-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How can I make WAN GroupVPN Route All traffic Policy for one user's GVC policy?



Description
This configuration allows you to control the behavior of a single WAN GroupVPN policy to behave differently for different users or user groups. Using one policy, you can have some users on a route all traffic policy and other users on a Split Tunnel (see definition below) policy. The different policy types are based on the Users or User Groups VPN Access settings, and are not based on global settings in the WAN GroupVPN policy configuration.
The term Split Tunnel in the world of VPN means a policy in which the VPN provides access to logically-defined protected networks behind a VPN Gateway device, such as a SonicWall UTM firewall, while all other traffic towards the Internet is unchanged and goes out the local Internet gateway. A route all VPN policy would take all traffic from the remote user and terminate it on the target network, where it is unpacked and inspected for the original desired destination IP addresses. For destinations which are inside the target network, they are sent directly, and for destinations toward the Internet, they are subject to NAT and then sent out the target network's WAN so that it appears to originate there, not from the remote user's part of the Internet.
 NOTE: in SonicOS 5.6 and beyond, the VPN Access configurations used in this technique also dictate the networks to which UTM SSLVPN remote users have access. This is important to know. Any user who is given the properties needed for GVC route all policy will also have settings appropriate for tunnel all NetExtender connections. NetExtender in split tunnel mode will work properly, and so will tunnel all mode if that checkbox is enabled on the SSLVPN | Client Routes screen.
