-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
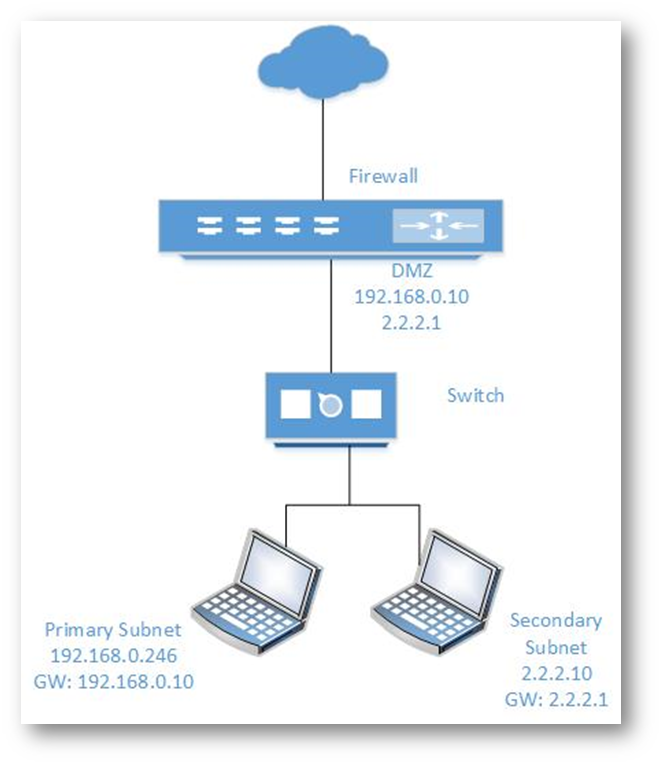
Firewall drops packets as "Bounce back traffic detected" when pinging secondary DMZ Subnet



