How to Restrict VPN Access to GVC Users
Description
There are multiple methods to restrict remote VPN users' access to network resources. This article list three, namely:
- Restrict access to hosts behind SonicWall based on Users.
- Restrict access to a specific service (e.g. Terminal Services) using Access Rules.
- Restrict access to a specific host behind the SonicWall using Access Rules.
When a user is created, the user automatically becomes a member of Trusted Users and Everyone under the Users | Local Groups page. If you click on the configure tab for any one of the groups and if LAN Subnets is selected, every user can access any resource on the LAN. Following are the steps to restrict access based on user accounts.
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Adding Address Objects:
- Create an address object for the computers to which restricted users will be allowed. This can be done by selecting the Objects | Match Objects | Addresses page. Under Address Objects click Add.
- Create an address object for the computer or computers to be accessed by Restricted Access group.
For more information on creating Address Objects, refer Understanding Address Objects in SonicOS
Adding and Configuring User Groups:
- Click on Device | Users | Local Users & Groups | Local Groups. Click the Configure tab for Everyone and Trusted Users group. Click the VPN Access tab and remove all Address Objects from the Access List.
- Click Users | Local Users & Groups | Local Groups | Add Group, crate two custom user groups such as “Full Access and Restricted Access”.
- For the “Full Access” user group under the VPN Access tab, select LAN Subnets.
- For the “Restricted Access” user group under the VPN Access tab, select the address object that you had previously created for the restricted computers.

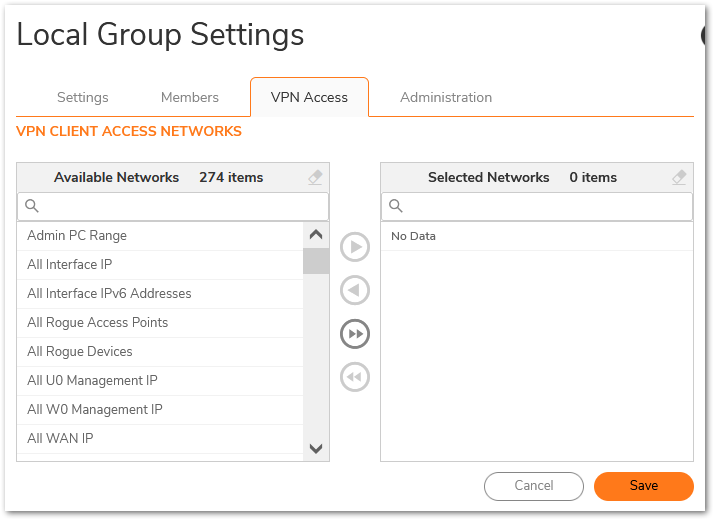
Adding users to appropriate Groups:
- Create users by clicking Users | Local Users & Groups | Local Users. For those users who need full access, include them under the Full Access user group by clicking the Groups tab and adding them under Member of. For those users who will be given restricted access, include them under the Restricted Access user group by clicking the Groups tab and adding them under Member of.
Restrict access to a specific service (e.g. Terminal Services) using Access Rules:
- In the SonicWall Management UI, navigate to the Policy| Rules and Policies | Access Rules page.
- Select From VPN To LAN from the drop down menu ot use the matrix. Create a Deny rule.
 NOTE: If you have other zones like DMZ, create similar rules From VPN to DMZ.
NOTE: If you have other zones like DMZ, create similar rules From VPN to DMZ.
