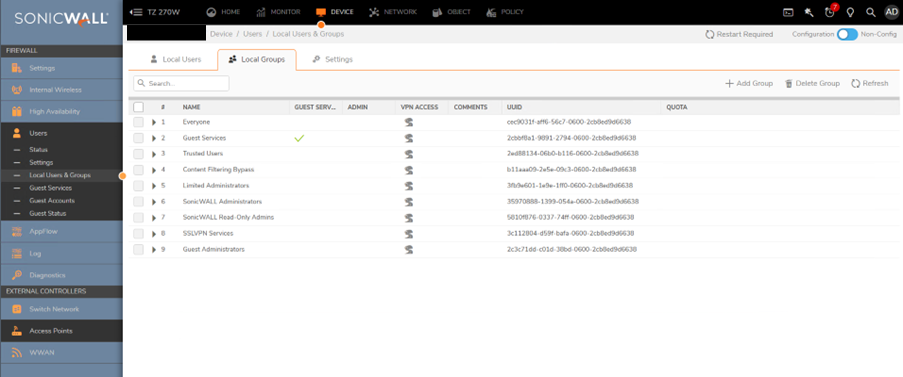
Creating Local Groups
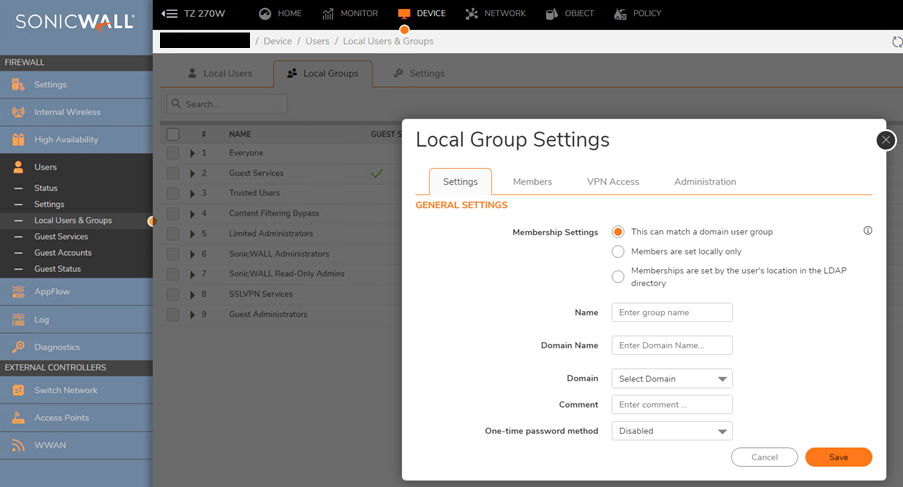
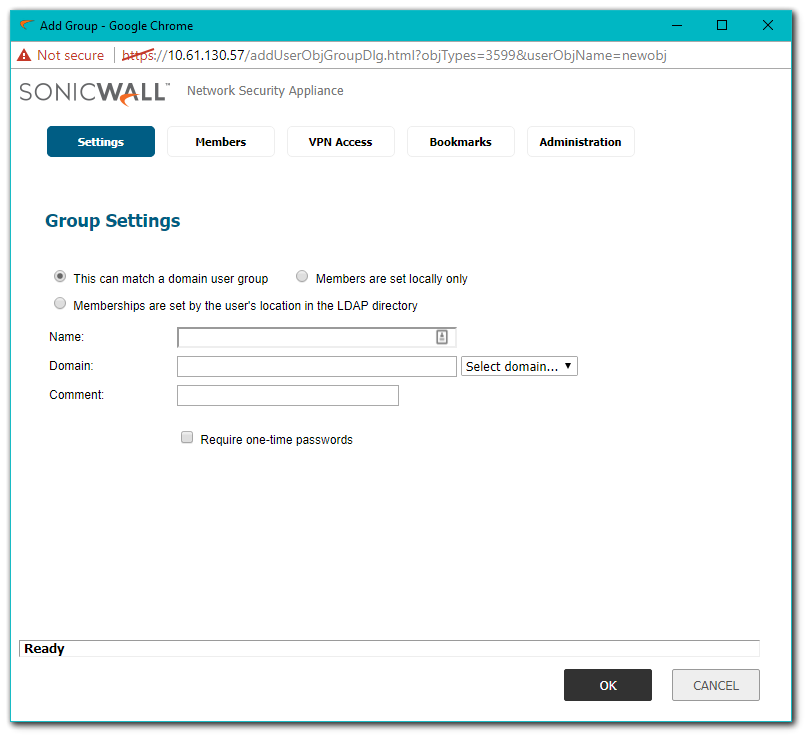
- Click Add Group and include a Name on the Local groups Tab.
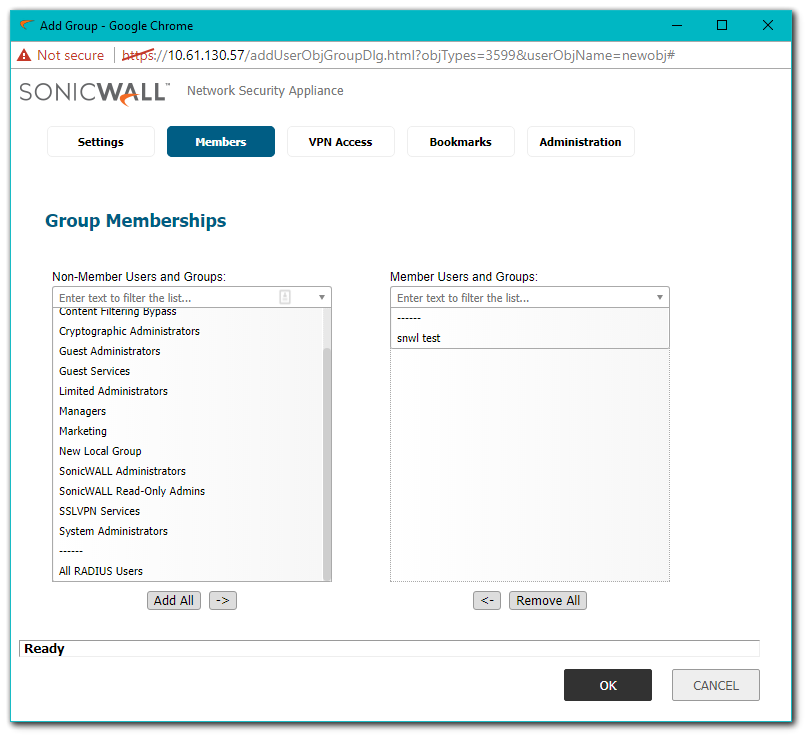
- On the Members tab move Users or Groups from the left to the right.