Description
Multiple networks are connected to a single physical interface which is configured as DMZ. When we try to access the secondary subnet from main DMZ subnet, firewall drops as "Bounce back traffic detected"
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
:ECB]
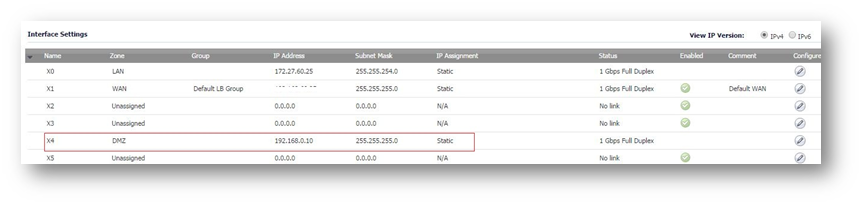
- Navigate to the Network tab and click System | Interfaces; configure an interface as DMZ with Static IP. In this case, we have configured X4 as DMZ with IP address 192.168.0.10, Subnet: 255.255.255.0
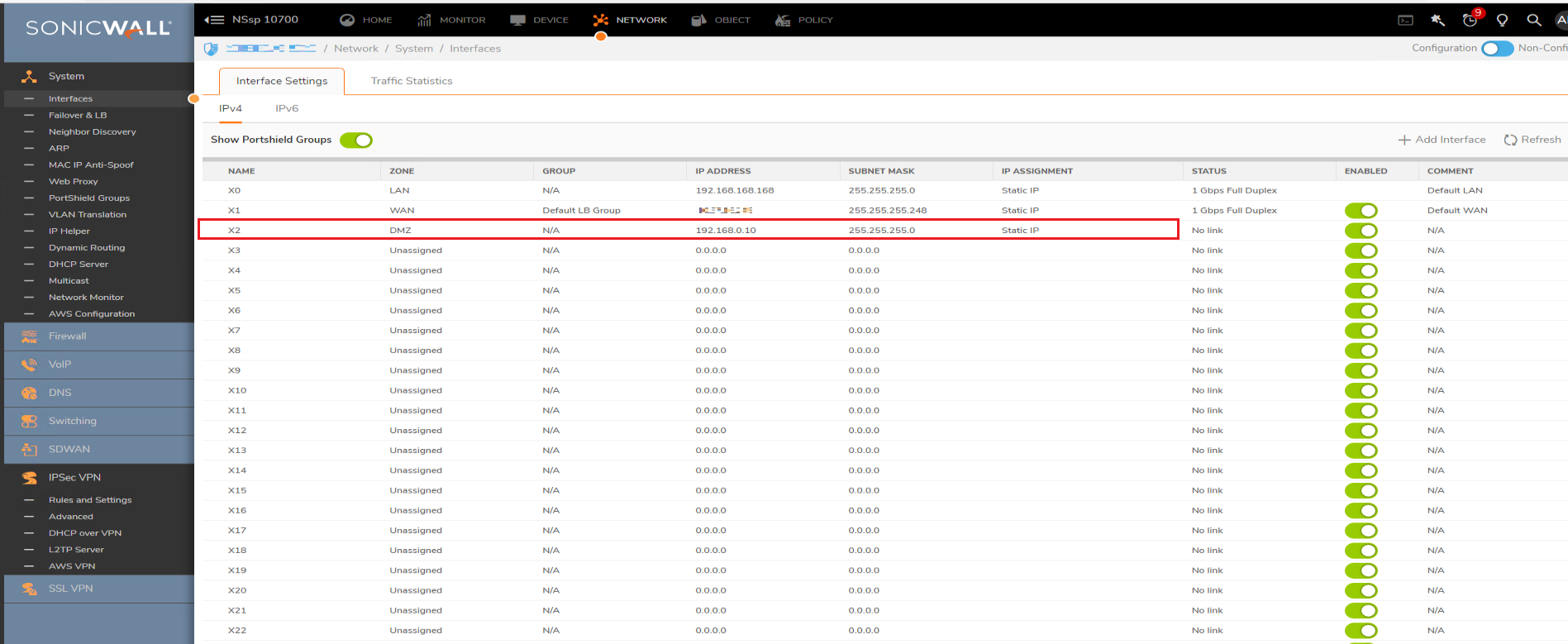
- We have one more network which is connected to the same switch without any VLANs. In this case, we have secondary network as 2.2.2.0/24
- In order for the 2.2.2.0 to go online through SonicWall, SonicWall should know how to reach it. Hence, we create a Static ARP for the network and Static Route as follows:
- Navigate to the Network tab
- Click System | ARP
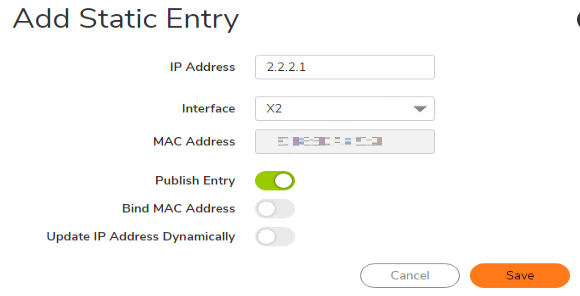
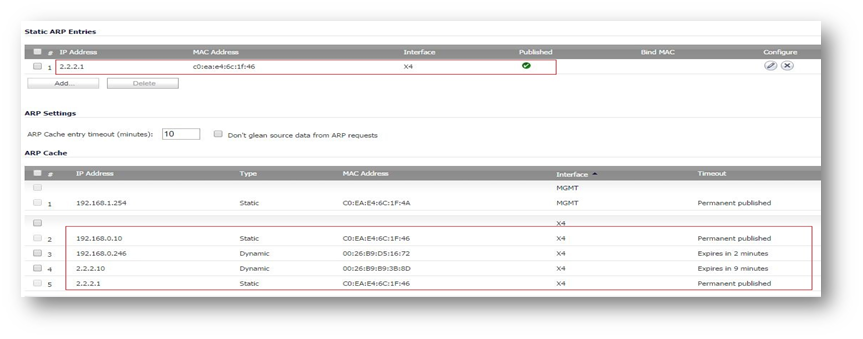
- Click Add under Static ARP and enter any one IP in the network which is going to act as gateway for that subnet.
| IP Address: | 2.2.2.1 |
| Interface: | X4 |
| Publish Entry: | Checked |


