-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to allow applications on SonicOSX 7.0



Description
SonicWall has a rich set of application signatures for various applications that can also be categorized into multiple categories, such as P2P, social networking and risk levels. These signatures can restrict application use to only those applications that are approved by the organization.
SonicWall has an implicit deny rule which blocks all traffic. To allow a specific application like Teamviewer we would need to add a security rule to specifically allow it. Security rules consists of three sections, match criterion, action and action profile. This KB gives you the configuration steps for security rules
 NOTE: When creating positive app match rule, make sure to allow all related application signatures so that application works without issues. It is recommended to create ANY ANY ANY allow rule from LAN to WAN zone and find out the required application signatures that are needed to run.
NOTE: When creating positive app match rule, make sure to allow all related application signatures so that application works without issues. It is recommended to create ANY ANY ANY allow rule from LAN to WAN zone and find out the required application signatures that are needed to run.
Resolution
We would need to create and add the following to security policies to allow certain applications.
Before a connection can be made, the end machine would need to perform DNS resolution of the URLs that it needs to connect to for this application to work. Since we have an implicit deny rule, DNS traffic needs to be allowed as well.
To create the DNS-related Security Policy:
- Navigate to Policy | Rules and Policies | Security policy tab and click on Top at the bottom of the screen. This adds the new policy at the top of the list. You might need to adjust its priority based on other rules you have.
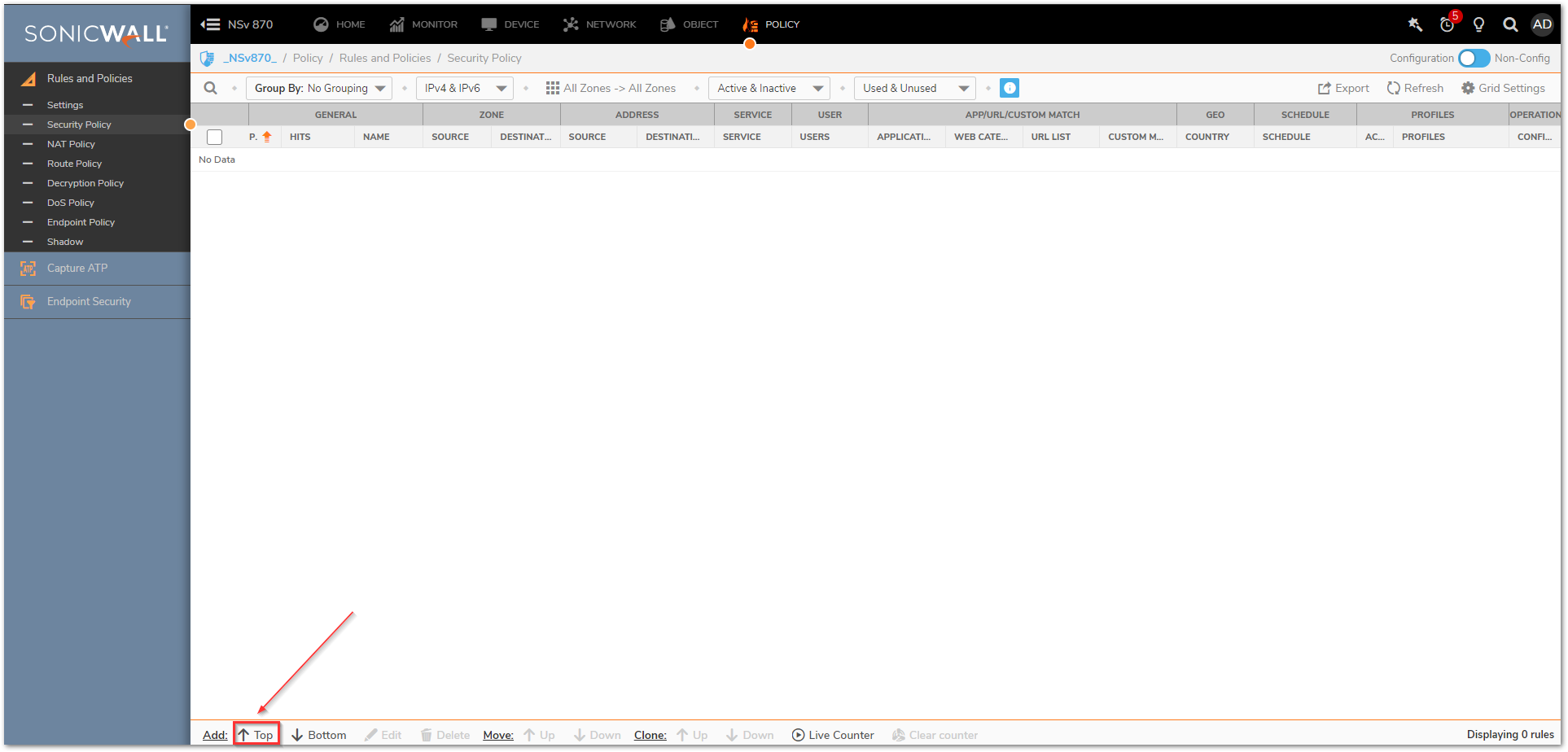
