SteelFox Leverages Signed Windows Drivers to Attack Kernel

Overview
This week, the SonicWall Capture Labs threat research team investigated a sample of SteelFox malware. This is bundled with “software activators” for JetBrains and Foxit PDF readers. During installation, they run as a service and use vulnerable signed Windows drivers to exploit and attack the kernel. Secondarily, cryptominers such as XMRig are run in memory via AppInfo, as well as network communications.
Infection Cycle
The sample is detected as an executable without a packer or protector; however, the file entropy shows that it is, in fact, packed.
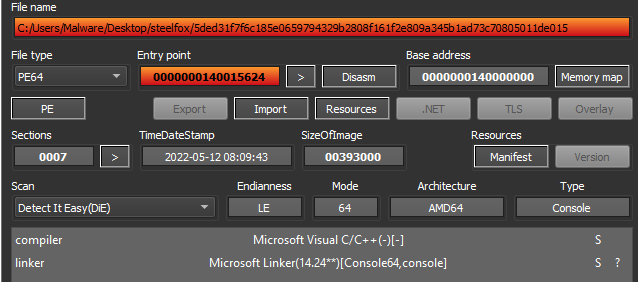
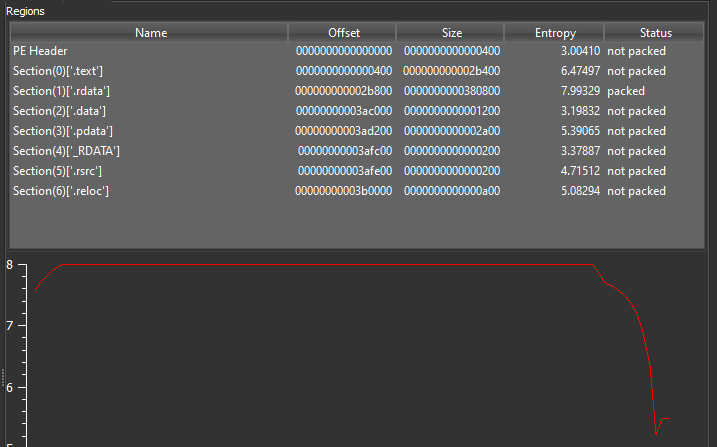
Figures 1 (top), 2(bottom): Initial detection, high entropy means rdata is packed
Attempting to run this in any way other than as a service will result in the program immediately exiting. It will also crash many analysis tools or take an exceedingly long time to load. Once the malware has been loaded as a service, it will run and begin enumerating all running processes. A DNS request to Google is attempted to establish connectivity; if this fails, no further network activity is attempted.
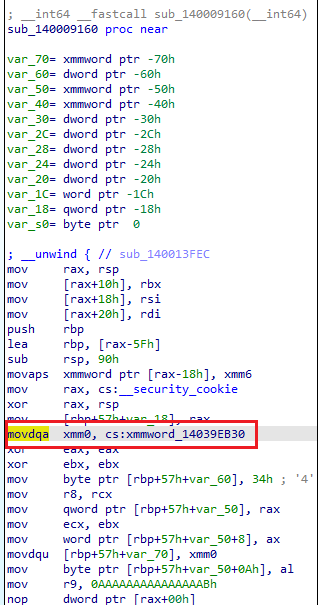
Figure 3: One of the main decryption routines
Once the payload has been unpacked in memory using 7-byte XOR keys, a separate svchost process will launch AppInfo and control is passed to that. The original process will close. AppInfo will load WinRing0, a vulnerable driver as noted in CVE-2020-14979 and CVE-2021-41295. The driver is then exploited and kernel-level access is gained. SteelFox will use this system-level access to pull user account information, browser data and login information, email credentials, etc.
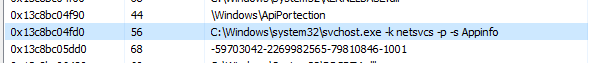
Figure 4: Secondary svchost.exe process running AppInfo
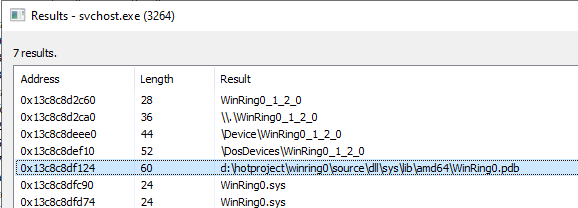
Figure 5: WinRing0 is accessed using \\.\WinRing0_1_2_0
Although other versions have been noted attempting to download XMRig cryptominer from a GitHub repository, that was not observed during testing.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this malware, the following signatures have been released:
- MalAgent.SteelFox.A
IOCs
8d9abb726799da54909ebd7a9c356b990fd68175945e6c05e64de18ca7d1d3d8
Share This Article

An Article By
An Article By
Security News
Security News

