-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
The log shows "Connection Timed Out"



Description
Logs such as a connection cache entry timed out, Connection has been dropped are very common for TCP connections. This is due to inactivity of the session. The default TCP timeout setting for a rule is 15 minutes.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
You can extend the timeout setting on specific rules for applications that experience long idle times, such as Citrix or MS Terminal Server.
- Login to the SonicWall management interface.
- Go to Policy| Rules and Policies | Access Rules, edit the appropriate rule by clicking the edit icon.
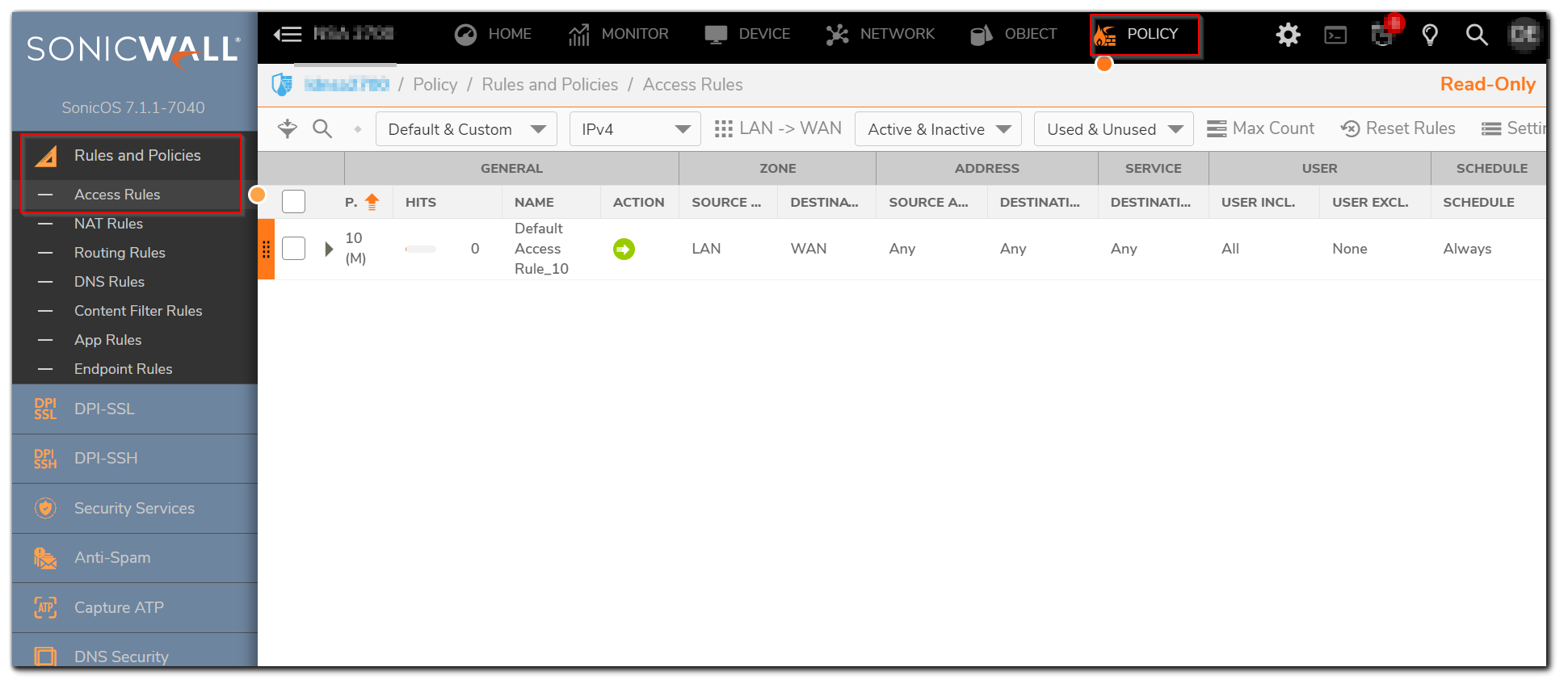
- Click on Users & TCP/UDP tab.