- Assign a relevant name and in the Source/Destination tab, you can select many fields like source/destination zones, address, services, users and geo-location settings. Under the Destination, select the Port/Services as 'DNS(Name Service)'.

- Leave everything in the App/URL/Custom Match tab on defaults.
- Select the Default Profile as the Security Rule Action. Make sure that the Action is set to Allow and the policy is in Enable state. Click Add.

 NOTE: This policy can also be created using the DNS protocol application signature, but service is used in this example.
NOTE: This policy can also be created using the DNS protocol application signature, but service is used in this example.
To create the Allow Application related Security Policy:
 TIP: Some of the application signatures need DPI SSL. You can refer to the KB article: How to create a Decryption Policy on SonicOSX 7.0? for more details on the decryption rule configuration. Navigate to Objects | Match Objects | Applications and verify the signatures to confirm. The signatures have [Reqs DPI SSL CI] next to it that are dependent on DPI SSL Client inspection.
TIP: Some of the application signatures need DPI SSL. You can refer to the KB article: How to create a Decryption Policy on SonicOSX 7.0? for more details on the decryption rule configuration. Navigate to Objects | Match Objects | Applications and verify the signatures to confirm. The signatures have [Reqs DPI SSL CI] next to it that are dependent on DPI SSL Client inspection.

 EXAMPLE: Let's walk through the steps to allow the Remote Access application Teamviewer.
EXAMPLE: Let's walk through the steps to allow the Remote Access application Teamviewer.
- Navigate to Policy | Rules and Policies | Security policy tab and click on Bottom at the bottom of the screen. This adds the new policy at the bottom of the list. You might need to adjust its priority based on other rules you have.
