SonicWall Detects Credential-Stealing SVG File in Phishing Campaign

This week, the SonicWall Capture Labs threat research team performed an analysis of a phishing email that included an SVG file attachment, which contains HTML and JavaScript code designed to capture user credentials.
Understanding SVG Files
Scalable Vector Graphics (SVG) is an XML-based format for creating two-dimensional vector images, allowing for interactivity and animation. SVG files utilize CSS for styling and JavaScript for scripting. The ability to incorporate JavaScript within an SVG file makes it appealing to malware developers, who often exploit these files as a means of initial attack.
Infection Cycle
The harmful file is sent as an attachment in a spam email, disguised as a purchase order, and is named:
"New Purchase Order__pdf.svg."
The inclusion of "pdf" in the filename is intended to deceive users into thinking it is a PDF document. However, this file is actually an SVG file that contains obfuscated JavaScript code, which transmits credentials to a remote server during execution. The use of the SVG extension may be a tactic to bypass restrictions on commonly blocked file types in email applications.
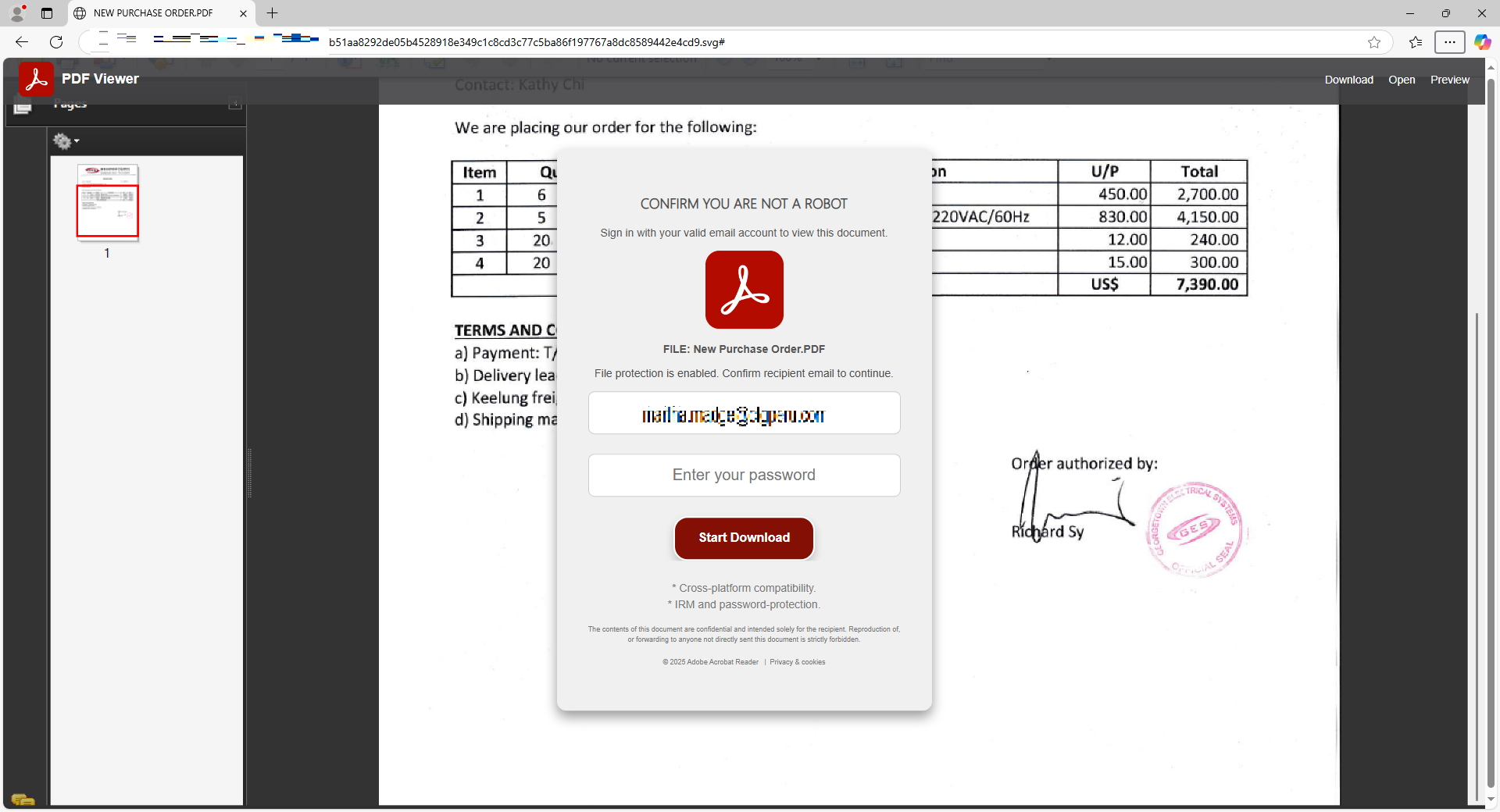