- Click OK.
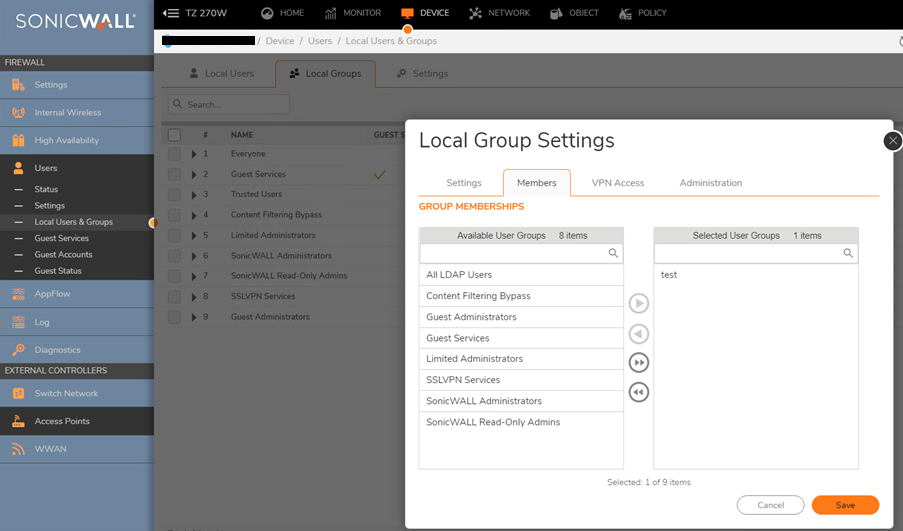
Importing LDAP Group
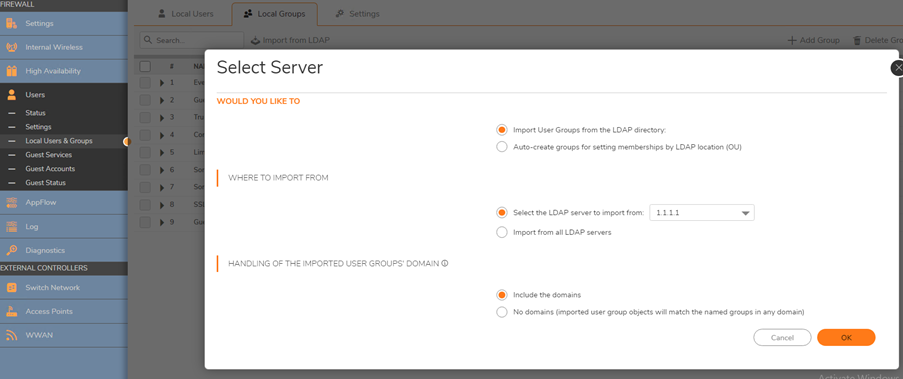
- Click Import User Groups and choose Import User Groups from the LDAP directory. Choose an LDAP Server to Import from under Where to import from.
- Click OK.
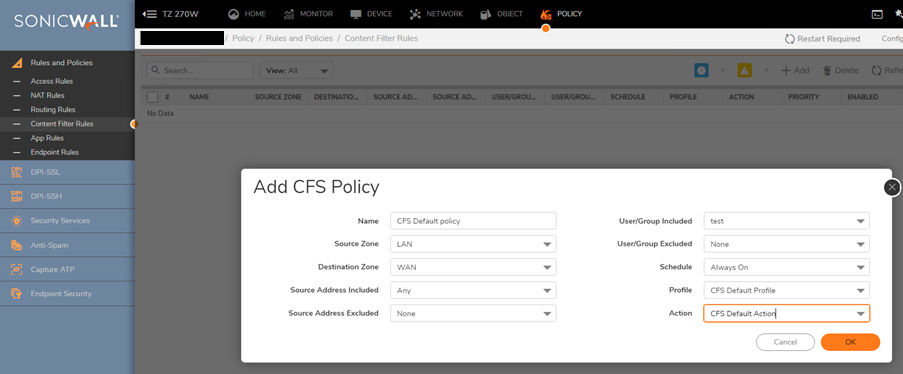
Configuring Content Filter and Policies
- Navigate to Policy | Rules and Policies | Content Filter Rules, then click Configure for the policy you'd like to edit.
- Select the User Group that this policy should apply to. This can either be a Local Group, or an LDAP Group.
 CAUTION: While it is possible to nest Groups this is not recommended. It is better to make multiple Policies for each Group, even if those policies are identical to one another.
CAUTION: While it is possible to nest Groups this is not recommended. It is better to make multiple Policies for each Group, even if those policies are identical to one another.
Configuring Access Rule for the User Group
- Now that we have our Groups either Imported or created and also applied to our CFS Policies we need to create a way for users to authenticate against the SonicWall. Since we're not using Single Sign On we will have to force users to signing to the SonicWall directly.
- While Users can navigate to the SonicWalls IP address manually and login this is a cumbersome solution. Instead it's possible to create an access rule which redirects Users to the SonicWall and forces them to Authenticate.
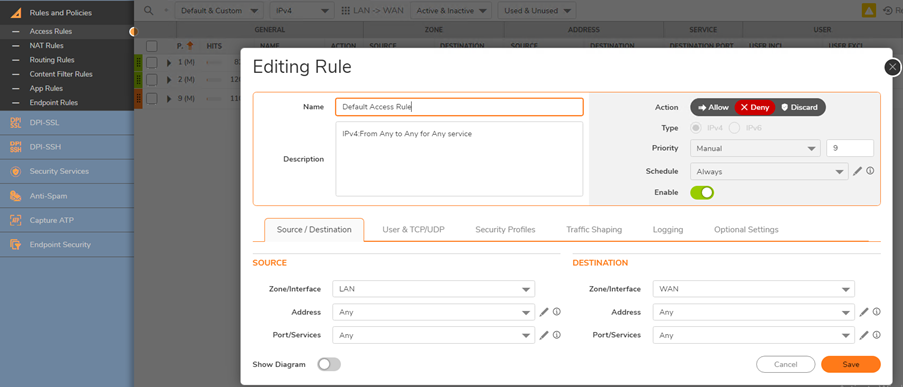
- First, we need to create an Access Rule to allow DNS
- Navigate to Policy | Rules and Policies | Access Rules and select Add. In the From and To fields select the Zone that traffic originates from and WAN, respectively.