NOTE: in SonicOS 5.6 and beyond, the VPN Access configurations used in this technique also dictate the networks to which UTM SSLVPN remote users have access. This is important to know. Any user who is given the properties needed for GVC route all policy will also have settings appropriate for tunnel all NetExtender connections. NetExtender in split tunnel mode will work properly, and so will tunnel all mode if that checkbox is enabled on the SSLVPN | Client Routes screen.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
- Navigate to Network | IPSec VPN | Rules and Settings.
- Edit the WAN GroupVPN, on the WAN GroupVPN policy, on the Client tab, set Split Tunnel, in the section Allow Connections to.
- Set the Virtual adapter settings to DHCP lease.( Set Default Route as this Gateway should be disabled).
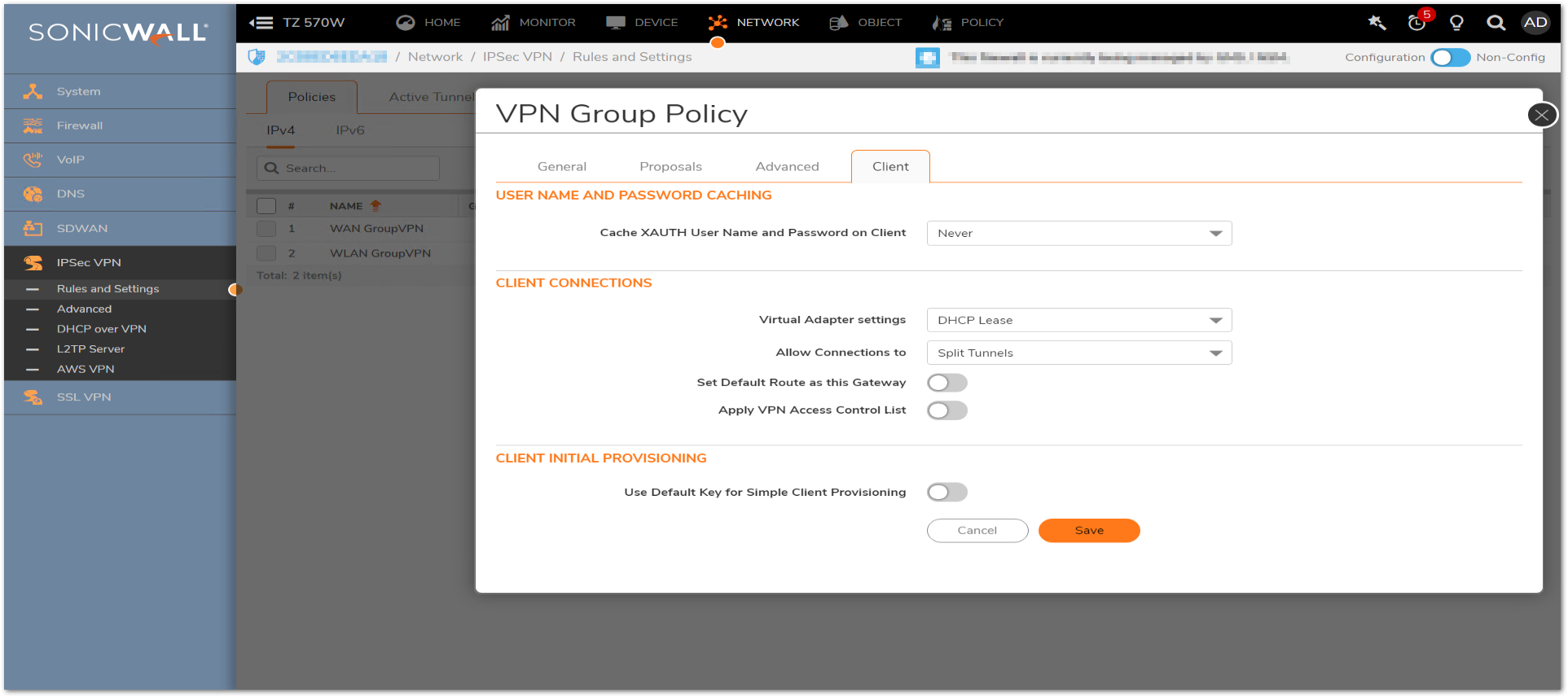
- On the WAN GroupVPN policy, on the Advanced tab, make sure that the Default Gateway field is blank, and make sure that the Require authentication of VPN Clients by XAUTH checkbox is enabled. The User Group Trusted Users is selected by default for XAUTH. This group contains all local users, but other custom user groups can be used.
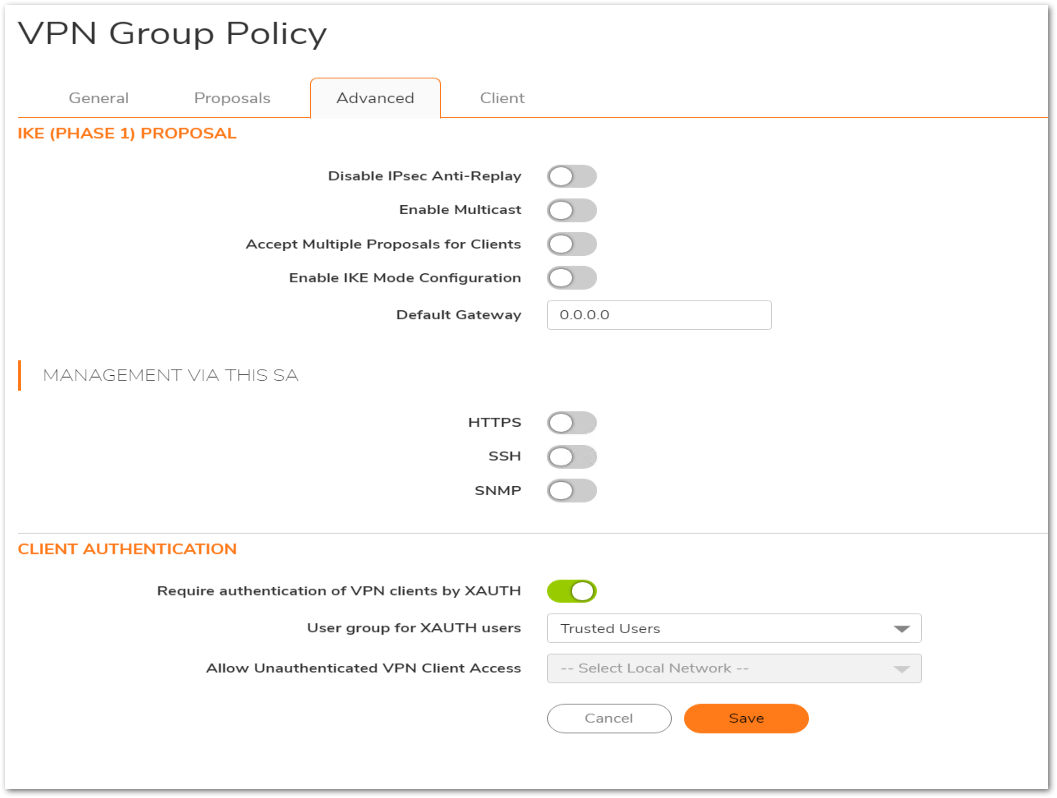
- Navigate to Device | Local Users and Groups; for each user, there is a list of assigned network objects in the VPN Access tab. This is what dictates the type of GVC policy they have.
