-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Port Forwarding configured using SonicOS API



Description
This article describes the steps involved in creating Polices using SonicOS APIs that will let you access internal devices or servers behind the SonicWall firewall.
Cause
SonicWall by default does not allow inbound traffic which not a part of a session that was initiated by an internal device on the network. This is done to protect the devices in the internal network from malicious access. If required certain parts of the network can be opened to external access, for example Webservers, Exchange servers and so on.
To open the network, we need to specify an access rule from the external network to the internal network and a NAT Policy so we direct traffic only to the intended device.
With APIs this can be achieved on scale for example you can create multiple Access Rules and NAT policies with one command and all the attributes can be specified into Json Objects.
Resolution
Manually opening Ports / enabling Port forwarding to allow traffic from the Internet to a Server behind the SonicWall using sonicos API involves the following steps:
Step1: Enabling the API Module.
Step2:Getting into Swagger.
Step3:Login to the SonicWall with API.
Step4:Create Address Objects and Service Objects with API.
Step5:Creating NAT Policy with API.
Step6: Creating Access Rules with API.
Step7:Committing all the configurational changes made with APIs.
Step8: Log out the SonicWall with API:
Scenario Overview
The following walk-through details allowing TCP 3389 From the Internet to a Terminal Server on the Local Network.Once the configuration is complete, Internet Users can RDP into the Terminal Server using the WAN IP address.Although the examples below show the LAN Zone and TCP 3389 they can apply to any Zone and any Port that is required.
Step 1: Enabling the API Module:
- Log into the SonicWall GUI.
- Click Manage in the top navigation menu.
- Click Appliance | Base Settings
- Under Base Settings search for sonicos API
- Click Enable sonicos API
- Click Enable RFC-2617 HTTP Basic Access authentication
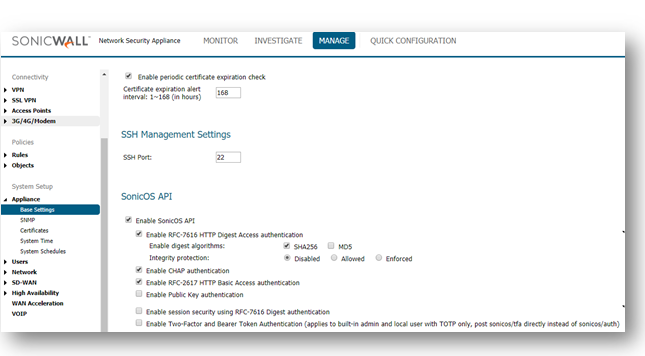
Step2: Getting into Swagger
- Click on the Mange Tab
- Scroll Down to find API
- Click on the Link https://sonicos-api.sonicwall.com
- Swagger will prepopulate your SonicWalls’s IP, MGMT Port, Firmware so it can give you a list of applicable APIs.
 NOTE: All the APIs required for configuring Port Forwarding will be listed in this Article.
NOTE: All the APIs required for configuring Port Forwarding will be listed in this Article.
Step3:Login to the SonicWall with API:
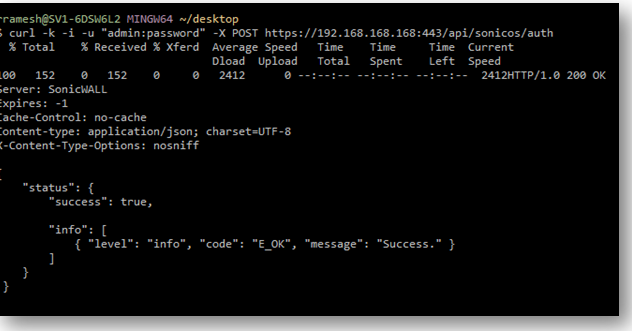
- curl -k -i -u "admin:password" -X POST https://192.168.168.168:443/api/sonicos/auth
“admin:password” – Replace this with your SonicWalls username : password
https://192.168.168.168:443/-- Replace this with your SonicWalls Public or private IP address
Command Output should contain a string: "success": true
 NOTE: You are free to choose Swagger, Postman, Git bash or any application that allows API calls, if you are using a Linux based operating system you can execute cURL from the terminal.For this article I am using Git bash on Windows.
