Hexamethy Ransomware Displays Scary Lock Screen During File Encryption

The Sonicwall Capture Labs threat research team has recently observed new ransomware named HEXAMETHYLCYCLOTRISILOXANE, or Hexamethy in short. This malware produces a scary cinematic display during the encryption process and flashes text stating, “No more files for you,” and “Your files are in hostage by the HEXAMETHYLCYCLOTRISILOXANE Ransomware." The threat actors demand 0.1 BTC, roughly $8400 USD at the time of writing, for a ransom payment. However, no operator contact information is provided for negotiation.
Infection Cycle
The malware uses the following icon:

Upon execution, files on the system are encrypted. Each encrypted file is given a “.HXAMTHY” extension.
During the encryption process, the following text flashes by in quick succession on the screen:
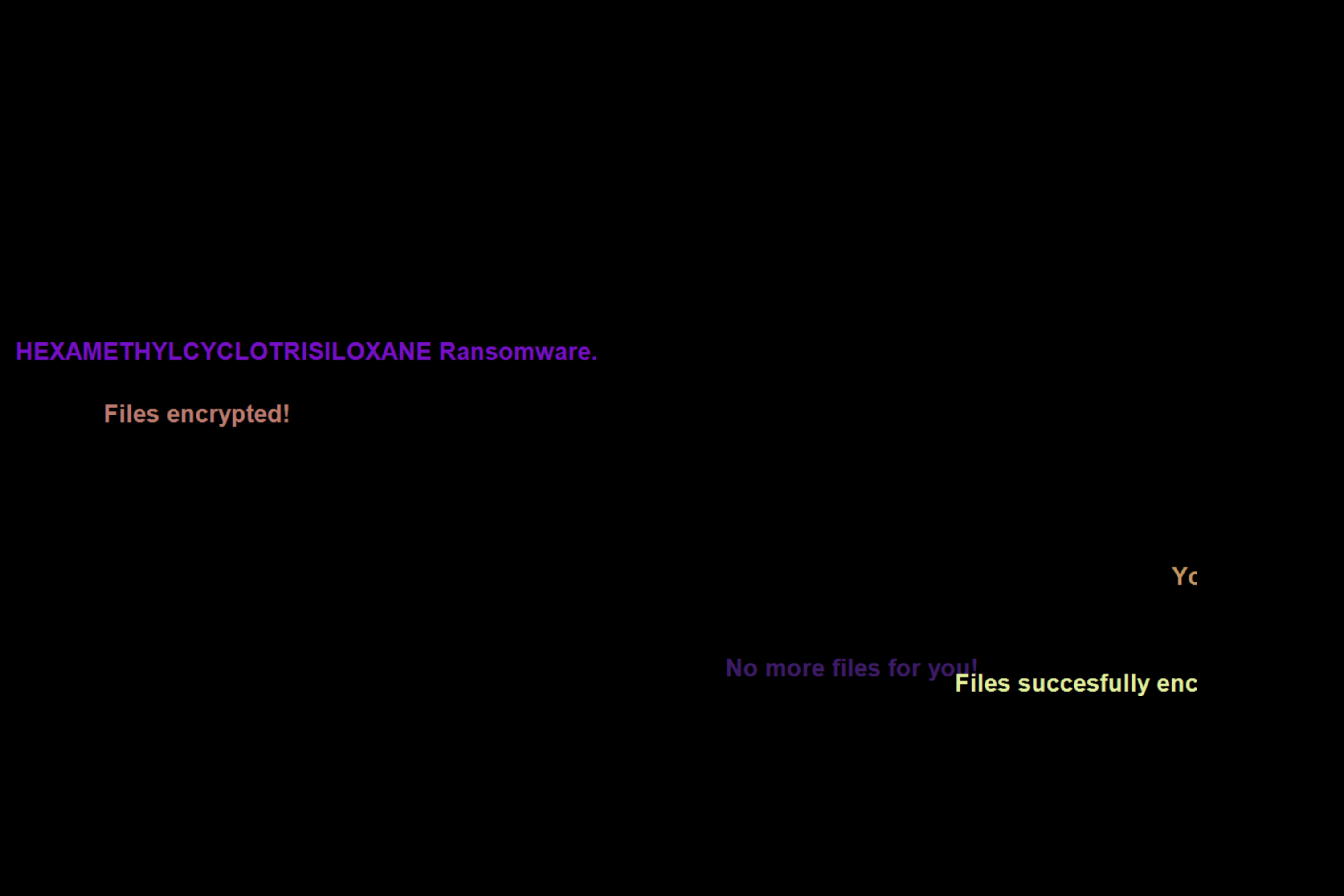
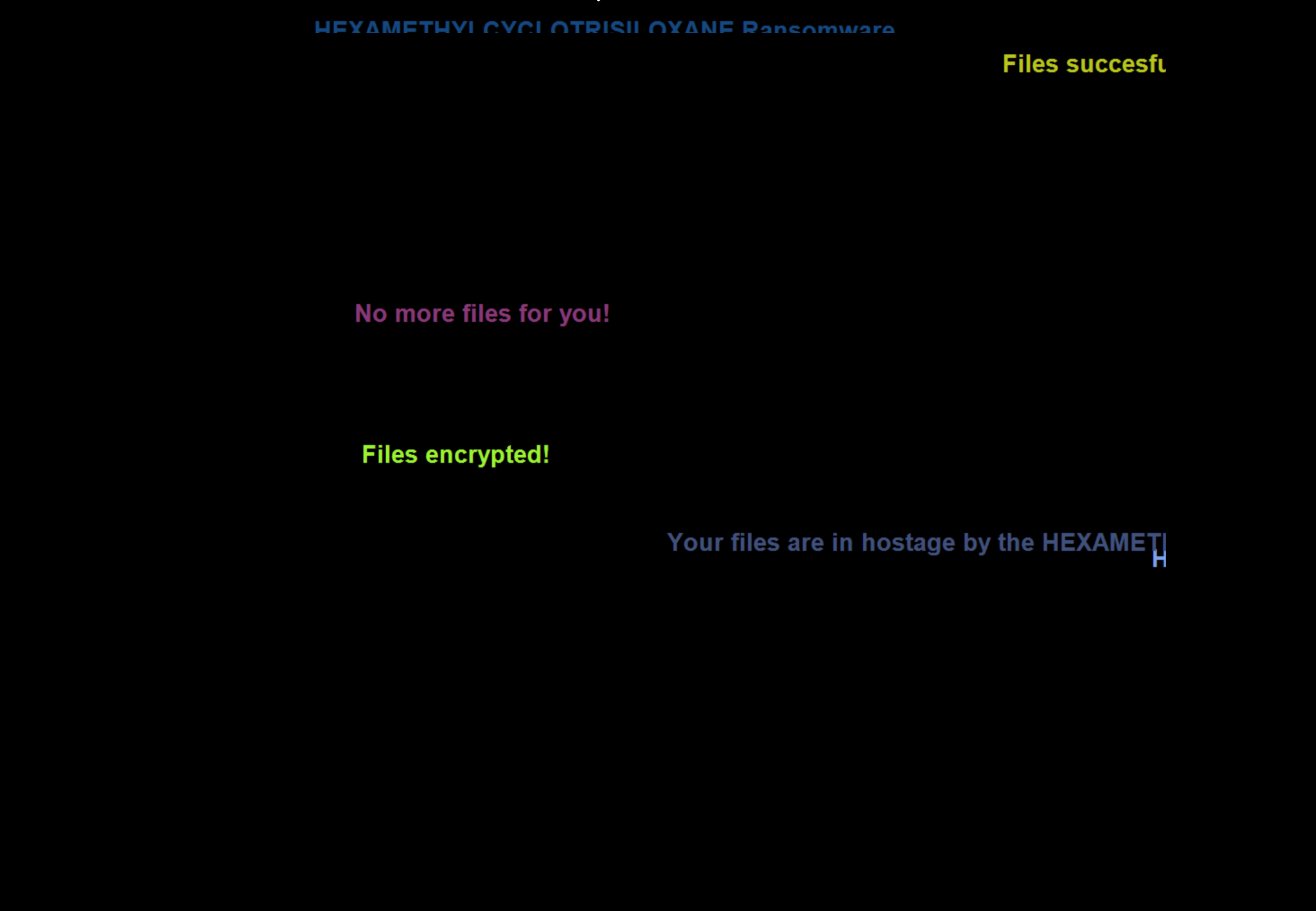
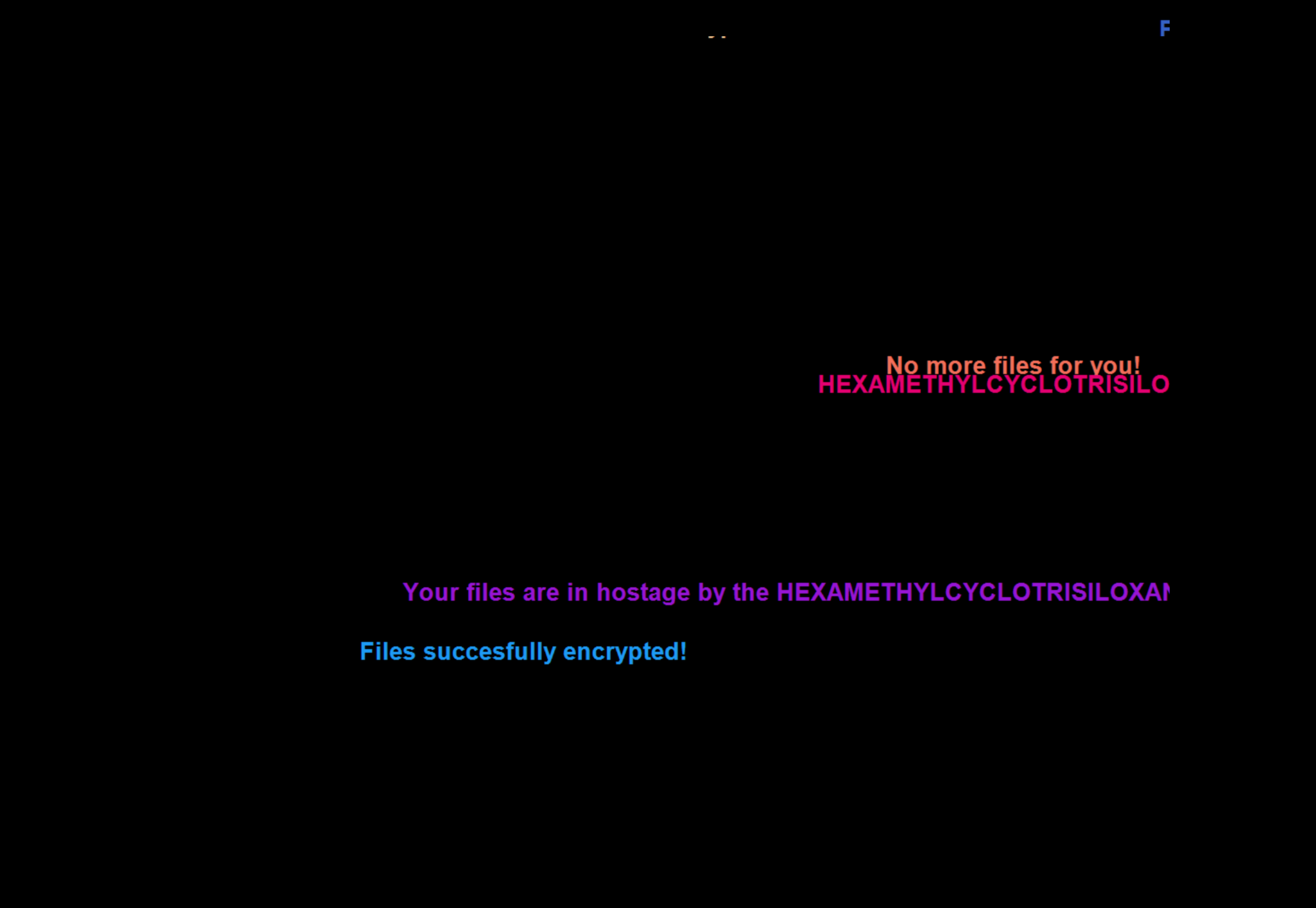
There is no conventional way to exit back to the desktop during this display.
