-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
MSS FW Best Practices: VPN (Site to Site & Client)



Description
 CAUTION: These documents are intended to provide partners with firewall configuration recommendations ONLY. They contain examples and caution should be exercised when making changes to your firewall as unplanned changed could result in downtime based on the complexity of the environment and/or configuration.
CAUTION: These documents are intended to provide partners with firewall configuration recommendations ONLY. They contain examples and caution should be exercised when making changes to your firewall as unplanned changed could result in downtime based on the complexity of the environment and/or configuration.
MSS Recomended SonicWall Firewall Best Practices Index
Site to Site VPN
Notes/Recommendations
- Always remove unused tunnels. The firewall uses Core 0 to try and establish S2S VPN tunnels.
- It is recommended to use IKEv2, DH Group 5, and AES-256 Encryption if both sides support it.
Setup/Configuration
- For how to setup Site to Site VPNs, see the following SonicWall KB: Setting Up A Site to Site VPN Policy | SonicWall.
- See the following SonicWall KB for more information about the different kinds of VPN Scenarios and Configurations: Types of site to site VPN scenarios and configurations | SonicWall.
SSL VPN
Notes/Recommendations
- It is recommended to have a public (purchased) cert meeting the latest encryption standards. The self-signed cert provided by the firewall is adequate but will not pass PCI audits.
Setup/Configuration
- See the following SonicWall KB for information on configuring SSLVPN on a firewall: Configuring the SSL-VPN Feature on SonicWall Firewalls | SonicWall.
- Ensure that the following best practices are implemented as well:
- Server Settings:
- Change SSLVPN Port to 443 is possible.
- This is done to enhance the end user’s experience.
- You must first change the default HTTPS Management port (443) mentioned previously.
- SSLVPN terminates on the SonicWall’s Interface IP(s) and cannot be changed to another IP in Interface’s subnet. Note this so you can address other potential inbound NAT Policy conflicts.
- Change SSLVPN Port to 443 is possible.
- Client Settings (Edit the Default Device Profile):
- Settings
- Network Address is for the IP(s) that will be issued to the SSLVPN clients (make this a range that contains enough IPs equal to the number of SSLVPN licenses).
- Client Routes
- Client routes are the networks the SSLVPN clients will be able to access (This does not mean they will be allowed to).
- Client Settings
- Enter the internal DNS server(s).
- Enter the internal domain (with suffix).
- This is required for DNS/NetBIOS to work through NetExtender.
- Enable Client Auto update.
- Enable NetBIOS over SSLVPN
- Create Client Connection Profile
- Disable Username & Password Caching
- Settings
- User/User Group Settings:
- Edit default SSLVPN Services user group.
- Add members as needed.
- VPN access are the networks the user/group can access. Anything here should be added as a route under client settings as well.
- Add Wan Remote Access Networks to VPN access.
- This is required for DNS/NetBIOS to work through NetExtender.
- Edit default SSLVPN Services user group.
- Server Settings:
Restricting/Blocking IP Addresses From Accessing the SSLVPN
Blocking WAN SSLVPN Access
Use the following steps to Block Access to the SSLVPN for specific IP addresses:
- Create Address Objects for the public IPs that will NOT be allowed to access the SSLVPN.
- If there are multiple public IPs, you will need to add them to an Address Object group.
- Go to Policies > Rules and Policies > Access Rules
- Change the View to WAN to WAN
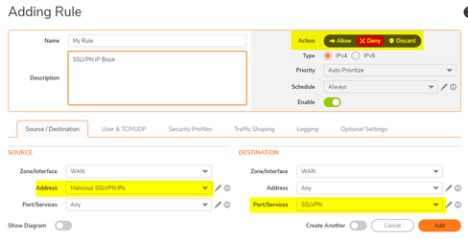
- Click +Add and enter the following:
- Action: Deny
- Source Address: The Address Object Group of the IP address that you would like to block from accessing the SSLVPN.
- Destination Port/Services: SSLVPN
- Click Save
- You should now see this Deny rule about the default SSLVPN allow rule.
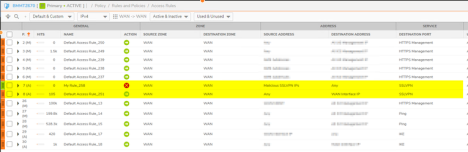
- To block additional IP addresses from accessing the SSLVPN, simply create an Address Object for them and add them to the Address Object Group with the rest.
Global VPN Client (WAN Group VPN)
- See the following SonicWall KB for information on configuring Global VPN on a firewall - How can I configure WAN GroupVPN for connecting with Global VPN client? | SonicWall
Related Articles
- Cloud Threat Analytics: SaaS Alerts Onboarding
- NDR: Integration Guide (Start Here)
- MSS CAS Migrations: Frequently Asked Questions (FAQs)
Categories
- Managed Security Services > Firewall Monitoring and Management > Firewall Configuration and Best Practices






 YES
YES NO
NO