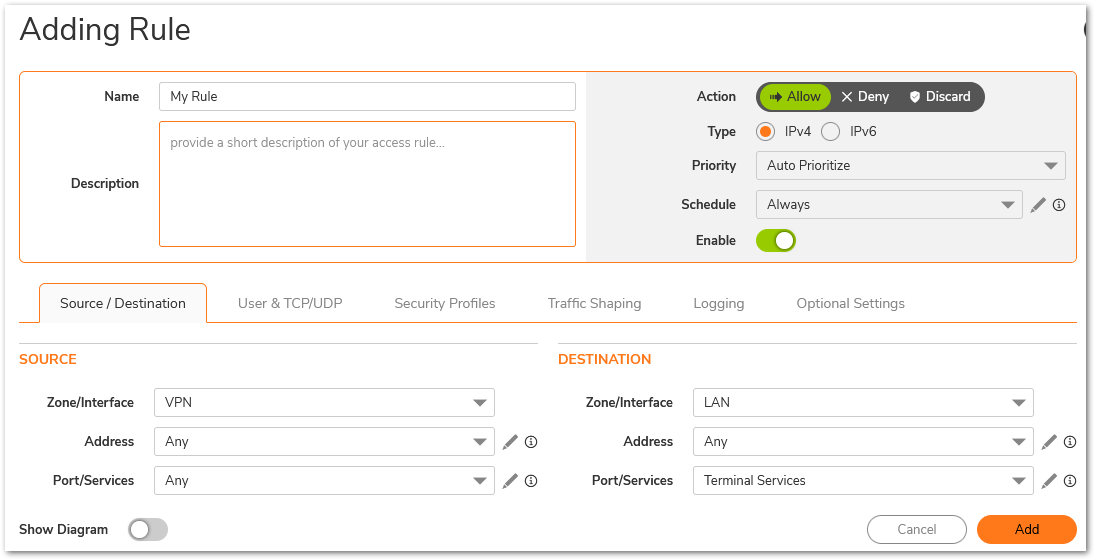
How to Test:
Test by trying to ping an IP Address on the LAN from a remote GVC PC. Since we have selected Terminal Services ping should fail. Try to do Remote Desktop Connection to the same host and you should be able to.
Restrict access to a specific host behind the SonicWall using Access Rules:
In this scenario, remote VPN users' access should be locked down to one host in the network, namely a Terminal Server on the LAN. It is assumed that WAN GroupVPN, DHCP over VPN and user access list has already configured.
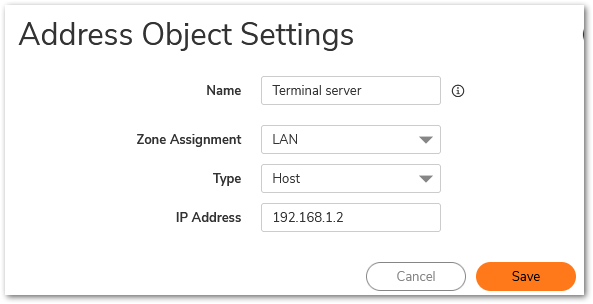
Creating an address object for the Terminal Server
- Login to the SonicWall management interface.
- Navigate to Objects | Match Objects | Addresses.
- Create the following address object.
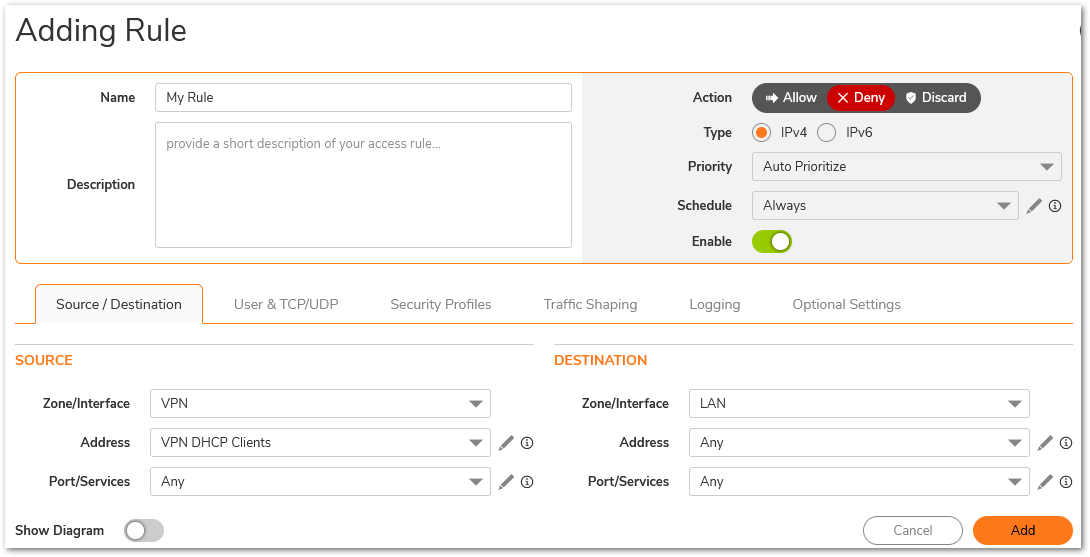
Creating access rules to block all traffic to the network and allow traffic to the Terminal Server.