After rebooting, the desktop background is changed:

Two files are now present on the desktop: “Hexamethy decryptor.exe” and “RAPIDOVERWRITER.exe”
“Hexamethy decryptor.exe” uses the following icon:

Running RAPIDOVERWRITER.exe leads to the following lock screen

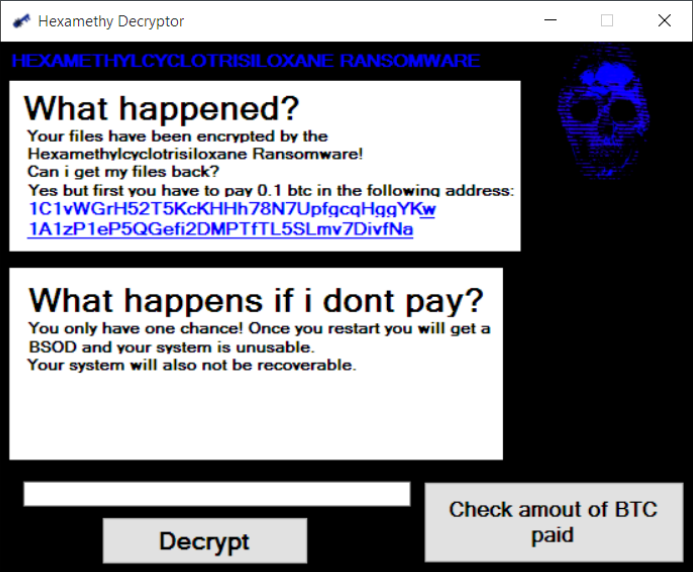
Running “Hexamethy decryptor.exe” brings up the following dialog:
After decompiling the code, we can see its intent to disable Task Manager:
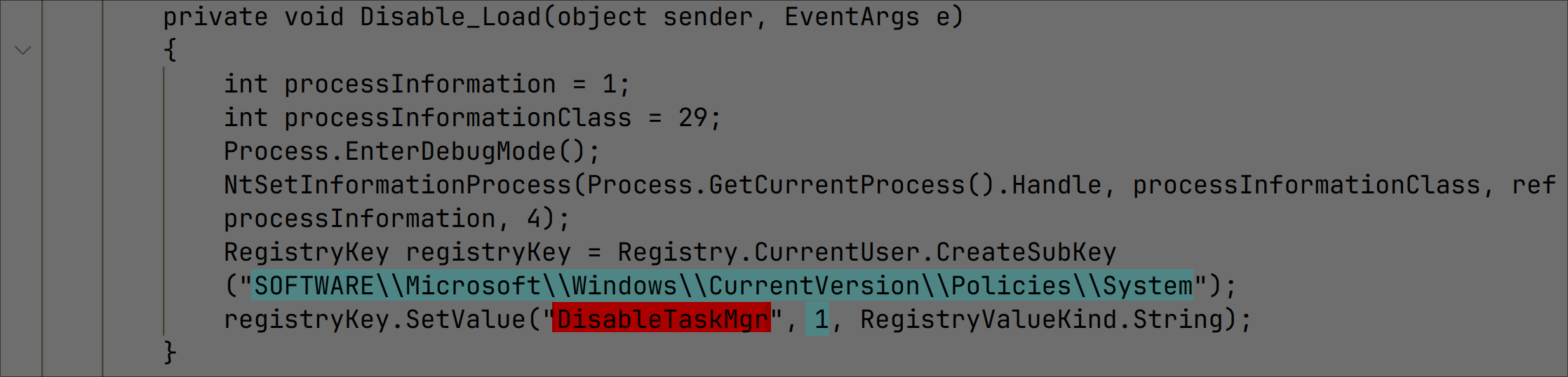
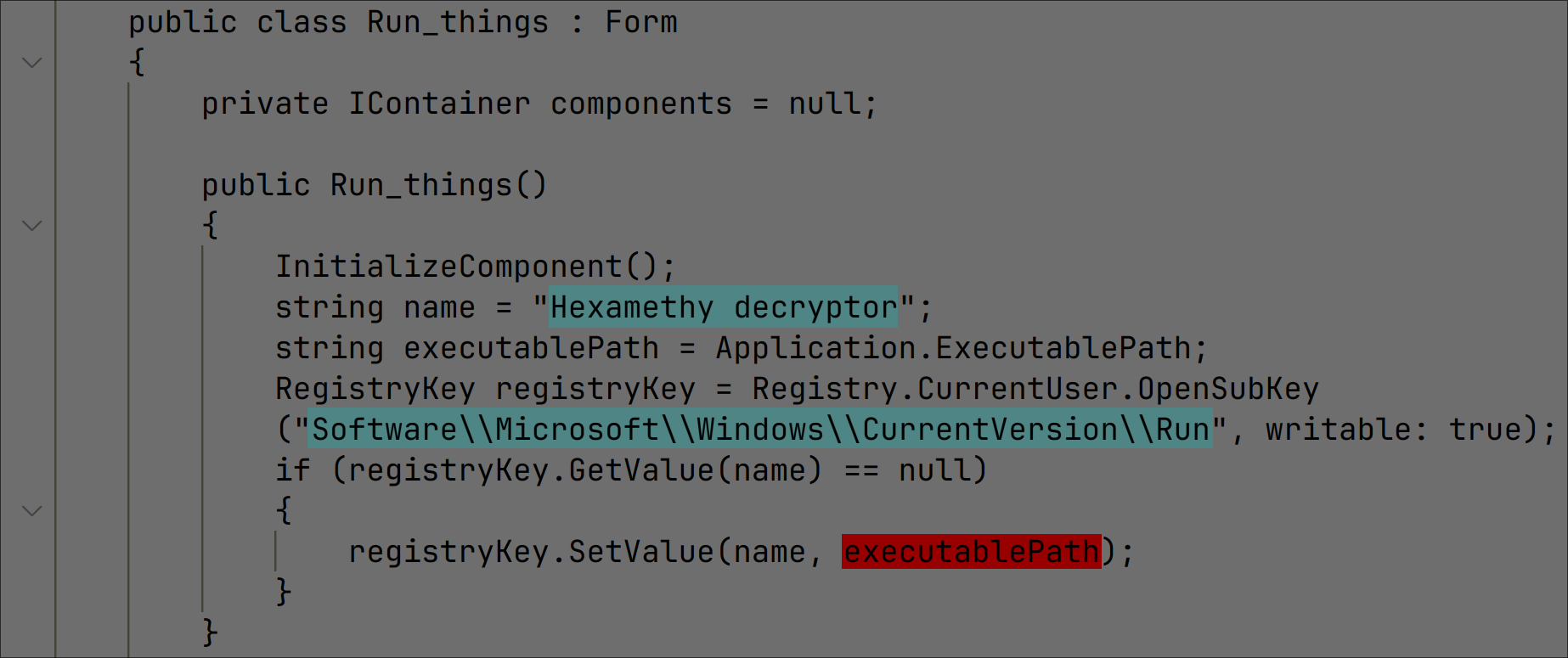
It sets itself up to run again after reboot:
