-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
SonicWall SonicOSX 7.0 FAQ



Description
Q: What is SonicOSX 7.0?
A: SonicOSX 7.0 is the new SonicWall firewall firmware that allows granular control and enforcement of dynamic Layer 7 applications within the security policy.
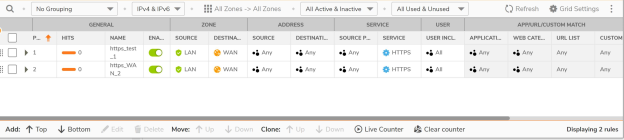
Q: How is SonicOSX different from SonicOS 7.0?
A: SonicOSX combines Layer3 to Layer 7 rules into a single rule called Security Policy. Hence, user will no longer need to configure any rules in separate tabs as in the case of classic mode. It also includes multiple improvements around user experience with rule exporting, cloning of a rule, shadowing alerts, bulk editing and many more
Q: Which models will be enabled with SonicOSX?
A: NSsp 15700 hardware and NSv 270, 470 and 870(virtual platform models) will be running SonicOSX 7.0 by default. This is the model/platform supported during the initial release phase. With latest release SonicOS 7.0.1, user will have a choice to select between classic and policy mode during initial deployment itself.
Q: What are different components on SonicOSX?
A: Components of the new platform are
- Info (Information)
- Match attributes
- Policies/Rules
- Action
- Action Profile
- Enhanced Reporting, Audit and Logging
- Diagnostics, Monitoring and Debugging
Q: What is security rule in SonicOSX?
A: Security rule in SonicOSX merges all the separate components in SonicOS like access rules, app rules, cfs policy, app control, botnet filter, geo-ip filter, intrusion prevention(IPS), gateway antivirus(GAV), anti-spyware into a single rule. The set of these rules combined into one is termed as security policy of an organization.
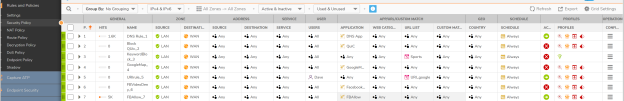
Q: What is decryption rule in SonicOSX?
A: Decryption rule in SonicOSX merges all the separate components in SonicOS like exclude/include objects, exclude include websites and exclude/include users in DPI-SSL and DPI-SSH into a single rule. It also enables user to take decision on what traffic needs to be decrypted and what needs to be bypassed.
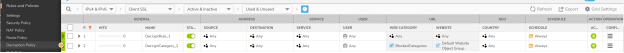
Q: What is DoS rule in SonicOSX?
A: DoS rule in SonicOSX merges all the separate components in SonicOS like DoS attacks, flood protection, DNS rebinding, connection limiting, SMURF, Land attacks etc into a single rule. It also enables user to take decision on what traffic needs to be protected and what needs to be bypassed.
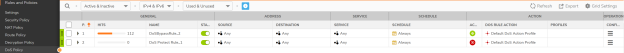
Q: How does NAT policy and route policy work in SonicOSX?
A: During the first release, NAT and Route Policy is designed to work similar to SonicOS 7.0. With added feature of reference to a security rule where it is being referenced.
Q: What is action profile?
A: They are additional actions that user can perform on a traffic. The different action that a user can take are:
- Bandwidth Management/Reporting/Auditing
- Security Services like IPS, GAV, Anti-Spyware etc
- CFS Action, Block Pages, Passphrase
- Ciphers, TCP/UDP/ICMP Flood
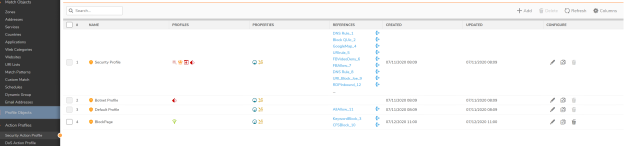
Q: What is rule cloning?
A: Rule cloning refers to copying an existing rule like security rule and placing it in the required priority as required by the user.
Q: What is shadowing rule?