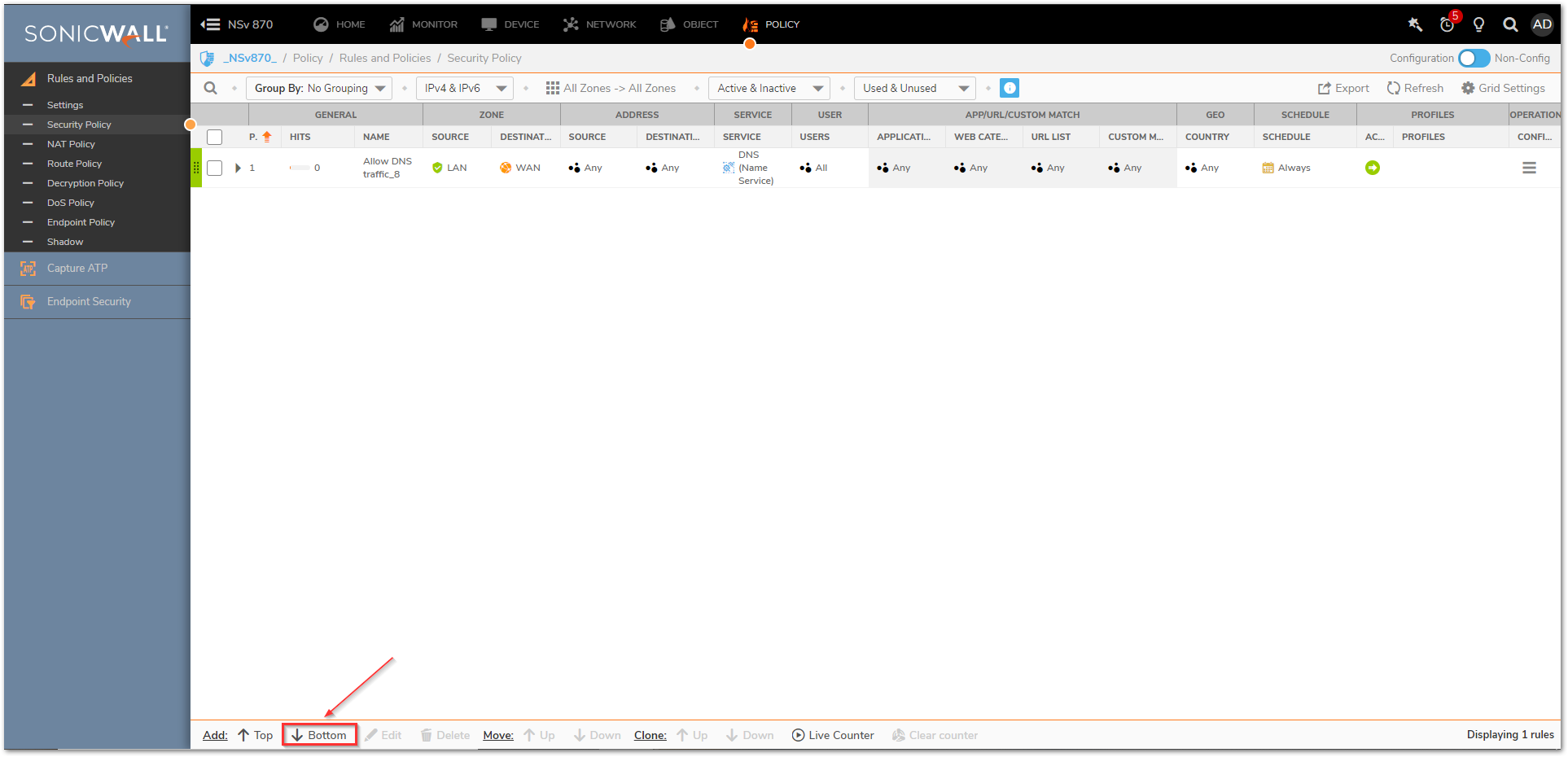
- Assign a relevant name and in the Source/Destination tab, you can select many fields like source/destination zones, address, services, users and geo-location settings.
