-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to configure Rogue Access Point Detection in Wireless?



Description
This article explains about Rogue Access Point Detection in Wireless Intrusion Detection Settings (IDS).
Rogue Access Points
- Rogue Access Points have emerged as one of the most serious and insidious threats to wireless security.
- In general terms, an access point is considered rogue when it has not been authorized for use on a network.
- The convenience, affordability, and availability of non-secure access points and the ease with which they can be added to a network creates an easy environment for introducing rogue access points.
- Specifically, the real threat emerges in a number of different ways including unintentional and unwitting connections to the rogue device, transmission of sensitive data over non-secure channels, and unwanted access to LAN resources. So while this doesn't represent a deficiency in the security of a specific wireless device, it is a weakness to the overall security of wireless networks.
Resolution:
The security appliance can alleviate this weakness by recognizing rogue access points potentially attempting to gain access to your network.
It accomplishes this in two ways:
- Active scanning for access points on all 802.11a, 802.11g, 802.11n, and 802.11ac channels.
- Passive scanning while in Access Point mode) for beacon of access points on a single channel of operation.?
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
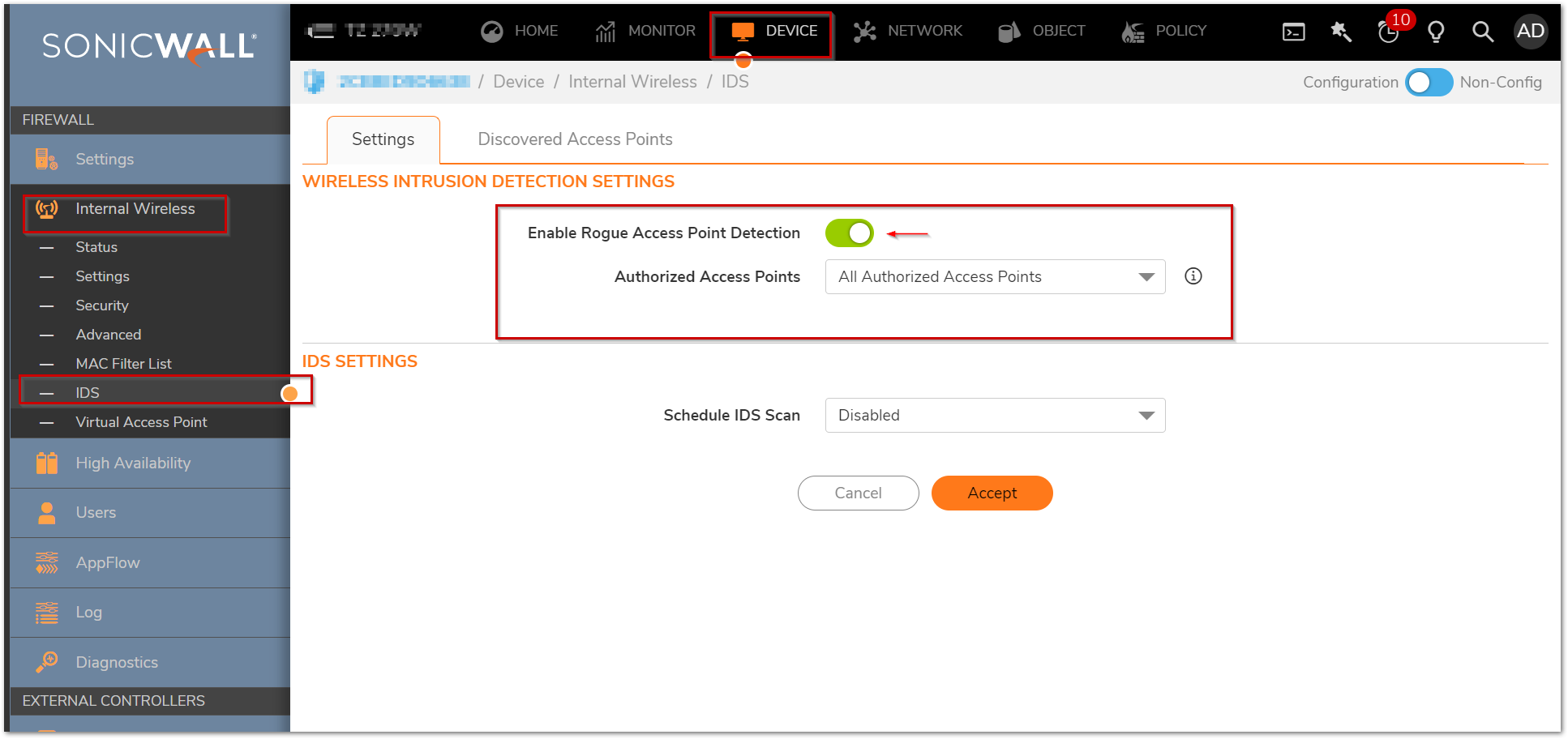
- Login to the SonicWall management GUI
- Navigate to Device|Internal Wireless|IDS
- Select "Enable Rogue Access Point Detection" checkbox to specify the rogue access point detection method. The Authorized Access Points menu allows you to specify All Authorized Access Points.
- Create new MAC Address Object Group or Select an Address Object Group.
- Click the Accept button in top of the page to save the changes
 NOTE:
NOTE: - The Authorized Access Points menu allows you to specify which access points the SonicWall security appliance will consider authorized when it performs a scan.
- You can select All Authorized Access Points to allow all SonicPoints or you can select Create new MAC Address Object Group to create an address object group containing a group of MAC addresses to limit the list to only those SonicPoints whose MAC addresses are contained in the address object group.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
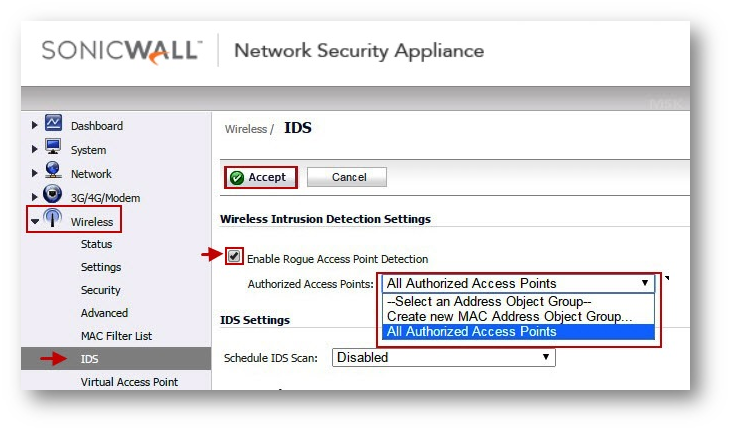
- Login to the SonicWall management GUI
- Navigate to Wireless | IDS, making the following change on the Right side under Wireless Intrusion Detection Settings.
- Select "Enable Rogue Access Point Detection" checkbox to specify the rogue access point detection method. The Authorized Access Points menu allows you to specify All Authorized Access Points.
- Create a new MAC Address Object Group or Select an Address Object Group.
- Click the Accept button at top of the page to save the changes.
 NOTE:
NOTE:
- The Authorized Access Points menu allows you to specify which access points the SonicWall security appliance will consider authorized when it performs a scan.
- You can select All Authorized Access Points to allow all SonicPoints or you can select Create new MAC Address Object Group to create an address object group containing a group of MAC addresses to limit the list to only those SonicPoints whose MAC addresses are contained in the address object group.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall NSA Series






 YES
YES NO
NO