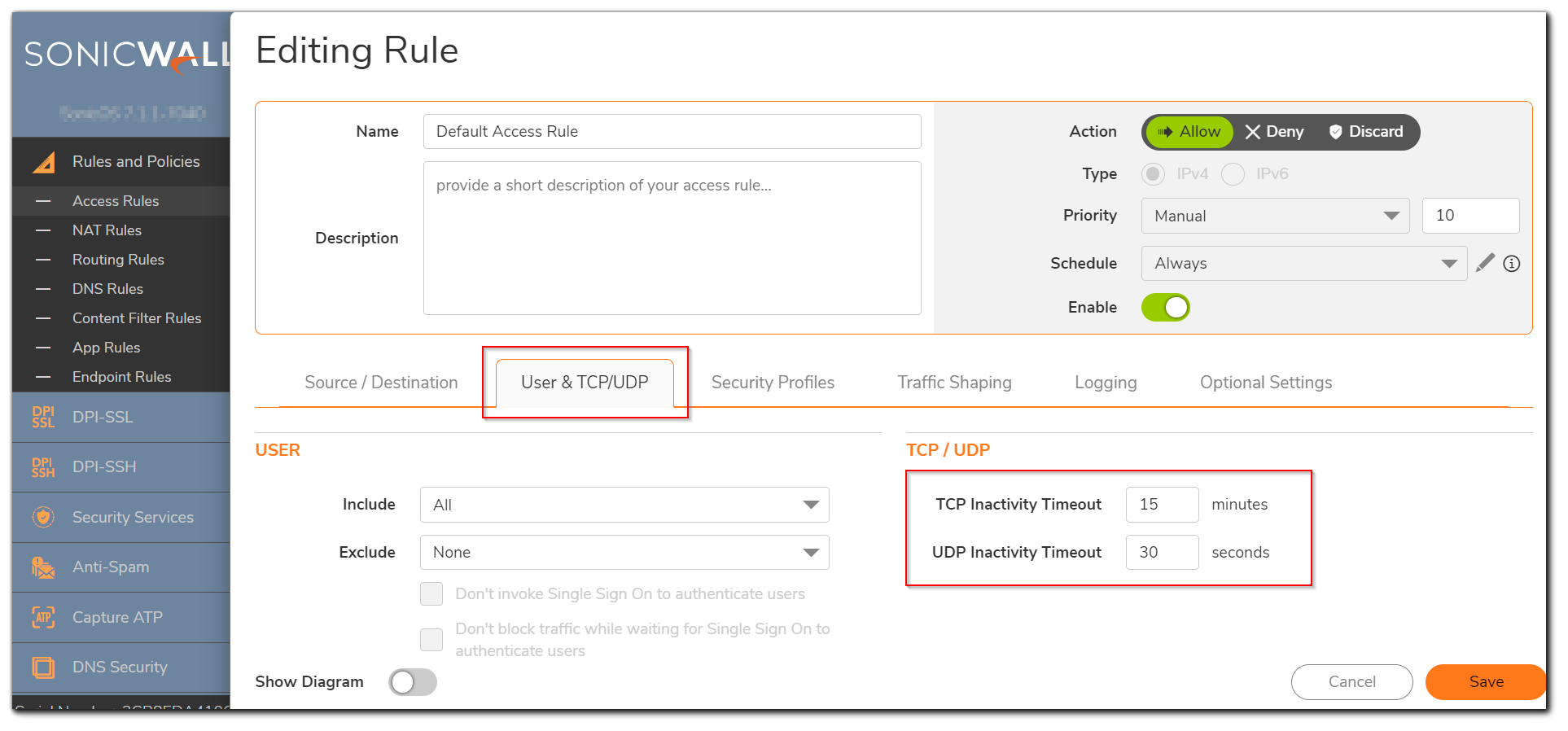
If you would like for the access rule to timeout after a period of TCP inactivity, set the amount of time, in minutes, in the TCP Connection Inactivity Timeout (minutes) field. The default value is 15 minutes.
If you would like for the access rule to timeout after a period of UDP inactivity, set the amount of time, in minutes, in the UDP Connection Inactivity Timeout (seconds) field. The default value is 30 seconds. - Click on OK button to update the rule.