- Fill in the rest of the Access Rule as shown below.
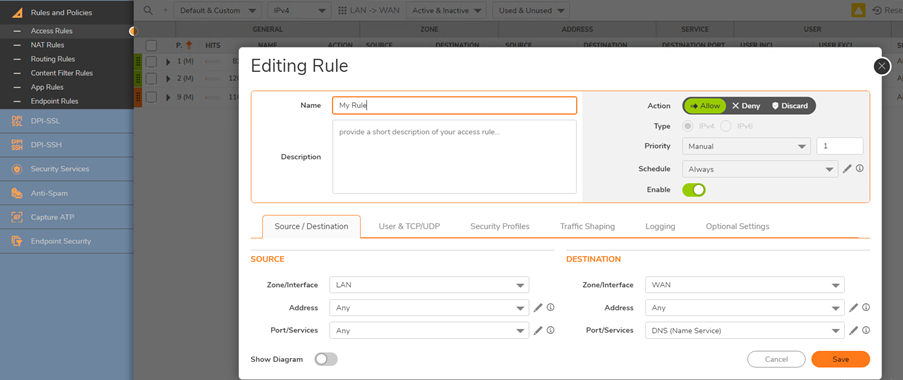
 CAUTION: Caution text here Ensure that this access rule is the #1 Priority under the Zone to Zone page, if other more permissive access rules are a higher priority then this configuration will not work.
CAUTION: Caution text here Ensure that this access rule is the #1 Priority under the Zone to Zone page, if other more permissive access rules are a higher priority then this configuration will not work.
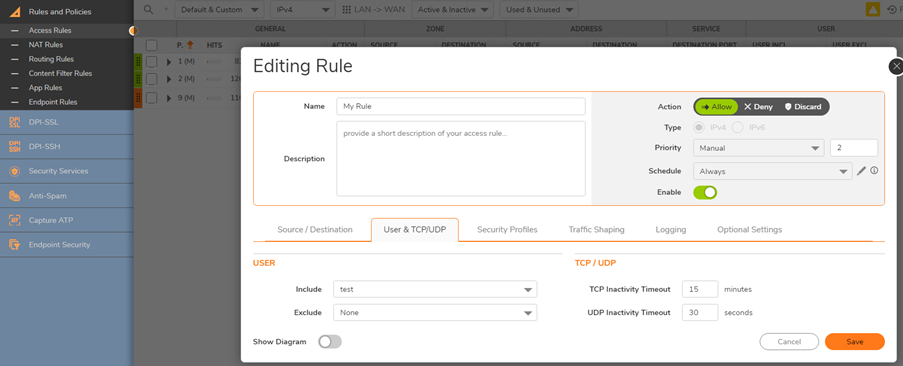
- Click Add again and set the From and To Zones to be the same as they were in the previous Access Rule.
- Fill in the rest of the Access Rule as shown below (Substitute your own Group for the one shown).
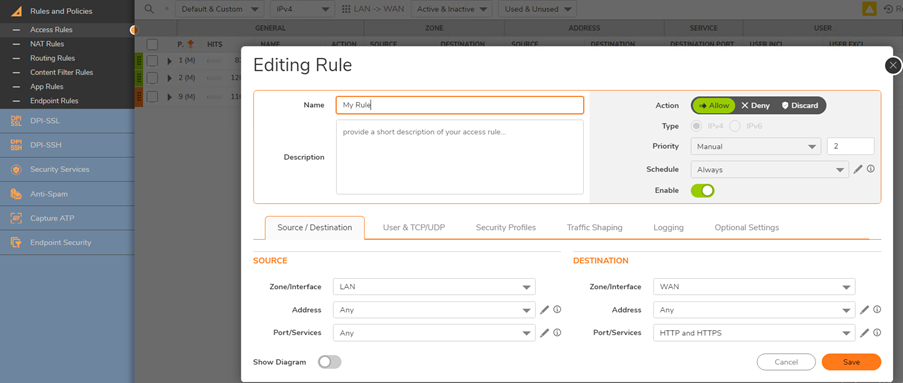
 TIP: It's possible to create a Service Group and combine HTTP, HTTPS, and any other Services you'd like and only use one Access Rule. This is a recommended Best Practice.
TIP: It's possible to create a Service Group and combine HTTP, HTTPS, and any other Services you'd like and only use one Access Rule. This is a recommended Best Practice.
 CAUTION: Ensure that this access rule is the #2 Priority under the Zone to Zone page.
CAUTION: Ensure that this access rule is the #2 Priority under the Zone to Zone page.
How to Test
From a Host on one of the Zones where you have setup both Content Filtering and the required Access Rules try to access any website. The SonicWall should redirect the request and request the User to login.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Enabling HTTPS Login for LAN Interface
 TIP: This step can be used for any Zone, not just the LAN. Make sure to Enable HTTPS Login for every Zone that you need Users to Authenticate from!
TIP: This step can be used for any Zone, not just the LAN. Make sure to Enable HTTPS Login for every Zone that you need Users to Authenticate from!
 CAUTION: It is possible to follow this setup using HTTP but this is highly insecure, not recommended, and thus not explicitly detailed in this article.
CAUTION: It is possible to follow this setup using HTTP but this is highly insecure, not recommended, and thus not explicitly detailed in this article.
- Log into the SonicWall and navigate to Manage | Network | Interfaces | LAN then click Configure button. Select HTTPS under User Login.
Configuring LDAP on SonicWall (If You're Using Local Groups Only Skip This Step)
- For Details on this process please follow: Integrating LDAP/Active Directory with SonicWall UTM Appliance.
Configuring the Local/LDAP Groups
- [For Local Groups] Navigate to Manage | Users | Local Groups. From here you can click Add and choose either Import Groups from LDAP or create Local Groups which reside on the SonicWall.
