-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Enabling TCP, UDP and ICMP Flood Protection.



Description
This article details how to enable the flood protection for TCP, UDP and ICMP traffic.
Flood attacks are also known as Denial of Service (DoS) attacks. In a flood attack, attackers send a very high volume of traffic to a system so that it cannot examine and allow permitted network traffic. For example, an ICMP flood attack occurs when a system receives too many ICMP ping commands and must use all its resources to send reply commands.
Before we can proceed with the enabling of this protection we will need to first determine if we are dealing with a flood attack or not. Network slowdowns, unresponsive services, and high CPU or bandwidth utilization are common signs of a ping flood attack.
Also we would be able to see in the firewall logs messages, because on the TCP flood, the option on SYN Flood Protection Mode is set to "Watch and report possible SYN floods":
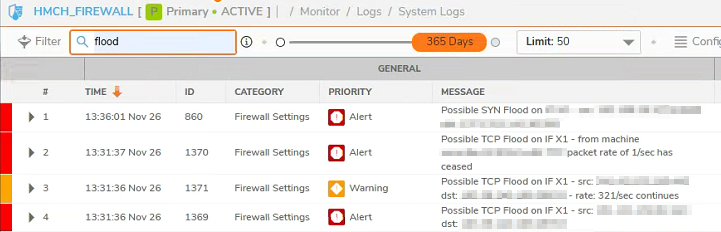
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
TCP Flood Protection:
1. Click Network in the top navigation menu. Navigate to Firewall| Flood Protection |TCP|Layer 3 SYN Flood Protection-SYN Proxy and for SYN Flood Protection Mode, select Proxy WAN client connections when attack is suspected:
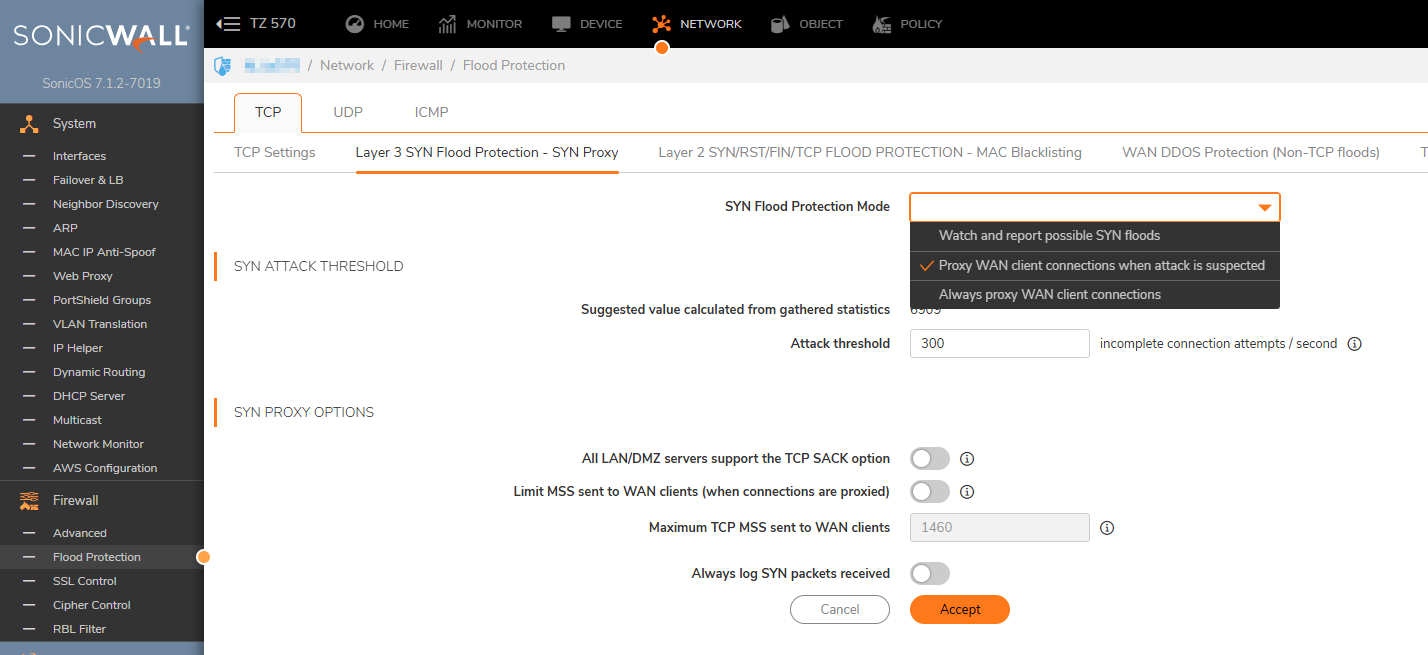
-
- Watch and Report Possible SYN Floods – This option enables the device to monitor SYN traffic on all interfaces on the device and to log suspected SYN flood activity that exceeds a packet count threshold. The feature does not turn on the SYN Proxy on the device so the device forwards the TCP three-way handshake without modification. This is the least invasive level of SYN Flood protection. Select this option if your network is not in a high risk environment.