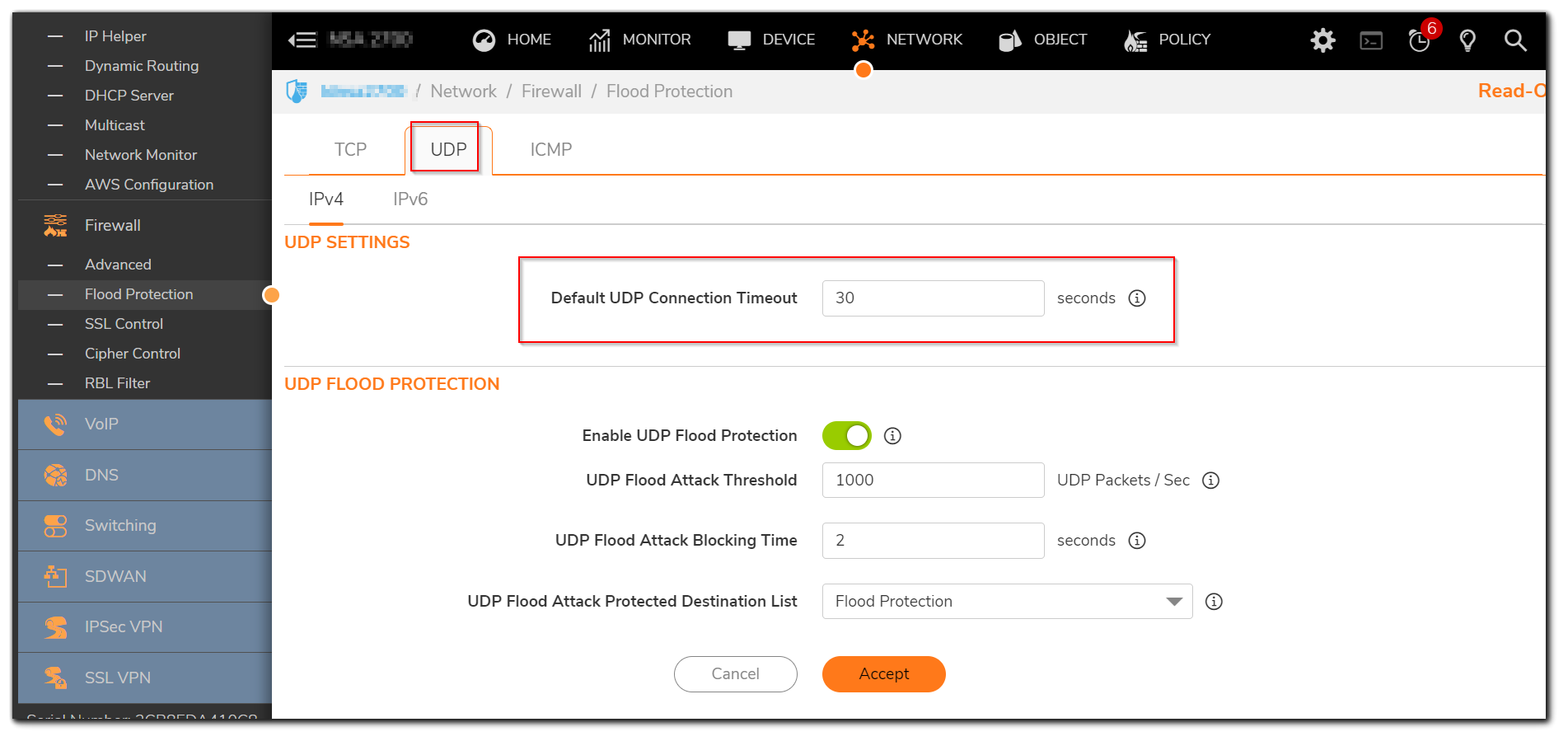
There is a global TCP/UDP timeout setting available under Network| Firewall | Flood protection. There are separate tabs to set this for TCP and UDP.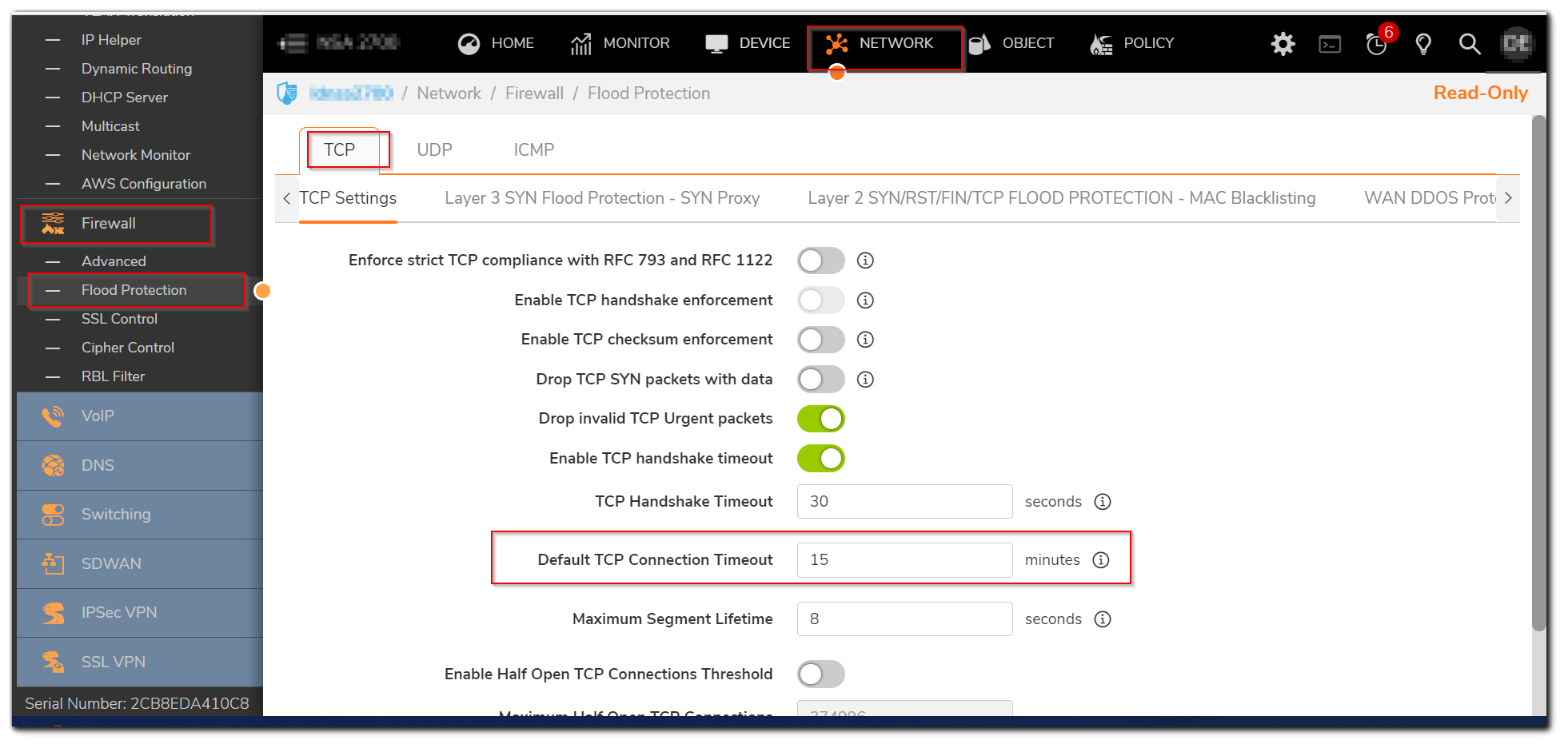
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
You can extend the timeout setting on specific rules for applications that experience long idle times, such as Citrix or MS Terminal Server.
- Login to the SonicWall management interface.
- Go to MANAGE | Rules | Access Rules, edit the appropriate rule by clicking the edit icon.
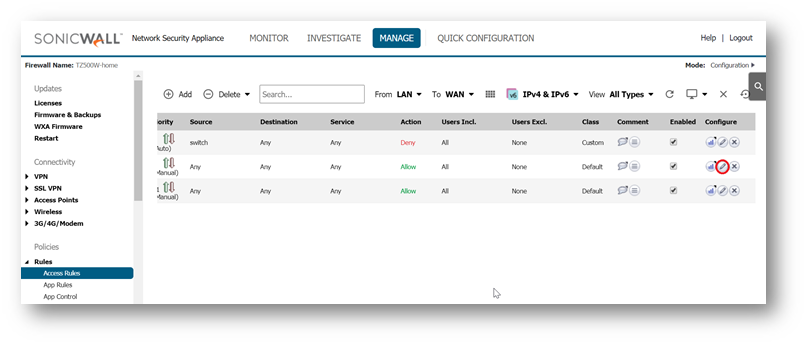
- Click on Advanced tab.