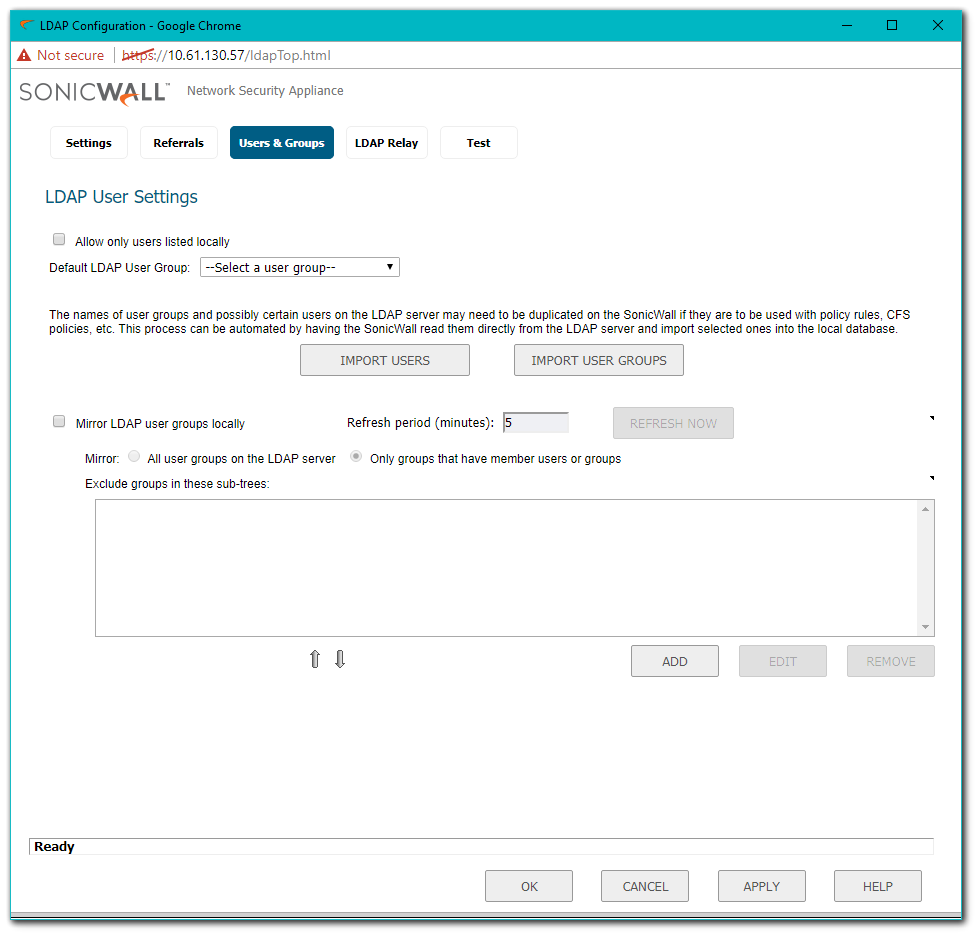
- [For LDAP Groups] Navigate to Manage | Users | Settings | Configure LDAP | Users & Groups and select Import User Groups.
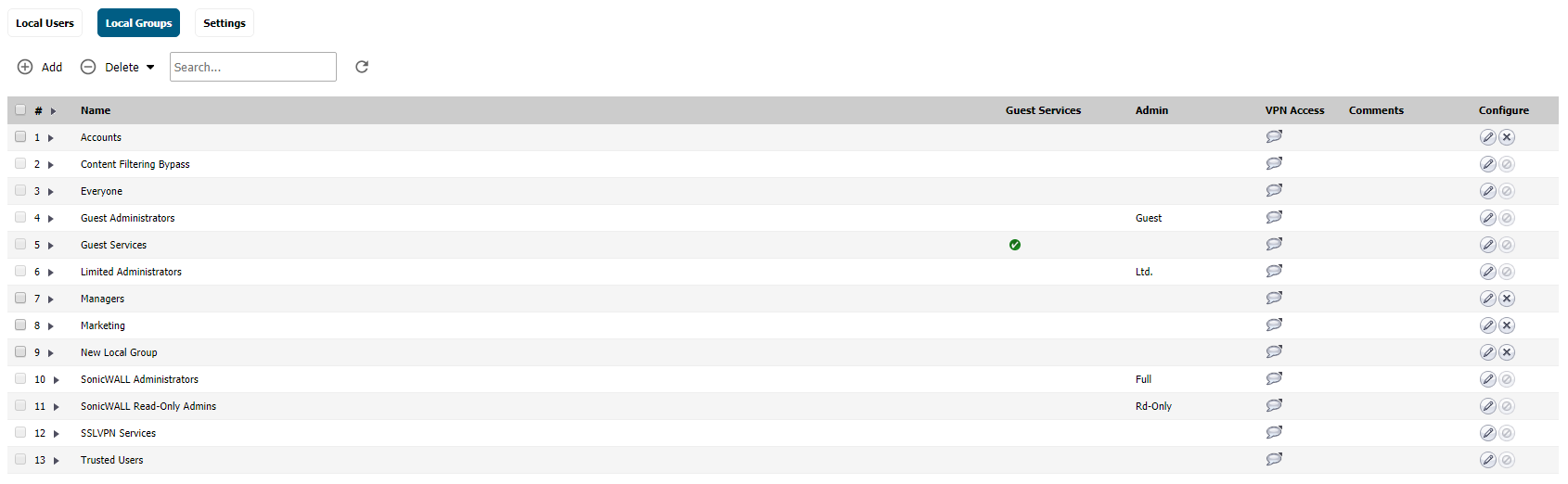
Creating Local Groups
- Click Add and include a Name on the Settings Tab.
- On the Members tab move Users or Groups from the left to the right.
- Click OK.