- Navigate to Policy| Rules and Policies | Access Rules
- Go to the From VPN | To LAN page.
- Create the following access rules.
 NOTE: If you have other zones like DMZ, create similar deny rules From VPN to DMZ.
NOTE: If you have other zones like DMZ, create similar deny rules From VPN to DMZ.
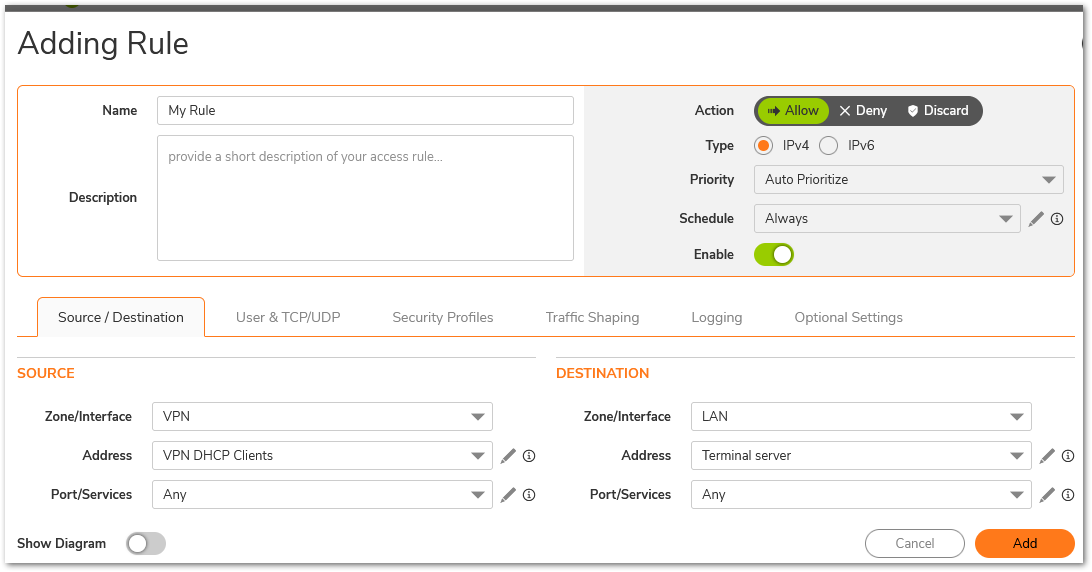
How to Test:
Test by trying to ping an IP address on the LAN or DMZ from a remote GVC PC. Since we have created a deny rule to block all traffic to LAN or DMZ from remote GVC users, the ping should fail. Try to do a ping or Remote Desktop Connection to the Terminal Server on the LAN and you should be able to.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Restrict access to hosts behind SonicWall based on Users:
Adding Address Objects:
- Create an address object for the computers to which restricted users will be allowed. This can be done by selecting the Manage | Objects | Address Objects page. Under Address Objects click Add.
- Create an address object for the computer or computers to be accessed by Restricted Access group.
For more information on creating Address Objects, refer Understanding Address Objects in SonicOS
Adding and Configuring User Groups:
- Click Users | Local Users & Groups | Local Groups. Click the Configure tab for Everyone and Trusted Users group. Click the VPN Access tab and remove all Address Objects from the Access List.
- Click Users | Local Users & Groups | Local Groups | Add Group, crate two custom user groups such as “Full Access and Restricted Access”.
- For the “Full Access” user group under the VPN Access tab, select LAN Subnets.
- For the “Restricted Access” user group under the VPN Access tab, select the address object that you had previously created for the restricted computers.
