-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
MSS FW Best Practices: DPI-SSL (Client)



Description
 CAUTION: These documents are intended to provide partners with firewall configuration recommendations ONLY. They contain examples and caution should be exercised when making changes to your firewall as unplanned changed could result in downtime based on the complexity of the environment and/or configuration.
CAUTION: These documents are intended to provide partners with firewall configuration recommendations ONLY. They contain examples and caution should be exercised when making changes to your firewall as unplanned changed could result in downtime based on the complexity of the environment and/or configuration.
MSS Recomended SonicWall Firewall Best Practices Index
Table of Contents
Notes/Recommendations
- Exclude devices that don’t have the cert/ get to the internet on the network DPI-SSL is enabled. (Printers, cameras, VoIP Equipment, etc.)
- http://Exclude.update.microsoft.com from DPI-SSL. (Custom domain) No choice but to trust traffic if you want updates.
- Exclude http://youtube.com. Helps lower DPI-SSL connections.
- Proper discovery should be done to ensure the implementation goes as smooth as possible.
- DPI-SSL is a disruptive service as it acks as sort of a “main in the middle” scenario.
- No matter how much prep you do, IT WILL BREAK THINGS. Prepare the customer accordingly.
Resources
- SonicWall DPI-SSL Troubleshooting
- How Can I Configure Client DPI-SSL
- Where Can I Learn More About DPI-SSL (Comprehensive list of all SonicWall DPI-SSL KBs)
1. Discovery and Considerations
Device Exclusions
- The biggest thing the customer will need to provide is a list of IPs that should be excluded from DPI-SSL. These devices access the internet on the subnet where DPI-SSL will be enabled, but do not support certificates. Example devices can be Printers, Camera’s network storage, IP Phones, IoT devices, etc.
Where will DPI-SSL be implemented?
Subnet Level
- The most common place to enable DPI-SSL is at the subnet level.
- This is the most secure method as it ensures that all new devices won’t be able to get to the internet without the DPI-SSL certificate installed.
- This method requires exclusions to be made.
Address Object Group Level
- If you only want to apply DPI-SSL to a specific number of IPs or MACs, you can choose to only apply DPI-SSL to a specified address object group.
- This is less secure as new devices may bypass DPI-SSL if not added to the specified address object group.
- This method does NOT require exclusions.
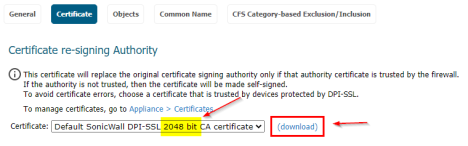
2. Download the DPI-SSL Certificate
- By default, DPI-SSL will use the firewall’s self-generated certificate.
- If using the default SonicWall DPI-SSL certificate, we recommend selecting and using the 2048-bit certificate.
- If the customer wants to replace the default DPI-SSL CA certificate with a 3rd party certificate, follow this KB: How Can I Create A DPI-SSL Certificate For The Purpose Of DPI-SSL Certificate Resigning?
- Once the correct certificate is selected and applied in the drop-down menu, proceed.
- Click “Download” next to the certificate drop down menu.
- This will download the .cer that needs to be deployed.
3. Deploy the Certificate
- To be done by the customer, the SonicWall DPI-SSL (CA) certificate (or the imported certificate used for re-signing) should be added to the trusted root store of the client machines on the network.
- In a Windows PKI environment, the certificate can be distributed to clients using Group Policy. Feel free to provide this SonicWall KB on how to do this: “Distributing The Default SonicWall DPI-SSL CA Certificate To Client Computers Using Group Policy”
4. Configure Exclusions
- With the list of IPs from the customer that need to be excluded you can:
- Create address objects for the IPs and/or MAC addresses that need to be excluded.
- Create an address object group called “DPI-SSL Exclusion Group” that contains those AOs.
5. DPI-SSL Pre-Configuration
- We want to do as much as possible BEFORE enabling DPI-SSL to avoid as many interruptions as possible.
- On the Network/Zones page, ensure that “DPI-SSL Client” is enabled for each zone that contains devices, networks, or devices that will have DPI-SSL applied to:
- Back on the DPI-SSL/TLS Client page, under “General Settings”, ensure the following options are checked:
- Intrusion Prevention
- Gateway Anti-Virus
- Gateway Anti-Spyware
- Application Firewall
- Content Filtering

- On the Objects Page for the “Address Object/Group” Exclude box, select the “DPI-SSL Exclusion Group” that you created earlier.
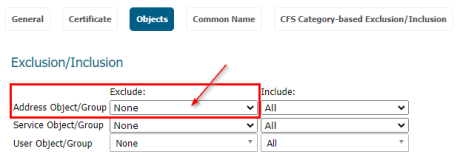
- For the “Address Object/Group” Include box, select either the interface subnet or address object group depending on what you are applying DPI-SSL to.

- On the “CFS Category-Based Exclusion/Inclusion” tab, select the following categories:
- Online Banking
- Online Brokerage and Trading
- This is done to sensitive financial data is not exposed.
6. Enable DPI-SSL
- On the DPI-SSL/TLS Client page, under “General Settings”, check “Enable SSL Client Inspection” and hit accept.

- You should start to see the counters go up
![]()
7. Troubleshooting
- At this point the customer needs to test and ensure that all programs, applications, and website that they use still work.
- To troubleshoot and/or exclude a website that is not working:
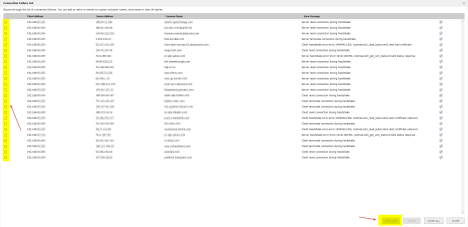
- Under the “Common Name” tab click on “Show Connection Failures”

- Here you will see websites that are being affected by DPI-SSL.
- The below messages are nothing to worry about as they are not “stopping” the traffic. If websites with the below Error Messages are not working, exclude them.
- Server reset connection during handshake.
- Server terminate connection during handshake.
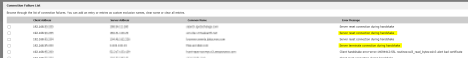
- Websites with an error message that contains “Server handshake error-error” are most likely not working. They need to be excluded.

- To Exclude websites from the Connection Failure List
- Select the website and click “exclude.”
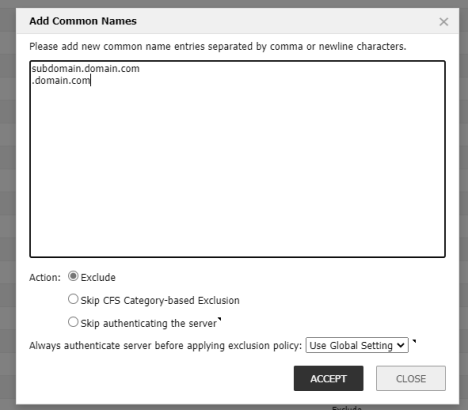
- To exclude websites manually:
- Under the “Common Name” tab click on “Add”
- Enter the website(s) and click “Exclude.”
- Wildcard/Sub domains can be added as “. http://domain.com”
Related Articles
- Cloud Threat Analytics: SaaS Alerts Onboarding
- NDR: Integration Guide (Start Here)
- MSS CAS Migrations: Frequently Asked Questions (FAQs)
Categories
- Managed Security Services > Firewall Monitoring and Management > Firewall Configuration and Best Practices






 YES
YES NO
NO