NOTE: You are free to choose Swagger, Postman, Git bash or any application that allows API calls, if you are using a Linux based operating system you can execute cURL from the terminal.For this article I am using Git bash on Windows.
Step4:Create Address Objects and Service Objects with API:
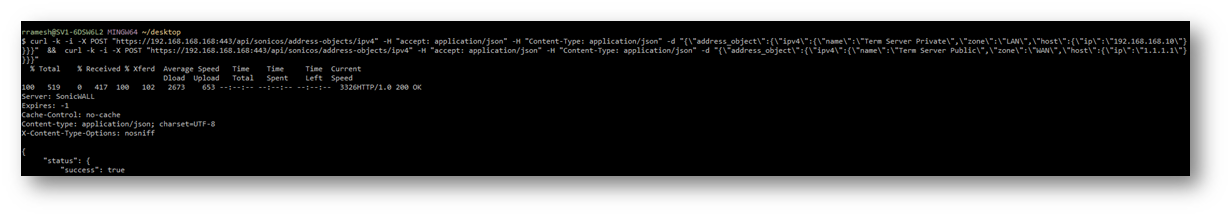
- curl -k -i -X POST "https://192.168.168.168:443/api/sonicos/address-objects/ipv4" -H "accept: application/Json" -H "Content-Type: application/Json" -d "{\"address_object\":{\"ipv4\":{\"name\":\"Term Server Private\",\"zone\":\"LAN\",\"host\":{\"ip\":\"192.168.168.10\"}}}}" && curl -k -i -X POST "https://192.168.168.168:443/api/sonicos/address-objects/ipv4" -H "accept: application/Json" -H "Content-Type: application/Json" -d "{\"address_object\":{\"ipv4\":{\"name\":\"Term Server Public\",\"zone\":\"WAN\",\"host\":{\"ip\":\"1.1.1.1\"}}}}"
OR
curl -k -i -X POST "https://192.168.168.168:443/api/sonicos/address-objects/ipv4" -H "accept: application/Json" -H "Content-Type: application/Json" -d @add.Json
@add.Json is a file with the following information:
{
"address_objects": [
{
"ipv4": {
"name": "Term Server Private",
"zone": "LAN",
"host": {
"ip": "192.168.168.10"
}
}
},
{
"ipv4": {
"name": "Term Server Public",
"zone": "WAN",
"host": {
"ip": "1.1.1.1"
}
}
}
]
}
Output of the First command where we have parsed the address object data on the command instead of creating a separate File:
Output of the second Command where we have used a file called @add instead of specifying data on the command:
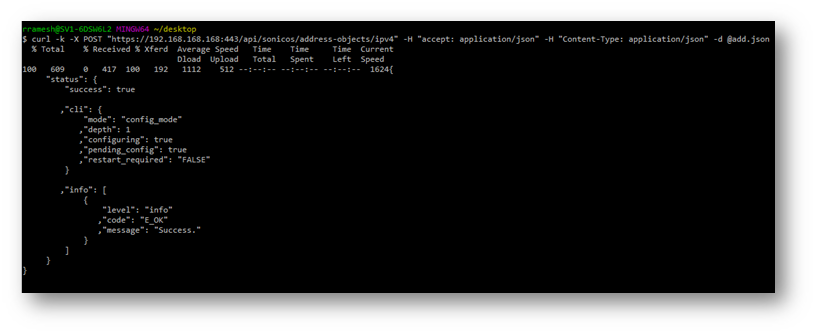
 TIP: If you are creating only one Address Object then the First command should be sufficient, if you are creating multiple address objects then the second command should be used.
TIP: If you are creating only one Address Object then the First command should be sufficient, if you are creating multiple address objects then the second command should be used.
 CAUTION: I have the add.Json file saved on to my desktop and hence I was able to call it into the command, if you have created the Json the file in a different location then make sure you are executing the command from that location.
CAUTION: I have the add.Json file saved on to my desktop and hence I was able to call it into the command, if you have created the Json the file in a different location then make sure you are executing the command from that location.