A: Shadowing rule in SonicOSX 7.0 alerts the user if a new rule being created is a super-set or a sub-set of an existing rule.
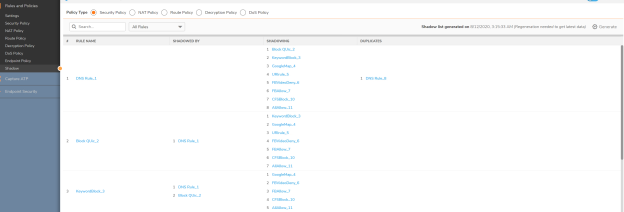
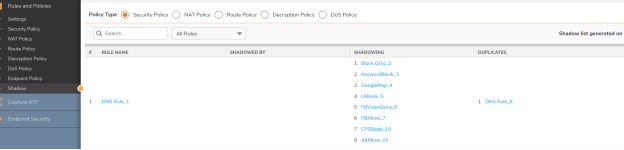
Q: How is shadowing different from duplicate rules?
A: Duplicate rule refers to exact match of all the criteria in the existing rule whereas shadowing refers to a part of components(tuples) that are matching an existing rule in the firewall.
Q: What are the top guidelines to be noted on SonicOS X?
A: Below are the important guidelines to be noted on SonicOSX:
- Rule order is important. No auto rule priority used anymore.
- Rules are always executed in the rule order created by user.
- No Add Rule button. It means user needs to decide where to place the rule while rule creation itself.
- No more default rules
- Implicit deny any any rule in place
- Management rule exists for management zone. In-band management allowed for X0 interface on NSv.
Q: What are the three ways to create rules in SonicOS X UI?
A: Below are the three ways how a user can create rules:
- User can clone an existing rule and insert below or above it.
- User can add rule at the top or bottom
- User can add a rule above or below a selected rule by editing the rule.
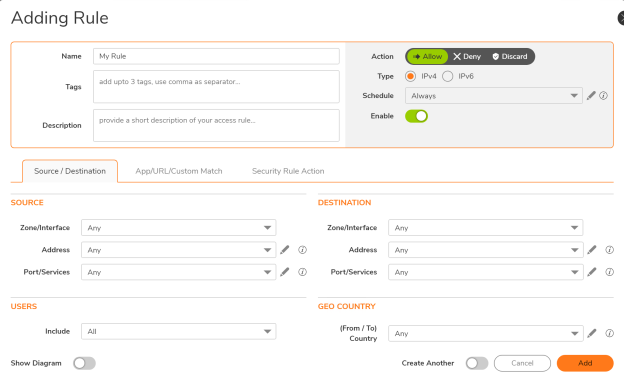
Q: What are the steps involved in creating a security rule on SonicOSX?
A: Below are the steps to be followed to create a security rule:
- Navigate to Policy|Security Policy Tab
- Click on Add Rule; at TOP (if you want to have the rule at the top of the table) or at BOTTOM (if you want to have the rule at the bottom of the table). You can select CLONE option to copy an existing security rule.
- Now use dropdown to select already existing match attributes or use the pencil icon to add custom user/objects/groups/country while you are on the add rule screen.
- Select the match operation as OR in case you want to match any of the Layer 7 classification attribute. Select the match operation as AND in case you want to match all the Layer 7 classification attributes strictly.
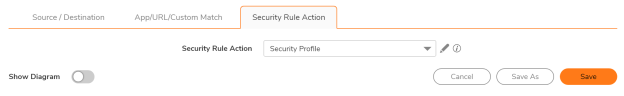
- Choose action: Drop/Deny/Discard
- Create a new action profile or use an existing “security action profile”
- Provide a rule name, schedule (always/custom), comments and tag/ticket
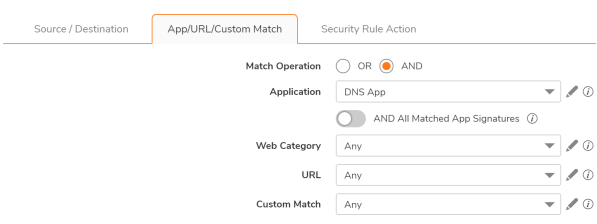
Q: What are the steps involved in creating a decryption rule on SonicOSX?