- Navigate to the Policy tab
- Click Rules and Policies | Routing Rules and click Add.
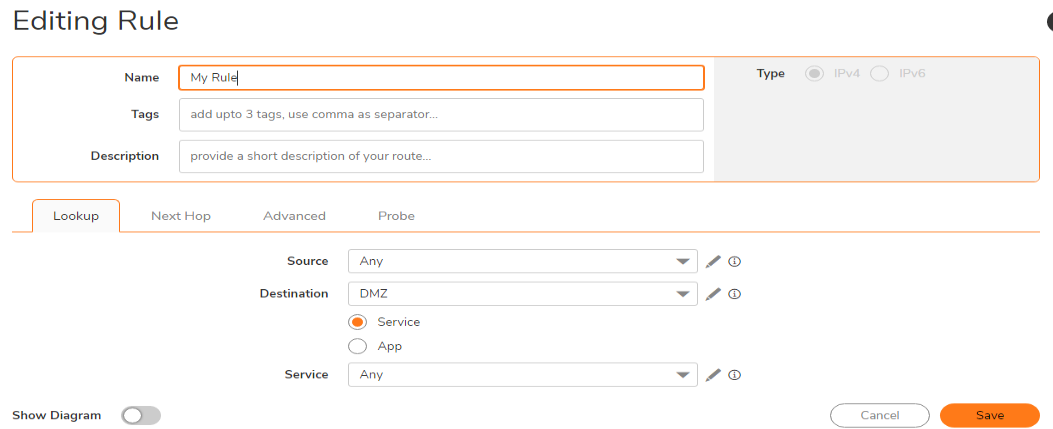
Source: Any
Destination: 2.2.2.0 / 24 (Create address object for 2.2.2.0 of type DMZ)
Service: Any
Gateway: 0.0.0.0
Interface: X4
Metric: 1
Disable Route when interface is disconnected: Checked
Click Ok.


From any computer of 192.168.0.x, try to ping the computer in 2.2.2.x.