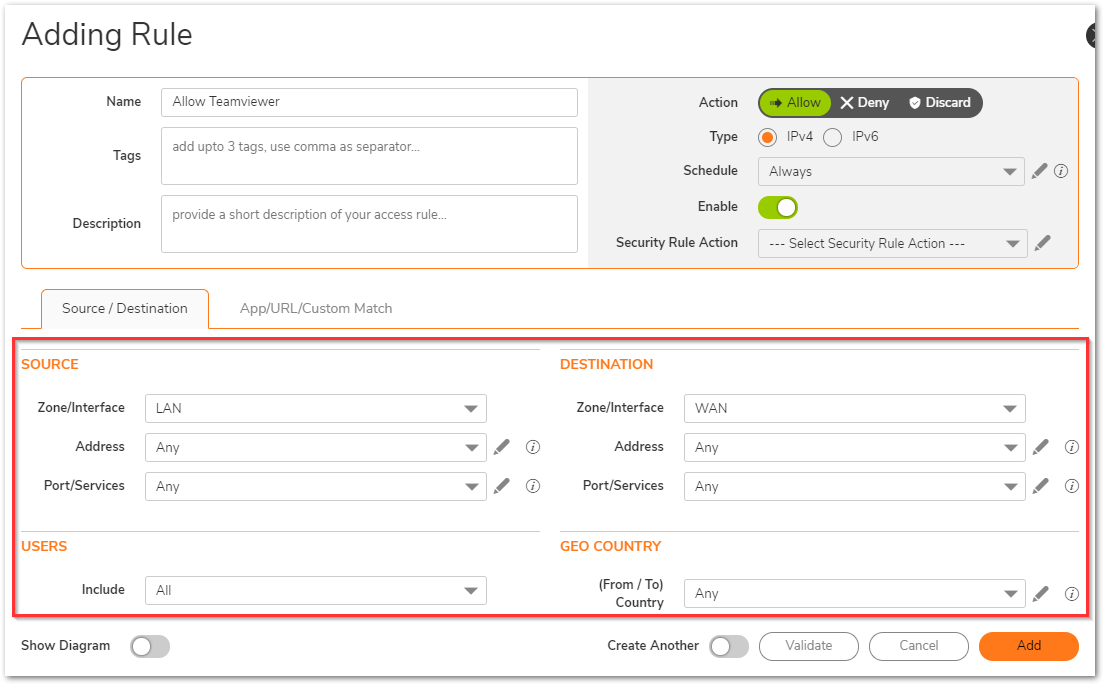
- Under App/URL/Custom Match, use the radio button for 'Match Operation' as OR. Then, select the pencil icon to add a new Application Match Group.
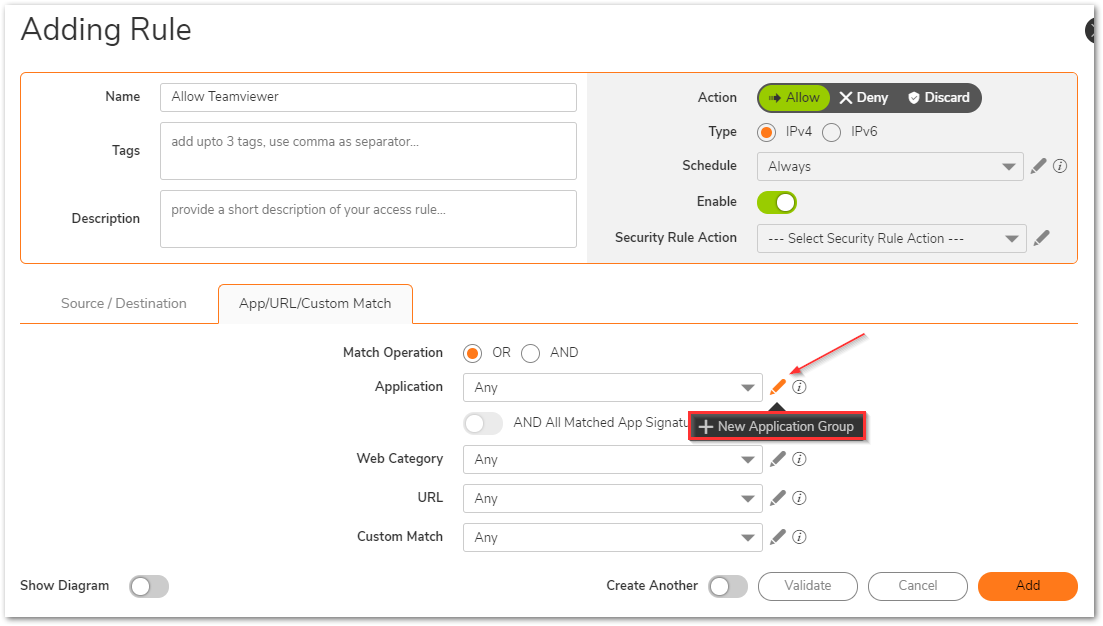