- Proxy WAN Client Connections When Attack is Suspected – This option enables the device to enable the SYN Proxy feature on WAN interfaces when the number of incomplete connection attempts per second surpasses a specified threshold. This method ensures the device continues to process valid traffic during the attack and that performance does not degrade. Proxy mode remains enabled until all WAN SYN flood attacks stop occurring or until the device blacklists all of them using the SYN Blacklisting feature. This is the intermediate level of SYN Flood protection. Select this option if your network experiences SYN Flood attacks from internal or external sources.
- Always Proxy WAN Client Connections – This option sets the device to always use SYN Proxy. This method blocks all spoofed SYN packets from passing through the device. Note that this is an extreme security measure and directs the device to respond to port scans on all TCP ports because the SYN Proxy feature forces the device to respond to all TCP SYN connection attempts. This can degrade performance and can generate a false positive. Select this option only if your network is in a high risk environment.
2. Navigate to Firewall| Flood Protection |TCP|Layer 2 SYN/RST/SIN/TCP FLOOD PROTECTION-MAC Blacklisting and enable the option Enable SYN/RST/SIN/TCP flood blacklisting on all interfaces:
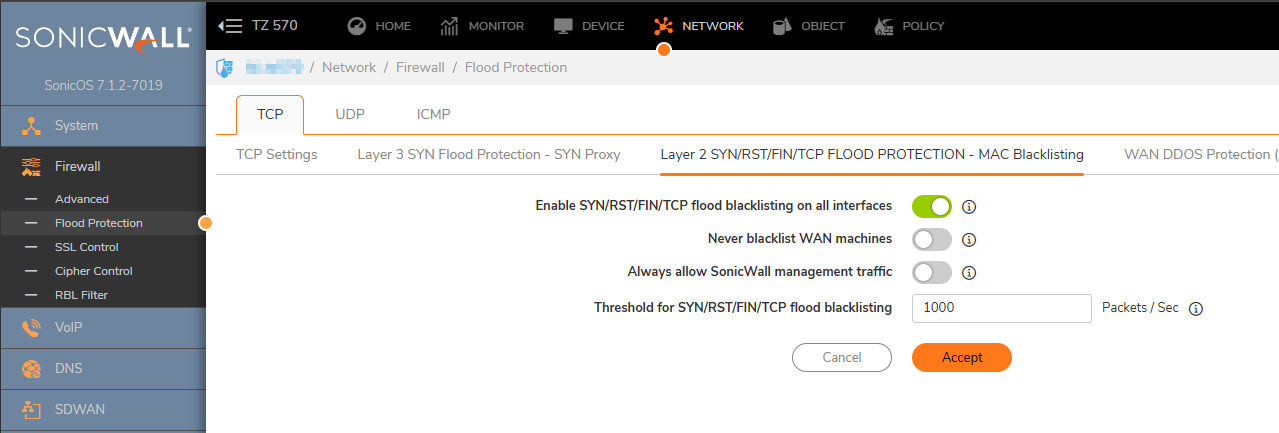
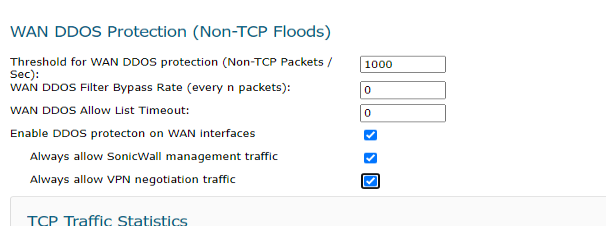
3. Navigate to Firewall| Flood Protection |TCP| WAN DDOS Protection (Non-TCP floods) and enable all three options:
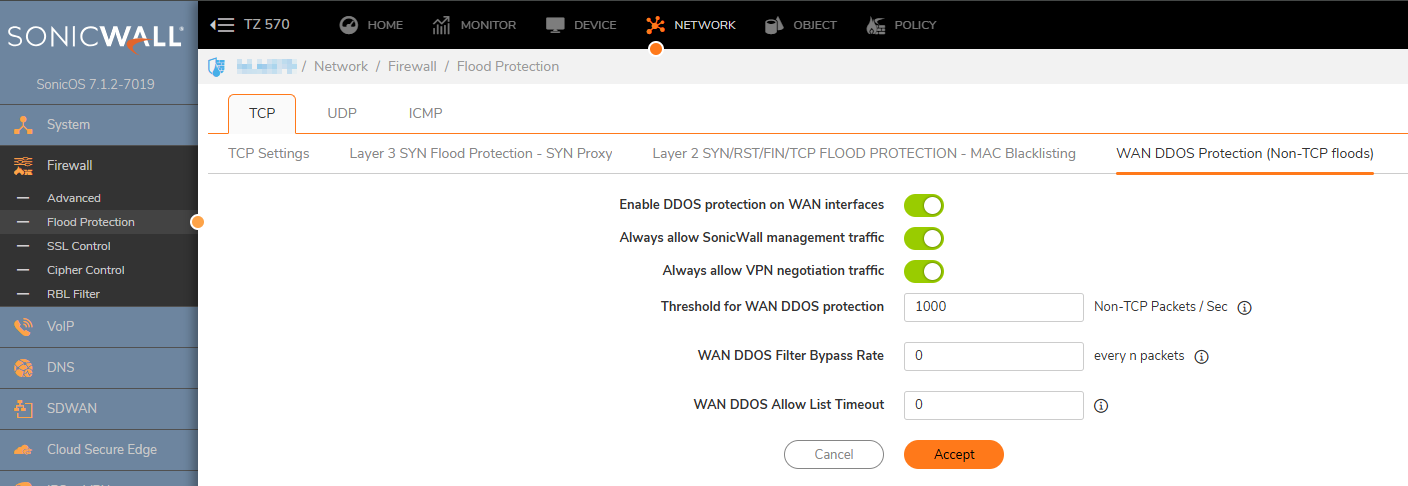
UDP Flood Protection:
 CAUTION: Enabling this option may cause connection issues that are UDP based like video conferences and real time streaming. Example: Microsoft Teams meetings/calls, VOIP. In case this option needs to be enabled we can increase the UDP Flood Attack Threshold value.
CAUTION: Enabling this option may cause connection issues that are UDP based like video conferences and real time streaming. Example: Microsoft Teams meetings/calls, VOIP. In case this option needs to be enabled we can increase the UDP Flood Attack Threshold value.
