-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
MSS FW Best Practices: Unifi Equipment



Description
 CAUTION: These documents are intended to provide partners with firewall configuration recommendations ONLY. They contain examples and caution should be exercised when making changes to your firewall as unplanned changed could result in downtime based on the complexity of the environment and/or configuration.
CAUTION: These documents are intended to provide partners with firewall configuration recommendations ONLY. They contain examples and caution should be exercised when making changes to your firewall as unplanned changed could result in downtime based on the complexity of the environment and/or configuration.
MSS Recomended SonicWall Firewall Best Practices Index
Unifi Network Cloud
- These instructions apply if the Unifi Network Application is hosted in the cloud.
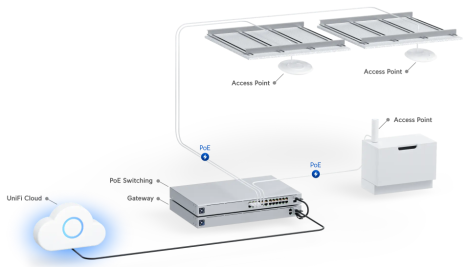
![]() Unifi Network Hosted in the Cloud
Unifi Network Hosted in the Cloud
Finding Inform URL IP
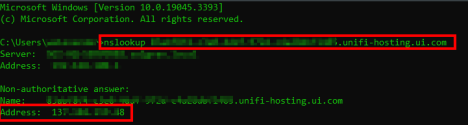
The user will need to provide their Unifi Inform URL. They can do this by:
- clicking on Copy Inform URL in their Unifi Network dashboard page.

- Paste that into a notepad and copy the link NOT including the “http://” or anything after “.com”.
![]()
- Do an NSLookup on that URL and that will give you the Inform URL IP address.
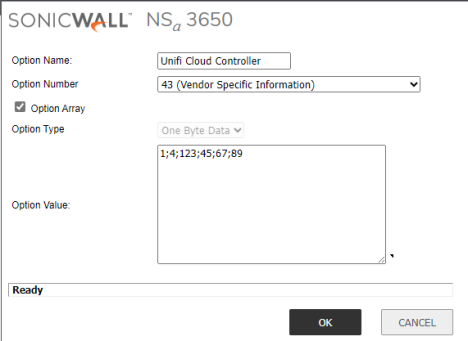
DHCP Option 43
You will need to create this so that the management traffic from the AP is forwarded to the Unifi Cloud Controller.
- In the SonicWall firewall, navigate to Network > DHCP Server > Advanced and click Add Option
- Fill in the following:
- Option Name: Enter the name for this (Unifi Cloud for example).
- Option Number: 43 (Vendor Specific Information)
- Option Array: Check this box
- Option Value: Enter the Inform URL IP address in One Byte Data. To do this, take the Inform URL IP and:
- Replace each “.” with a semicolon.
- Add “1;4;” to the front of the IP address.
- For example, if the IP address is “123.45.67.89”, you will enter “1;4;123;45;67;89” in the Option Value field.
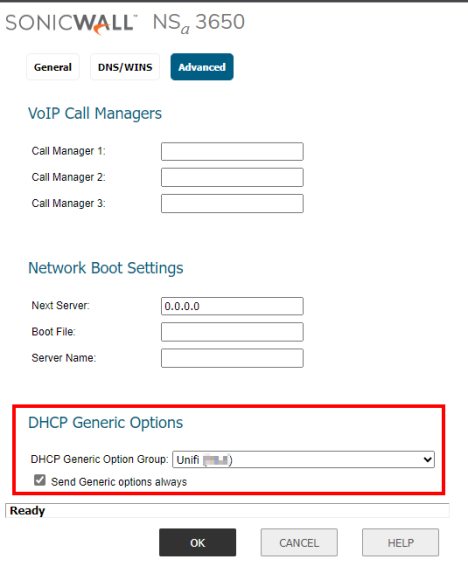
- Click Ok twice.
Access Point DHCP
Now we need to assign this DHCP option to the Unifi Access Points. To do this you can either edit the Dynamic DHCP scope for the network that the APs are on, or create static DHCP entries for each AP to statically assign them an IP address based on their MAC address.
- Whichever option you go with, make sure to select the DHCP option created above on the Advanced page under DHCP Generic Options
Port/Service Restrictions
If the firewall has outbound port/service restrictions in place, you will need to ensure that the correct ports are open from the Unifi equipment to the WAN.
For the current list of required ports, see: UniFi Network - Required Ports Reference – Ubiquiti Support and Help Center
- The article assumes that you are hosting the Unifi Network Controller onsite which is why most of the tables say Incoming. Since the Unifi Network Controller is hosted in the cloud for this example, you will need to make sure these ports are open outbound.
- You DO NOT need to open any ports inbound.
Security Service Exclusions
It is recommended that you exclude Unifi equipment from the security services of the SonicWall as some of the Security Services will interfere with the management traffic.
You will first need to ensure that the Unifi equipment has static IP addresses.
To do this:
- Create an Address Object Group that contains the IP addresses of the Unifi equipment.
- Create a Service Object that contains the required ports.
- Exclude the Address Object Group from the Security Services by following: MSS FW Best Practices: 12 Security Services
Unifi Network (Onsite)
- These instructions apply if the Unifi Network Application is hosted onsite.
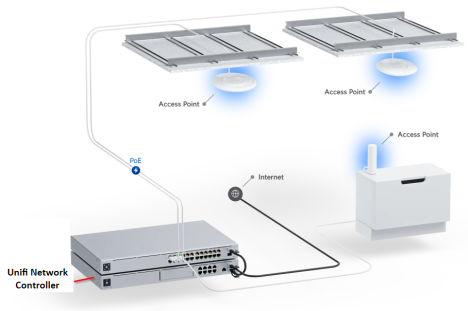
Unifi Network Hosted Onsite (Same Network)
Same Network
These notes assume that the Unifi equipment and Unifi Network application are on the same network.
Port/Service Restrictions
If the firewall has outbound port/service restrictions in place, you will need to ensure that the correct ports are open from the Unifi equipment to the WAN.
For the current list of required ports, see: UniFi Network - Required Ports Reference – Ubiquiti Support and Help Center
- The article assumes that you are hosting the Unifi Network Controller onsite which is why most of the tables say Incoming. Since the Unifi Network Controller is hosted in the cloud for this example, you will need to make sure these ports are open outbound.
- You DO NOT need to open any ports inbound.
Security Service Exclusions
It is recommended that you exclude Unifi equipment from the security services of the SonicWall as some of the Security Services will interfere with the management traffic.
You will first need to ensure that the Unifi equipment has static IP addresses.
To do this:
- Create an Address Object Group that contains the IP addresses of the Unifi equipment.
- Create a Service Object that contains the required ports.
- Exclude the Address Object Group from the Security Services by following: MSS FW Best Practices: 12 Security Services
Unifi Network Hosted Onsite (Different Networks)
Different Networks
These notes assume that the Unifi equipment and Unifi Network application are on different networks.
DHCP Option 43
You will need to create this so that the management traffic from the AP is forwarded to the Unifi Network application.
- In the SonicWall firewall, navigate to Network > DHCP Server > Advanced and click Add Option
- Fill in the following:
- Option Name: Enter the name for this (Unifi Cloud for example).
- Option Number: 43 (Vendor Specific Information)
- Option Array: Check this box
- Option Value: Enter the Unifi Network IP address in One Byte Data. To do this, take the Unifi Network IP and:
- Replace each “.” with a semicolon.
- Add “1;4;” to the front of the IP address.
- For example, if the IP address is “123.45.67.89”, you will enter “1;4;123;45;67;89” in the Option Value field.

