Critical CrushFTP Authentication Bypass (CVE-2025-31161) Exposes Servers to Remote Attacks

Overview
The SonicWall Capture Labs threat research team became aware of an authentication bypass vulnerability in CrushFTP Servers, assessed its impact, and developed mitigation measures. CrushFTP is a resourceful enterprise-grade file transfer application used widely among organizations. It also supports multi-protocols for data exchange among systems and users with S3-compatible API access.
CrushFTP versions 10.0.0 through 10.8.3 and 11.0.0 through 11.3.0 allow unauthenticated attackers to bypass authentication and gain unauthorized access due to parameter overloading in lookup_user_pass boolean flag. This overloading of logic allows attackers to authenticate without providing any password—simply by crafting an HTTP request with Credential=username/ header and skipping the tilde (~) character, which bypasses the password. With a CVSS score of 9.8, CVE-2025-31161 can lead to severe security implications due to its low complexity and publicly available PoCs. Therefore, users are strongly encouraged to upgrade their instances to the latest fixed version, as the advisory outlines.
Technical Overview
CrushFTP is accessed with specific credentials, and authentication plays a significant role. The vulnerable versions of CrushFTP implement S3 authentication for signing. Clients must include an Authorization header along with the authentication cookie to access CrushFTP.
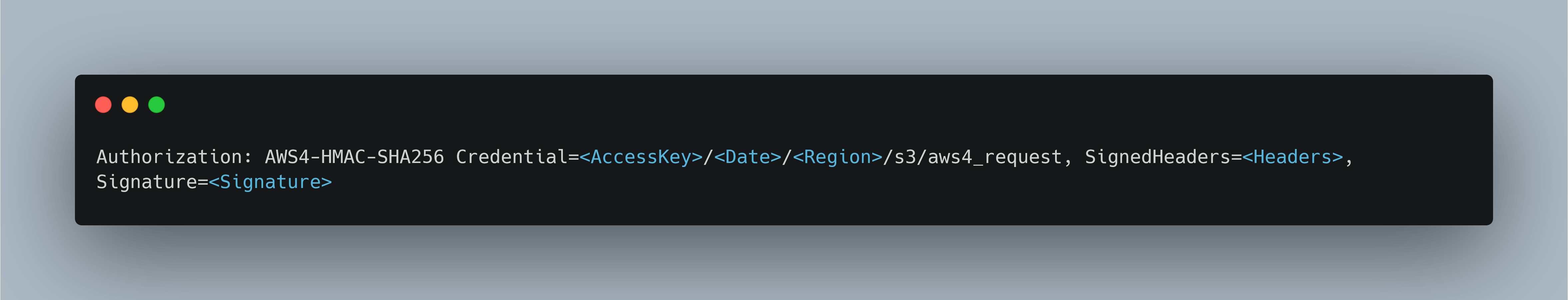
The user is identified and verified using the “Credential” field in the Authorization header. The last parameter, “Signature,” is bypassed in the vulnerable versions of CrushFTP.
To access any CrushFTP, it must possess a CrushAuth cookie. Even though being random, the format or syntax of this cookie is particular, with 44 alphanumeric characters patterned such that the last 4 characters must match the c2f value. In the context of CrushFTP, the c2f parameter is the last 4 characters of the CrushAuth cookie, which is used for authentication in API requests. For example, if the CrushAuth cookie is 1049161285377_jZiGxXHpBrrLsAEJmBfAaiFsImLZ9606, the c2f parameter should be 9606. In general,
Cookie: CrushAuth={{string_1}}_{{string_2}}{{string_3}}; currentAuth={{string_3}}
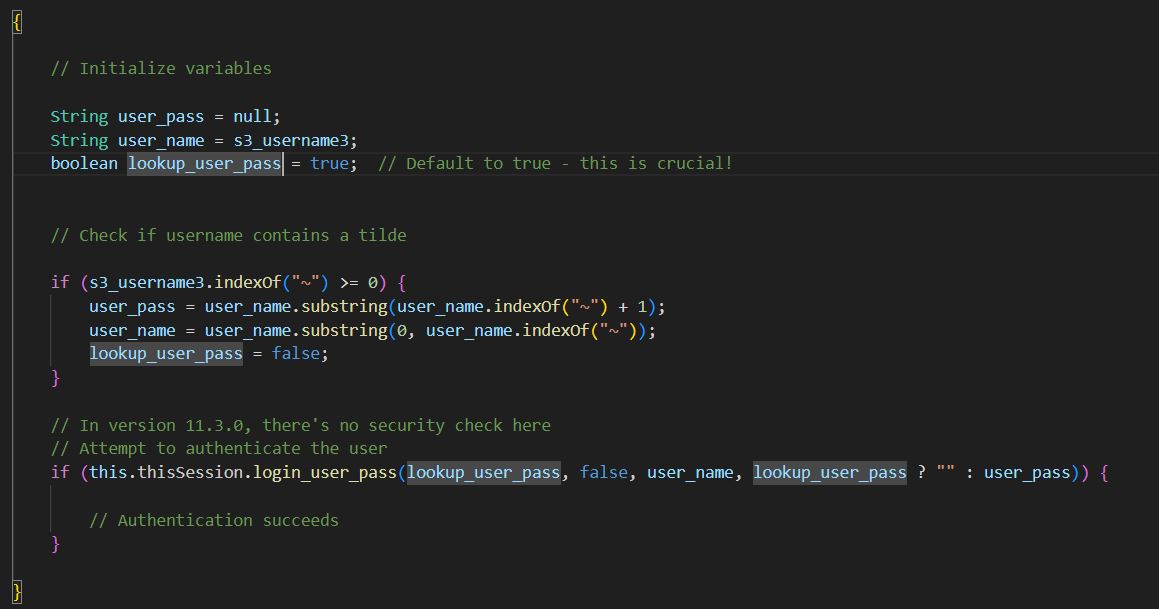
Furthermore, as shown in Figure 2, the lookup_user_pass flag’s default setting within ServerSessionHTTP.java is a critical issue for CVE-2025-31161. While parsing the username, the Boolean flag is set to true, where the authentication bypass begins. This flag was designed to determine whether to fetch a password from storage or use one provided in the request. Figure 2 shows a snippet of loginCheckHeaderAuth() in ServerSes sionHTTP.java.