- For Global VPN Client users who need to have a route all Policy, you must include the object WAN RemoteAccess Networks ; this object has a value of 0.0.0.0 and is what makes the user's policy a route all Global VPN client policy.
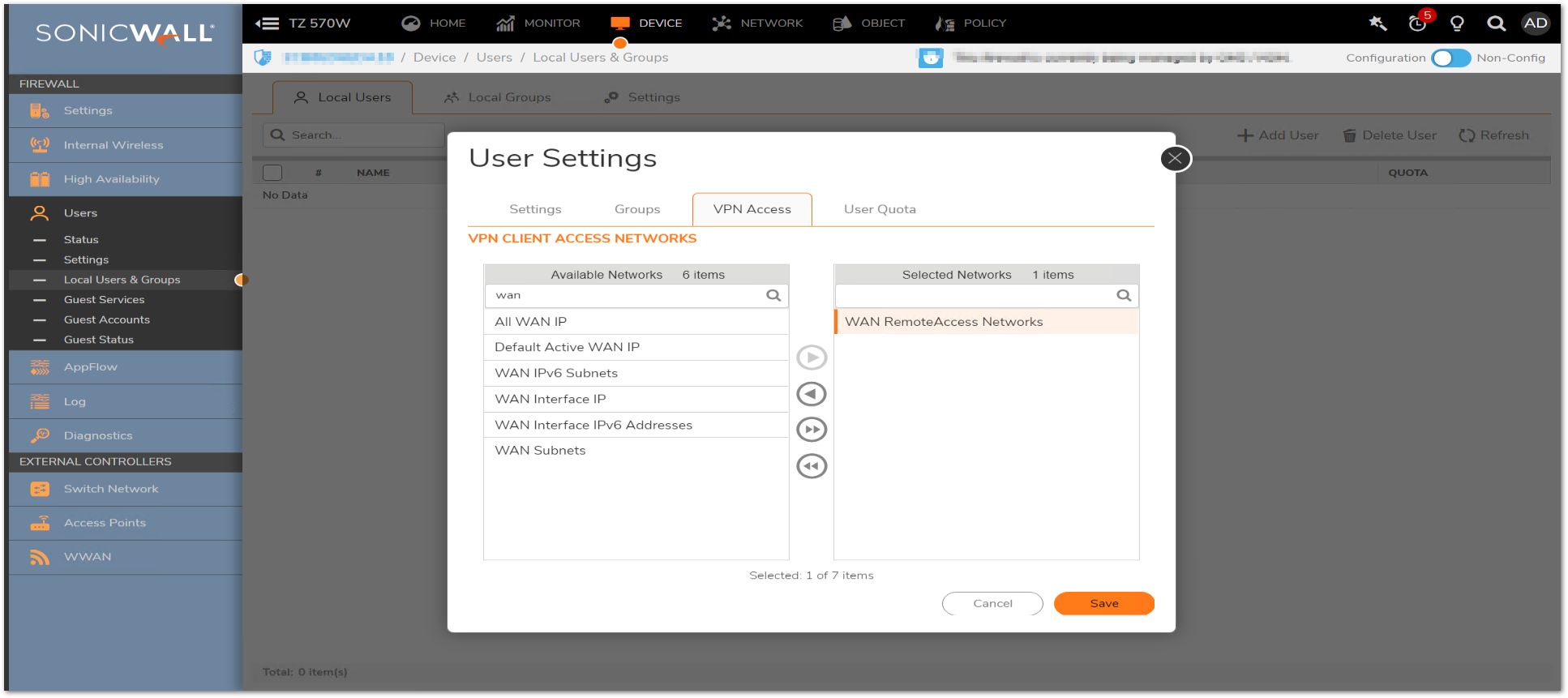
- For all other users, who need Split Tunnel GVC policies, you can assign them a variety of internal network objects, such as LAN Subnets, X0 Subnet, or Firewalled Subnets.