- Navigate to the Investigate tab
- Click Packet Monitor
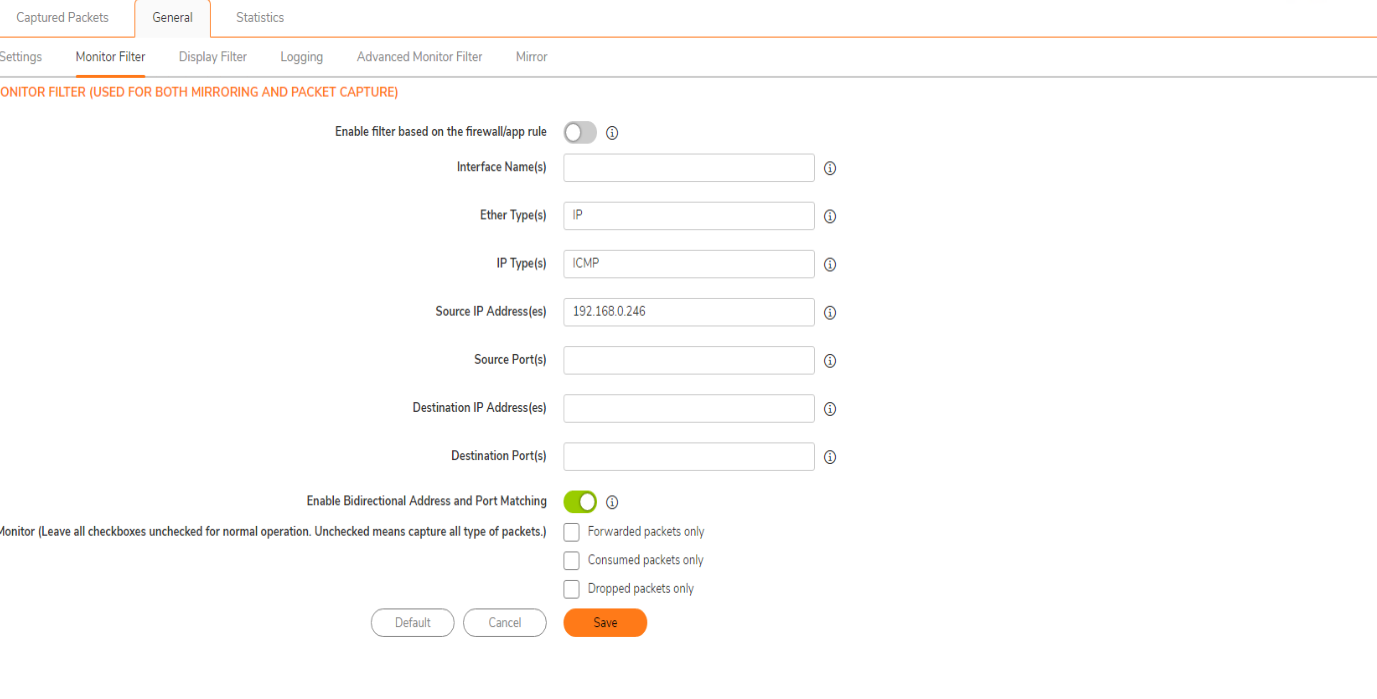
- Click Configure, go to Monitor Filter tab and configure as follows:
- Ether type: IP
- IP type: ICMP
- Source IP: 192.168.0.246
- Rest all fields should be blank
- Under Display Filter, all fields should be blank
- Under Advanced Monitor filter, enable all checkboxes. Click Ok.
- Click Clear and Start Capture.
From the computer, 192.168.0.246, try to ping 2.2.2.10.
In Packet Monitor, refresh the page and we can see the packets getting dropped by firewall.
 NOTE: This behavior is only on DMZ Interfaces. In LAN Interface, with correct ARP and route, traffic will flow without any drops.
NOTE: This behavior is only on DMZ Interfaces. In LAN Interface, with correct ARP and route, traffic will flow without any drops.
To resolve this:
- Login to SonicWall.
- The Diag page can be reached by typing in the LAN IP of the SonicWall in the browser, with a IP/sonicui/7/m/mgmt/settings/diag at the end.
 EXAMPLE: 192.168.168.168/sonicui/7/m/mgmt/settings/diag
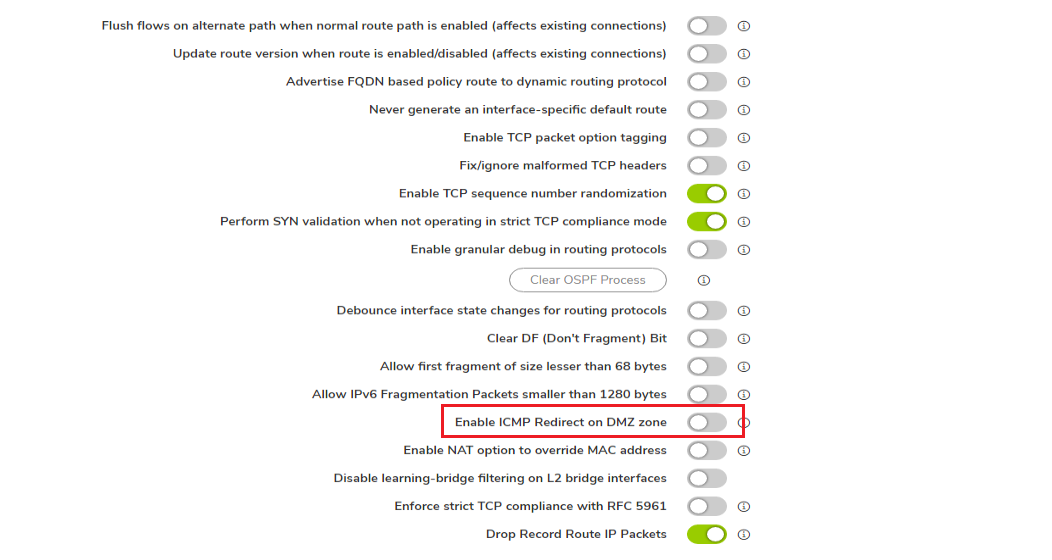
EXAMPLE: 192.168.168.168/sonicui/7/m/mgmt/settings/diag - Click Internal Settings.
- Under "Routing and Network Settings" heading, enable "Enable ICMP Redirect on DMZ zone"
- Click Accept on top and Click Close.
Now try to ping 2.2.2.x, we can see successful pings.
[BCB:6:SonicOS 6.5:ECB]- Navigate to the Manage tab and click Network | Interfaces; configure an interface as DMZ with Static IP. In this case, we have configured X4 as DMZ with IP address 192.168.0.10, Subnet: 255.255.255.0
- We have one more network which is connected to the same switch without any VLANs. In this case, we have secondary network as 2.2.2.0/24
- In order for the 2.2.2.0 to go online through SonicWall, SonicWall should know how to reach it. Hence, we create a Static ARP for the network and Static Route as follows:
- Navigate to the Manage tab
- Click Network | ARP
- Click Add under Static ARP and enter any one IP in the network which is going to act as gateway for that subnet.
| IP Address: | 2.2.2.1 |
| Interface: | X4 |
| Publish Entry: | Checked |
- Navigate to the Manage tab
- Click Network | Routing and click Add.
| Source: Any Destination: 2.2.2.0 / 24 (Create address object for 2.2.2.0 of type DMZ) Service: Any Gateway: 0.0.0.0 Interface: X4 Metric: 1 Disable Route when interface is disconnected: Checked Click Ok. | 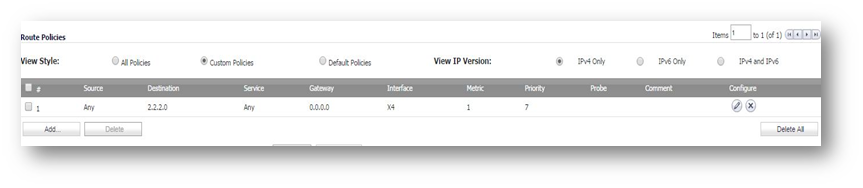 |
Now, the computers of network 2.2.2.0 should have gateway as 2.2.2.1
From any computer of 192.168.0.x, try to ping the computer in 2.2.2.x.