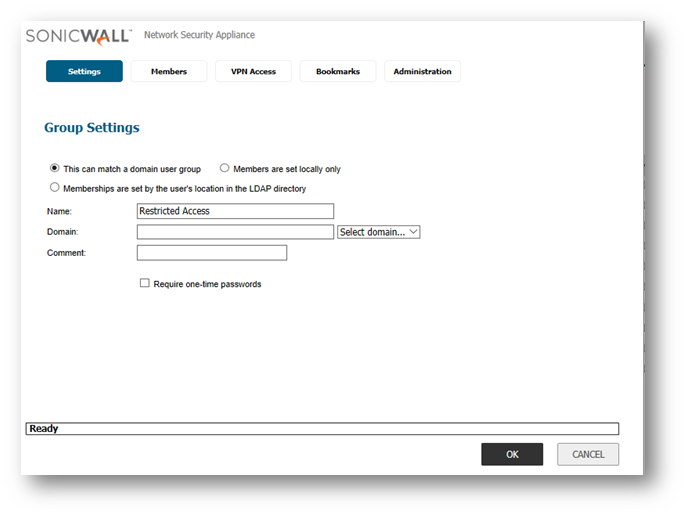
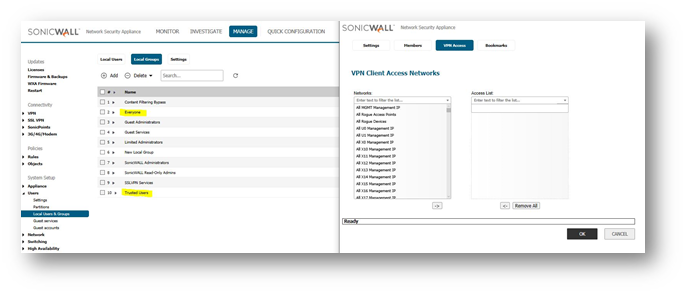
Adding users to appropriate Groups:
- Create users by clicking Users | Local Users & Groups | Local Users. For those users who need full access, include them under the Full Access user group by clicking the Groups tab and adding them under Member of. For those users who will be given restricted access, include them under the Restricted Access user group by clicking the Groups tab and adding them under Member of.
Restrict access to a specific service (e.g. Terminal Services) using Access Rules:
- In the SonicWall Management UI, navigate to the Manage | Rules | Access Rules page.
- Select From VPN To LAN from the drop down menu ot use the matrix. Create a Deny rule.

 NOTE: If you have other zones like DMZ, create similar rules From VPN to DMZ.
NOTE: If you have other zones like DMZ, create similar rules From VPN to DMZ.
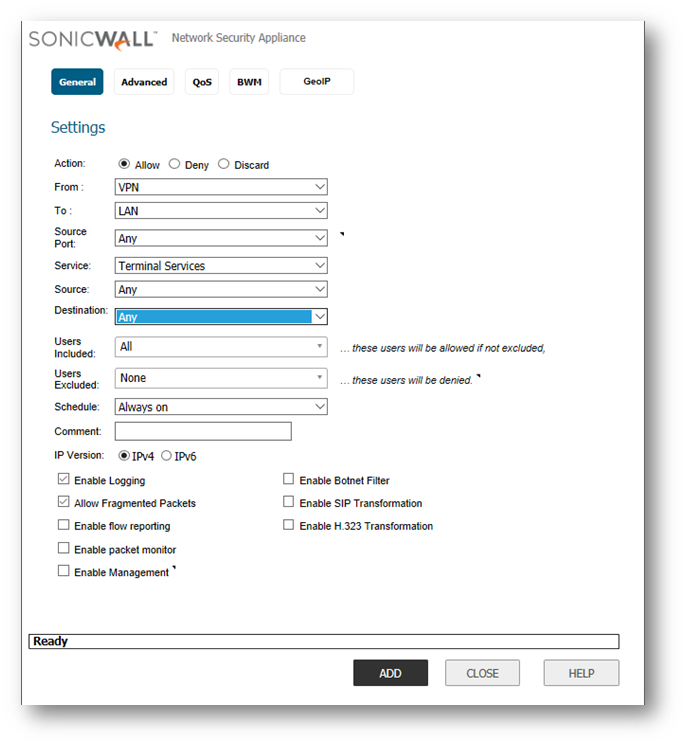
How to Test:
Test by trying to ping an IP Address on the LAN from a remote GVC PC. Since we have selected Terminal Services ping should fail. Try to do Remote Desktop Connection to the same host and you should be able to.
