Fake Google Chrome Website Tricks Users into Installing Malware

Google Chrome is the most widely used web browser in the world, and this dominance makes it a great vector for cybercriminals to use to spread malware to unsuspecting users. The SonicWall Capture Labs threat research team recently found what appears to be a legitimate website where a user can download and install Google Chrome. But the website is a fake – it installs malicious files that have nothing to do with Google Chrome.
Infection Cycle
An unsuspecting user is presented with this legitimate looking website at the following URL: httpx://google.tw.cn
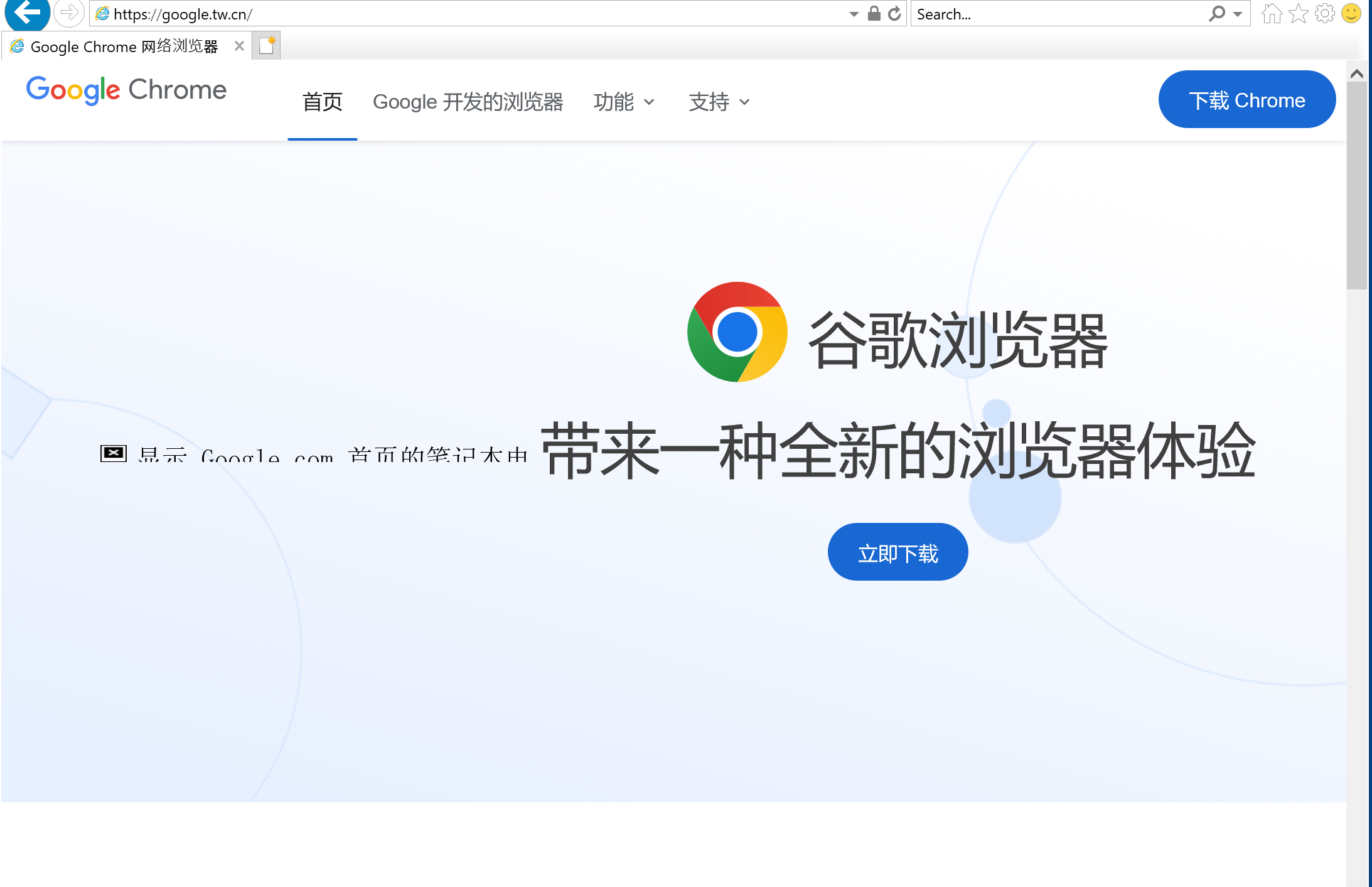
Figure 1: Legitimate looking website hosting “Google Chrome” download
Upon clicking on the download button, an archive file named “Goegle sretp.zip” is downloaded. Within this zip file is an executable with the same name.

