Critical Apache Tomcat RCE Vulnerability (CVE-2025-24813) Under Active Exploitation

Overview
The SonicWall Capture Labs threat research team became aware of the threat CVE-2025-24813, assessed its impact and developed mitigation measures for the vulnerability.
This critical vulnerability affects Apache Tomcat versions 9.0.0.M1 through 9.0.98, 10.1.0-M1 through 10.1.34, and 11.0.0-M1 through 11.0.2. Apache Tomcat is an open-source web server and servlet container used to deploy and run Java-based web applications. It is widely adopted in enterprise environments due to its lightweight design, reliability, and strong community support. The issue, assigned CVE-2025-24813 with a CVSS score of 9.8, stems from improper handling of file paths during partial PUT requests, which can potentially lead to remote code execution (RCE), information disclosure, or unauthorized modification of uploaded files. The best mitigation is to upgrade to a fixed version of Apache Tomcat—11.0.3, 10.1.35, or 9.0.99. While it’s likely that the vulnerable configuration is relatively uncommon, proof of concept code has been released and there have been reports of known exploitation in the wild.
Technical Overview
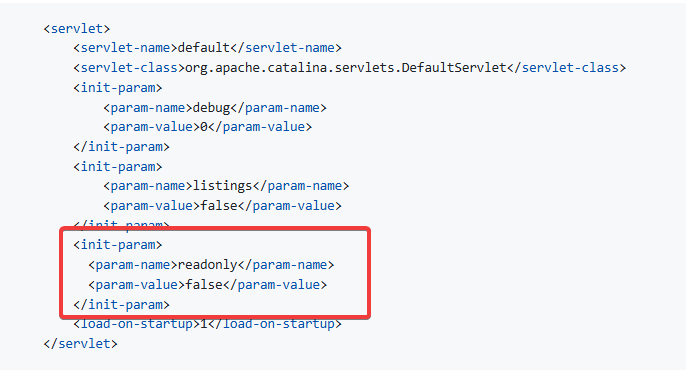
The vulnerability arises due to Apache Tomcat’s mishandling of file paths during partial PUT requests. When the default servlet is configured with write permissions (disabled by default), as seen in Figure 1, and partial PUT support is enabled (enabled by default), attackers can exploit this flaw. The vulnerability is tied to a behavior where partial PUT requests create temporary files whose names are derived by replacing path separators with dots. The vulnerability becomes especially dangerous when the application’s logic later performs operations based on those files, such as during session persistence operations. If the uploaded file is then moved, renamed, or otherwise treated as a legitimate resource by application logic, the attacker can abuse this process to escalate impact beyond simple file manipulation.
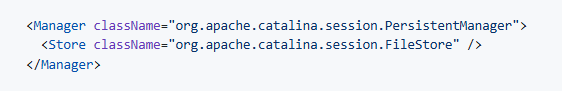
In scenarios where remote code execution is targeted, successful exploitation also typically requires Apache Tomcat's file-based session persistence to be enabled, as this allows attackers to upload and later deserialize malicious session files. This is also not enabled by default.
Triggering the Vulnerability
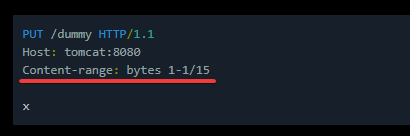
To trigger CVE-2025-24813, an attacker can upload a maliciously crafted file via a partial PUT request. A key element in enabling this behavior is using the 'Content-Range' HTTP header in the PUT request. This is what triggers a partial file upload handling by Tomcat. This header defines the specific byte range of the file being uploaded, allowing the server to create or append to temporary files. Figure 3 shows an example of this malicious request as seen in the original blog written by Lingua Diabolis. Here the file “/dummy” will be written as “.dummy” to the file system with the content of “X”.
Exploitation
Successful exploitation of this vulnerability can lead to:
Remote Code Execution: If the application uses Tomcat’s file-based session persistence and includes a deserialization-prone library, an attacker may upload a crafted session file and trigger its deserialization.
Information Disclosure: If an attacker can guess filenames and the server configuration allows access, sensitive data can be exposed.
Data Corruption: Malicious content may be inserted into existing files, compromising data integrity.
Proof-of-concept exploit code is publicly available, and exploitation attempts have been observed in the wild.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
IPS: 20839 Apache Tomcat Path Equivalence RCE
Remediation Recommendations
To mitigate risks from CVE-2025-24813:
Upgrade Apache Tomcat to versions 11.0.3, 10.1.35, or 9.0.99.
Disable Write Permissions for the default servlet by setting the readonly attribute to true in conf/web.xml.
Disable Partial PUT Support by setting the allowPartialPut parameter to false in conf/web.xml.
Avoid File-Based Session Persistence unless absolutely necessary.
Utilizing up-to-date IPS signatures to detect and block malicious payloads targeting this vulnerability.
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News