2. Adding Service Object:
curl -k -i -X POST "https://192.168.168.168:443/api/sonicos/service-objects" -H "accept: application/Json" -H "Content-Type: application/Json" -d @serviceobj.Json
https://192.168.168.168:443 – Replace that with the IP of the SonicWall
@serviceobj.Json is a file that contains the Attributes of the service object:
{
"service_object": {
"name": "Terminal Server 3389",
"TCP": {
"begin": 3389,
"end": 3389
}
}
}
Output of the command:
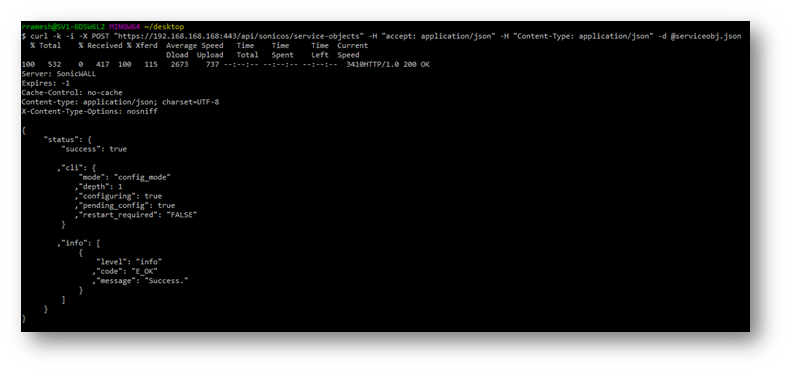
3. Committing the changes made to the SonicWall: We need to do this to be able to use the Address Objects and service objects that we just created to make a NAT Policy and an Access Rule.
curl -k -X POST "https://192.168.168.168:443/api/sonicos/config/pending" -H "accept: application/Json"
https://192.168.168.168:443 – Replace that with the IP of the SonicWall
Output of the command:
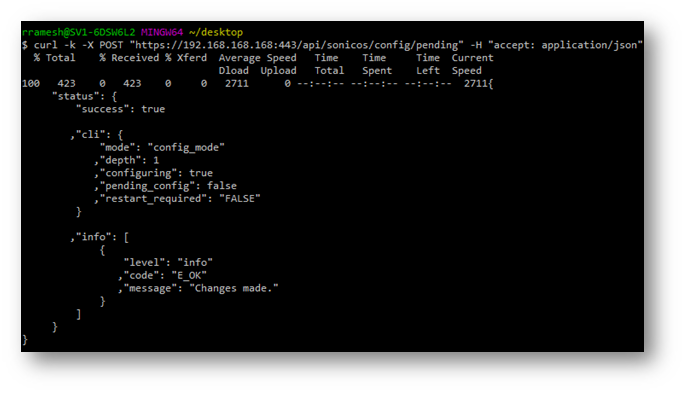
Step5: Creating NAT Policy with API:
1. curl -k -i -X POST "https://192.168.168.168:443/api/sonicos/nat-policies/ipv4" -H "accept: application/Json" -H "Content-Type: application/Json" -d @natpolicy.Json
https://192.168.168.168:443 – Replace that with the IP of the SonicWall
@natpolicy.Json is a file that contains the Attributes of the NAT Policy:
{
"nat_policies": [
{
"ipv4": {
"name": "Inbound NAT 3389",
"enable": true,
"comment": "",
"inbound": "X1",
"outbound": "any",
"source": {
"any": true
},
"translated_source": {
"original": true
},
"destination": {
"name": "Term Server Public"
},
"translated_destination": {
"name": "Term Server Private"
},
"service": {
"name": "Terminal Server 3389"
},
"translated_service": {
"original": true
}
}
}
]
}
Output of the command:
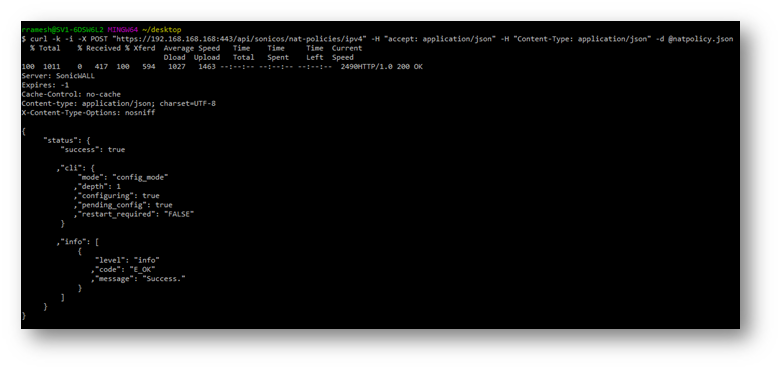
Step6: Creating Access Rules with API:
1. curl -k -X POST "https://192.168.168.168:443/api/sonicos/access-rules/ipv4" -H "accept: application/Json" -H "Content-Type: application/Json" -d @accessrule.Json
https://192.168.168.168:443 – Replace that with the IP of the SonicWall
@accessrule.Json is a file that contains the Attributes of the access rule:
{
"access_rules": [
{
"ipv4": {
"name": "Inbound 3389",
"enable": true,
"from": "WAN",
"to": "LAN",
"action": "allow",
"source": {
"address": {
"any": true
},
"port": {
"any": true
}
},
"service": {
"name": "Terminal Server 3389"
},
"destination": {