Restrict access to a specific host behind the SonicWall using Access Rules:
In this scenario, remote VPN users' access should be locked down to one host in the network, namely a Terminal Server on the LAN. It is assumed that WAN GroupVPN, DHCP over VPN and user access list has already configured.
Creating an address object for the Terminal Server
- Login to the SonicWall management interface.
- Navigate to Manage | Objects | Address Objects
- Create the following address object.
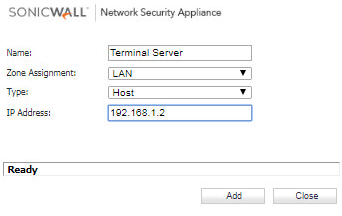
Creating access rules to block all traffic to the network and allow traffic to the Terminal Server.
- Navigate to Manage| Rules | Access Rules
- Go to the From VPN | To LAN page.
- Create the following access rules.
 NOTE: If you have other zones like DMZ, create similar deny rules From VPN to DMZ.
NOTE: If you have other zones like DMZ, create similar deny rules From VPN to DMZ.
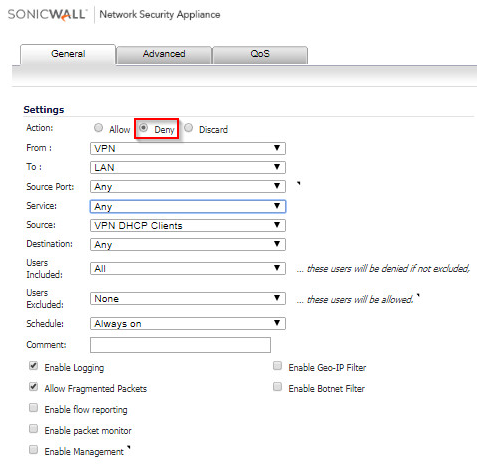
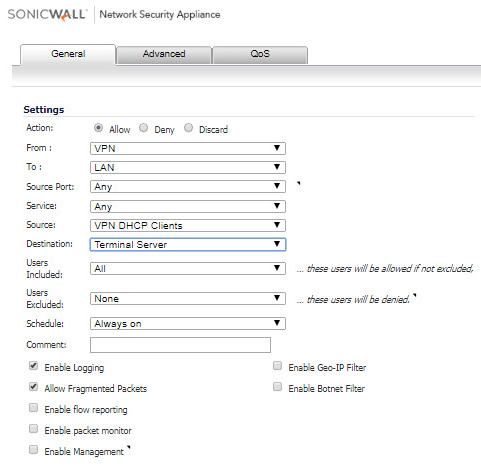
How to Test:
Test by trying to ping an IP address on the LAN or DMZ from a remote GVC PC. Since we have created a deny rule to block all traffic to LAN or DMZ from remote GVC users, the ping should fail. Try to do a ping or Remote Desktop Connection to the Terminal Server on the LAN and you should be able to.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
Restrict access to hosts behind SonicWall based on Users:
Adding Address Objects:
- Create an address object for the computers to which restricted users will be allowed. This can be done by selecting the Network | Address Objects page. Under Address Objects click Add. Create an address object for the computer or computers to be accessed by Restricted Access group.
For more information on creating Address Objects, refer Understanding Address Objects in SonicOS
Adding and Configuring User Groups:
- Click Users | Local Groups. Click the Configure tab for Everyone and Trusted Users group. Click the VPN Access tab and remove all Address Objects from the Access List.
- Click Users | Local Groups | Add Group, crate two custom user groups such as “Full Access and Restricted Access”.
- For the “Full Access” user group under the VPN Access tab, select LAN Subnets.
- For the “Restricted Access” user group under the VPN Access tab, select the address object that you had previously created for the restricted computers.