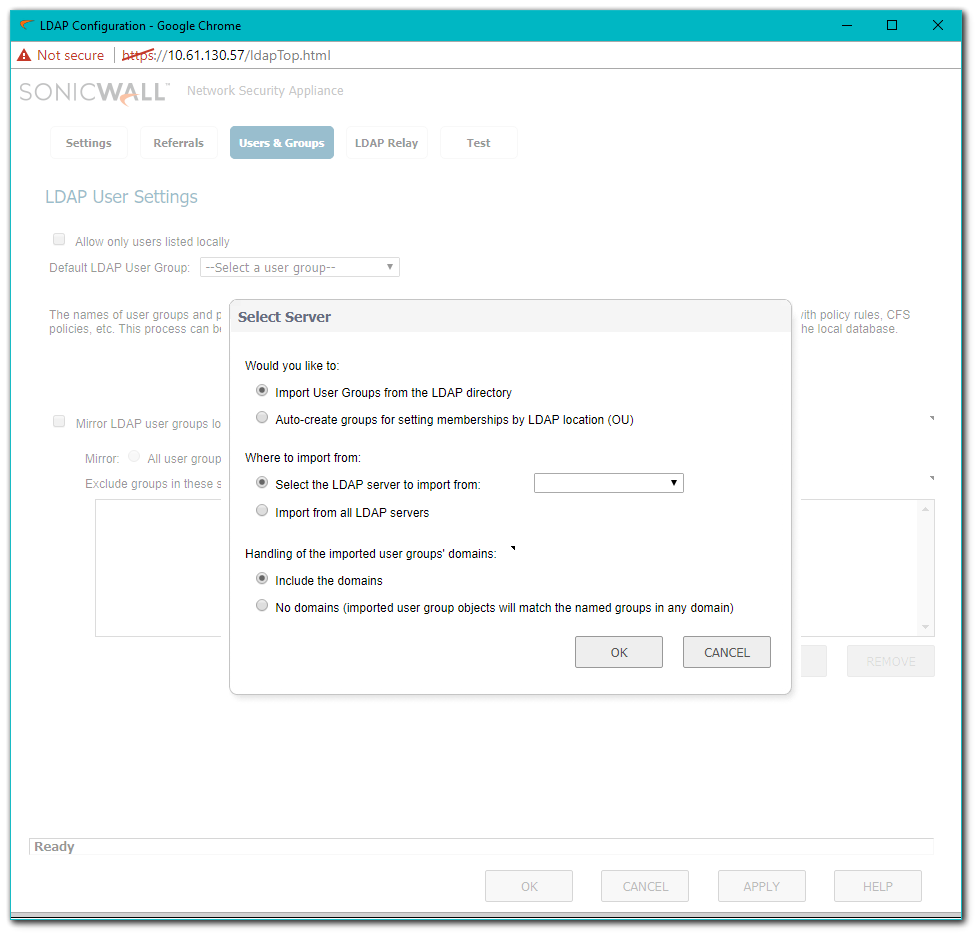
Importing LDAP Groups
- Click Import User Groups and choose Import User Groups from the LDAP directory. Choose an LDAP Server to Import from under Where to import from.
- Click OK.
Configuring Content Filter and Policies
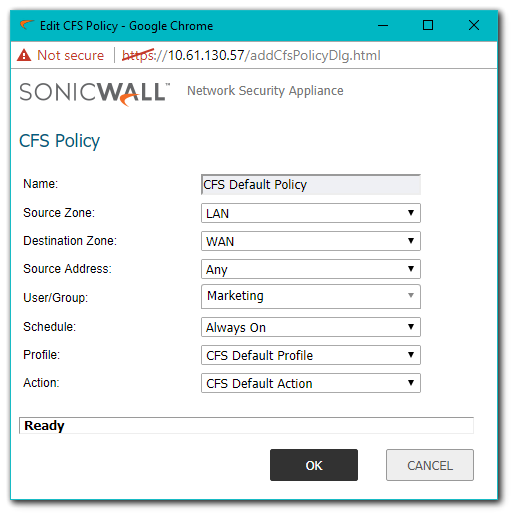
- Navigate to Manage | Security Services | Content Filter, then click Configure for the policy you'd like to edit.
- Select the User Group that this policy should apply to. This can either be a Local Group, or an LDAP Group.
 CAUTION: While it is possible to nest Groups this is not recommended. It is better to make multiple Policies for each Group, even if those policies are identical to one another.
CAUTION: While it is possible to nest Groups this is not recommended. It is better to make multiple Policies for each Group, even if those policies are identical to one another.
Configuring Access Rule for the User Group
Now that we have our Groups either Imported or created and also applied to our CFS Policies we need to create a way for users to authenticate against the SonicWall. Since we're not using Single Sign On we will have to force users to signing to the SonicWall directly.
While Users can navigate to the SonicWalls IP address manually and login this is a cumbersome solution. Instead it's possible to create an access rule which redirects Users to the SonicWall and forces them to Authenticate.
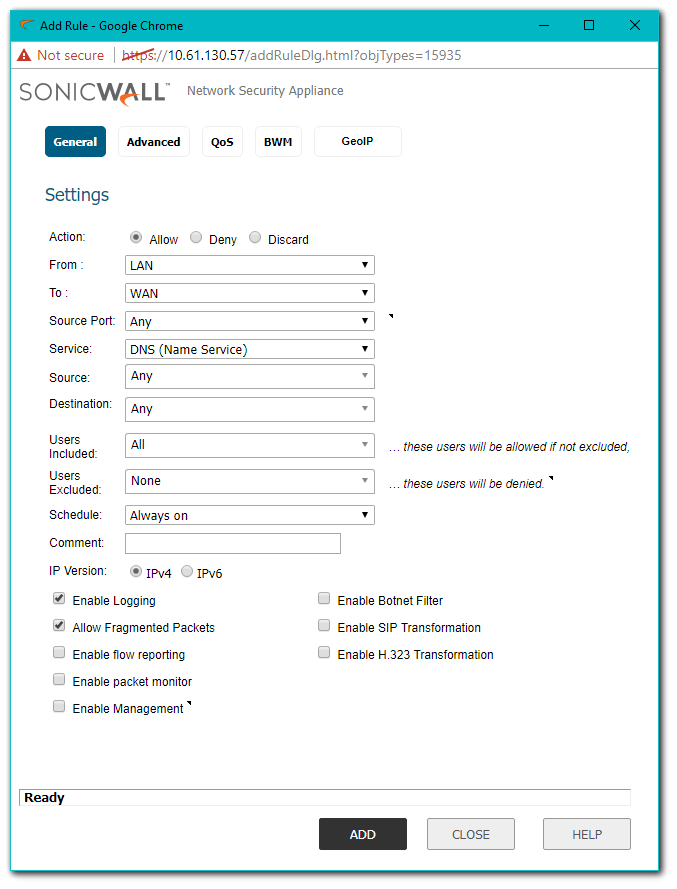
First we need to create an Access Rule to allow DNS:
- Navigate to Manage | Rules | Access Rules and select Add. In the From and To fields select the Zone that traffic originates from and WAN, respectively.
- Fill in the rest of the Access Rule as shown below.
 CAUTION: Ensure that this access rule is the #1 Priority under the Zone to Zone page, if other more permissive access rules are a higher priority then this configuration will not work.
CAUTION: Ensure that this access rule is the #1 Priority under the Zone to Zone page, if other more permissive access rules are a higher priority then this configuration will not work.
