Debug build of Jigsaw Ransomware contains SMTP email credentials

The SonicWall Capture Labs Threat Research Team observed reports of a new version of the Jigsaw ransomware. The version analysed here appears to be an early debug build and sports a new interface, a significant departure from interfaces using clown images in previous versions. As this is a test version of the malware, no encryption actually takes place.
Infection Cycle:
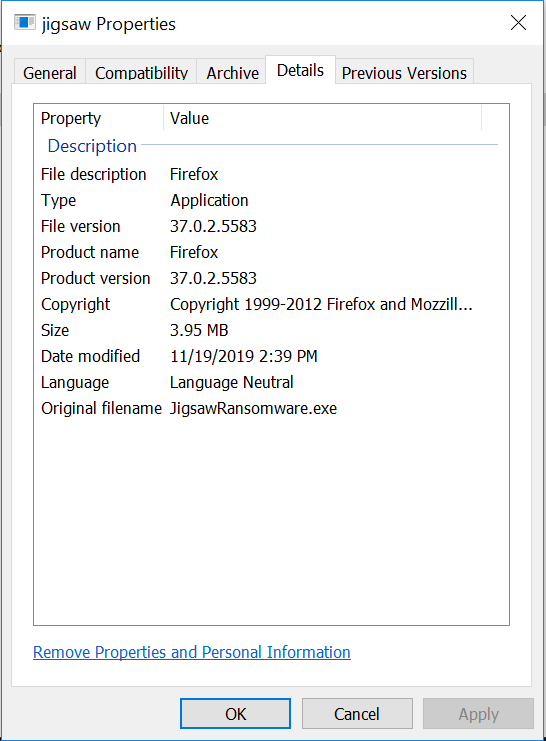
The malware exeutable file contains the following metadata:
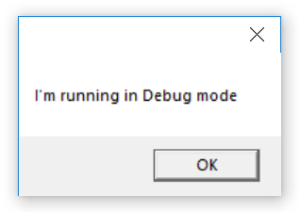
Upon execution it displays the following messagebox:
It brings up the following dialog:
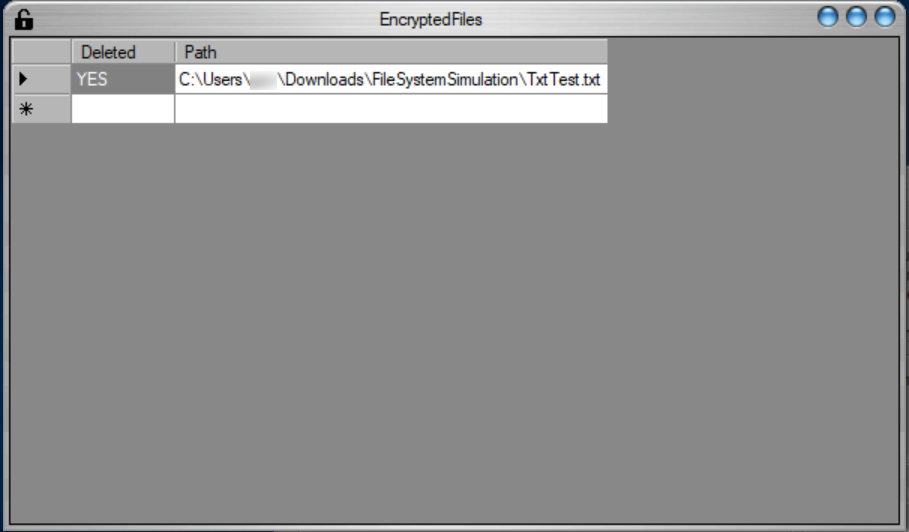
The "View encrypted files" button brings up the following page:
The following files are added to the system:
- %APPDATA%\SkinSoft\VisualStyler\2.4.59444.6\x86\ssapihook.dll
- {run location}\EncryptedFileList.txt
- {run location}\FileSystemSimulation\NotTxtTest.nottxt
- {run location}\FileSystemSimulation\TxtTest.txt.die (empty file)
- {run location}\Newtonsoft.Json.dll
- {run location}\SkinSoft.VisualStyler.dll
NotTxtTest.nottxt contains the following text:
I am NOT a txt test.
EncryptedFileList.txt contains the following text:
{run location}\FileSystemSimulation\TxtTest.txt
Nothing is actually encrypted on the system. Presumably, this is because it is a debug version.