A: Below are the steps to be followed to create a security rule:
- Navigate to Policy|Decryption Policy Tab
- Click on Add Rule; at TOP (if you want to have the rule at the top of the table) or at BOTTOM (if you want to have the rule at the bottom of the table). You can select CLONE option to copy an existing security rule.
- Now use dropdown to select already existing match attributes or use the pencil icon to add custom user/objects/groups/country while you are on the add rule screen.
- Select the match operation as OR in case you want to match any of the URL classification attribute. Select the match operation as AND in case you want to match all the URL classification attributes strictly.
- Choose action: Decrypt/Bypass
- Provide a name (optional), schedule (always/custom), comments(description) and tag/ticket
- Click on Save.
- Similar steps can be used for Client DPI-SSL, Server DPI-SSL and DPI-SSH. By default, the selection is Client SSL. Dropdown can be used to change this selection for other decryption modes.
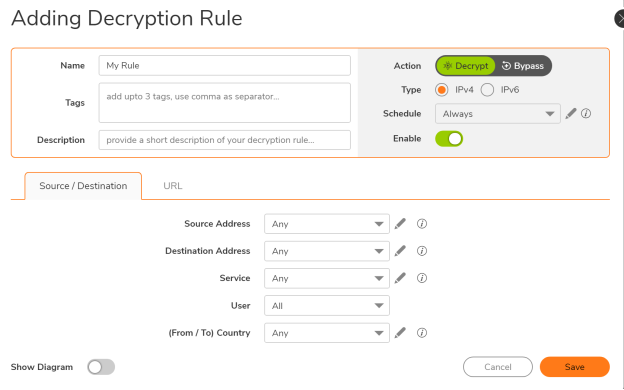
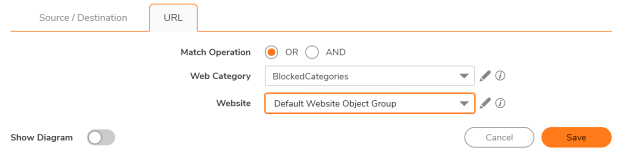
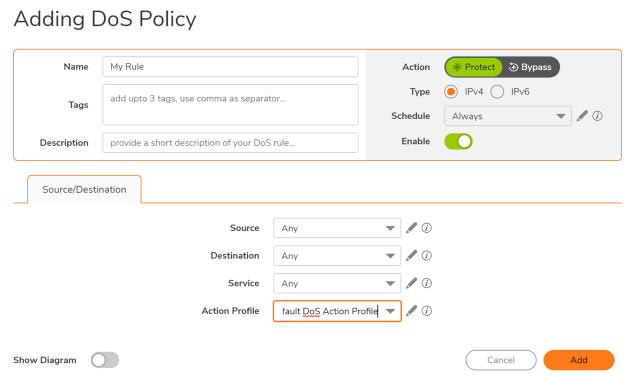
Q: What are the steps involved in creating a DoS rule on SonicOSX?
A: Below are the steps to be followed to create a security rule:
- Navigate to Policy|DoS Policy Tab
- Click on Add Rule; at TOP (if you want to have the rule at the top of the table) or at BOTTOM (if you want to have the rule at the bottom of the table). You can select CLONE option to copy an existing security rule.
- Now use dropdown to select already existing match attributes or use the pencil icon to add custom objects/groups/service while you are on the add rule screen.
- Choose action: Protect/Bypass
- Create a new DoS profile or use an existing “Default DoS Action Profile”
- Provide a name (optional), schedule (always/custom), comments(description) and tag/ticket
- Click on Save.
Q: How does the content-filtering (CFS) rule work in SonicOSX?
A: Below are the important changes around content-filtering rule processing in SonicOSX:
- If the traffic needs to be blocked, then user will see the blocking page from Security Policy. CFS customized blocking page will be ignored in this platform.