- Navigate to Policy |Rules and Policies | NAT rules You must create a custom NAT policy for the Internet traffic which originates from your remote user who has a route all GVC policy. This NAT policy, if written in the syntax shown below, will have no effect on anything but Internet-bound traffic coming out of either GVC or Site-to-Site Route All VPN Policies. The syntax shown below is correct in most cases. Alternative or additional NAT policies may be needed if other interfaces (e.g., X2, X3, OPT, etc.) are used for inbound, route all VPN policies.
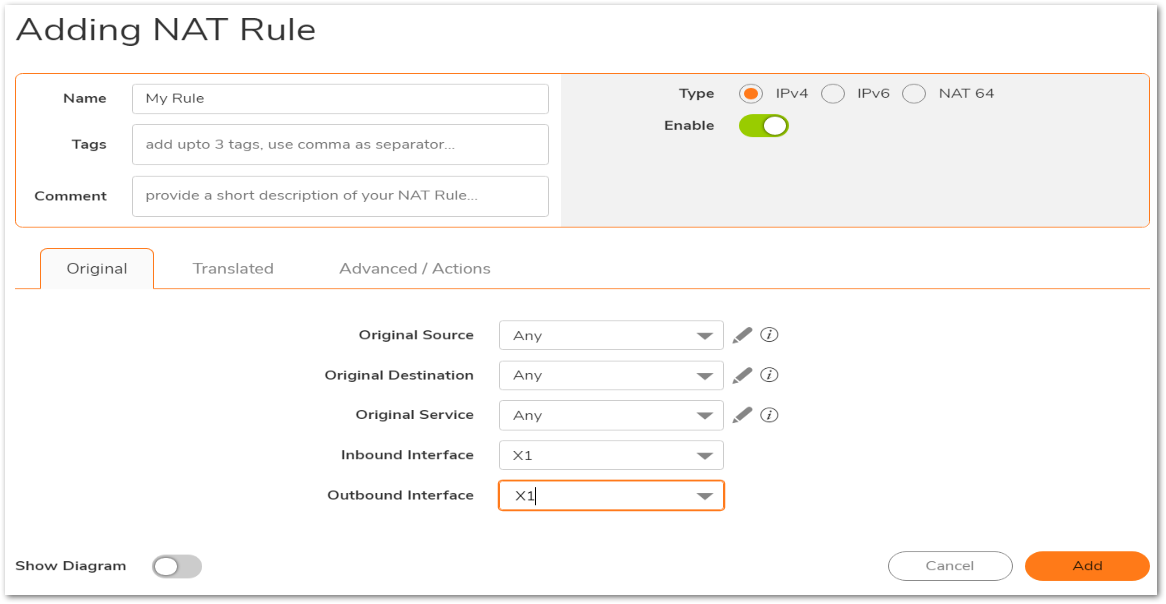
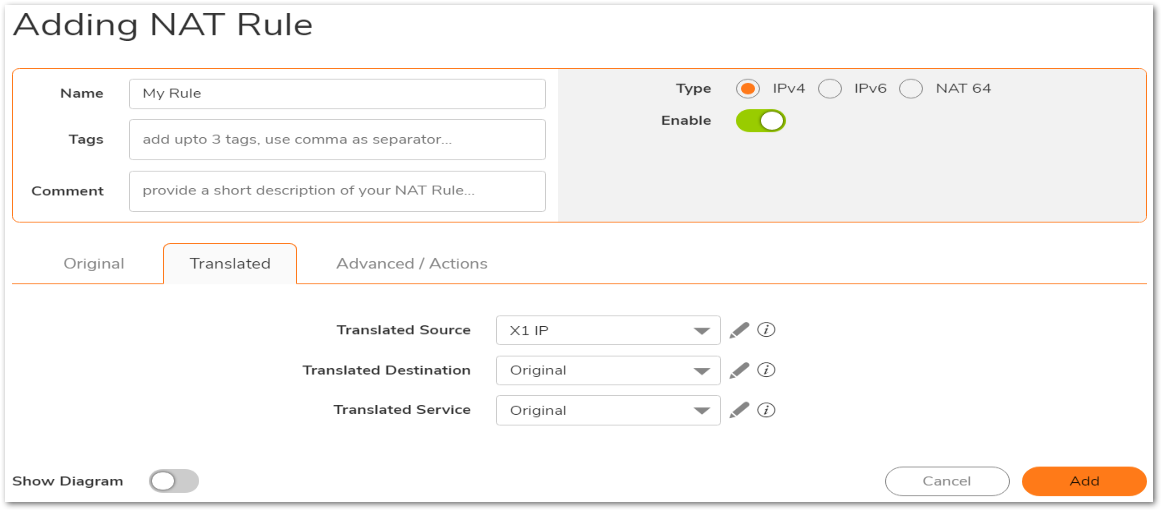
- The above NAT Policy screenshot has the following settings.