Select the allowed applications using the right arrow, then move them to the right. Click Save.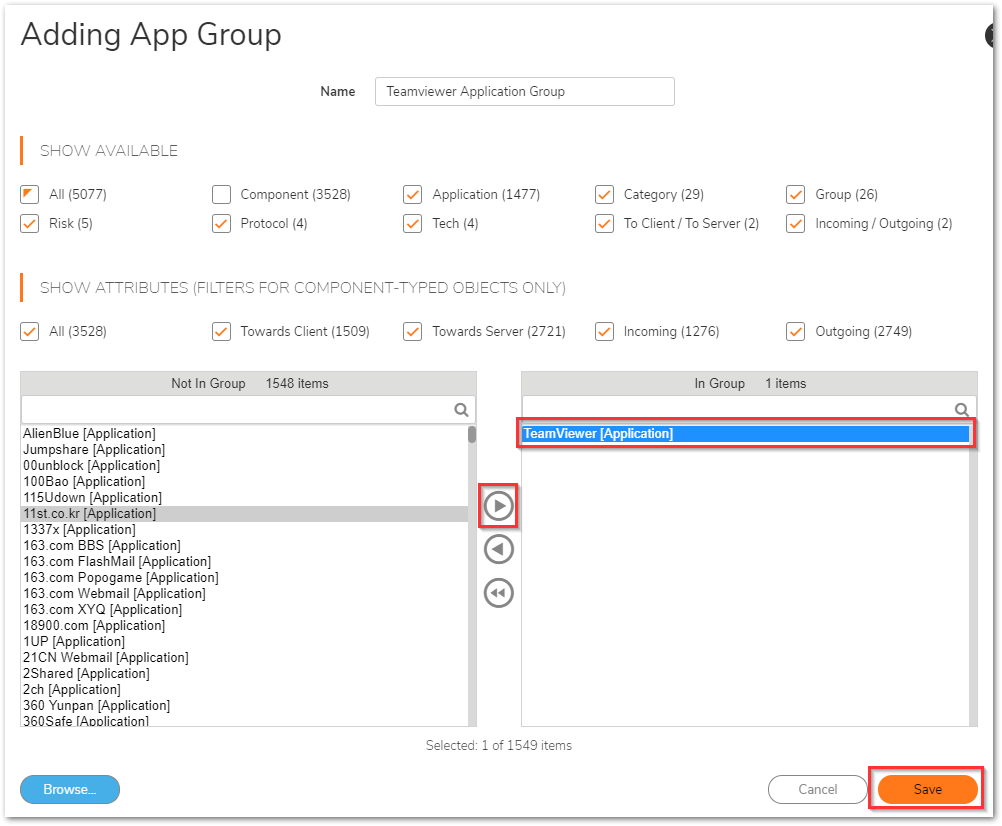
Leave other fields on this tab set to Any.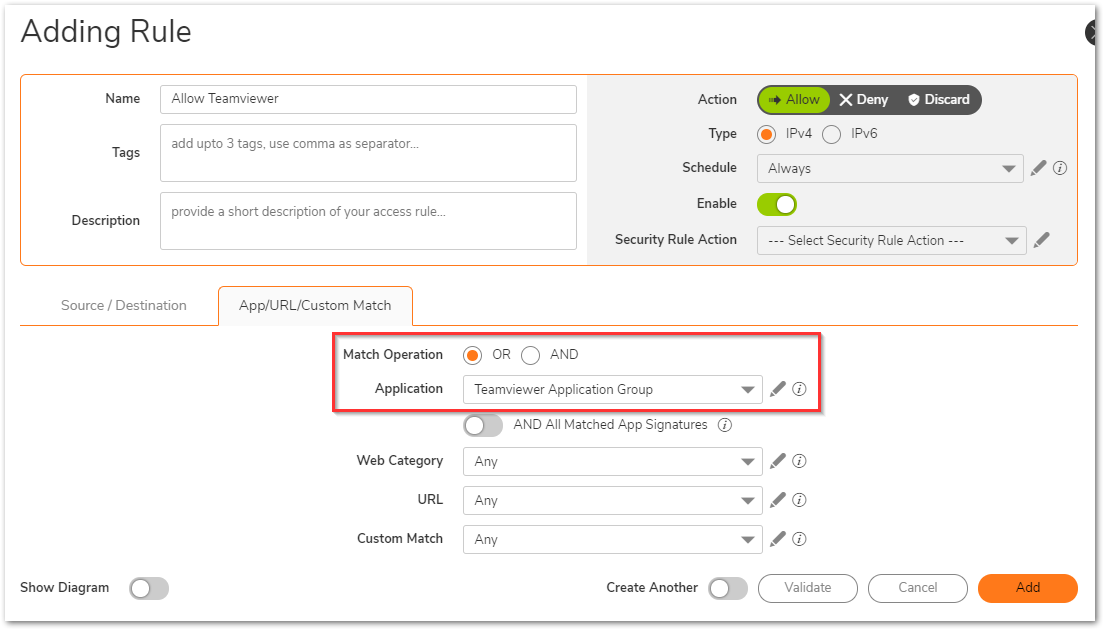
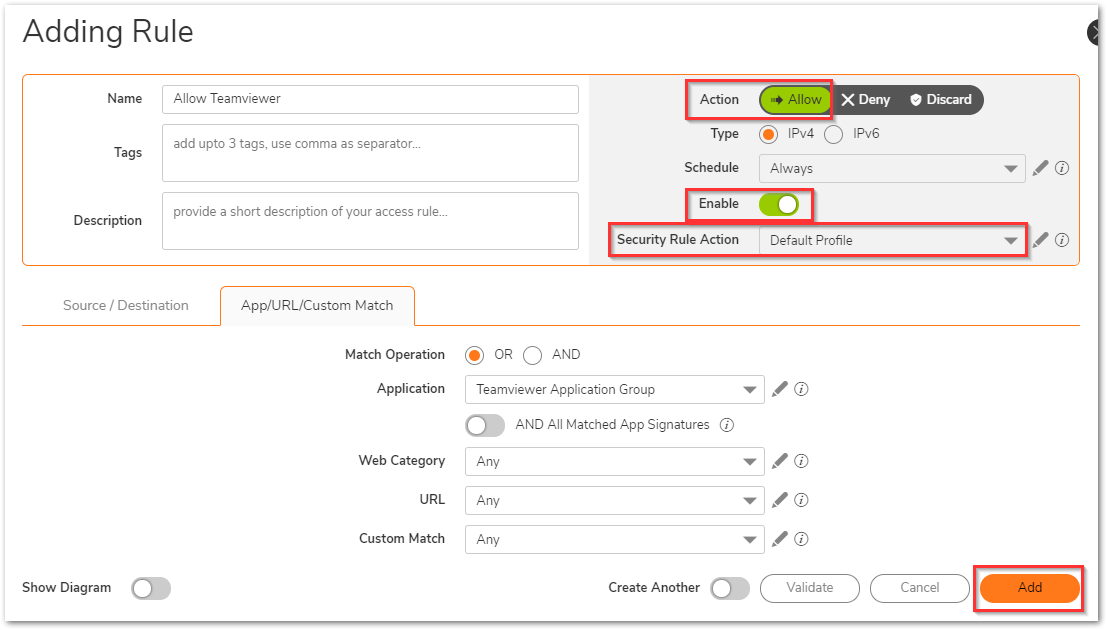
Under the Security Rule Action dropdown, select Default profile, which has everything set to allowed.- On the Security Policy, make sure that the Action is set to Allow and the policy is in Enable state. Click Add.
