-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
SMA1000- Configuration Extensions used to be used when FIPS is enabled



Description
Once FIPS is enabled on the Physical appliances- 6200/6210, 7200/7210, the following configuration extension values are required for effective functioning.
Resolution
To put the device into FIPS mode - Navigate to System Configuration|General Settings|FIPS Security.
 NOTE: Turning on FIPS mode will cause a reboot and delete all existing certificates on the appliance.
NOTE: Turning on FIPS mode will cause a reboot and delete all existing certificates on the appliance.

Enter the following CEM extensions in System Configuration|Maintenance|Advanced.
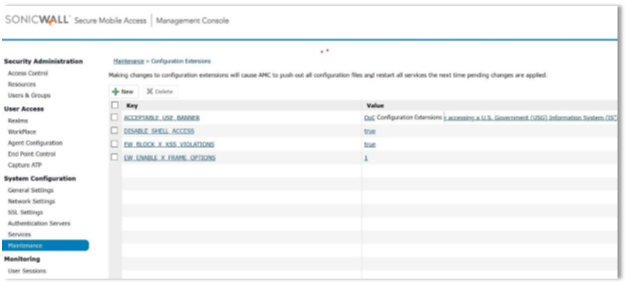
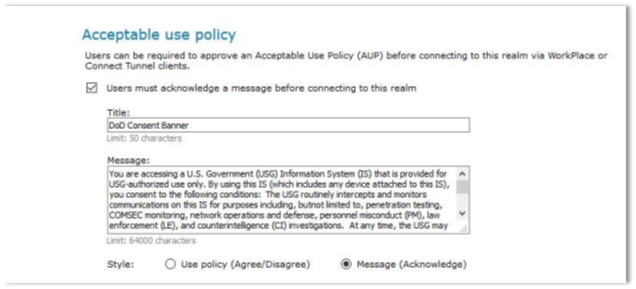
a. ACCEPTABLE_USE_BANNER [Enter the DoD banner]
See the DOD Banner section for a current version of the banner used for APL testing.
This extension enables the display of an Acceptable Use Policy or DoD Banner on an administrative logon (https://IP address:8443).
Configure an Acceptable Use Policy or DoD Banner for user logon in the appropriate Realm (User Access|Realms|[Select an existing realm]|Advanced|Acceptable Use Policy).
b. DISABLE_SHELL_ACCESS =true
This extension disables the Operating System shell normally available through the Console connection on the front of the SMA. The lack of access to the shell is mandatory for APL compliance.
c. EW_BLOCK_X_XSS_VIOLATIONS= true
This extension is necessary for mitigating web vulnerabilities.
d. EW_ENABLE_X_FRAME_OPTIONS 1
This extension is necessary for mitigating web vulnerabilities.
e. AMC_SESSION_TIMEOUT_SECS [number of seconds]
(e.g., AMC_SESSION_TIMEOUT_SECS=600 would result in a timeout of 10 minutes for administrators.
This setting determines how long to allow an AMC or shell session to be idle before forcing a logout.
Additional CEM Commands:
A site may be required by local security policies to limit incorrect logon attempts by a primary administrator.
Similarly, the site may insist that the administrator lockout lasts for a specific period. Finally, local security policies may dictate that SYSLOG traffic be encrypted when sent to an external SYSLOG server, perhaps on a different network or subnet. The following commands will allow the configuration of these things.
 CAUTION:Do regular configuration backups (Maintenance|System Configuration|Import or Export) – especially before making configuration changes, usually by clicking on the “Pending changes” icon in the upper right-hand corner of the AMC screen!
CAUTION:Do regular configuration backups (Maintenance|System Configuration|Import or Export) – especially before making configuration changes, usually by clicking on the “Pending changes” icon in the upper right-hand corner of the AMC screen!
1. Set # of failed logins before the admin account is locked out:
ADMINISTRATOR_ACCOUNT_LOCKOUT_ATTEMPTS=#
2. Set # of seconds an admin account is locked out:
ADMINISTRATOR_ACCOUNT_LOCKOUT_SECONDS=#
3. Force TLS for all remote syslog servers:
LOGGING_SECURE_SYSLOG=true|false
Related Articles
- How do I integrate Ianum with a SonicWall SMA?
- SMA 8200v Azure/AWS Deployment Guidelines
- SMA 1000: SAML Identity Provider Service Configuration Guide






 YES
YES NO
NO