- Original Source: Any
- Translated Source: X1 IP
- Original Destination: Any
- Translated Destination: Original
- Original Service: Any
- Translated Service: Original
- Inbound Interface: X1
- Outbound Interface: X1
 NOTE: No custom access rules are needed, under Rules|Access Rules SonicOS automatically creates a rule allowing traffic from VPN to WAN for you.
NOTE: No custom access rules are needed, under Rules|Access Rules SonicOS automatically creates a rule allowing traffic from VPN to WAN for you.

Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
- Click Manage in the top navigation menu.
- Navigate to VPN | Base Settings screen and edit the WAN GroupVPN, on the WAN GroupVPN policy, on the Client tab, set Split Tunnel, in the section Allow Connections to.
- Set the Virtual adapter settings to DHCP lease.( Set Default Route as this Gateway should be disabled).
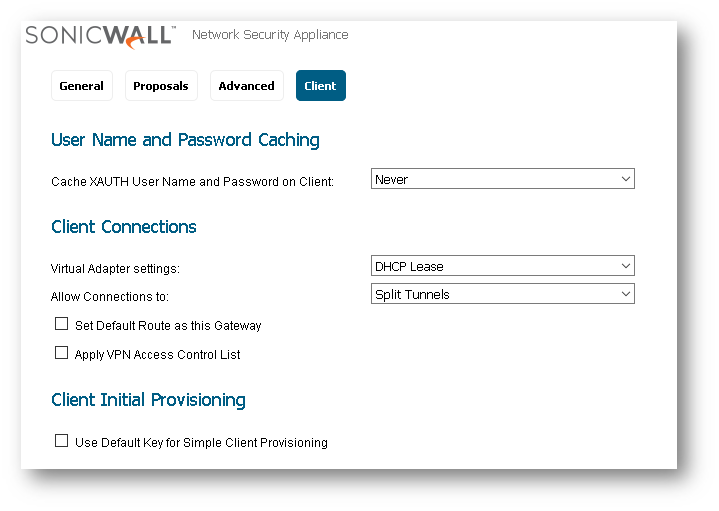
- On the WAN GroupVPN policy, on the Advanced tab, make sure that the Default Gateway field is blank, and make sure that the Require authentication of VPN Clients by XAUTH checkbox is enabled. The User Group Trusted Users is selected by default for XAUTH. This group contains all local users, but other custom user groups can be used.
- Navigate to Users | Local Users screen; for each user, there is a list of assigned network objects in the VPN Access tab. This is what dictates the type of GVC policy they have.
- For Global VPN Client users who need to have a route all Policy, you must include the object WAN RemoteAccess Networks ; this object has a value of 0.0.0.0 and is what makes the user's policy a route all Global VPN client policy.
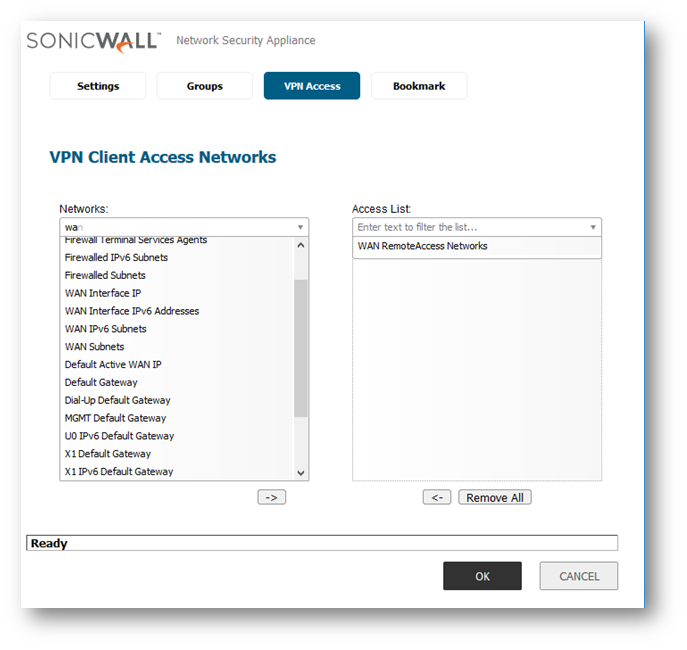
- For all other users, who need Split Tunnel GVC policies, you can assign them a variety of internal network objects, such as LAN Subnets, X0 Subnet, or Firewalled Subnets.

