Critical Strapi Vulnerability Allows RCE via Server-Side Template Injection

Overview
SonicWall Capture Labs threat research team became aware of the threat CVE-2023-22621, assessed its impact and developed mitigation measures for this vulnerability.
CVE-2023-22621 is a high-severity vulnerability affecting Strapi versions 3.0.0 through 4.5.5. The flaw permits authenticated Server-Side Template Injection (SSTI), allowing a remote attacker with access to the Strapi admin panel to bypass validation checks and execute arbitrary code on the server. With a CVSS score of 7.2 (NIST), this vulnerability arises from improper neutralization of special elements in outputs used by downstream components (CWE-74). The Exploit Prediction Scoring System (EPSS) assigns it a 64.09% probability of exploitation within 30 days, placing it in the 98th percentile of vulnerabilities most likely to be exploited.
Although initial access to Strapi’s administrative interface requires valid credentials, the high exploitability rating (64.09% EPSS) underscores the practical risk posed by compromised or weak administrative accounts, which attackers frequently target. Additionally, vulnerabilities such as CVE-2023-22893 an Authentication Bypass affecting the AWS Cognito Login Provider in Strapi versions ≤ 4.5.6 amplify these risks by potentially enabling unauthorized access to administrative interfaces, thereby facilitating attacks like CVE-2023-22621. This exploitation demonstrates how multiple chained vulnerabilities, such as regex validation bypass combined with unrestricted lodash template rendering, can culminate in critical security compromises.
Administrators are strongly advised to update promptly to version 4.5.6 or later and consult Strapi’s official security disclosure and release notes for comprehensive remediation guidance.
Technical Overview
The root cause of CVE-2023-22621 originates from Strapi’s integration of the lodash template engine within its email template processing. This implementation inadvertently allowed JavaScript code embedded in email templates to be rendered and executed due to insufficient input sanitization and inadequate delimiter controls. Specifically, the sendTemplatedEmail function dynamically processes email templates using lodash's _.template() method (highlighted on line 32 in Figure 1), without explicitly restricting the template evaluation capabilities. Consequently, malicious JavaScript commands embedded in email templates could be executed directly on the server.
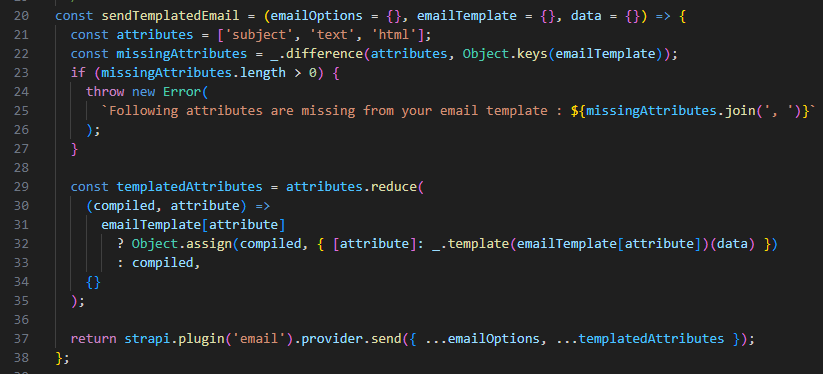
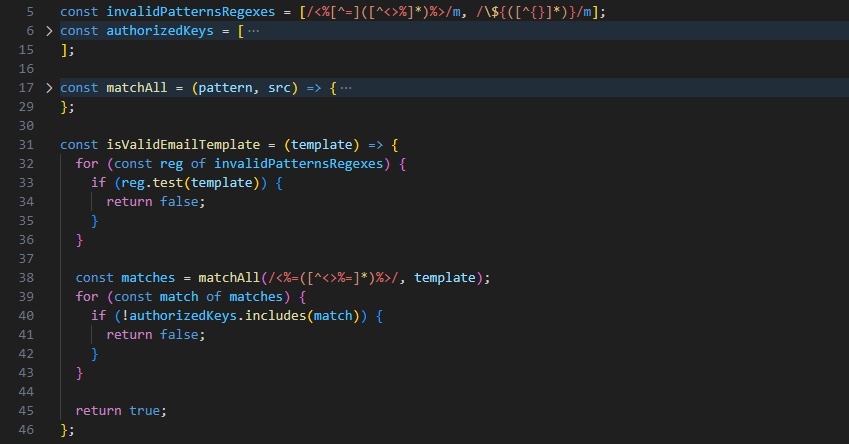
Moreover, the vulnerability was intensified by deficiencies within the email template validation function, isValidEmailTemplate. As depicted in Figure 2, this function employed regular expressions (invalidPatternsRegexes on line 5 and validation logic beginning on line 33) intended to detect and reject malicious payloads in email templates. These regex checks inadequately accounted for special characters such as <, >, %, and =, allowing attackers to craft payloads that bypassed validation entirely. Thus, malicious inputs easily reached the lodash template renderer, significantly simplifying and enhancing the reliability of attacks.