1. Click Network in the top navigation menu. Navigate to Firewall| Flood Protection |UDP and do the following:
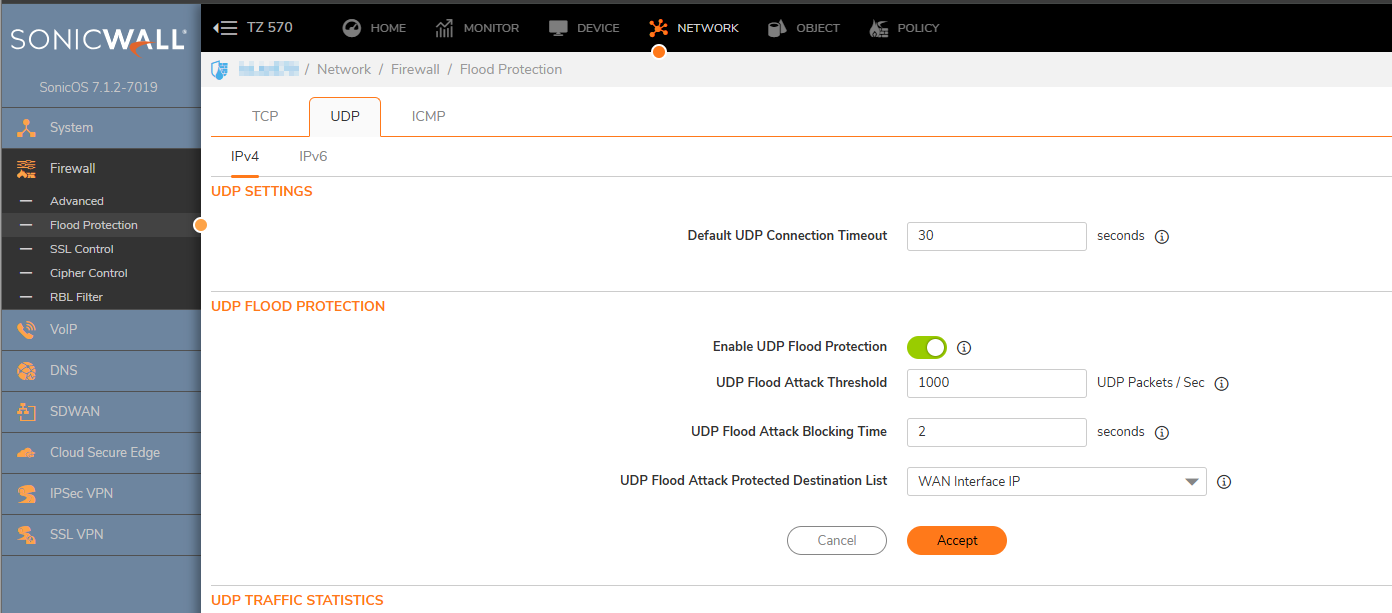
- UDP Flood Attack Threshold (UDP Packets / Sec) - the rate of UDP packets per second sent to a host, range or subnet that triggers UDP Flood Protection. The Threshold must be set carefully as too small a threshold may affect unintended traffic and too large a threshold may not effectively protect from an attack. The default value is 1000.
- UDP Flood Attack Blocking Time (Sec) - after the appliance detects the rate of UDP packets exceeding the attack threshold for this duration of time, UDP Flood protection is activated, and the appliance will begin dropping subsequent UDP packets.
- UDP Flood Attack Protected Destination List The destination address object or address group that will be protected from UDP Flood Attack. We select WAN Interface IP to limit the impact on the UDP LAN traffic. We will put the value ANY if there is flood present in the internal network as well as in the WAN network.
ICMP Flood Protection:
1. Click Network in the top navigation menu. Navigate to Firewall| Flood Protection |ICMP and do the following:
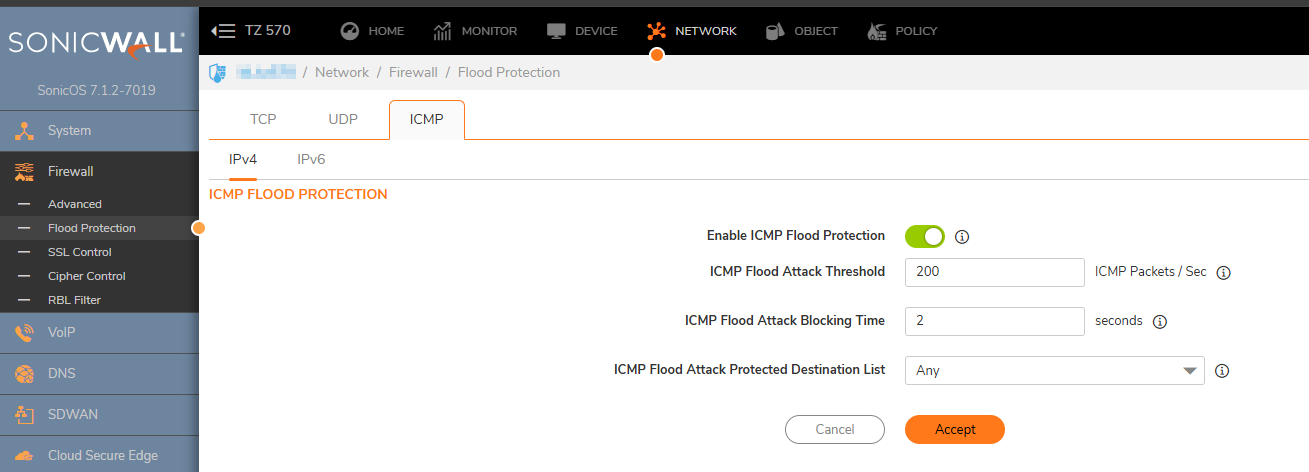
- ICMP Flood Attack Threshold (ICMP Packets / Sec) - the rate of ICMP packets per second sent to a host, range or subnet that triggers ICMP Flood protection. The Threshold must be set carefully as too small a threshold may affect unindented traffic and too large a threshold may not effectively protect from an attack. The default value is 200.