- Navigate to the Investigate tab
- Click Packet Monitor
- Click Configure, go to Monitor Filter tab and configure as follows:
- Ether type: IP
- IP type: ICMP
- Source IP: 192.168.0.246
- Rest all fields should be blank
- Under Display Filter, all fields should be blank
- Under Advanced Monitor filter, enable all checkboxes. Click Ok.
- Click Clear and Start Capture.
From the computer, 192.168.0.246, try to ping 2.2.2.10.
In Packet Monitor, refresh the page and we can see the packets getting dropped by firewall.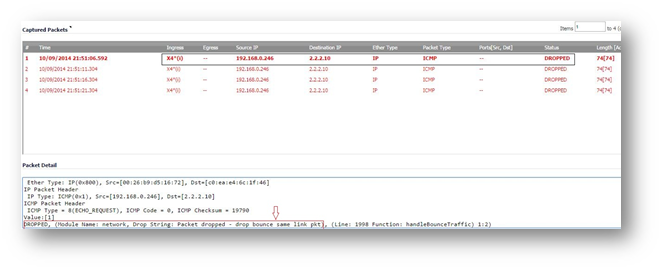
 NOTE: This behavior is only on DMZ Interfaces. In LAN Interface, with correct ARP and route, traffic will flow without any drops.
NOTE: This behavior is only on DMZ Interfaces. In LAN Interface, with correct ARP and route, traffic will flow without any drops.
To resolve this:
- Login to SonicWall.
- On address bar, instead of main.html, use diag.html and hit enter. (For example, https://x.x.x.x/diag.html)
- Click Internal Settings.
- Under "Routing and Network Settings" heading, enable the checkbox "Enable ICMP Redirect on DMZ zone"
- Click Accept on top and Click Close.
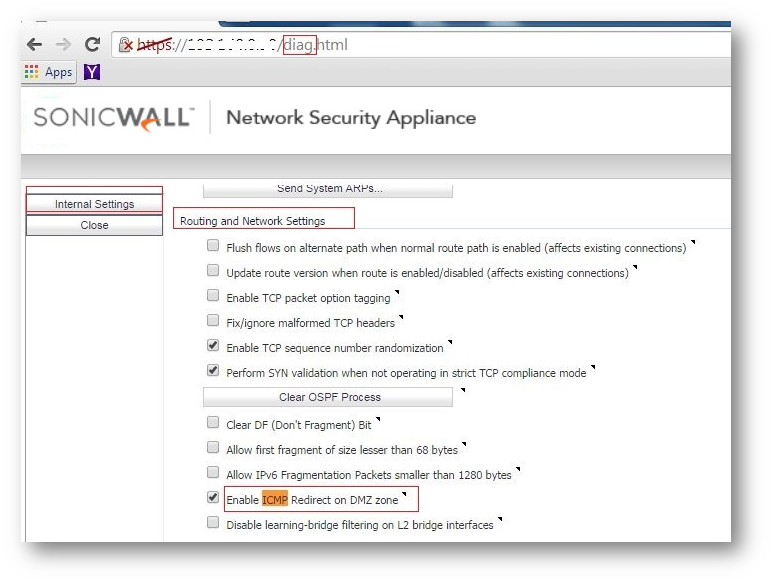
- Now try to ping 2.2.2.x, we can see successful pings.