- Navigate to Rules|NAT Policies You must create a custom NAT policy for the Internet traffic which originates from your remote user who has a route all GVC policy. This NAT policy, if written in the syntax shown below, will have no effect on anything but Internet-bound traffic coming out of either GVC or Site-to-Site Route All VPN Policies. The syntax shown below is correct in most cases. Alternative or additional NAT policies may be needed if other interfaces (e.g., X2, X3, OPT, etc.) are used for inbound, route all VPN policies.
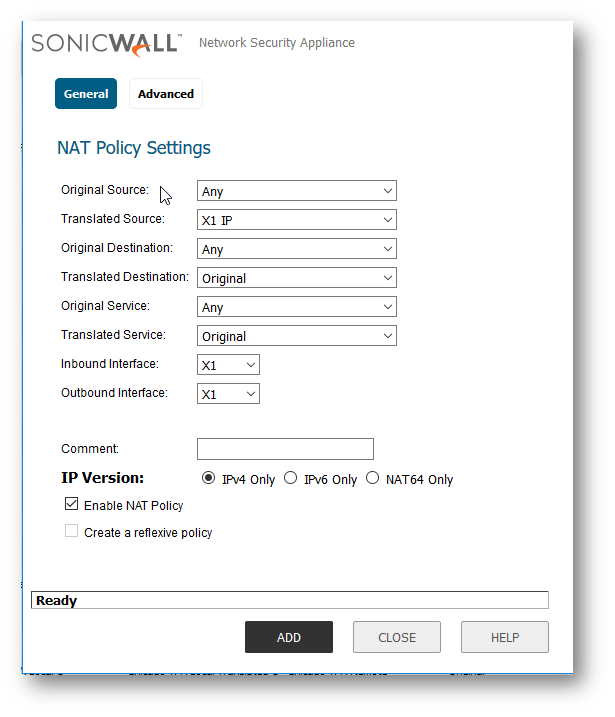
- The above NAT Policy screenshot has the following settings.
- Original Source: Any
- Translated Source: X1 IP
- Original Destination: Any
- Translated Destination: Original
- Original Service: Any
- Translated Service: Original
- Inbound Interface: X1
- Outbound Interface: X1
 NOTE: No custom access rules are needed, under Rules|Access Rules SonicOS automatically creates a rule allowing traffic from VPN to WAN for you.
NOTE: No custom access rules are needed, under Rules|Access Rules SonicOS automatically creates a rule allowing traffic from VPN to WAN for you.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
- Navigate to VPN | Settings screen and edit the WAN GroupVPN, on the WAN GroupVPN policy, on the Client tab, set Split Tunnel in the section Allow Connections to.
- Set the Virtual adapter settings to DHCP lease. ( Set Default Route as this Gateway should be disabled).