- ICMP Flood Attack Blocking Time (Sec) - after the appliance detects the rate of ICMP packets exceeding the attack threshold for this duration of time, ICMP Flood protection is activated, and the appliance will begin dropping subsequent ICMP packets.
- ICMP Flood Attack Protected Destination List - the destination address object or address group that will be protected from ICMP Flood attack.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
TCP Flood Protection:
1. Click Manage in the top navigation menu. Navigate to Firewall Settings| Flood Protection |TCP. Under Layer 3 SYN Flood Protection-SYN Proxy see SYN Flood Protection Mode, select Proxy WAN client connections when attack is suspected:
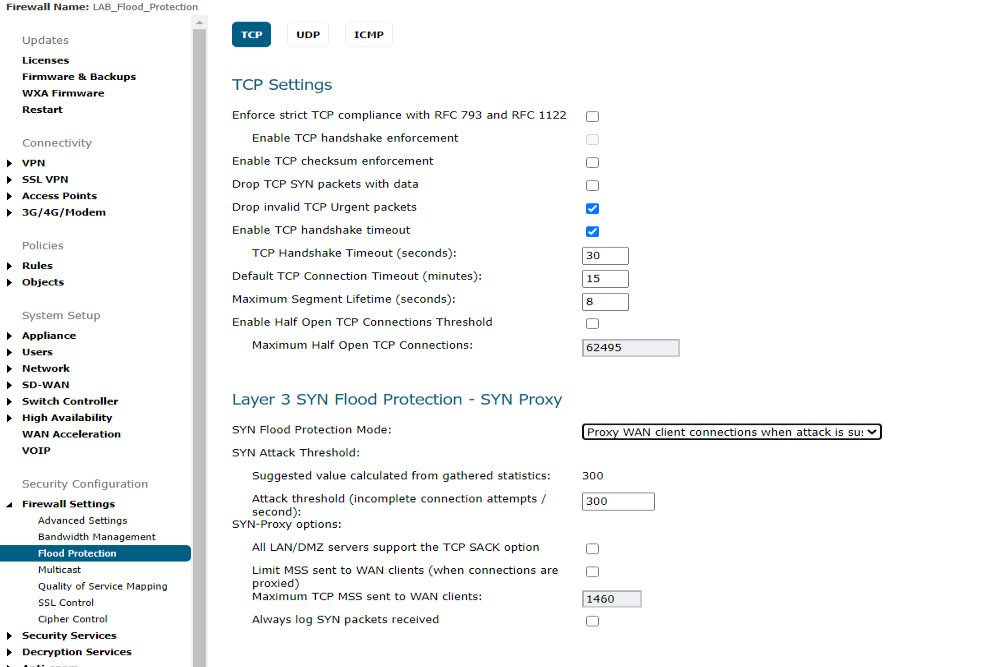
-
- Watch and Report Possible SYN Floods – This option enables the device to monitor SYN traffic on all interfaces on the device and to log suspected SYN flood activity that exceeds a packet count threshold. The feature does not turn on the SYN Proxy on the device so the device forwards the TCP three-way handshake without modification. This is the least invasive level of SYN Flood protection. Select this option if your network is not in a high risk environment.
