Windows LDAP Denial of Service Vulnerability (CVE-2024-49113): Crucial Information and How to Stay Protected

Overview
The SonicWall Capture Labs threat research team became aware of a denial-of-service vulnerability in the Windows Lightweight Directory Access (LDAP) Protocol, assessed its impact and developed mitigation measures. LDAP is a directory service protocol that provides a mechanism for connecting to, searching, and modifying Internet directories. It is essential for Active Directory Domain Controllers (DCs) to manage users, servers and other devices efficiently.
Windows 10, 11, and Windows Server OS, without having installed the updates released on 10 December 2024, allow an unauthenticated threat actor to crash the server by sending a malicious CLDAP (Connectionless Lightweight Directory Access Protocol) referral response. A publicly available PoC to reproduce the exploit has been released. Considering its critical role in Active Directory Domain Controllers, any vulnerabilities in LDAP can pose severe risks. Hence, users are strongly encouraged to upgrade their instances to the latest fixed version, as Microsoft mentioned in the advisory.
Technical Overview
The exploit targets the DCE/RPC (Distributed Computing Environment/Remote Procedure Call) connection mechanism to access the vulnerable functionality. The connection involves the below steps.
- Initially, the DCE/RPC bind request is sent to the Windows server, followed by the DsrGetDcNameEx2 request containing the client account's domain name.
- The server will perform a DNS lookup for an SRV query about the domain to get the target LDAP server information and establish the connection.
- DNS query will be responded with the appropriate LDAP server hostname and LDAP port.
- The Windows server will send the CLDAP request to the given machine.
This vulnerability arises due to an out-of-bounds read flaw in the LdapChaseReferral function of LDAP in wldap32.dll. This function redirects an LDAP client to other servers when the original LDAP server is unable to fulfill the request.
The relevant code in the LdapChaseReferral function, as seen in Figure 1, shows that the values of “msgid” and “lm_referral” are being fetched from the same variable named “value_from_response_packet”, which can be controlled by the sender or the attacker.
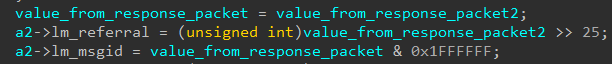
Figure 1: Snippet from LdapChaseReferral function as provided by SafeBreach
To trigger the vulnerable code and force an access violation, the attacker needs to craft a packet as below.
- Modify the byte representing the length of “value_from_response_packet” to 4 instead of 1.
- Set the value of “lm_referral” to non-zero by setting the most significant byte of “value_from_response_packet”, which is now 4 bytes long.
Referring to Figure 2, given the non-zero value of “lm_referral” and the NULL value of “ref_table,” the last line of the code will cause a dereference to an unreal address, leading to an out-of-bounds read.
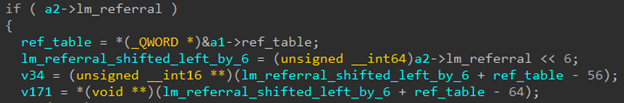
Figure 2: Vulnerable code as provided by SafeBreach
The successful exploitation of this vulnerability will result in the LSAAS service crashing, followed by a reboot of the Windows server. This can be confirmed by checking the application event logs with ID 1000, as illustrated in Figure 3.
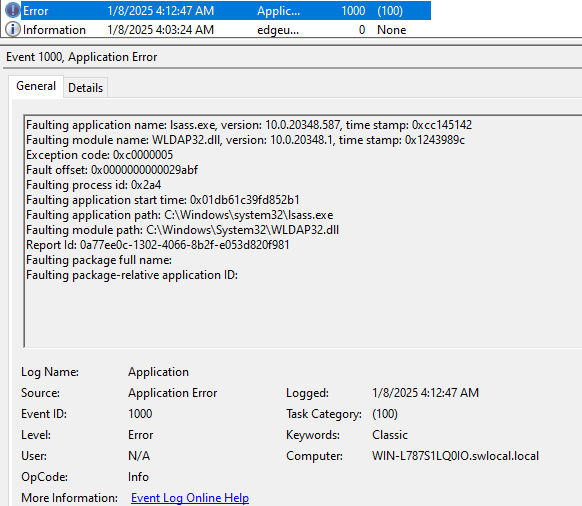
Figure 3: LSAAS crash event log
Triggering the Vulnerability
Leveraging the vulnerability mentioned above requires the attacker to meet the below prerequisites.
- The victim Windows server must be an Active Directory Domain Controller with a netlogon service running.
- The attacker must have network access to the target vulnerable system.
- The attacker must send a DCE-RPC request, using the DsrGetDcNameEx2 operation to be specific, with the attacker-controlled domain, which will trigger a DNS SRV query (Ex. _ldap._tcp.dc._msdcs.<domain_name>) lookup from the victim machine.
- The attacker must control the DNS server response and respond to the above query with the hostname and LDAP port of their own machine.
- The victim server will send the CDAP (Connectionless Lightweight Directory Access Protocol) searchRequest to the attacker-controlled machine.
- Finally, the attacker must send the searchResDone response with a malformed referral value, triggering the integer out-of-bounds read flaw and leading to an abrupt reboot of the victim server.
Exploitation
Exploiting this vulnerability allows the remote threat actor to achieve DoS on the server. We leveraged a publicly available PoC to reproduce the exploit. The PoC requires the attacker to host a DNS server, which should serve the victim-initiated DNS SRV queries with the attacker-controlled machine’s hostname and LDAP port. It must have two DNS SRV records, as mentioned below.
- _ldap._tcp.dc._msdcs.<domain_name> -> LDAP_PORT <attacker_machine_hostname>
Ex. _ldap._tcp.dc._msdcs.example.domain -> 389 s1.example.domain - _ldap._tcp.default-first-site-name._sites.dc._msdcs.<domain_name> -> LDAP_PORT <attacker_machine_hostname>
The video demonstrates the publicly available exploit in the action, mimicking the steps mentioned in “Triggering the Vulnerability” to crash the target Windows server.
Figure 4: Exploit in action
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 4547 Windows LDAP Denial of Service (CVE-2024-49113)
- IPS: 4548 Windows LDAP Denial of Service (CVE-2024-49113) 2
- IPS: 4551 Windows LDAP Denial of Service (CVE-2024-49113) 3
Remediation Recommendations
We have not observed exploit attempts in the wild at the time of publishing this article. However, given the pivotal role of Domain Controllers in an organization's network infrastructure, Windows server users are strongly encouraged to update their instances to the latest version, as mentioned in the vendor advisory.
Additionally, the following temporary workarounds can be implemented if someone cannot apply the updates immediately.
1. Do not allow the domain controllers the internet connectivity, or
2. Do not allow inbound RPC from untrusted networks.
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News