Figure 2: Zip file download
To make it seem even more legitimate, this installer file uses “Google Browser” as its file description.
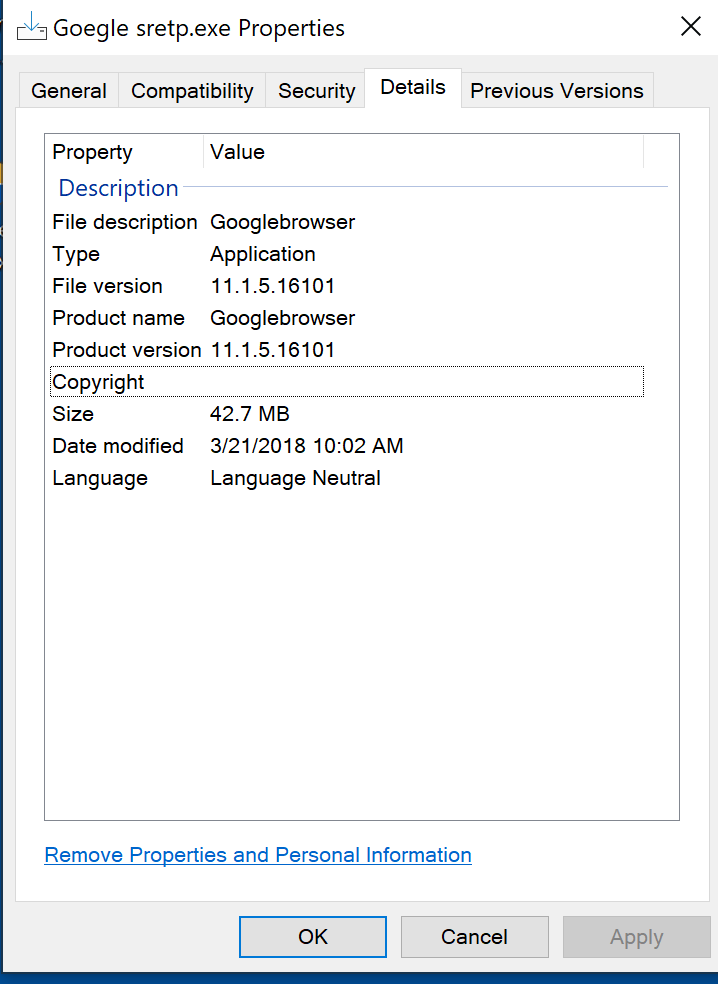
Figure 3: File properties of the installer file Goegle sretp.exe
Upon execution, an installation window pops up which guides the user through the installation process.