- Proxy WAN Client Connections When Attack is Suspected – This option enables the device to enable the SYN Proxy feature on WAN interfaces when the number of incomplete connection attempts per second surpasses a specified threshold. This method ensures the device continues to process valid traffic during the attack and that performance does not degrade. Proxy mode remains enabled until all WAN SYN flood attacks stop occurring or until the device blacklists all of them using the SYN Blacklisting feature. This is the intermediate level of SYN Flood protection. Select this option if your network experiences SYN Flood attacks from internal or external sources.
- Always Proxy WAN Client Connections – This option sets the device to always use SYN Proxy. This method blocks all spoofed SYN packets from passing through the device. Note that this is an extreme security measure and directs the device to respond to port scans on all TCP ports because the SYN Proxy feature forces the device to respond to all TCP SYN connection attempts. This can degrade performance and can generate a false positive. Select this option only if your network is in a high risk environment.
2. Navigate to Firewall Settings| Flood Protection |TCP. Under Layer 2 SYN/RST/SIN/TCP FLOOD PROTECTION-MAC Blacklisting enable the option Enable SYN/RST/SIN/TCP flood blacklisting on all interfaces:
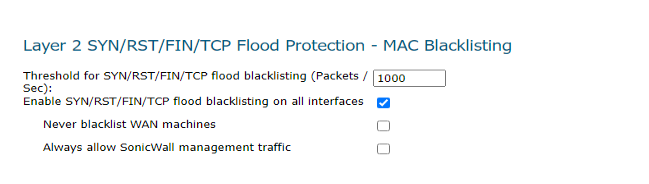
3. Navigate to Firewall Settings| Flood Protection |TCP. Under WAN DDOS Protection (Non-TCP floods) enable all three options:
UDP Flood Protection:
 CAUTION: Enabling this option may cause connection issues that are UDP based like video conferences and real time streaming. Example: Microsoft Teams meetings/calls, VOIP. In case this option needs to be enabled we can increase the UDP Flood Attack Threshold value.
CAUTION: Enabling this option may cause connection issues that are UDP based like video conferences and real time streaming. Example: Microsoft Teams meetings/calls, VOIP. In case this option needs to be enabled we can increase the UDP Flood Attack Threshold value.
1. Click Manage in the top navigation menu. Navigate to Firewall Settings| Flood Protection|UDP and do the following:
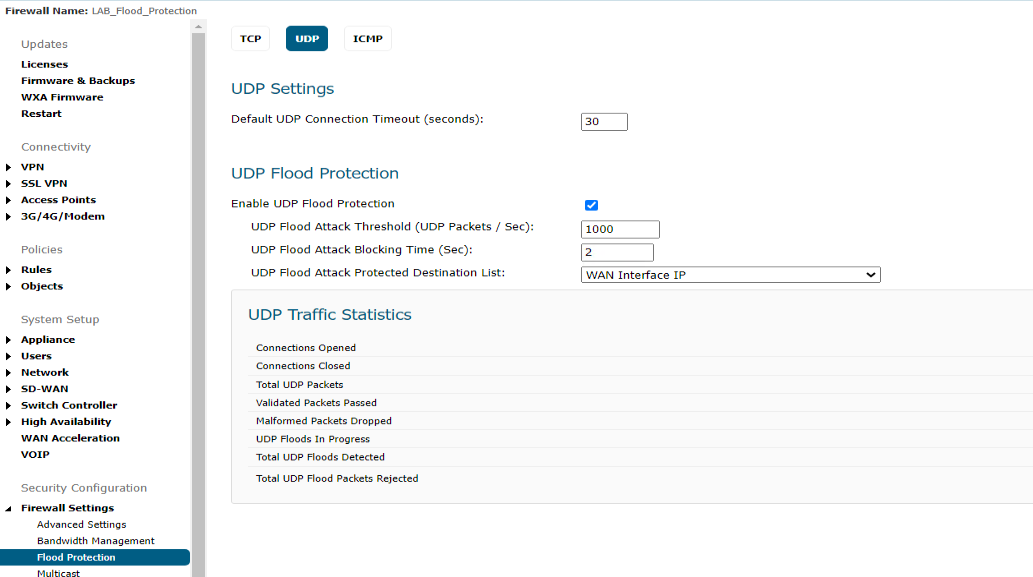
- UDP Flood Attack Threshold (UDP Packets / Sec) - the rate of UDP packets per second sent to a host, range or subnet that triggers UDP Flood Protection. The Threshold must be set carefully as too small a threshold may affect unintended traffic and too large a threshold may not effectively protect from an attack. The default value is 1000.