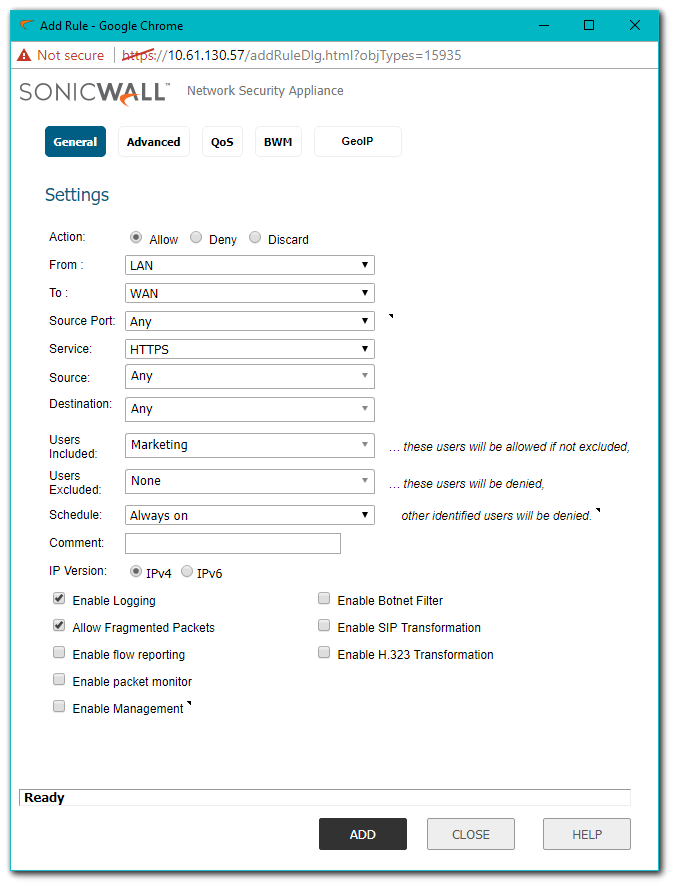
- Click Add again and set the From and To Zones to be the same as they were in the previous Access Rule.
- Fill in the rest of the Access Rule as shown below (Substitute your own Group for the one shown).
 TIP: It's possible to create a Service Group and combine HTTP, HTTPS, and any other Services you'd like and only use one Access Rule. This is a recommended Best Practice.
TIP: It's possible to create a Service Group and combine HTTP, HTTPS, and any other Services you'd like and only use one Access Rule. This is a recommended Best Practice. CAUTION: Ensure that this access rule is the #2 Priority under the Zone to Zone page.
CAUTION: Ensure that this access rule is the #2 Priority under the Zone to Zone page.
How to Test
From a Host on one of the Zones where you have setup both Content Filtering and the required Access Rules try to access any website. The SonicWall should redirect the request and request the User to login.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
Enabling HTTPS Login for LAN Interface
 TIP: This step can be used for any Zone, not just the LAN. Make sure to Enable HTTPS Login for every Zone that you need Users to Authenticate from!
TIP: This step can be used for any Zone, not just the LAN. Make sure to Enable HTTPS Login for every Zone that you need Users to Authenticate from!
 CAUTION: It is possible to follow this setup using HTTP but this is highly insecure, not recommended, and thus not explicitly detailed in this article.
CAUTION: It is possible to follow this setup using HTTP but this is highly insecure, not recommended, and thus not explicitly detailed in this article.
- Log into the SonicWall and navigate to Network | Interfaces | LAN then click the Configure button. Select HTTPS under User Login.
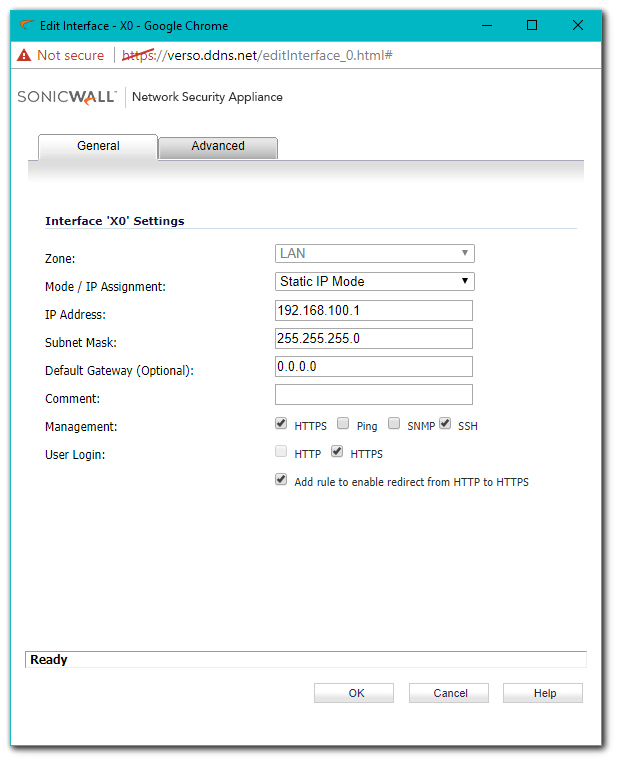
Configuring LDAP on SonicWall (If You're Using Local Groups Only Skip This Step)
- For details on this process please follow: Integrating LDAP/Active Directory with SonicWall UTM Appliance.
Configuring the Local/LDAP Groups
- Navigate to Users | Local Groups. From here you can either Import Groups from LDAP or create Local Groups which reside on the SonicWall.
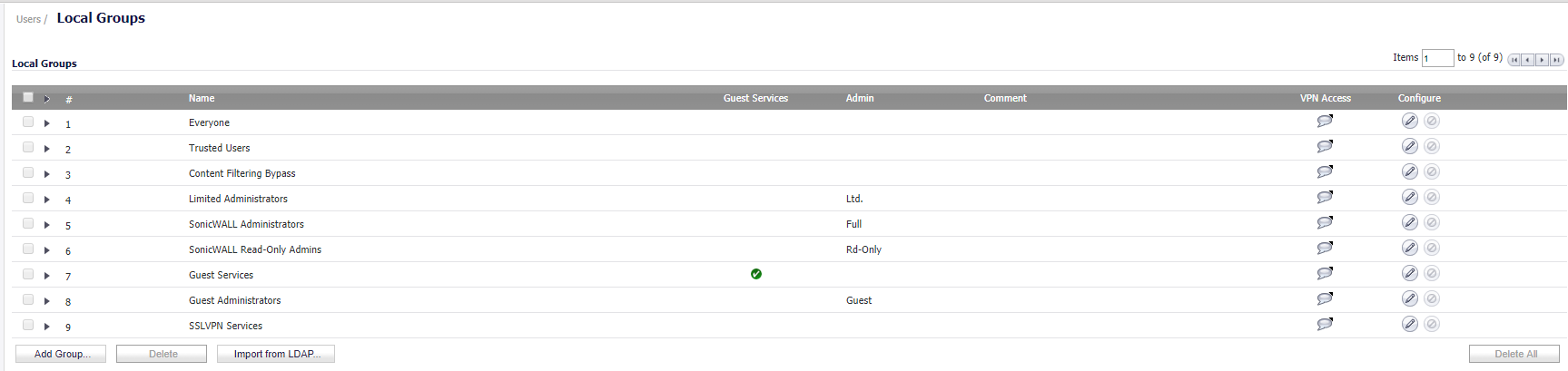
Creating Local Groups
- Click Add Group and include a Name on the Settings tab.