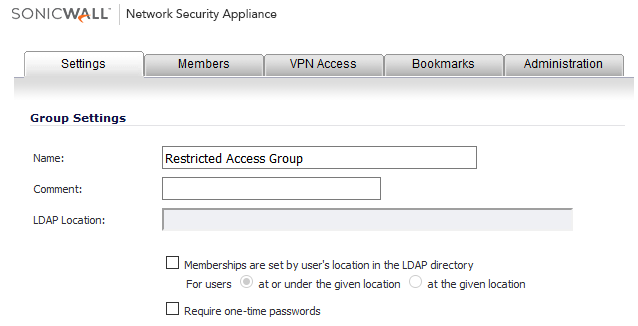

Adding users to appropriate Groups:
- Create users by clicking Users | Local Users. For those users who need full access, include them under the Full Access user group by clicking the Groups tab and adding them under Member of. For those users who will be given restricted access, include them under the Restricted Access user group by clicking the Groups tab and adding them under Member of.
Restrict access to a specific service (e.g. Terminal Services) using Access Rules:
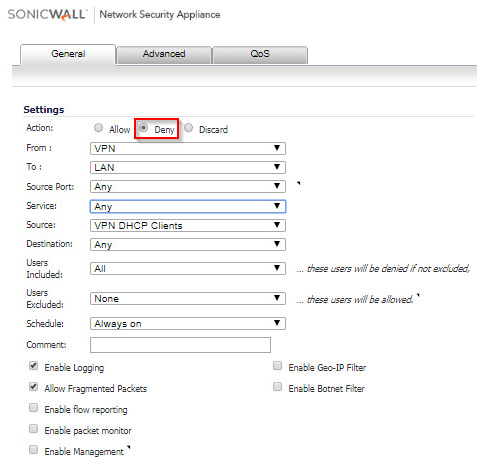
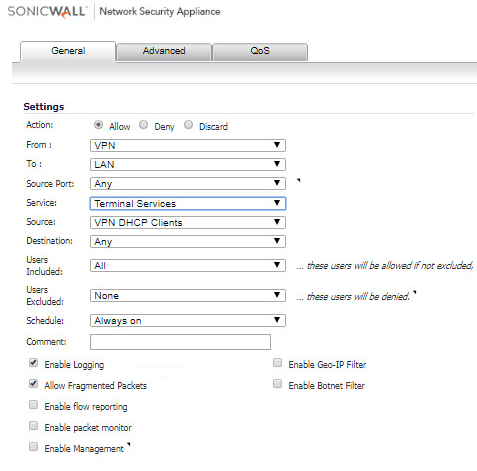
- In the SonicWall Management UI, navigate to the Firewall | Access Rules page.
- Select From VPN To LAN in the matrix.
- Create the following access rules.
Note: If you have other zones like DMZ, create similar rules From VPN to DMZ.
How to Test:
Test by trying to ping an IP Address on the LAN from a remote GVC PC. Since we have selected Terminal Services ping should fail. Try to do Remote Desktop Connection to the same host and you should be able to.
Restrict access to a specific host behind the SonicWall using Access Rules:
In this scenario, remote VPN users' access should be locked down to one host in the network, namely a Terminal Server on the LAN. It is assumed that WAN GroupVPN, DHCP over VPN and user access list has already configured.
Creating an address object for the Terminal Server
- Login to the SonicWall management interface.
- Navigate to Network | Address Objects
- Create the following address object.

Creating access rules to block all traffic to the network and allow traffic to the Terminal Server.
- Navigate to Firewall | Access Rules
- Go to the From VPN | To LAN page.
- Create the following access rules.
 NOTE: If you have other zones like DMZ, create similar deny rules From VPN to DMZ.
NOTE: If you have other zones like DMZ, create similar deny rules From VPN to DMZ.


How to Test:
Test by trying to ping an IP address on the LAN or DMZ from a remote GVC PC. Since we have created a deny rule to block all traffic to LAN or DMZ from remote GVC users, the ping should fail. Try to do a ping or Remote Desktop Connection to the Terminal Server on the LAN and you should be able to.