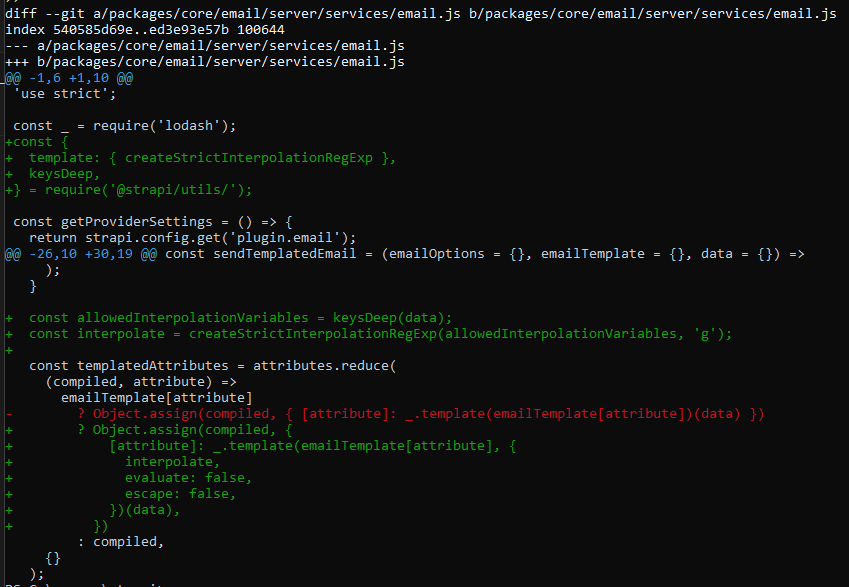
In response, Strapi’s security team enhanced the validation mechanism by introducing rigorous regex patterns and explicitly disabling lodash’s hazardous functionalities. Specifically, the patch employs dynamically generated interpolation rules through the newly introduced createStrictInterpolationRegExp function. This enhancement limits template rendering strictly to predefined allowable keys derived from supplied data. Additionally, the potentially exploitable evaluate and escape features within lodash's template processing have been explicitly disabled (evaluate: false, escape: false), thereby strengthening defenses against injection attacks. These combined modifications effectively prevent malicious inputs from being executed as JavaScript.
Triggering the Vulnerability
Triggering CVE-2023-22621 involves exploiting weaknesses in Strapi's email template processing functionality. An authenticated attacker with admin panel access can abuse insufficient input validation mechanisms to inject malicious payloads into email templates. The vulnerability occurs when specifically crafted payloads evade regex validation, reaching the lodash template renderer, leading to server-side JavaScript execution. The following conditions outline the necessary steps to trigger this vulnerability:
- Obtain Authenticated Access:
The attacker first gains authenticated administrative access to the Strapi admin panel. - Navigate to Email Templates:
Within the admin panel, the attacker accesses the "Users & Permissions" plugin and navigates to the email template configuration page. - Inject Malicious Template Payload:
The attacker crafts and inserts a malicious lodash template payload specifically designed to bypass validation checks into an email template (e.g., email confirmation or password reset). - Save and Activate Malicious Template:
The attacker saves the injected payload, successfully bypassing validation due to regex vulnerabilities. - Trigger Template Rendering:
The attacker initiates actions (e.g., user registration or password reset) causing Strapi to render and execute the compromised email template, resulting in arbitrary JavaScript code execution on the server.
Exploitation
Exploitation of CVE-2023-22621 hinges upon the attacker’s ability to bypass Strapi's template validation logic by leveraging specific regex parsing weaknesses. After authenticating to Strapi's administrative interface, an attacker carefully constructs and submits a malicious Server-Side Template Injection (SSTI) payload into the email template fields. This payload, deliberately engineered with strategically placed special characters and inline JavaScript, evades regex-based detection checks as previously detailed, effectively circumventing the validation process. Once saved, the malicious template awaits a triggering event such as a user registration or password reset action—which initiates the rendering of the compromised template, thereby activating the embedded JavaScript code on the server. At this point, the attacker attains remote code execution, gaining the ability to issue arbitrary system commands and potentially compromise the server further.
Figure 4: Video demonstration showcasing the injection and subsequent execution.
Leveraging administrative credentials in tandem with a meticulously crafted payload underscores how even minor oversights in regex-based validation can precipitate significant security breaches. This attack pathway highlights the profound importance of end-to-end input sanitization and illustrates how seemingly trivial parsing flaws in high-stakes components can escalate to full remote code execution. As such, thorough testing and rigorous validation remain paramount in preventing these vulnerabilities from being weaponized.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 20857 “Strapi Server Side Template Injection”
Remediation Recommendations
The risks posed by CVE-2023-22621 can be mitigated or eliminated by:
- Promptly upgrading Strapi to version 4.5.6 or later, as recommended in the official security advisory.
- Utilizing up-to-date IPS signatures to detect and block malicious payloads targeting this vulnerability.
- Restricting administrative panel access strictly to authorized personnel, employing strong authentication mechanisms and role-based access controls.
- Conducting regular security reviews and audits of template-rendering code and input validation logic to proactively identify similar injection vulnerabilities.
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News