"address": {
"name": "Term Server Public"
}
}
}
}
]
}
Output of the command:
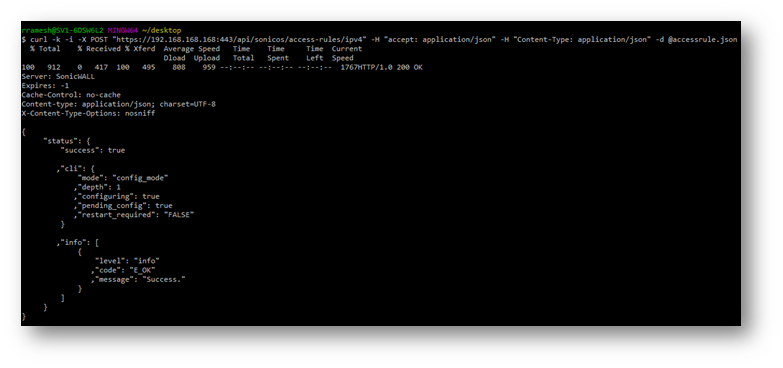
Step7: Committing all the configurational changes made with APIs:
1. We have already committed Address objects and Service Objects in Step 4, In this step we are committing the NAT Policy and the Access Rule to the SonicWalls configuration:
curl -k -X POST "https://192.168.168.168:443/api/sonicos/config/pending" -H "accept: application/Json"
https://192.168.168.168:443 – Replace that with the IP of the SonicWall
We have Only used the POST method in most of the API calls for this Article because we are only Adding things into the configuration, there are other methods Like GET,DELETE,PUT and etc. I recommend that you go through https://sonicos-api.sonicwall.com for more API commands.
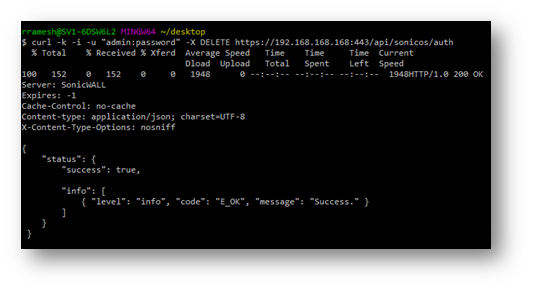
Step8: Log out the SonicWall with API:
1. It is recommended to log out from the SonicWall via API once the desired configuration is committed.
curl -k -i -u "admin:password" -X DELETE https://192.168.168.168:443/api/sonicos/auth
https://192.168.168.168:443 – Replace that with the IP of the SonicWall
“admin:password” – is the actual username and password for the SonicWall.
Output of the command:
 CAUTION: Caution: If you miss to perform the action in Step 7 and Execute the command in Step 8 you will lose all the configuration changes made in the current session.
CAUTION: Caution: If you miss to perform the action in Step 7 and Execute the command in Step 8 you will lose all the configuration changes made in the current session.
Summary:We have successfully configured a Port Forwarding for a user in the Internet to access a Term Server that is behind a Firewall on port 3389 using sonicos API.
 NOTE: It is always recommended to use Client VPN for RDP connections this article here is just an example.
NOTE: It is always recommended to use Client VPN for RDP connections this article here is just an example.
Related Articles
- Initial and Advanced Firewall Setup for high security environments
- How to setup Active/Standby High Availability on NSSP 13700 appliances?
- How to Create URI List Objects/Groups on SonicOSX 7?
Categories
- Firewalls > TZ Series > Networking
- Firewalls > NSa Series > Networking
- Firewalls > SonicWall SuperMassive 9000 Series






 YES
YES NO
NO