GhostRAT Plays Effective Hide and Seek

Overview
This week, the SonicWall Capture Labs threat research team investigated a sample of GhostRAT malware. This highly infectious file is built to be persistent and thorough, with many anti-analysis, anti-AV, anti-VM, and evasion techniques. Upon infection, the entire system is scraped for data, all points of input are hooked to be recorded, and it has multiple methods of loading itself or one of its dropped modules into memory.
Infection Cycle
The initial sample is a 73MB file which is detected as being packed with 7-Zip, as well as having suspicious markers: the time stamp is fifteen years old, and any file with 7-Zip should not have an installer, archive, and overlay with the same data.
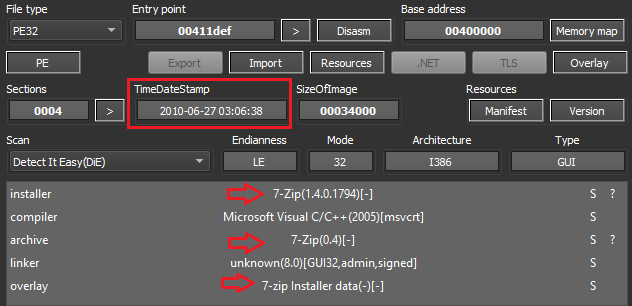
Figure 1: Initial sample detection
However, attempting to unzip the file gives an error that the checksum data is bad, meaning the only way a normal user would be able to see the file contents is by launching the program.
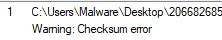
Figure 2: Error received when attempting to manually unzip
Dynamic analysis is necessary as the sample is substantially larger than the average malware file, as well as the excessive amount of anti-analysis, anti-VM and anti-debug capabilities. When the sample is run through a debloat program, the size drops to 184kb but generates new errors, despite running similar system checks when launched.
During runtime, the following actions are taken:
Parent sample drops files in the following locations:
- C:\Users\Public\Bilite\Axialis\Update.exe
- C:\Users\Public\Bilite\Axialis\Update.dll
- C:\Users\Public\Bilite\360inst_install.exe
- C:\Users\Public\Bilite\360inst_install.exe.lnk
- C:\Users\user\AppData\Local\Temp\backup.dll
- C:\Users\user\AppData\Local\Temp\backup.exe
- C:\Users\user\AppData\Local\Temp\monitor.bat
- C:\Users\user\AppData\Local\updated.ps1
Update.exe runs commands to set persistence
- cmd.exe /B /c "C:\Users\user\AppData\Local\Temp\\monitor.bat"
- cmd.exe /C powershell -Command "Set-ExecutionPolicy Unrestricted -Scope CurrentUser
- powershell -ExecutionPolicy Bypass -File C:\Users\user\AppData\Local\updated.ps1
The “monitor.bat” file checks for the running process and, if not found, loads a copy of the binary into memory.
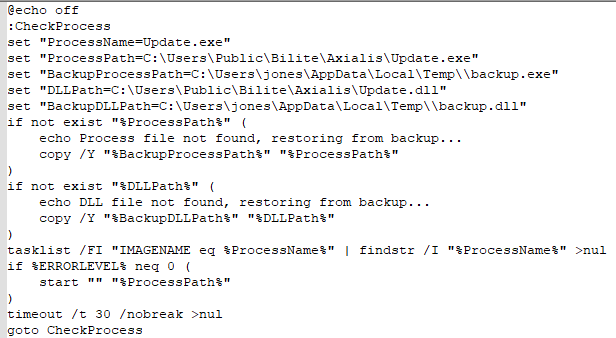
Figure 3: Contents of “monitor.bat”
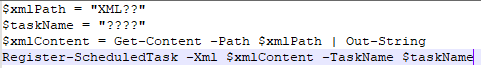
Figure 4: Updated.ps1 script contents
In addition to the PowerShell script, a .lnk, or shortcut file, is created and dropped. This is actually a Shell32 command that will create a new executable but only if the required system path exists.