- If the traffic is allowed, then CFS will continue to check whether it belongs to CFS Allowed/Confirm/Passphrase under Security Action Profile.
- There is a feature for CFS to Exclude Administrator/Address Objects from blocking. Since the blocking behavior belongs to Security Policy, so this option will not work on CFS anymore. If user needs this feature, he/she may have to create additional security policy for the same.
- If the traffic needs to be blocked, then user will see the blocking page from Security Policy. So 'Enable HTTPS content filter' button is not used/required anymore since it is only valid for block action in previous platforms. So, this tab is no longer active on the SonicOSX.
Q: Where are Website objects used in the SonicOSX?
A: Website objects can only be used in a decryption policy during the initial release.
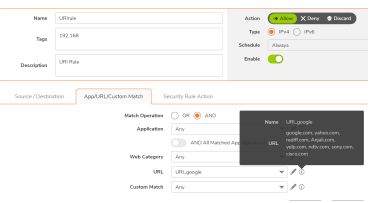
Q: How to block/allow specific websites/domains in the SonicOSX?
A: User can make use of URI objects and apply it to a Security Policy with specific action to allow/block specific domains/websites.
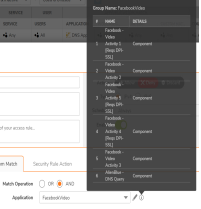
Q: How to allow/block specific applications in SonicOSX?
A: User can make use of application group under objects and apply it to a Security Policy with specific action to allow/block specific applications. Special care needs to be taken when creating allow rule, since some applications are federated wherein it may be required to allow additional application signatures to make it work. User can make use of packet monitor option to find out those missing signatures and then add it to the exiting security rule for the app match.

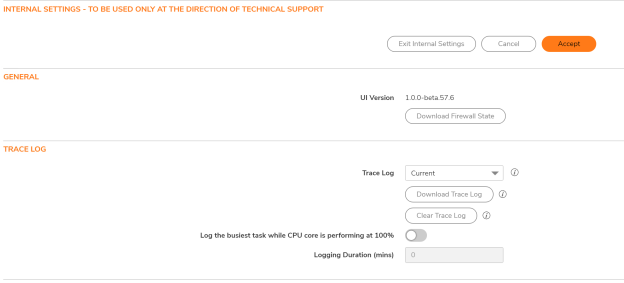
Q: How to access diag page on SonicOSX?
A: Access below URL after logging into UI and then click on Internal Settings.
https://<Firewall Mgmt IP>/sonicui/7/m/mgmt/settings/diag

Q: Can user upgrade from their current NSv instance running 6.5.4.4-44v-21-757 firmware to SonicOSX 7.0?
A: Users will have to perform fresh OVA deployments. With the release of SonicOSX 7.0.1, users can make use of Secure Upgrade Program and purchase key to perform a secure upgrade from Gen6 NSv model to NSv 270/470/870.
Q: Can users import settings file from an instance running SonicOS to that running SonicOSX?
A: Settings migration from previous versions is not supported on SonicOSX 7.0.0. It is recommended to perform a fresh configuration. With the latest release of SonicOSX 7.0.1, settings migration will work if NSv is running Classic mode. NSv running Policy Mode will still not support and not recommended for settings migration.
Q: Can users switch between SonicOSX 7.0 and SonicOS 7.0?
A: SonicWall NSv series firewalls support both SonicOS and SonicOSX. SonicOS is also known as Classic mode, and SonicOSX is known as Policy mode. Selection of or changing between Classic and Policy modes is supported on NSv series starting in SonicOSX 7.0.1 with the following use cases:
- Fresh deployments of SonicOS or SonicOSX
- Upgrading an existing deployment from SonicOSX 7.0.0 to SonicOSX 7.0.1
- Upgrading an existing deployment from SonicOS 6.5.4.v to SonicOS 7.0.1, will require a Secure Upgrade Program Key which can be purchased separately. Secure Upgrade process needs to be followed here.