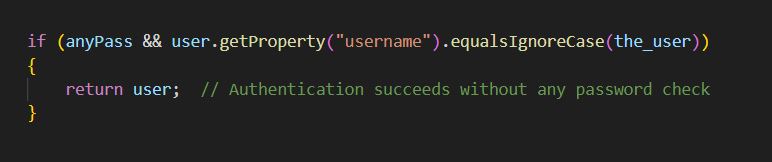
Finally, password verification is bypassed as the intended logic is implemented wrongly in vulnerable versions. Under UserTools.java, if no tilde (~) is used to pass the username, which occurs in S3 authentication by default, password verification is bypassed, as seen in Figure 3.
If the DMZ function is enabled, isolating the public-facing services from the backend infrastructure, it addresses this issue by implementing the interaction between DMZ and Internal, which is the HTTP protocol (inside an SSL connection).
Triggering the Vulnerability
Leveraging the vulnerability mentioned above requires the attacker to meet the below prerequisites.
- A vulnerable version of CrushFTP server with network access.
- A well-formed S3-style Authorization header.
- Authorization: AWS4-HMAC-SHA256 Credential=<username>.
- A CrushAuth cookie with a specific 44-character format.
- A c2f parameter matching the final 4 characters of the cookie.
By combining the above factors and crafting a malicious HTTP request to victim CrushFTP instances, the attacker can access files, upload malicious content, create admin users, and gain complete access to the server.
Exploitation
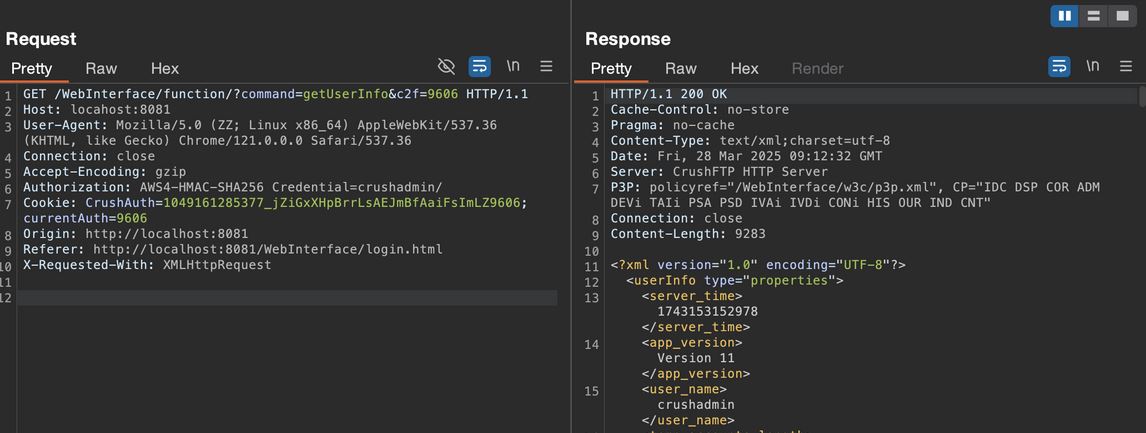
Exploitation of this vulnerability allows a remote threat actor to execute arbitrary commands on the affected server. In the sample malicious packet in Figure 4, note that the c2f value matches the last four digits of the CrushAuth Cookie.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 20878 - CrushFTP Authentication Bypass
Remediation Recommendations
We had not observed any exploit attempts in the wild at the time of publishing this article. However, given the significance of the CrushFTP servers in an organization's network infrastructure, users are strongly encouraged to update their instances to the latest version, as mentioned in the vendor advisory.
Relevant Links
- Vendor advisory
- CISA bulletins
- https://github.com/projectdiscovery/nuclei-templates-labs/tree/main/http/cves/2025/CVE-2025-2825
- https://projectdiscovery.io/blog/crushftp-authentication-bypass#proof-of-concept
- https://github.com/MarkusMcNugen/docker-CrushFTP
- https://www.crushftp.com/crush11wiki/Wiki.jsp?page=DMZ
Share This Article

An Article By
An Article By
Dhiren Vaghela
Dhiren Vaghela
Dhiren Vaghela has over a decade of experience in the IPS domain, with a strong focus on defensive security. His expertise lies in identifying, analyzing and mitigating vulnerabilities. Dhiren is well-versed in content-based signature writing, scanner-based alert generation and technical blog writing. By leveraging emerging technologies, he has developed numerous IPS signatures across various protocols. Known for his exceptional signature writing skills and collaborative team spirit, Dhiren is a valuable asset in the field of cybersecurity.
