-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
SMB SSL-VPN: Web Application Firewall FAQs (Version 3.5 or higher)



Description
SMB SSL-VPN: Web Application Firewall FAQs (Version 3.5 or higher)
Resolution
We value your feedback! While viewing an article, please click the "Rate" button and help us improve the knowledge base.
Frequently Asked Questions:
1. Why does any organization need to worry about Web security?
2. What is a Web Application Firewall?
3. What purpose does a Web Application Firewall serve?
4. How is a WAF different from a Non-proxy based IPS or Application Fiewall?
5. What features does SonicWall’s Web Application Firewall support?
6. What is OWASP Top Ten?
7. How do I deploy SonicWall's WAF solution?
8. Will WAF be integrated into the UTM?
9. How do I set up WAF to work as a Reverse Proxy?
10. What is Application Offloading?
11. Does the SRA User licensing apply for WAF?
12. What is the maximum number of concurrent connections for WAF running on SRA 4200?
1. Why does any organization need to worry about Web security?
The SC Magazine recently published a report from Cenzic that reveals that Web applications account for 80 percent of Internet vulnerabilities.
[http://www.scmagazineus.com/web-apps-account-for-80-percent-of-internet-vulnerabilities/article/129027/]
“Vulnerabilities in web applications made up 80 percent of all web-related flaws in the second half of 2008 and rose in prevalence by about eight percent from the first half of the year, according to a report released Tuesday by Cenzic.”
“The web application vulnerabilities, for example, were in Adobe, SAP, Microsoft, Mozilla, Sun, Apache, and Oracle products.”
SANS rates Web application vulnerabilities as the number one class of server-side vulnerabilities in their Top 20. MITRE’s “Top 25 Most Dangerous Programming Errors” covers most of the Web application vulnerabilities. The community has constructed this list based on the prevalence and the severity of the threats. MITRE has also captured the prevalence of these vulnerabilities in their vulnerability trend report:
“The most notable trend is the sharp rise in public reports for vulnerabilities that are specific to web applications.
Buffer overflows were number 1 year after year, but that changed in 2005 with the rise of web application vulnerabilities, including cross-site scripting (XSS), SQL injection, and remote file inclusion, although SQL injection is not limited just to web applications.”
Needless to say, organizations will certainly want to protect their intellectual property from the most prevalent form of Cyber attacks.
2. What is a Web Application Firewall?
A Web Application Firewall acts as a single point of control to determine what should go in and out of the protected organization in the form of Web traffic. It is a special type of firewall that can inspect content exchanged over clear-text HTTP traffic, encrypted SSL traffic and traffic encoded using various encoding schemes.
With the advancement in Web 2.0 technologies, such as Ajax, a generic firewall is no longer sufficient in preventing attacks embedded inside dynamic Web content. A Web Application Firewall, on the other hand, is also capable of protecting applications written using Web 2.0 technologies.
An effective Web Application Firewall should protect against the OWASP Top Ten vulnerabilities (described below).
3. What purpose does a Web Application Firewall (WAF) serve?
3.1 PCI DSS version 1.1 Requirement 6.6 states the following:
"Ensure that web-facing applications are protected against known attacks by applying either of the following methods:
a) Having all custom application code reviewed for common vulnerabilities by an organization that specializes in application security.
b) Installing an application layer firewall in front of web facing applications."
3.2 Most of the vulnerabilities arise from insecure programming or weak architectural design practices followed by an engineering organization. However, it is also not cost-effective for organizations to train their staff regularly on information security. New vulnerabilities are discovered on a daily basis, which necessitates regular training and fresh code reviews. WAF, on the other hand, can be up-to-date with signatures as and when a new vulnerability is discovered giving a 24 x 7 protection for the suite of Web applications it protects.
3.3 As soon as a vulnerability is found within an application by either using a Vulnerability Assessment tool or by reviewing the programming logic, it takes days or weeks before the patch gets deployed in production. During this time, a WAF can serve as a quick fix for the discovered vulnerability by a process called Virtual Patching reducing the down time needed before the patch is deployed. Virtual Patching is particularly useful if the discovered flaw exists in more than just one Web application.