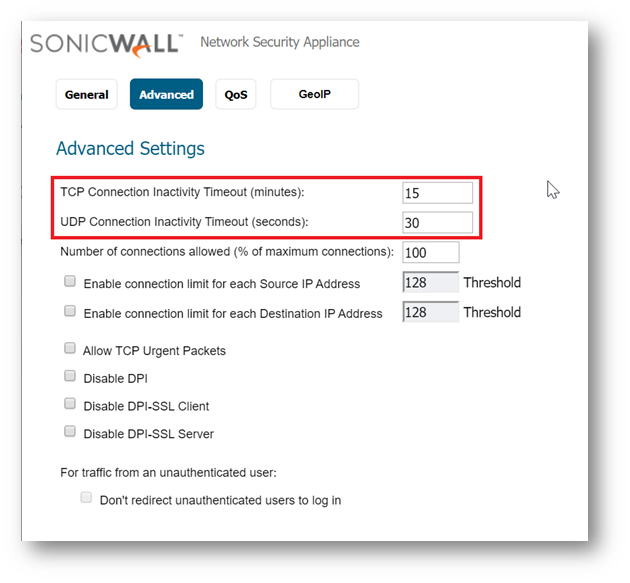
If you would like for the access rule to timeout after a period of TCP inactivity, set the amount of time, in minutes, in the TCP Connection Inactivity Timeout (minutes) field. The default value is 15 minutes.
If you would like for the access rule to timeout after a period of UDP inactivity, set the amount of time, in minutes, in the UDP Connection Inactivity Timeout (seconds) field. The default value is 30 seconds. - Click on OK button to update the rule.
There is a global TCP/UDP timeout setting available under MANAGE | Firewall Settings | Flood protection. There are separate tabs to set this for TCP and UDP.
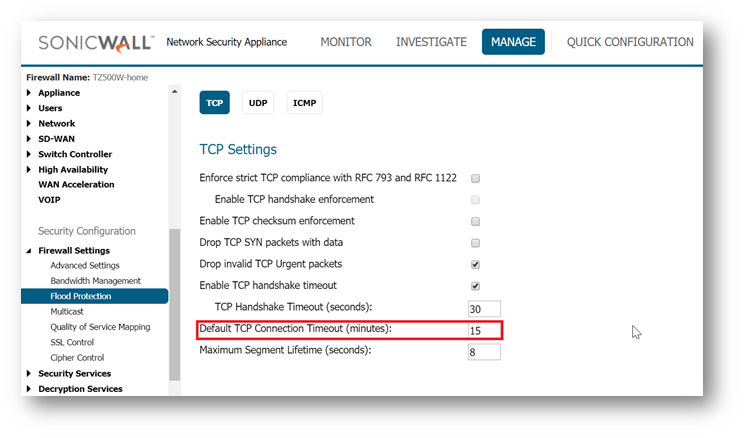
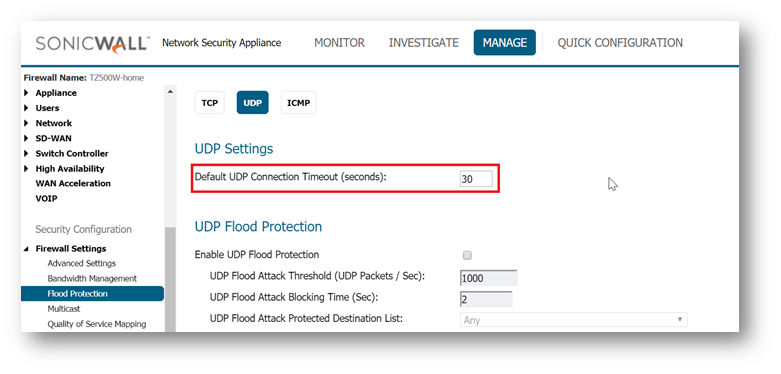
 CAUTION: Making changes globally is not recommended as this affects all access rules and will apply to all TCP/UDP connections on the firewall. This might result in stale connections being held up causing Core 0 Spikes.
CAUTION: Making changes globally is not recommended as this affects all access rules and will apply to all TCP/UDP connections on the firewall. This might result in stale connections being held up causing Core 0 Spikes.
Related Articles
- Enabling TCP, UDP and ICMP Flood Protection.
- CFS Category 100
- GVC 4.9.14 and above are not connecting - Phase 1 Proposal does not match






 YES
YES NO
NO