The malware executable file contains the following string:
- C:\Users\Moises\Desktop\jigsawransomware2019-master\JigsawRansomware\obj\Debug\JigsawRansomware.pdb
The malware makes the following DNS requests:
- hostas8.cf
- google-analytics.com
- ip-api.com
- osdsoft.com
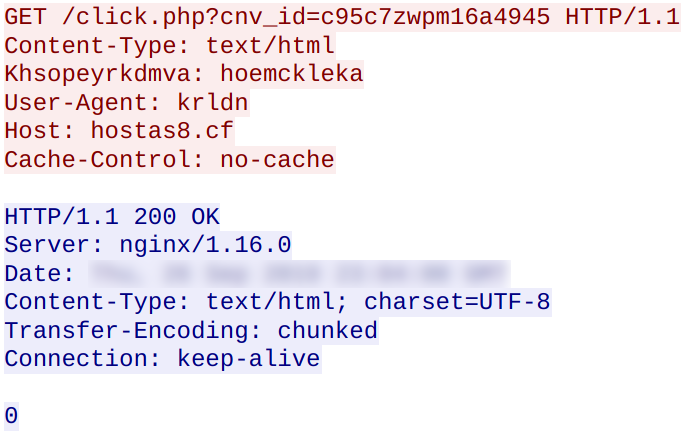