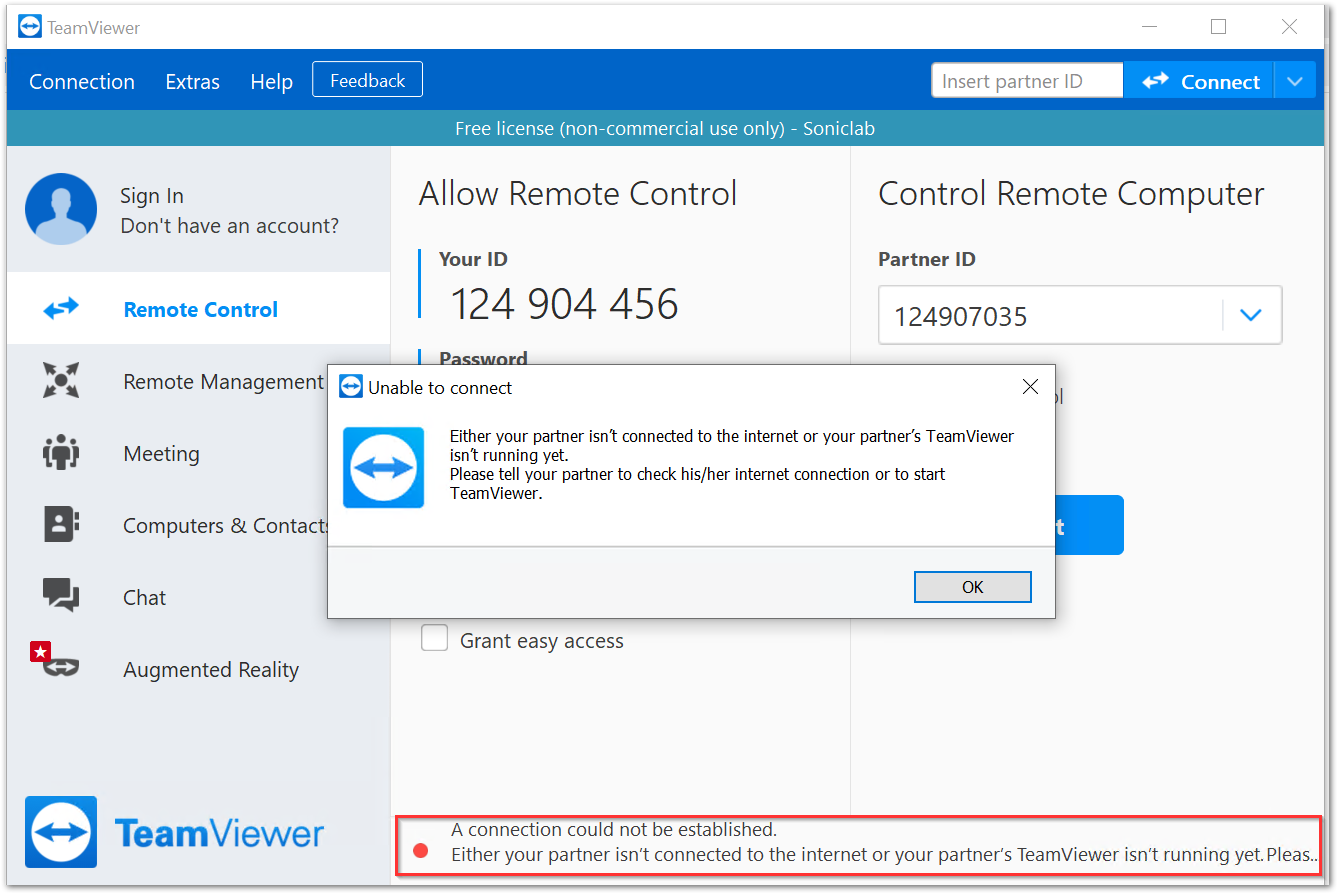
- Without the above security rules, a machine that already has Teamviewer installed, might run into errors while making a connection. If the app isn't alreeady installed, the user will not be allowed to visit teamviewer.com for download.
- After adding the security rules, the Team viewer session asks for Password. Once it's entered, users can connect just fine.

 TIP: For applications that also have websites like youtube.com, facebook.com etc might not load completely or intermittently as they could have several intermediate cdn servers, or image signatures loaded from various sites that are not part of the mentioned signatures.In those scenarios, it would be best to create an Any, Any, Any allow rule at the bottom of your security policies list and find out those missing signatures. You can use the packet monitor tool and check for the signatures that are needed along with the ones already allowed. You can refer to the KB article: How Can I Setup And Utilize The Packet Monitor Feature For Troubleshooting? for more details on Packet monitor tool.
