-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Ensuring DPI-SSL Functionality and Resolving Slowness



Description
Why Disable UDP on Ports 443 and 80?
Disabling UDP traffic on ports 443 and 80 ensures that all encrypted web traffic defaults to TCP. TCP traffic can be decrypted, inspected, and properly filtered by DPI-SSL, while UDP-based protocols like QUIC bypass traditional DPI-SSL inspection. This step ensures:
-
Complete compliance with security policies.
-
No unscanned traffic bypasses firewall inspection.
Prerequisites
-
DPI-SSL must be enabled on the SonicWall firewall.
-
The SonicWall DPI-SSL certificate must be installed on all client devices to avoid SSL errors.
Resolution
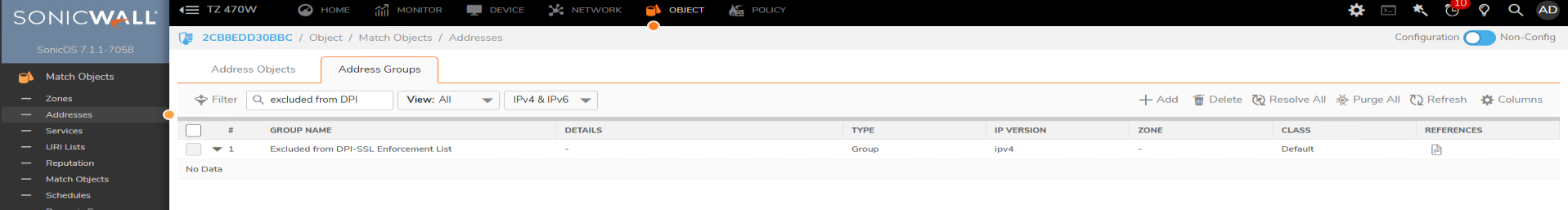
1. Check DPI-SSL Exclusion List
Ensure that no Fully Qualified Domain Name (FQDN) objects or common objects are unintentionally added to the DPI-SSL exclusion list. These exclusions can allow traffic to bypass DPI-SSL inspection.
Steps:
-
Navigate to Manage > DPI-SSL > Client SSL.
-
Under DPI-SSL Exclusions, review the list of excluded objects.
-
Remove any FQDN objects or add those FQDN in common names.
2. Review the Connection Failure List
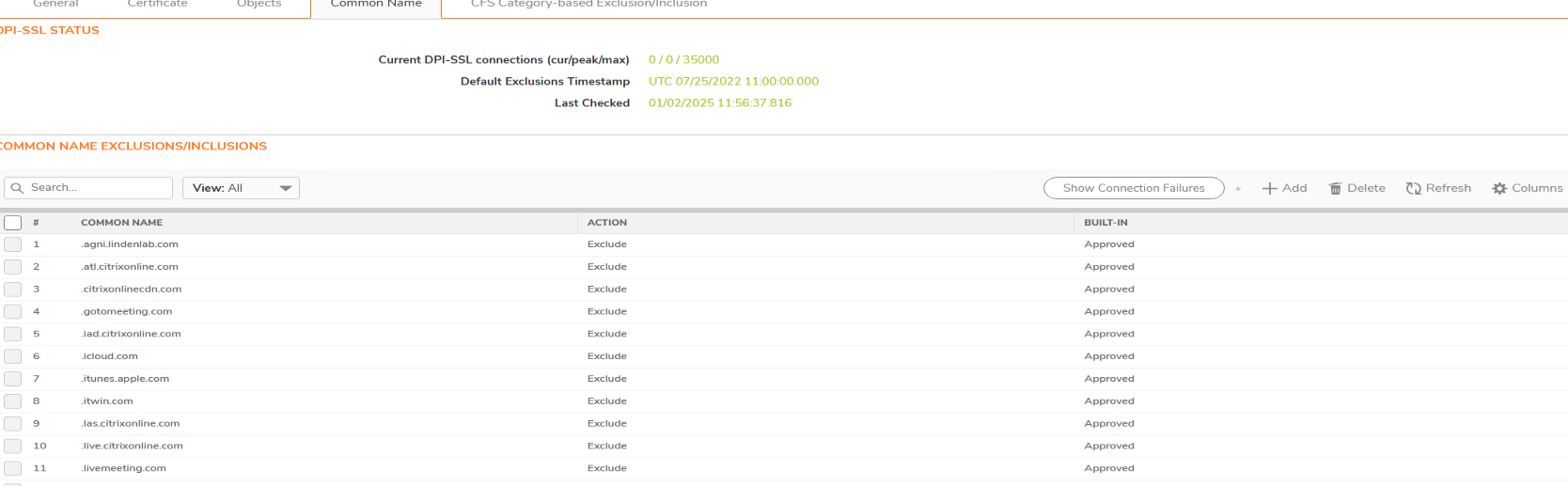
Analyze the connection failure list to determine if the issue is widespread or limited to certain objects.
Steps:
-
Navigate to Policy > DPI SSL > Common name >>show Connection Failures.
-
Check for any domains or IPs repeatedly failing DPI-SSL inspection.
-
Address the root cause of failures, such as invalid certificates or unsupported encryption methods for specific objects.
3. Create Deny Rules for UDP Ports 443 and 80
Blocking UDP traffic on these ports ensures that all encrypted traffic uses TCP, allowing DPI-SSL to properly decrypt and inspect the traffic.
Steps:
-
Navigate to Rules and Policies > Access Rules.
-
Select LAN to WAN as the zone pair.
-
Create a new rule with the following parameters:
-
Action: Deny
-
Service: UDP 443 and 80
-
Source: Any
-
Destination: Any
-
-
Save and apply the rule.
Reason: This ensures all encrypted web traffic defaults to TCP, which can be decrypted, inspected, and properly filtered by DPI-SSL.
4. Monitor and Flush Excessive DPI-SSL Connections
Check if the DPI-SSL connection count is exceeding, which can lead to slowness for users. Flushing these connections and rebooting the firewall can help resolve performance issues.
Steps:
-
Navigate to Investigate > Connection Monitor.
-
Filter connections related to DPI-SSL.
-
Manually flush connections that appear stuck or excessive.
-
Reboot the firewall to clear the buffer completely and reset DPI-SSL processes.
Note: Flushing connections and rebooting should only be performed during a maintenance window to minimize user impact.
Additional Notes
-
Ensure all client devices trust the l DPI-SSL certificate to avoid SSL errors during inspection.
-
Regularly update firmware to benefit from DPI-SSL improvements and bug fixes.
-
Monitor user feedback for slowness or accessibility issues and adjust policies as needed.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM






 YES
YES NO
NO