The following network traffic was observed between the malware and the hosts listed above:
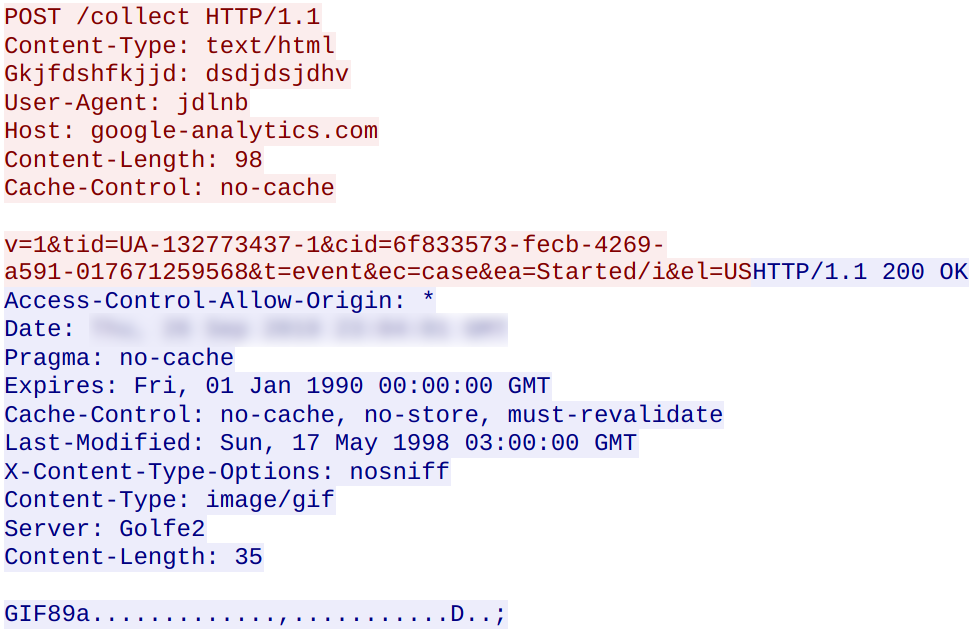
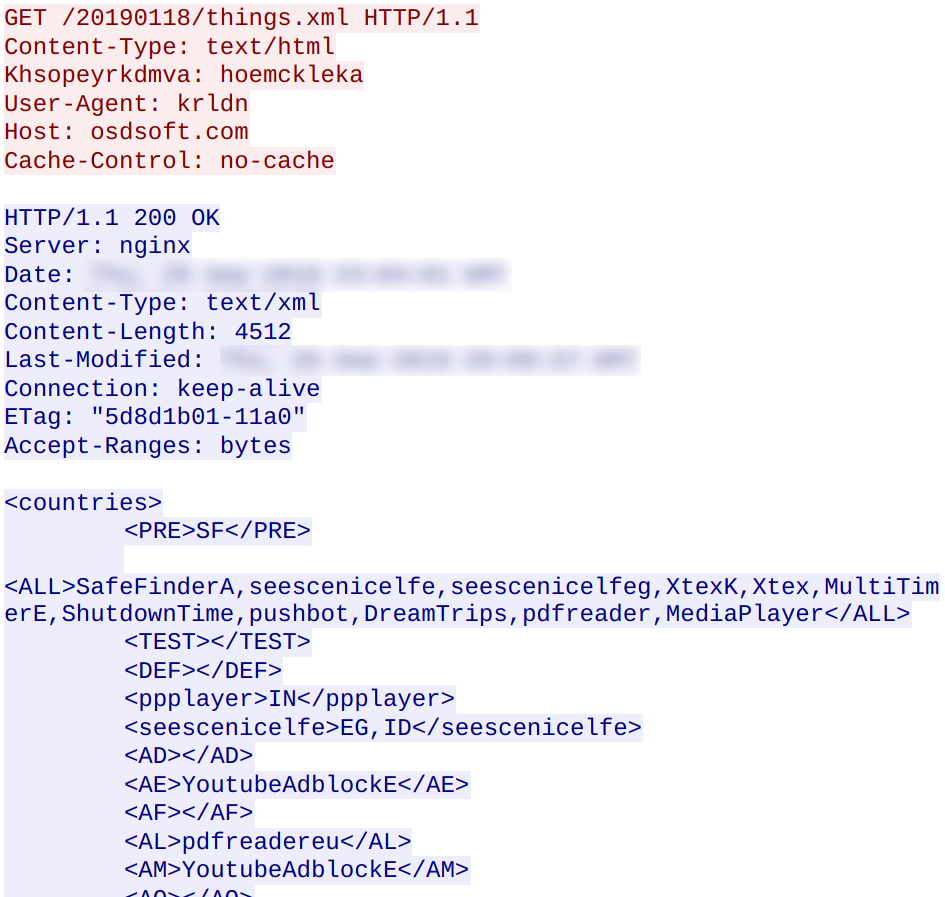
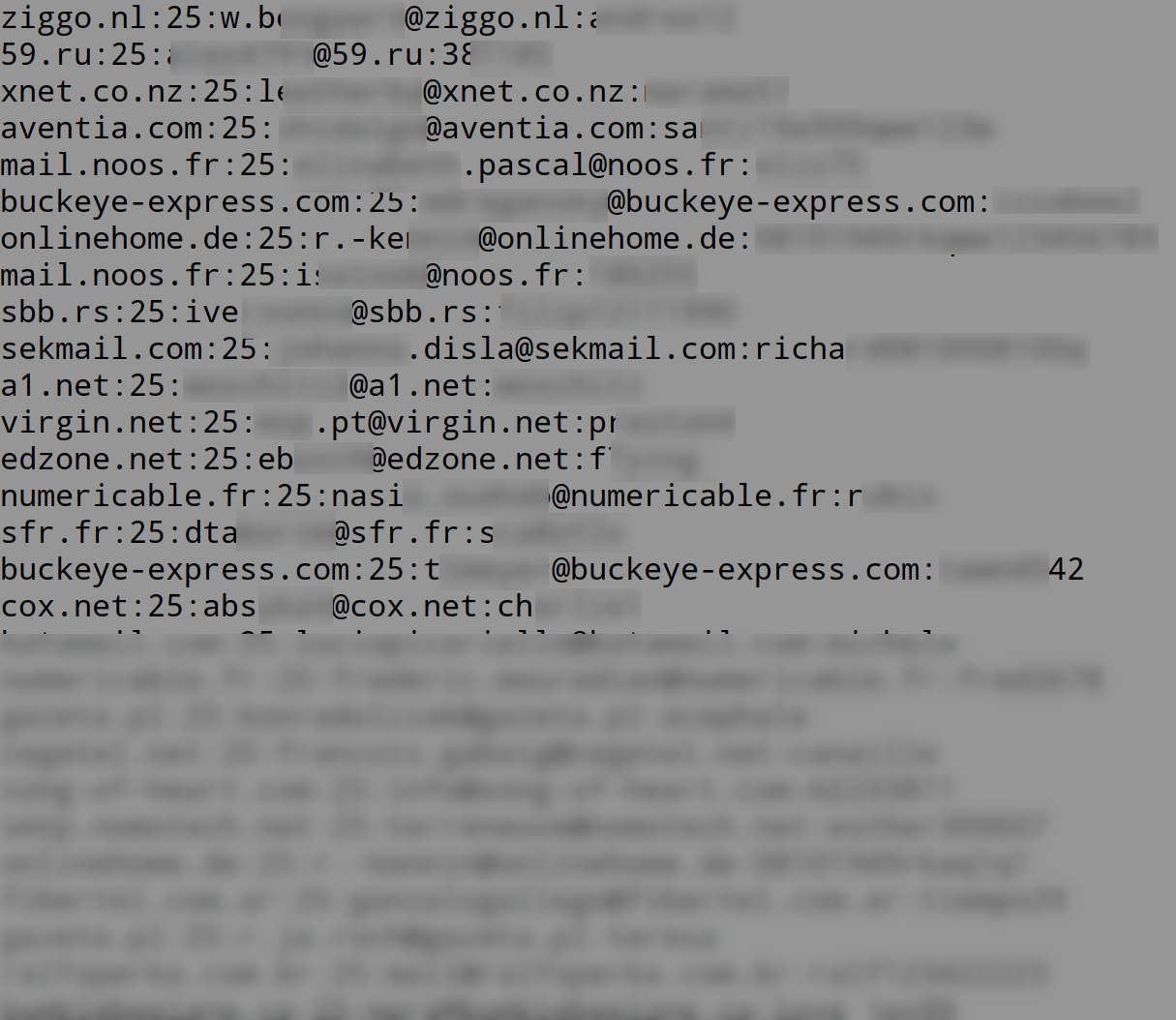
A further look into the executable file reveals credentials for 1455 SMTP email accounts:
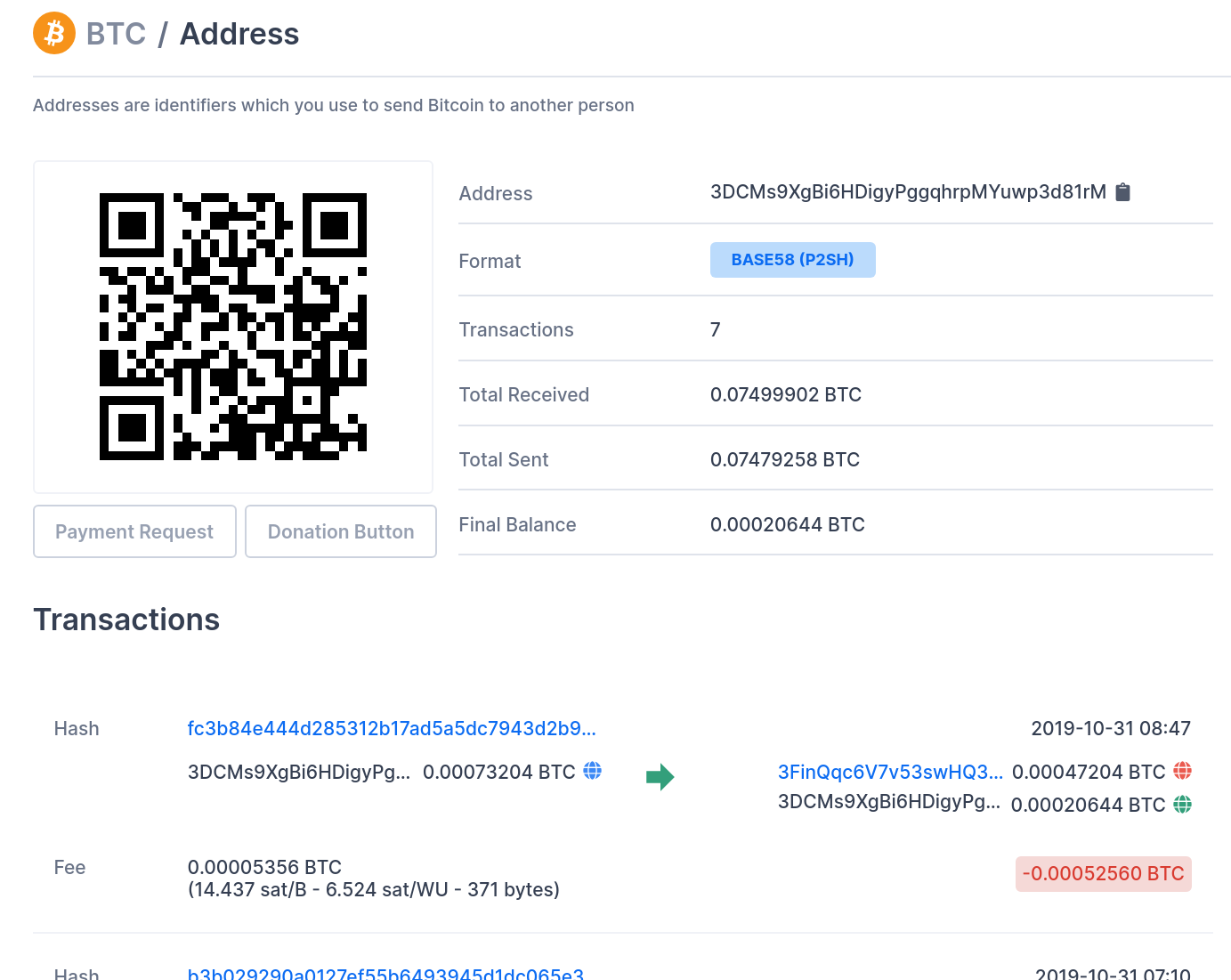
The BTC address (3DCMs9XgBi6HDigyPggqhrpMYuwp3d81rM) has some transaction history. However, it is not certain whether or not the transactions are directly related to ransom payments:
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Jigsaw.RSM_26 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News