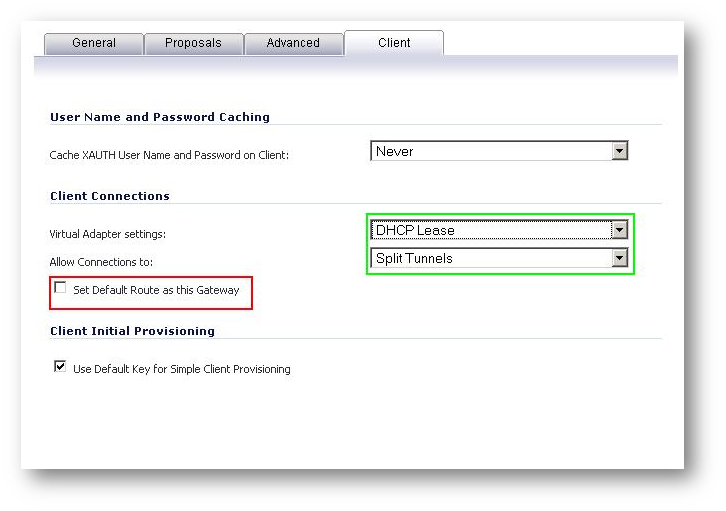
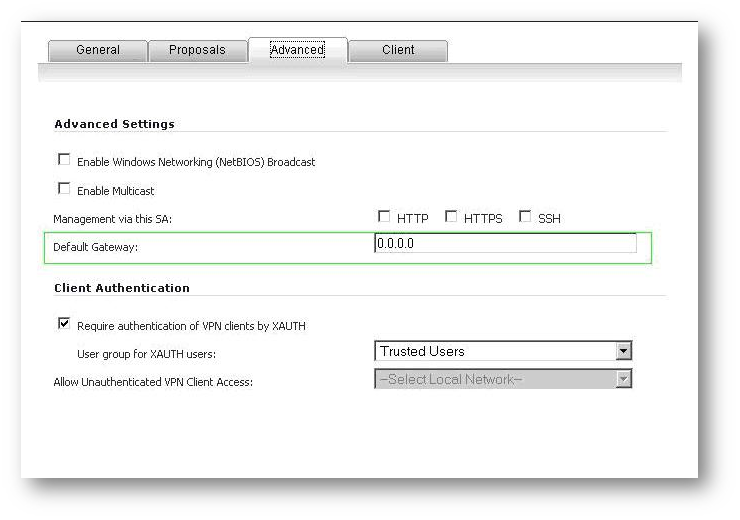
- On the WAN GroupVPN policy, on the Advanced tab, make sure that the Default Gateway field is blank, and make sure that the Require authentication of VPN Clients by XAUTH checkbox is enabled. The User Group Trusted Users is selected by default for XAUTH. This group contains all local users, but other custom user groups can be used.
- Navigate to Users | Local Users screen; for each user, there is a list of assigned network objects in the VPN Access tab. This is what dictates the type of GVC Policy they have.
- For Global VPN client users who need to have a route all Policy, you must include the object WAN RemoteAccess Networks ; this object has a value of 0.0.0.0 and is what makes the user's policy a route all Global VPN client policy.
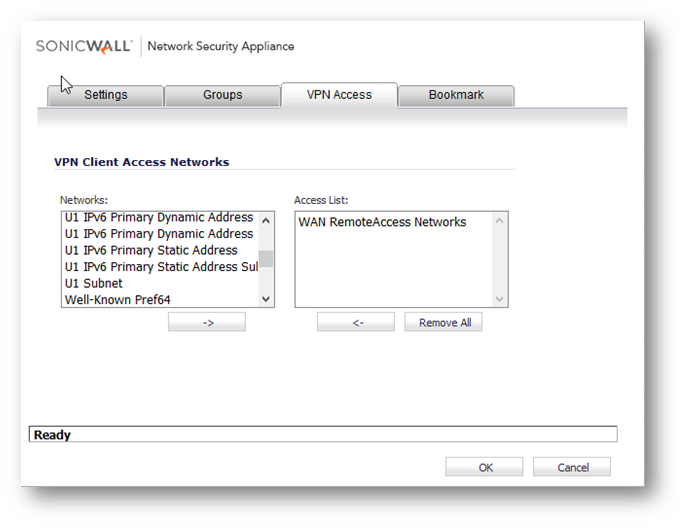
- For all other users, who need Split Tunnel GVC policies, you can assign them a variety of internal network objects, such as LAN Subnets, X0 Subnet, or Firewalled Subnets.