TIP: For applications that also have websites like youtube.com, facebook.com etc might not load completely or intermittently as they could have several intermediate cdn servers, or image signatures loaded from various sites that are not part of the mentioned signatures.In those scenarios, it would be best to create an Any, Any, Any allow rule at the bottom of your security policies list and find out those missing signatures. You can use the packet monitor tool and check for the signatures that are needed along with the ones already allowed. You can refer to the KB article: How Can I Setup And Utilize The Packet Monitor Feature For Troubleshooting? for more details on Packet monitor tool. - With SonicOSX 7.0, there is an App column that displays the App ID. If you hover over it, the actual application signature shows up (see below).
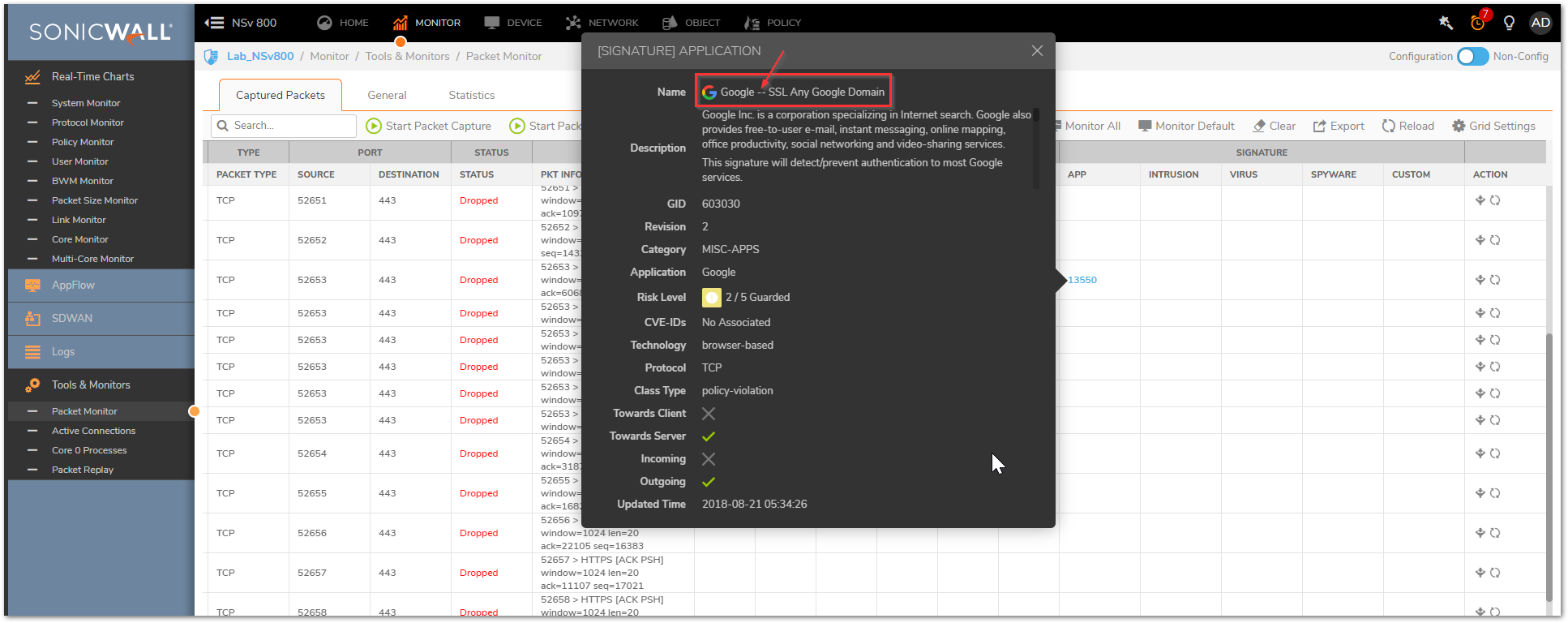
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM






 YES
YES NO
NO