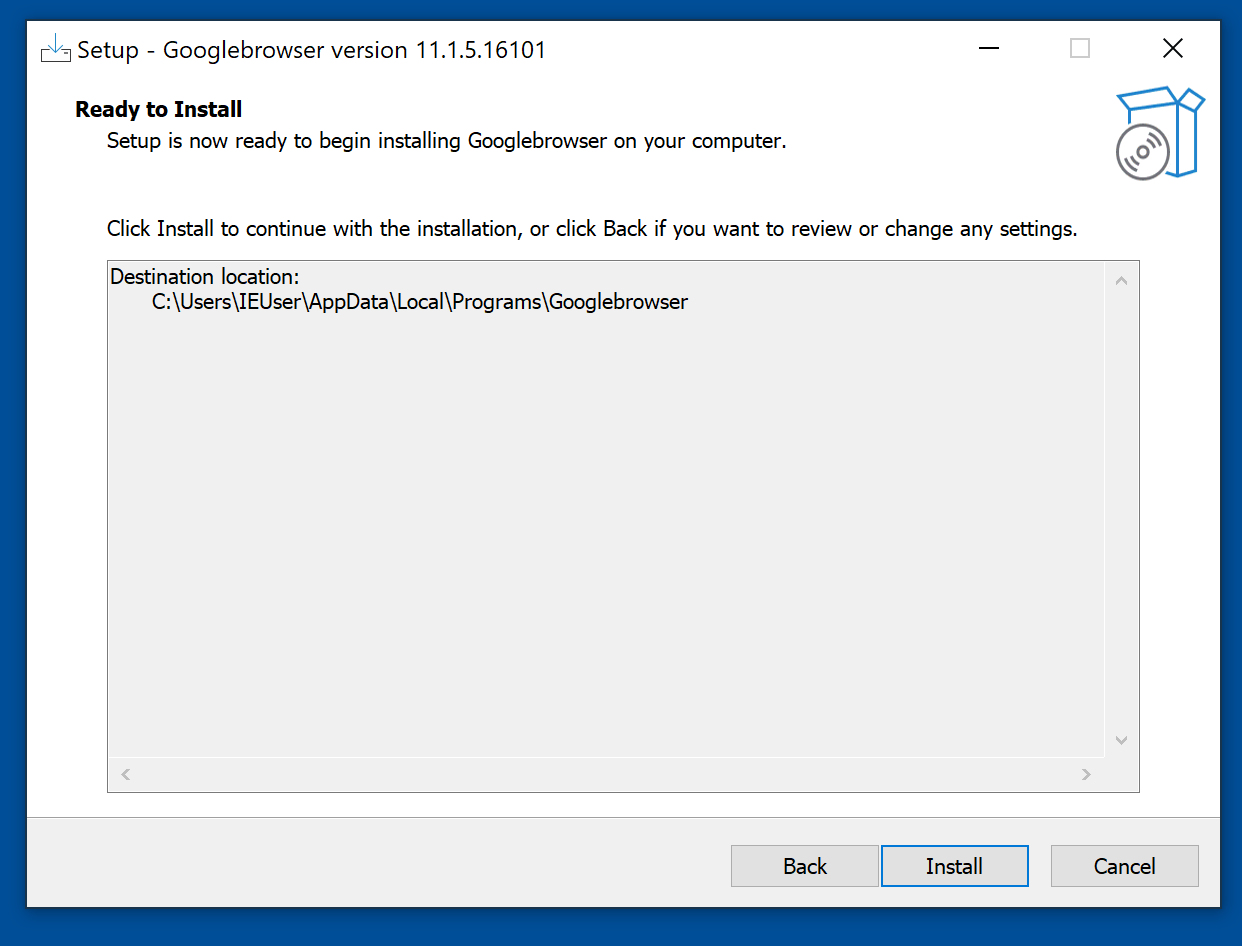
Figure 4: Installation window
A shortcut link to “Google Chrome” is then added to the desktop after the installation finishes. However, this lnk file opens another application, not the web browser.