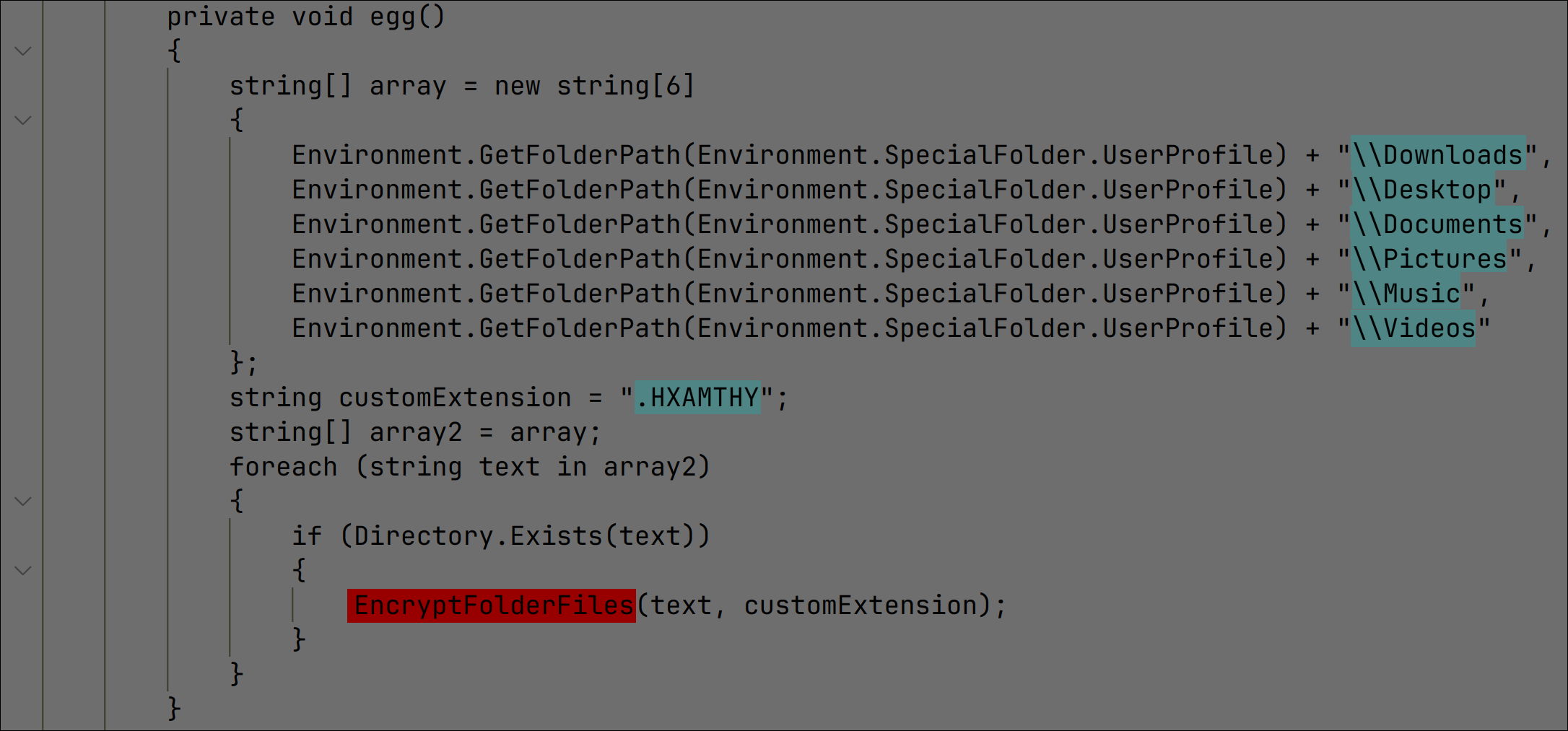
It contains a list of directories to target for encryption and the file extension to use for encrypted files:
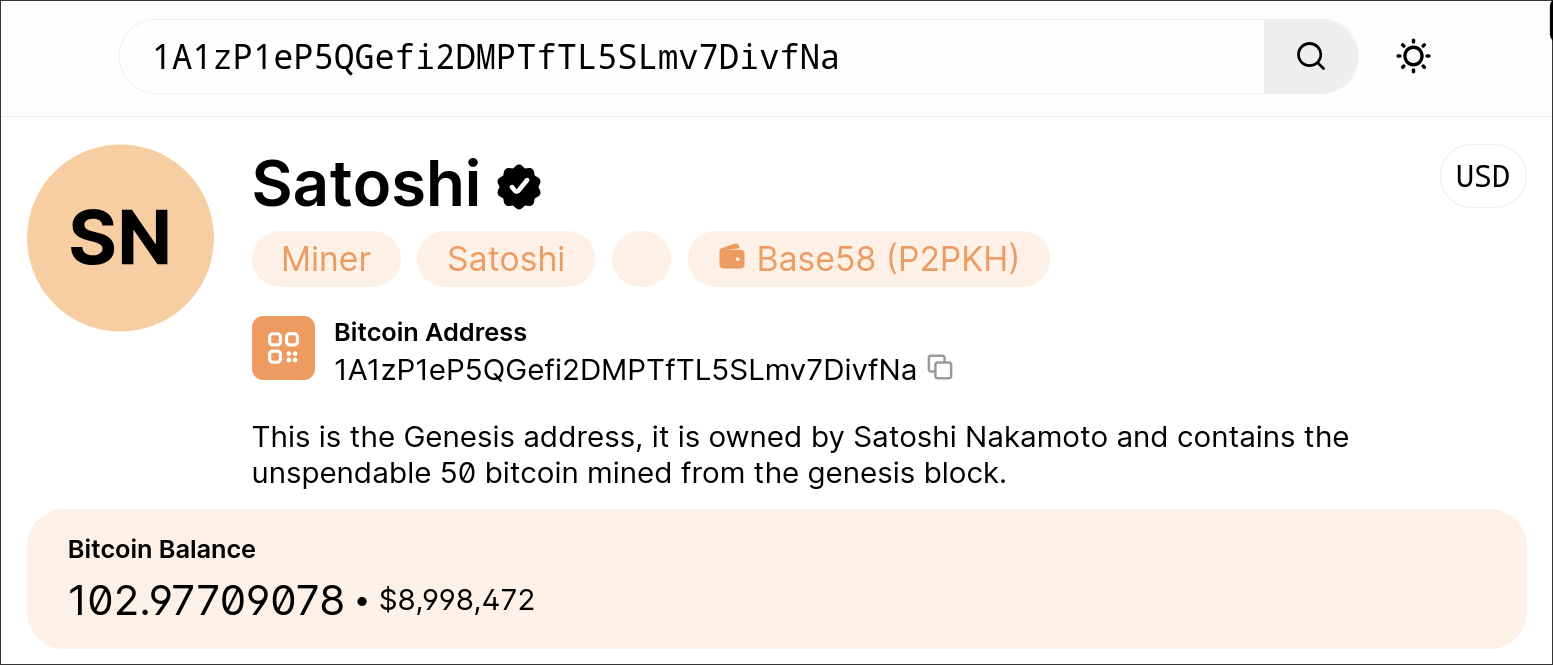
This variant of the malware points to the publically known Bitcoin address of Satoshi, the founder of Bitcoin. This is obviously not to be taken seriously and no Bitcoin should be deposited to this address as a ransom payment:
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Hexamethy.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News