When the SVG file is opened, it displays as a PDF document featuring an order template. It notifies the user that the file is secured and requires signing in with a valid email account to proceed with the download. The username field is automatically populated with the user's email address, as illustrated below:
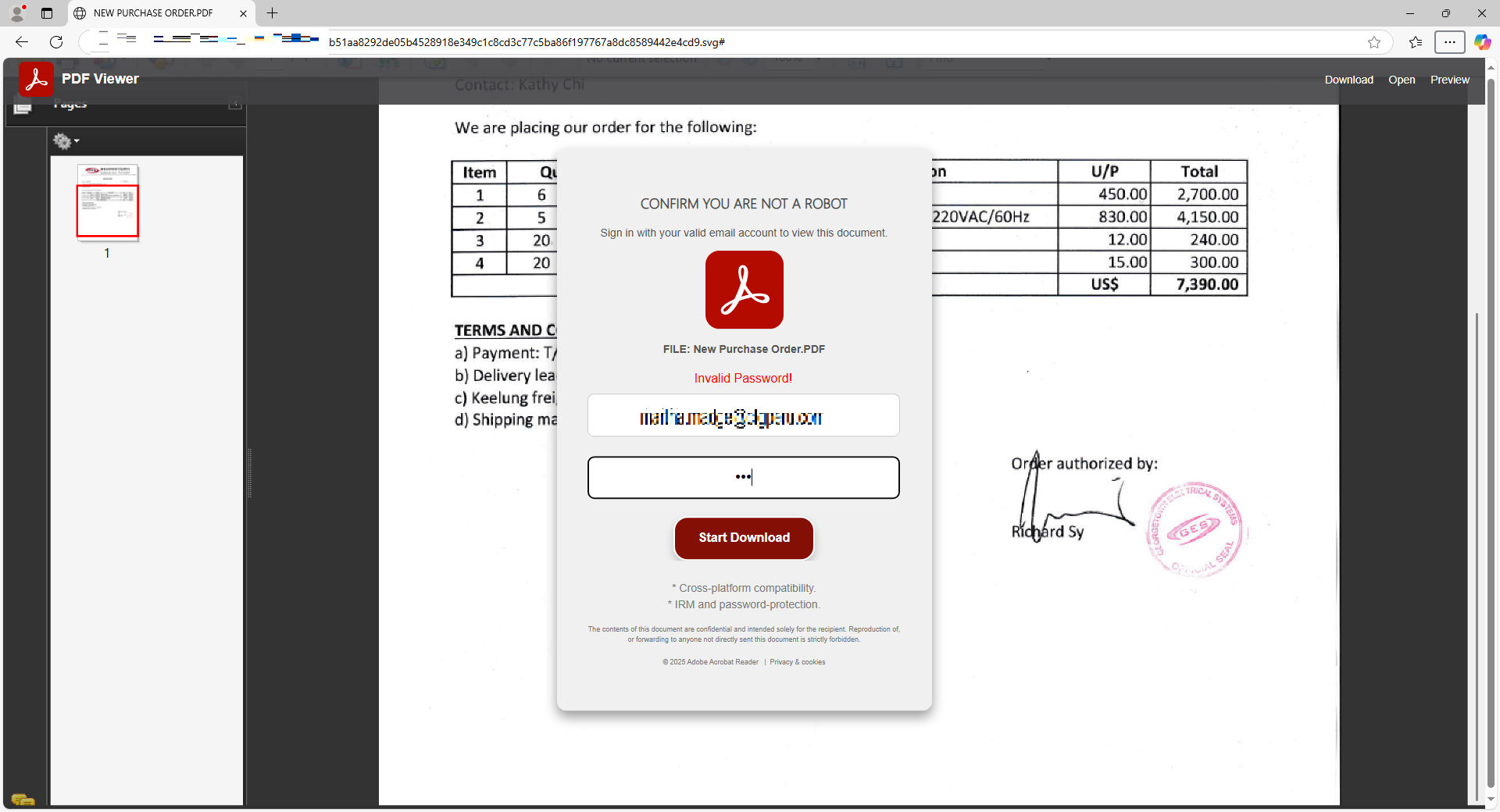
After the user clicks the ‘Download’ button and enters their credentials, the login details are sent to a remote server, resulting in an "Invalid Password!" message being displayed. The remote server, www.trektohimalayas.com, seems to be a compromised legitimate site.
We strongly advise our users to remain alert and cautious regarding any unsolicited emails and to refrain from sharing personal information, especially if the source is uncertain.
This threat was detected by SonicWall Capture ATP w/RTDMI.
IOCs
SHA256 of SVG files:
- b51aa8292de05b4528918e349c1c8cd3c77c5ba86f197767a8dc8589442e4cd9
- 094c90b00def187b86fe4f7f3af0c8662b54aa5345c33a77c9fb15280ec38216
- 06f00c681c2523a36e921fc4644a33b2621ae5213f428a7fa19bd60197b19f93
- 5d69acacaf8692a1df67ba280a2dded13249e49e61e50b7305276cc05a03a530
Network:
- hxxps://www[.]trektohimalayas[.]com/assets/next.php
Share This Article

An Article By
An Article By
Security News
Security News