- Navigate to Network | Interfaces; configure an interface as DMZ with Static IP. In this case, we have configured X4 as DMZ with IP address 192.168.0.10, Subnet: 255.255.255.0

- We have one more network which is connected to the same switch without any VLANs. In this case, we have secondary network as 2.2.2.0/24
- In order for the 2.2.2.0 to go online through SonicWall, SonicWall should know how to reach it. Hence , we create a Static ARP for the network and Static Route as follows:
- Navigate to Network | ARP
- click Add under Static ARP and enter any one IP in the network which is going to act as gateway for that subnet.
| IP Address: | 2.2.2.1 |
| Interface: | X4 |
| Publish Entry: | Checked |

- Navigate to Network | Routing and click Add.
| Source: Any Destination: 2.2.2.0 / 24 (Create address object for 2.2.2.0 of type DMZ) Service: Any Gateway: 0.0.0.0 Interface: X4 Metric: 1 Disable Route when interface is disconnected: Checked Click Ok. |  |
Now, the computers of network 2.2.2.0 should have gateway as 2.2.2.1
From any computer of 192.168.0.x, try to ping the computer in 2.2.2.x.

- Navigate to System | Packet Monitor
- click Configure, go to Monitor Filter tab and configure as follows:
- Ether type: IP
- IP type: ICMP
- Source IP: 192.168.0.246
- Rest all fields should be blank
- Under Display Filter, all fields should be blank
- Under Advanced Monitor filter, enable all checkboxes. Click Ok.
- Click Clear and Start Capture.
From the computer, 192.168.0.246, try to ping 2.2.2.10.
In Packet Monitor, refresh the page and we can see the packets getting dropped by firewall.
 NOTE: This behavior is only on DMZ Interfaces. In LAN Interface, with correct ARP and route, traffic will flow without any drops.
NOTE: This behavior is only on DMZ Interfaces. In LAN Interface, with correct ARP and route, traffic will flow without any drops.
To resolve this:
- Login to SonicWall.
- On address bar, instead of main.html, use diag.html and hit enter. (For example, https://x.x.x.x/diag.html)
- Click Internal Settings.
- Under "Routing and Network Settings" heading, enable the checkbox "Enable ICMP Redirect on DMZ zone"
- Click Accept on top and Click Close.

- Now try to ping 2.2.2.x, we can see successful pings.

Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > SonicWall NSA Series > Networking
- Firewalls > TZ Series > Networking
- Firewalls > SonicWall SuperMassive 9000 Series > Networking






 YES
YES NO
NO