4. How is a WAF different from a Non-proxy based IPS or Application Firewall?
|
IPSs or Non-Proxy based WAFs
|
Proxy-based WAFs
|
|
The input inspection is limited to signature matching. Due to the lack of ability to inspect HTML DOM, Javascript, and CSS content the IPS can still be vulnerable to information leakage, cookie poisoning, identity theft, parameter tampering, cross-site request forgery and session hijacking.
|
Proxy based Application Firewalls are effective against these attacks and the attacks targeting Web 2.0 technologies because they fully terminate TCP and SSL protocols; interpret HTML, Javascript and Ajax content; and secure based on positive security, negative security and real-time dynamic application learning and profiling.
|
|
Since they are not involved in the TCP 3-Way handshake, they can not control the packet flow from the client and all packets flow to the back-end servers, whether they are harmful or not. The packet based bridge inspection of IPS can not distinguish session traffic between the outside network and the inside network, which contain the resources to be protected.
|
WAFs terminate TCP and SSL protocols. Hence, totally separate TCP sessions are used to manage and inspect client sessions versus back end server sessions, which implies that bad traffic does not reach the back-end until the Proxy inspects and validates the client session.
|
|
The SSL decryption technique employed by IPSs requires an admin to upload private cryptographic keys of the back-end web servers into the device so that it can “look” into packets. This is both an administrative hassle and a security risk. If the device is compromised for any reason, all the Web servers that it is protecting are also compromised until the individual certificates are replaced.
|
Since WAFs terminate SSL connections it does not need to worry about key storage. It can also act as an SSL accelerator. WAF is designed to safely store and manage certificates and private keys and can also perform certificate based Client-Authentication when security policy demands it.
|
|
Since, IPSs do not maintain user sessions using cookies, they can not perform strong authentication, authorization using access policies and user/session level logging.
|
WAFs can provide strong authentication, such as 2-factor authentication and one-time passwords. They can enforce fine-grained access policies (URL Host and Path based) and perform user/session level logging.
|
|
Throughput optimization can not be performed by IPSs due to the inability to terminate TCP and SSL.
|
WAFs can additionally perform SSL hardware acceleration, connection multiplexing, caching static content, connection persistence and Gzip compression to reduce the end-user response times
|
5. What features does SonicWall’s Web Application Firewall support?
Security Features
- Protects against OWASP Top Ten vulnerabilities that includes protection from XSS, SQL Injection, and CSRF
- Has Anti-evasive capability to catch threats within encoded and compressed input data because it normalizes the input from user before matching against signatures
- Inspects SSL encrypted packets
- Can provide strong authentication including Two factor authentication, One time passwords and Client-certificate authentication for Web applications
- Inspects POST payload from user and response payload from Web server
- Provides fine-grained access control based on various URL components like host, port and path.
- Provides real-time protection with dynamic signature updates
- Delivers Web applications to remote users securely by acting as an SSL Offloader
Acceleration features
- Performs SSL hardware acceleration
- Performs Content Caching for static content and SSL Session Caching
- Performs GZIP compression, which significantly reduces bandwidth usage for remote users
- Enables Connection Persistence and Connection Multiplexing with the backend
- Supports Transfer-Chunk encoding needed to deliver large dynamic content
Note: These features optimize the data exchange between the client and the WAF even if backend Web servers do not support these features.
Administrative Features
- Ability to configure global exclusions and exclusions based on signature, host and URL path.
- Ability to enable or disable features based on severity (high, medium and low)
- Built-in false positive detection system weeds out stale signatures and signatures with high false positive rate
- Provides description of various threats and detailed information on prevalence, severity and remedial measures.
- Ability to turn on and off auto-updates for signatures
Reporting
- Reports incidence statistics
- Event logging
- GMS and Viewpoint Support
6. What is OWASP Top Ten?
OWASP Top Ten is the top 10 vulnerabilities listed by the OWASP working group. The protection for these vulnerabilities was listed as part of the PCI DSS 6.6 core requirements and has also been adopted by many industries as a compliance standard.
The Top Ten vulnerabilities include:
- Cross Site Scripting
- Injection Flaws, such as SQL injection and OS command injection.