- On the Members Tab move Users or Groups from the left to the right.
- Click OK.
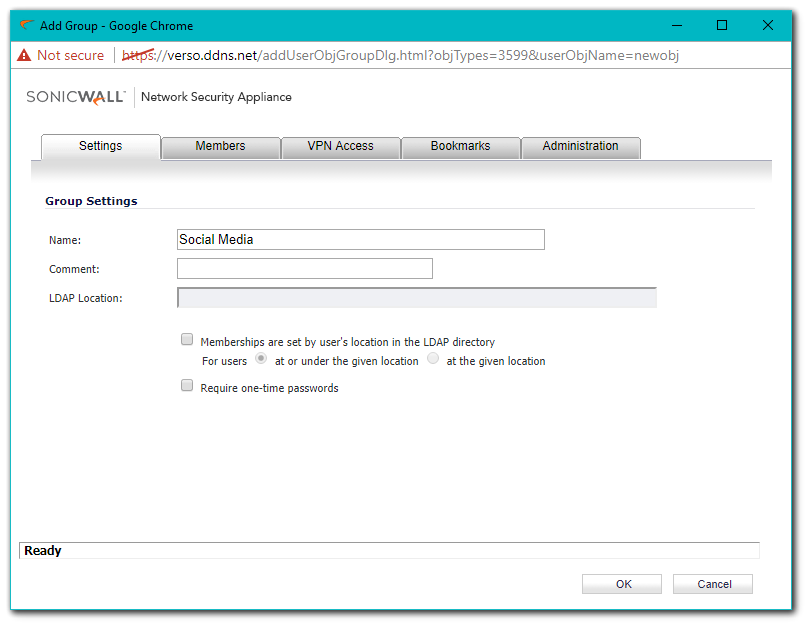
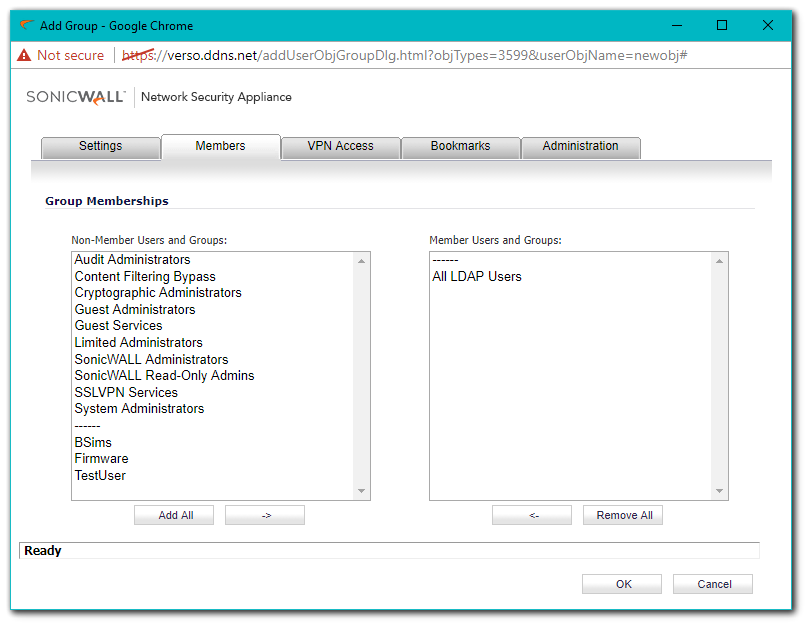
Importing LDAP Groups
- Click Import from LDAP and choose Import user groups from the LDAP directory.
- On the popup window select the Groups you'd like to Import from those available. You can select multiple Groups at once.
- Click Save Selected.
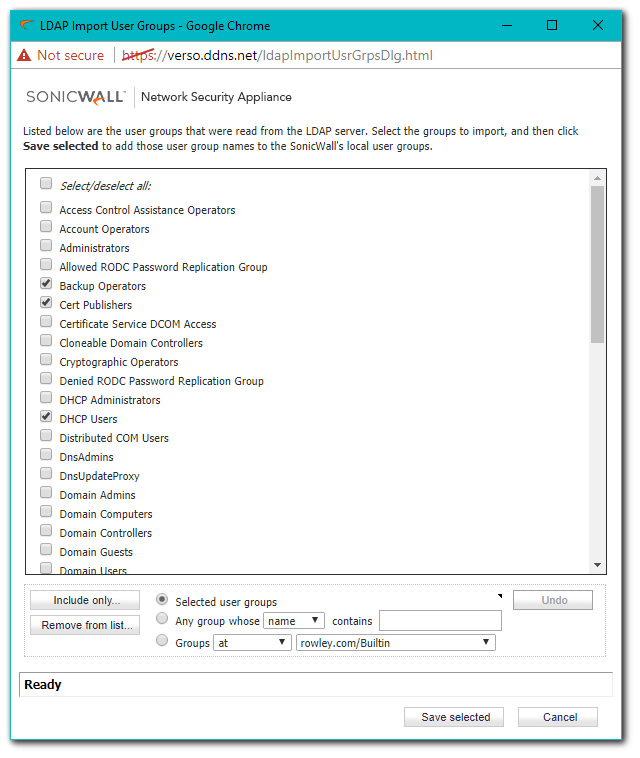
Configuring Content Filter and Policies
- Navigate to Security Services | Content Filter, then click Configure for the policy you'd like to edit.
- Select the User Group that this policy should apply to. This can either be a Local Group, or an LDAP Group.
 CAUTION: While it is possible to nest Groups this is not recommended. It is better to make multiple policies for each Group, even if those policies are identical to one another.