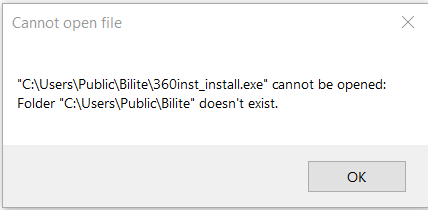
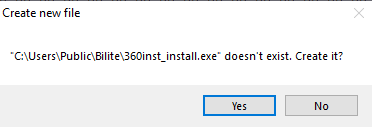
Figures 5 and 6: Attempting to open or edit the shortcut will result in one of these messages
Looking at the file in a hex editor reveals some of the commands.
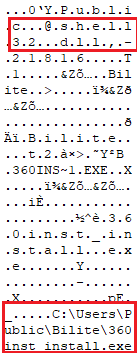
Figure 7: Decoded ASCII text from the .lnk file
The OS is queried for hardware and software versions, locale, installed languages, and system time. There are also multiple checks for virtualized environments with Xen or Qemu hosts, as well as debugging tools; GhostRAT will look for software breakpoints, use time comparisons, IsDebuggerPresent, IsProcessorFeaturePresent, and debug message output. A mutex is created in the following format:
The parent sample, along with a dropped file named ‘Update.exe’, will then perform the following actions while reaching out to two IP addresses acting as C2 servers:
- Checks for system drives alphabetically to infect attached drives
- Uses process injection to hide during runtime
- Sets system hooks for input capture via keystrokes, mouse, and screenshots
- Uses PowerShell for privilege escalation and initializing BitLocker, as well as running tests on AppLocker status
- Hunts for AV products: - 360Safe.exe/360Tray.exe: 360 Total Security (Qihu Technology Co., Beijing)
- Acs.exe: Atheros Configuration Server
- ashDisp.exe: Avast Antivirus
- AYAgent.aye: ALYac EDR
- Avcenter.exe: Avira Antivirus
- Avgwdsvc.exe: AVG Security
- Avp.exe: Avast Security
- Cfp.exe: Comodo Firewall Pro
- K7TSecurity.exe: K7 Total Security
- KSafeTray.exe: Kingsoft PC Doctor
- Kxetray.exe: Kingsoft Internet Security
- Mcshield.exe: McAfee Antivirus
- QUHLPSVC.EXE: Quick Heal Total Security
- RavMonD.exe: Rising Internet Security (Beijing)
- Rtvscan.exe: Symantec Endpoint Protection
- TMBMSRV.exe: TrendMicro Security
- Vsserv.exe: BitDefender Total Security
- Checks for Windows Defender: - Queries Defender Status at registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{2781761E-28E0-4109-99FE-B9D127C57AFE}
- Sets persistence in the registry: - HKEY_CURRENT_USER\Console\0 9e9e85e05ee16fc372a0c7df6549fbd4
- HKEY_CURRENT_USER\Console\IpStats
- Covers tracks via clearing Windows Event Logs: OpenEventLogW, OpenEventLogW, ClearEventLogW, CloseEventLog
In short, this will enumerate every file, process, clipboard data, registry entry, and drive. Using privilege escalation, it will shutdown or hinder antivirus products and create multiple points of persistence. All input is recorded, as well as screen activity, to the point that “Update.exe” can change the wallpaper on a victim’s system. Data is encoded via XOR and RC4 to be exfiltrated to designated C2 servers.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this malware, the following signatures have been released:
- MalAgent.GhostRAT
IOCs
- b86af545e9a2f86c05538eb7fcb85cf63085a0730925a9587253d46590a4e4e9
- b35314c2c3b1aab777d621c6fd8516a877b27efbde4dd4addd6843c411e96aa3
- c4d1454ad9740c5f0945650a250dbefa7fcdb516214e3242dd66ab4ea35ced67
- c1eb83993c85e01ee6ae84eb6e05744ff8c3ccc02c41d09c22286e3012ef46fc
- 9c6e9543c8bd435e3e02ef1a312c502eeb9fb42d11add8e45a063b6ed9cd9cf6
- 176d4dc9403dc70824912ea81379fa8c3c0bb8b555c672a648e1cb4ae9cd0805
Share This Article

An Article By
An Article By
Security News
Security News