- Changing an existing deployment from SonicOS 7.0.1 to SonicOSX 7.0.1 (from Classic mode to Policy mode)
- Changing an existing deployment from SonicOSX 7.0.1 to SonicOS 7.0.1 (from Policy mode to Classic mode)
 CAUTION: When switching from Classic mode to Policy Mode, any settings/configurations related to Access-Rules, Application Rules, Security Services, CFS Policies DPI-SSL, DPI-SSH and App Control are lost:Changing From Classic to Policy Mode
CAUTION: When switching from Classic mode to Policy Mode, any settings/configurations related to Access-Rules, Application Rules, Security Services, CFS Policies DPI-SSL, DPI-SSH and App Control are lost:Changing From Classic to Policy Mode CAUTION: When switching from Policy Mode to Classic Mode, configuration/settings are reset to factory-defaults: Changing From Policy to Classic Mode
CAUTION: When switching from Policy Mode to Classic Mode, configuration/settings are reset to factory-defaults: Changing From Policy to Classic Mode
If you have existing NSv deployments running SonicOS 6.5.4.v and plan to continue using NSv on SonicOS/X 7, the ability to change modes provides flexibility to upgrade seamlessly into Classic mode while evaluating or preparing for the move to Policy mode.
Closed-network NSv deployments also support Classic and Policy modes. In a closed network, the lack of internet access prevents the NSv from communicating with the SonicWall License Manager, so the Manual Keyset option is used to apply the security services and other licensing on the firewall. You can select the mode when obtaining the license keyset in MySonicWall. If you switch between modes, you will need to obtain and apply a new license keyset for your NSv.
The CLASSIC and POLICY mode switching option is only visible in SonicOSX after it is enabled in MySonicWall. Log into your MySonicWall account and enable Firewall Mode Switching for the respective firewall serial number.
The Settings screen on the NETWORK | Firewall | Advanced page displays the CLASSIC and POLICY options for Security Services Enforcements.
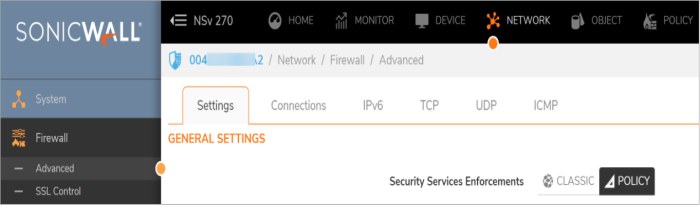
The current mode is indicated by the black button. These buttons are used to initiate the mode change.
Q: What are the installation platforms supported for running SonicOSX?
A: SonicOSX is planned to be supported on all NSv private cloud platforms like VMWARE, Hyper-V, KVM. AWS and Azure public cloud platform will also support SonicOSX.
Q: Will the new platform be manageable from NSM/CSC?
A: SonicOSX support is added in the NSM 2.2 release. Both SonicOS and SonicOSX templates can be created. However, SonicOS and SonicOSX devices cannot be grouped together for applying a single template.
Q: What are the best practices to be followed on the SonicOSX policy platform?
A: Here are some best practices:
- When creating positive app match rule, make sure to allow all related application signatures so that application works without issues. It is recommended to create ANY ANY allow rule from LAN to WAN zone and find out the required application signatures those are needed to run using packet monitor tool.
- Make sure the DNS rule to allow DNS service/application is the top rule to all the DNS servers.
- Migrating from SonicOS to SonicOSX is not supported during initial release so make sure to prepare the configurations manually. User can make use of CLI as well.
- While upgrading, make sure to take settings backup and create a local system backup.
Q: How many IPS Signatures are available on Gen 7 Firewalls?
A: Gen 7 Firewalls feature over 10,000 IPS type Signatures associated with protection against exploits targeting software vulnerabilities.
 NOTE: Some signatures associated with protection against exploits targeting software vulnerabilities are located under GAV and ASpy services.
NOTE: Some signatures associated with protection against exploits targeting software vulnerabilities are located under GAV and ASpy services.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM






 YES
YES NO
NO