- Malicious File Execution
- Insecure Direct Object Reference
- Cross Site Request Forgery
- Information Leakage and Improper Error Handling
- Broken Authentication and Session Management
- Insecure Cryptographic Storage
- Insecure Communications
- Failure to Restrict URL Access
7. How do I deploy SonicWall's WAF solution?
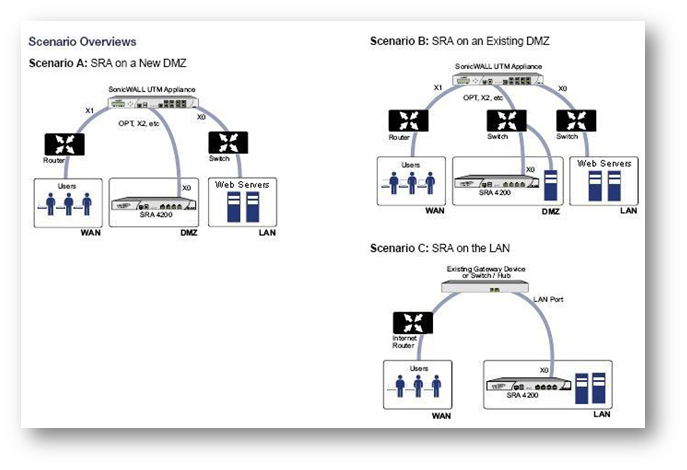
One-Arm Mode Deployment
A WAF-enabled SonicWall SRA appliance is commonly deployed in tandem in “one-arm” mode over the DMZ or Opt interface on an accompanying gateway appliance, for example, a SonicWall Unified Threat Management (UTM) appliance, such as a SonicWall NSA E7500 appliance.
The primary interface (X0) on the SonicWall SRA connects to an available segment on the gateway device. The encrypted user session from the client is passed through the gateway to the SonicWall SRA appliance. The SonicWall SRA appliance decrypts the SSL encrypted session, normalizes encoded data, scans the HTTP request for intrusions, and enforces authorization controls and access policies to determine if the requested resource should be allowed or blocked. If the HTTP request is safe, then it traverses the gateway appliance to reach the backend Web site. The Web site then returns the requested content to the SonicWall SRA appliance through the gateway, where the HTTP response is again scanned for intrusions and SSL encrypted. The SRA forwards the encrypted response to the client.
8. Will WAF be integrated into the UTM?
Probably not anytime soon. The SRA product lines already have a built-in Reverse Proxy that allows the WAF to terminate SSL connections and interpret content types, including HTML and Javascript. This is critical in effectively protecting Web 2.0 applications, against attacks, such as Cross-Site Request Forgery and Parameter manipulation. In addition, the Reverse Proxy allows the WAF to offer acceleration features, such as content caching, data compression, connection persistence and connection multiplexing.
9. How do I set up WAF to work as a Reverse Proxy?
WAF can be set up to work as a Reverse Proxy through Application Offloading or by setting up HTTP(S) bookmarks.
10. What is Application Offloading?
Application Offloading provides secure access to both internal and publicly hosted web applications.
Application Offloading can be used in any of the following scenarios:
• In conjunction with the Web Application Firewall subscription service to provide the offloaded web application continuous protection from malicious web attacks.
• To function as an SSL offloader and add HTTPS support to the offloaded web application, using the integrated SSL accelerator hardware of the SSL-VPN appliance.
• To add strong or stacked authentication to the offloaded web application, including two-factor authentication, One Time Passwords and client certificate authentication.
• To control granular access to the offloaded web application using global, group or user based access policies.
• To support web applications for remote access not currently supported by HTTP/HTTPS bookmarks. Application Offloading does not require URL rewriting, thereby delivering complete application functionality without compromising throughput.
11. Does the SRA User licensing apply for WAF?
If authentication is enabled for a regular or an Offloaded Portal, then the WAF enforces the SRA user licensing requirements. Authentication can be disabled for an Offloaded portal by enabling "Disable Authentication and Access Controls" checkbox under the "Offloading" tab. This is particularly useful for public sites or sites which manage authentication on its own. User licensing does not apply for this configuration.
12. What is the maximum number of concurrent connections for WAF running on SRA 4200?
Theoretically, the SRA 4200 can accept upto 600 concurrent connections. But, the actual number will depend on the configuration. If authentication and URL rewriting options are disabled for an Offloaded portal, the SRA 4200 with WAF enabled can do upto 120 concurrent requests/sec and upto 50Mbps of throughput.
Related Articles
- How do I integrate Ianum with a SonicWall SMA?
- SMA 8200v Azure/AWS Deployment Guidelines
- SMA 1000: SAML Identity Provider Service Configuration Guide






 YES
YES NO
NO