Apache Struts Path Traversal to RCE: CVE-2024-53677

Overview
The SonicWall Capture Labs threat research team became aware of an unauthenticated, remote code execution vulnerability in the Apache Struts 2 framework, assessed its impact, and developed mitigation measures. Apache Struts is an open-source model-view-controller (MVC) framework for creating Java web applications in the IT infrastructure. It is extensible using a plugin architecture and ships with plugins to support REST, AJAX, and JSON.
Identified as CVE-2024-53677, Apache Struts versions from 2.0.0 to before 6.4.0 allow an unauthenticated threat actor to perform path traversal via the file upload mechanism, which can further lead to remote code execution. This earns a critical CVSS score of 9.8. According to the advisory, Apache Struts 2 users are encouraged to upgrade their instances to the latest fixed version and migrate to the new file upload mechanism.
Technical Overview
This vulnerability arises from a flaw in the file upload mechanism “FileUploadInterceptor”, a component within the default stack that stores the file during the data file transfer operation. The vulnerable file-upload mechanism allows attackers to exploit a path traversal by uploading malicious files to the FileUploadInterceptor component to access it. Applications that do not use the FileUploadInterceptor component are unaffected. Apache Struts’ commit on version 6.4.0 shows multiple updates, out of which the new file upload mechanism introduced is ActionFileUpload interceptor. This interceptor will add several field errors, assuming the action is implemented, as shown in Fig 1. This new file upload mechanism addresses CVE-2024-53677. On close inspection, this path traversal vulnerability looks similar to CVE-2023-50164, wherein the file upload functionality was also used to exploit Apache Struts instances.
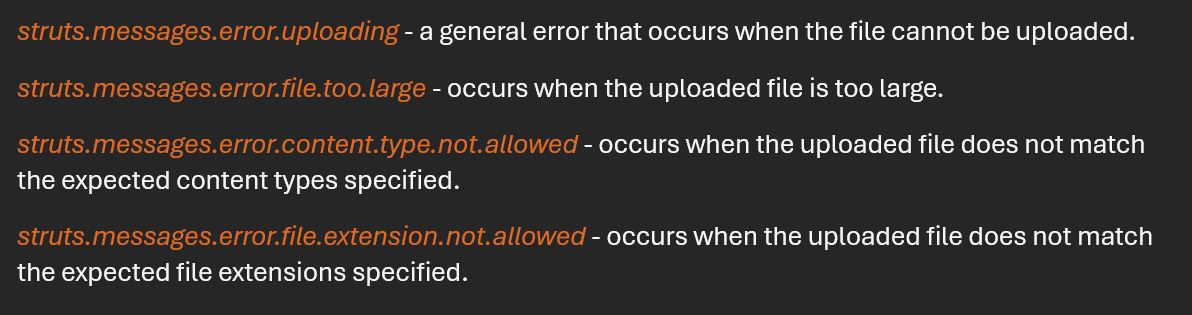
Figure 1: Field Errors in ActionFileUpload Interceptor
The measures were added to Apache Struts 6.4.0 to address a new upload mechanism using a dedicated callback interface to pass information about uploaded files referred to as ActionFileUpload interceptor. The function has been improved to restrict unauthenticated or unauthorized users from uploading or accessing unwanted content using parameters such as
- <file name>: File - the actual File
- <file name>ContentType: String - the content type of the file
- <file name>FileName: String - the actual name of the file uploaded (not the HTML name)
Inspecting the commit for Apache Struts version 6.4.0 indicates that the vulnerable version should not have allowed files to be uploaded without any callback with random filenames or problematic characters that can lead to path traversal. By leveraging this weakness, files with dangerous extensions can be uploaded, leading to remote code execution.
Triggering the Vulnerability
Leveraging the vulnerability mentioned above requires the attacker to meet the below prerequisites.
- The attacker must have network access to the target vulnerable system.
- Applications must use the File Upload Interceptor component for File Uploads.
- The browser must request the uploaded file to execute the specified code in the previous step.
Exploitation
Exploiting this vulnerability allows the remote threat actor to execute arbitrary code on the server. We leveraged a publicly available PoC to demonstrate a remote code execution exploit.
The PoC implants the “name=UploadFileName” file with a random filename into the directory “/upload.action” or “/Struts2FileUpload/upload,” which allows it to be accessible by remote threat actors using HTTP requests to the URL http(s)://vuln-apache-struts.com:port, as seen in Figure 2.
Figure 2: Exploit in action
The sample exploit request over the network can be seen in Figure 3.
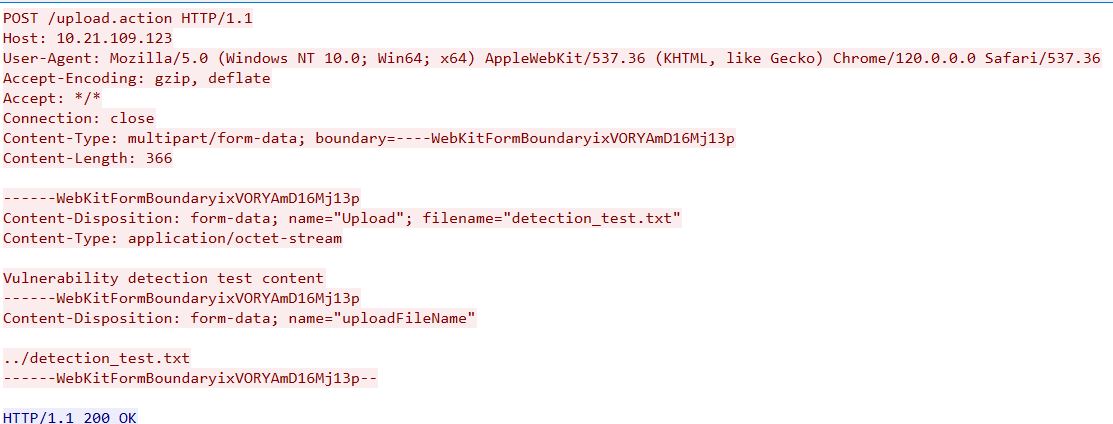
Figure 3: Exploit request over network
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS:20555 Apache Struts Arbitrary File Upload
- IPS:2764 Web Application Suspicious form-data 1
- IPS:4194 Web Application Suspicious form-data 2
- IPS:4541 Web Application Suspicious form-data 3
- IPS:4546 Web Application Suspicious form-data 4
Remediation Recommendations
As mentioned in the vendor advisory, Apache Struts users are strongly encouraged to upgrade their instances to the latest version. The vendor has also clearly noted that the new file-upload mechanism in Apache Struts 2 is not backward compatible with the old one.
Relevant Links
Share This Article

An Article By
An Article By
Dhiren Vaghela
Dhiren Vaghela
Dhiren Vaghela has over a decade of experience in the IPS domain, with a strong focus on defensive security. His expertise lies in identifying, analyzing and mitigating vulnerabilities. Dhiren is well-versed in content-based signature writing, scanner-based alert generation and technical blog writing. By leveraging emerging technologies, he has developed numerous IPS signatures across various protocols. Known for his exceptional signature writing skills and collaborative team spirit, Dhiren is a valuable asset in the field of cybersecurity.