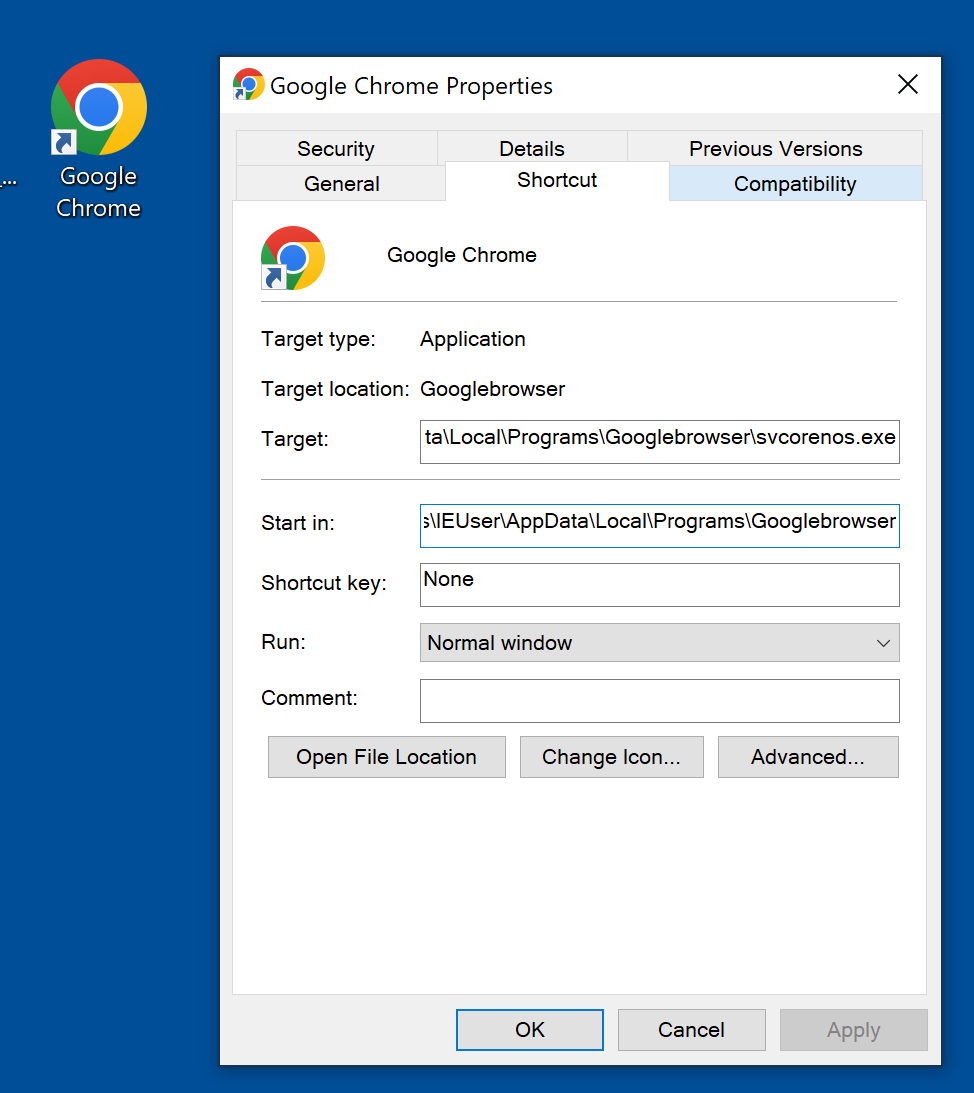
Figure 5: Google chrome lnk file on Desktop
A file named “svcorenos.exe” is silently executed in the background. This is the same file that the Google Chrome.lnk file will execute if the user decides to click that shortcut file. It spawns a legitimate Windows application called “ComputerDefaults.exe” to execute another copy of itself, possibly to circumvent detection.

Figure 6: ComputerDefaults.exe is used to execute svcorenos.exe
The program svcorenos.exe is a renamed copy of another legitimate application from Duality Software called DS Clock. It is a free desktop utility for displaying the time and date. It is highly customizable and allows users to specify their own remote server to sync the date and time using a config file. In this case, the malware is using this free utility to connect to a remote host to send and receive data.
During our analysis, this file maintained a connection to a remote host – 103(.)215(.)78(.)57.

Figure 7: svcorenos.exe constantly connecting to a remote host
Figure 8: Data exchanged between svcorenos and the remote host
To ensure that this application runs on reboot, it was added as a service in the system’s registry.
- HKLM\System\CurrentControlSet\Services\svcorenos project
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Malagent.CRM Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News