CAUTION: While it is possible to nest Groups this is not recommended. It is better to make multiple policies for each Group, even if those policies are identical to one another.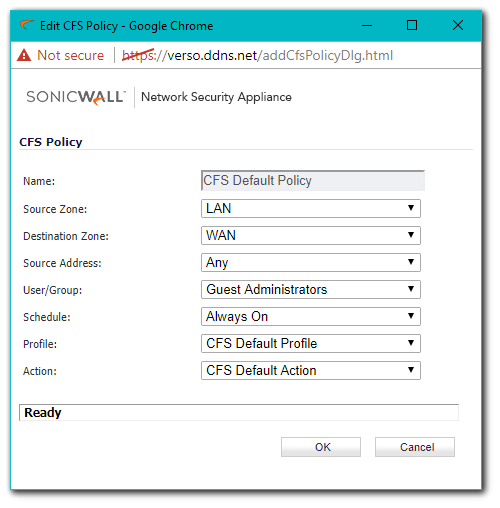
Configuring Access Rule for the User Group
Now that we have our Groups either Imported or Created and also applied to our CFS Policies we need to create a way for users to Authenticate against the SonicWall. Since we're not using Single Sign On we will have to force users to signing to the SonicWall directly.
While Users can navigate to the SonicWalls IP address manually and login this is a cumbersome solution. Instead it's possible to create an Access Rule which redirects Users to the SonicWall and forces them to Authenticate.
First we need to create an Access Rule to allow DNS
- Navigate to Firewall | Access Rules and click Add. In the From and To fields select the Zone that traffic originates from and WAN, respectively.
- Fill in the rest of the Access Rule as shown below.
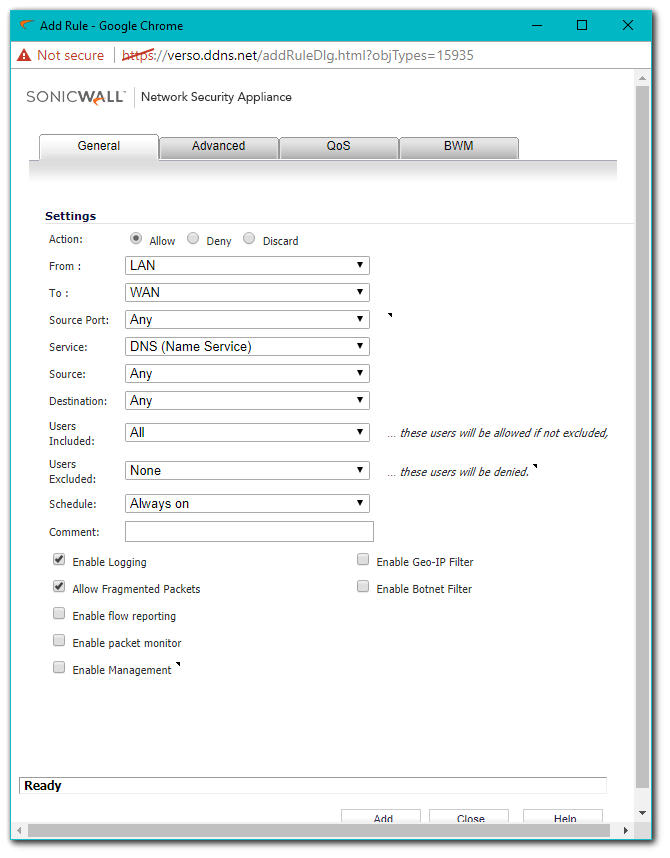
 CAUTION: Ensure that this access rule is the #1 Priority under the Zone to Zone page, if other more permissive access rules are a higher priority then this configuration will not work.
CAUTION: Ensure that this access rule is the #1 Priority under the Zone to Zone page, if other more permissive access rules are a higher priority then this configuration will not work.
- Click Add again and set the From and To Zones to be the same as they were in the previous access rule.
- Fill in the rest of the access rule as shown below (Substitute your own Group for the one shown).
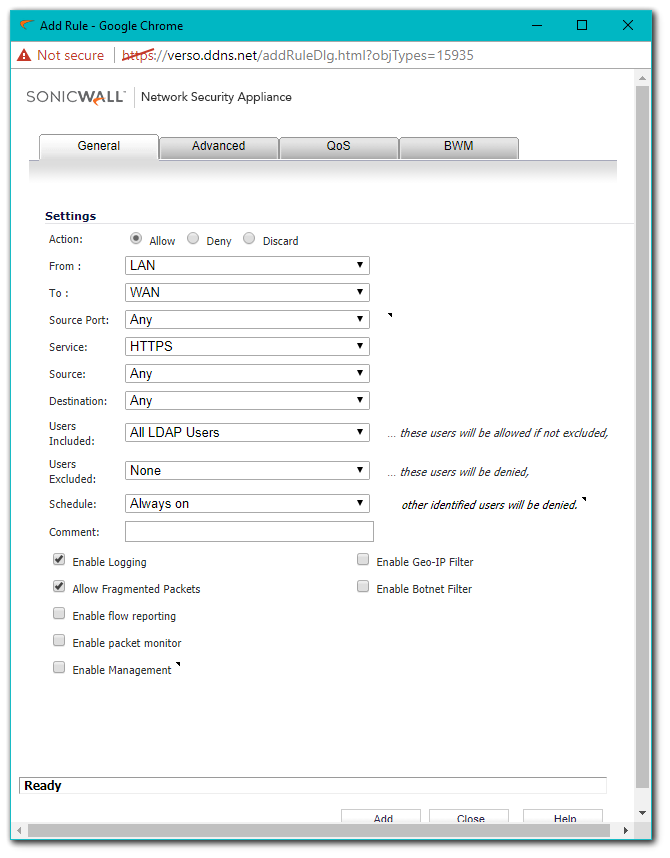
 TIP: It's possible to create a Service Group and combine HTTP, HTTPS, and any other Services you'd like and only use one Access Rule. This is a recommended Best Practice.
TIP: It's possible to create a Service Group and combine HTTP, HTTPS, and any other Services you'd like and only use one Access Rule. This is a recommended Best Practice. CAUTION: Ensure that this Access Rule is the #2 Priority under the Zone to Zone page.
CAUTION: Ensure that this Access Rule is the #2 Priority under the Zone to Zone page.
How to Test
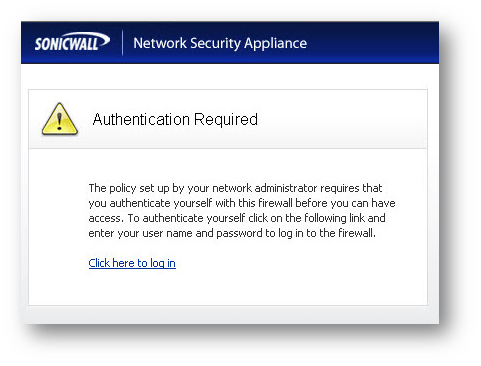
From a Host on one of the Zones where you have setup both Content Filtering and the required Access Rules try to access any website. The SonicWall should redirect the request and show a screen similar to the below image.