- Click Ok twice.
Access Point DHCP
Now we need to assign this DHCP option to the Unifi Access Points. To do this you can either edit the Dynamic DHCP scope for the network that the APs are on, or create static DHCP entries for each AP to statically assign them an IP address based on their MAC address.
- Whichever option you go with, make sure to select the DHCP option created above on the Advanced page under DHCP Generic Options

Port/Service Restrictions
Since the Unifi equipment needs to communicate to the Unifi Network application, you will need to ensure the required ports are opened from the equipment to the Network application.
For the current list of required ports, see: UniFi Network - Required Ports Reference – Ubiquiti Support and Help Center
- The article assumes that you are hosting the Unifi Network Controller onsite which is why most of the tables say Incoming. Since the Unifi Network Controller is hosted in the cloud for this example, you will need to make sure these ports are open from the Unifi equipment to the Network application.
- You DO NOT need to open any ports inbound.
Security Service Exclusions
It is recommended that you exclude Unifi equipment & Network application from the security services of the SonicWall as some of the Security Services will interfere with the management traffic.
You will first need to ensure that the Unifi equipment has static IP addresses.
To do this:
- Create an Address Object Group that contains the IP addresses of the Unifi equipment.
- Create a Service Object that contains the required ports.
- Exclude the Address Object Group from the Security Services by following: MSS FW Best Practices: 12 Security Services
Related Articles
- Cloud Threat Analytics: SaaS Alerts Onboarding
- NDR: Integration Guide (Start Here)
- MSS CAS Migrations: Frequently Asked Questions (FAQs)
Categories
- Managed Security Services > Firewall Monitoring and Management > Firewall Configuration and Best Practices






 YES
YES NO
NO