- UDP Flood Attack Blocking Time (Sec) - after the appliance detects the rate of UDP packets exceeding the attack threshold for this duration of time, UDP Flood protection is activated, and the appliance will begin dropping subsequent UDP packets.
- UDP Flood Attack Protected Destination List The destination address object or address group that will be protected from UDP Flood Attack. We select WAN Interface IP to limit the impact on the UDP LAN traffic. We will put the value ANY if there is flood present in the internal network as well as in the WAN network.
ICMP Flood Protection:
1. Click Manage in the top navigation menu. Navigate to Firewall Settings| Flood Protection|ICMP and do the following:
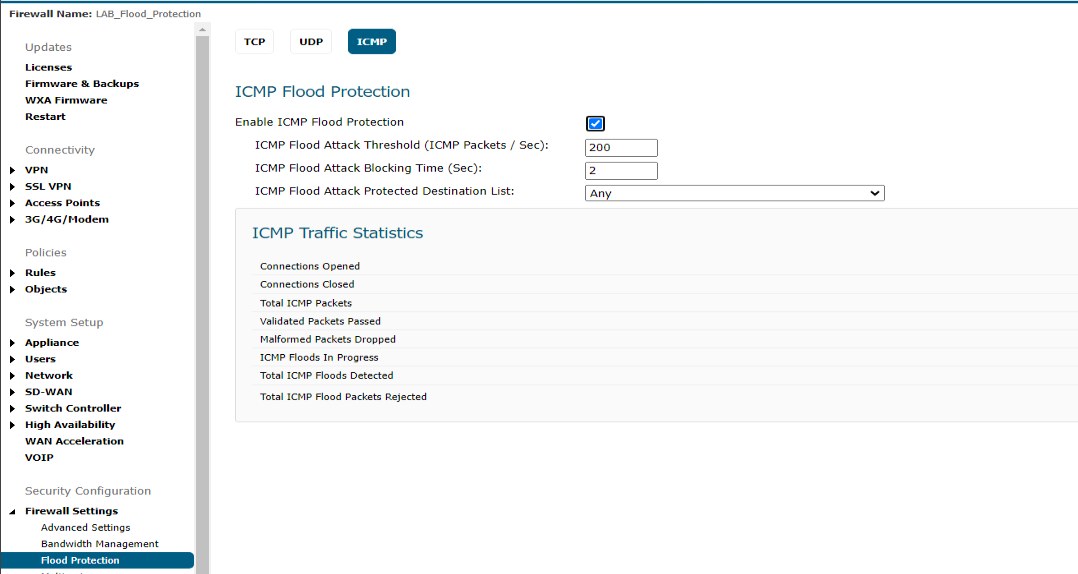
- ICMP Flood Attack Threshold (ICMP Packets / Sec) - the rate of ICMP packets per second sent to a host, range or subnet that triggers ICMP Flood protection. The Threshold must be set carefully as too small a threshold may affect unindented traffic and too large a threshold may not effectively protect from an attack. The default value is 200.
- ICMP Flood Attack Blocking Time (Sec) - after the appliance detects the rate of ICMP packets exceeding the attack threshold for this duration of time, ICMP Flood protection is activated, and the appliance will begin dropping subsequent ICMP packets.
- ICMP Flood Attack Protected Destination List - the destination address object or address group that will be protected from ICMP Flood attack.






 YES
YES NO
NO