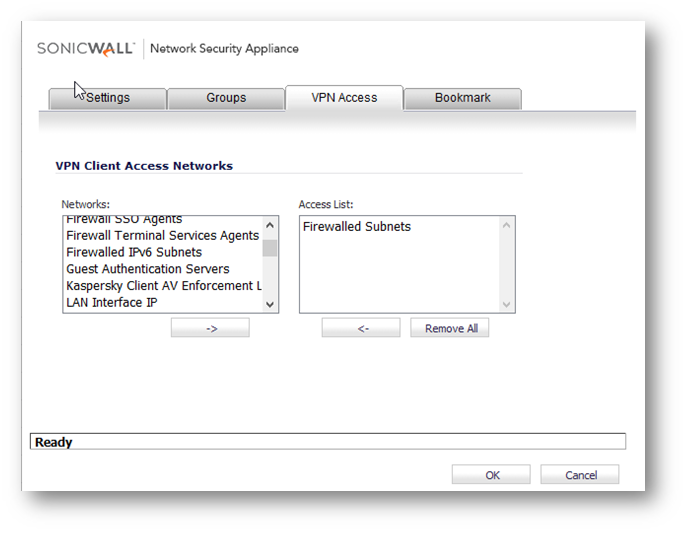
- For Global VPN client users who need to have a route all Policy, you must include the object WAN RemoteAccess Networks ; this object has a value of 0.0.0.0 and is what makes the user's policy a route all Global VPN client policy.
- You must create a custom NAT policy for the Internet traffic which originates from your remote user who has a route all GVC policy. This NAT Policy, if written in the syntax shown below, will have no effect on anything but Internet-bound traffic coming out of either GVC or Site-to-Site Route All VPN Policies. The syntax shown below is correct in most cases. Alternative or additional NAT policies may be needed if other interfaces (e.g., X2, X3, OPT, etc.) are used for inbound, route all VPN policies.
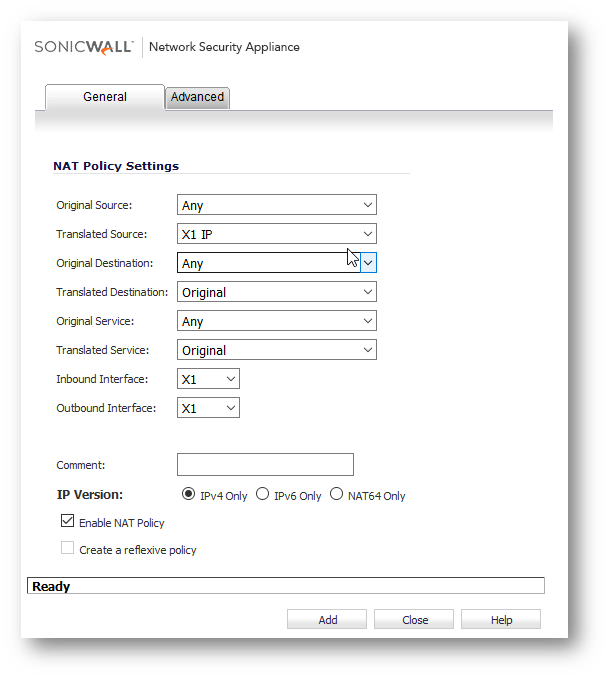
- The above NAT Policy screenshot has the following settings.
- Original Source: Any
- Translated Source: X1 IP
- Original Destination: Any
- Translated Destination: Original
- Original Service: Any
- Translated Service: Original
- Inbound Interface: X1
- Outbound Interface: X1
 NOTE: For some models, the names of the correct network address objects or interfaces may be different, such as this variation you would see on a TZ170 running SonicOS Enhanced.
NOTE: For some models, the names of the correct network address objects or interfaces may be different, such as this variation you would see on a TZ170 running SonicOS Enhanced.
- The above NAT Policy screenshot has the following settings.
- Original Source: Any
- Translated Source: WAN Primary IP
- Original Destination: Any
- Translated Destination: Original
- Original Service: Any
- Translated Service: Original
- Inbound Interface: WAN
- Outbound Interface: WAN
 NOTE: No custom access rules are needed, since SonicOS automatically creates a rule allowing traffic from VPN to WAN for you.
NOTE: No custom access rules are needed, since SonicOS automatically creates a rule allowing traffic from VPN to WAN for you.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > SonicWall SuperMassive 9000 Series > GVC/L2TP
- Firewalls > TZ Series > GVC/L2TP
- Firewalls > NSa Series > GVC/L2TP
- Firewalls > NSv Series > GVC/L2TP






 YES
YES NO
NO