-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Configuring SMTP Real-Time Black List (RBL) Filtering on the SonicWall



Description
SMTP Real-time Black List (RBL) is a mechanism for publishing the IP addresses of SMTP servers from which or through which spammers operate. There are a number of organizations that compile this information for example http://www.spamhaus.org.
How does RBL filter identify if a SMTP server is Blacklisted (possible SPAM)?
RBL list providers publish their lists via DNS. Blacklisted IP addresses appear in the database of the list provider's DNS domain using inverted IP notation of the SMTP server in question as a prefix to the domain name. A response code from 127.0.0.2 to 127.0.0.9 indicates some type of undesirability:
For example: An SMTP server with IP address 1.2.3.4 has been blacklisted by RBL list provider sbl-xbl.spamhaus.org, and then a DNS query to 4.3.2.1.sbl-xbl.spamhaus.org will provide a 127.0.0.4 response, indicating that the server is a known source of spam, and the connection will be dropped.
|
 CAUTION: Most spam today is known to be sent from hijacked or zombie machines running a thin SMTP server implementation, unbeknownst to the hosts operator. These zombie machines rarely attempt to retry failed delivery attempts, as would be the behavior of a legitimate SMTP server. As such, once the delivery attempt is thwarted by the SonicWall RBL filter, no subsequent delivery attempts for that same piece of spam will be made.
CAUTION: Most spam today is known to be sent from hijacked or zombie machines running a thin SMTP server implementation, unbeknownst to the hosts operator. These zombie machines rarely attempt to retry failed delivery attempts, as would be the behavior of a legitimate SMTP server. As such, once the delivery attempt is thwarted by the SonicWall RBL filter, no subsequent delivery attempts for that same piece of spam will be made.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Configuring Real Time Blacklist (RBL) Filter
- Login to the SonicWall Management Interface
- Go to Network | Firewall | RBL Filter
- Select the checkbox Enable Real-time Black List Blocking
- The RBL DNS Servers menu allows you to specify the DNS servers. You can choose Inherit Settings from WAN Zone or Specify DNS Servers Manually. If you select Specify DNS Servers Manually, enter the DNS server addresses in the DNS Server fields.
When Enable Real-time Black List Blocking in enabled inbound connections from hosts on the WAN, or outbound connections to hosts on the WAN are checked against each enabled RBL service with a DNS request to the DNS servers configured under RBL DNS Servers.
 NOTE: By default sbl-xbl.spamhaus.org and dnsbl.sorbs.net RBL Services are pre-configured; SonicWall will query these providers to determine the source of spam.
NOTE: By default sbl-xbl.spamhaus.org and dnsbl.sorbs.net RBL Services are pre-configured; SonicWall will query these providers to determine the source of spam.
 TIP: Statistics are maintained for each RBL Service in the RBL Service table, and can be viewed with a mouseover of the (statistics) icon to the right on the service entry.
TIP: Statistics are maintained for each RBL Service in the RBL Service table, and can be viewed with a mouseover of the (statistics) icon to the right on the service entry.
Add additional RBL Services
You can add additional RBL services to the Real-time Black List Services section by clicking the Add button.
In the Add RBL Domain window, you specify the RBL domain to be queried, enable it for use, and specify its expected response codes. Most RBL services list the responses they provide on their Web site, although selecting Block All Responses is generally acceptable.
User-Defined SMTP Server Lists
The User Defined SMTP Server Lists section allows for Address Objects to be used to construct a white-list (explicit allow) or black-list (explicit deny) of SMTP servers. Entries in this list will bypass the RBL querying procedure.
For example, to ensure that you always receive SMTP connections from a partner site's SMTP server:
- Create an Address Object for the server you added using the Add button
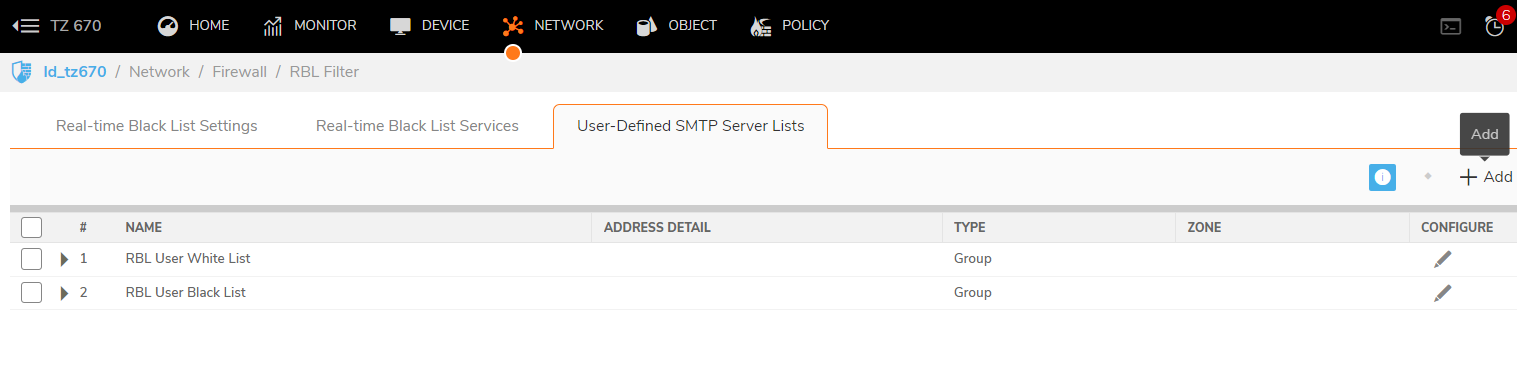
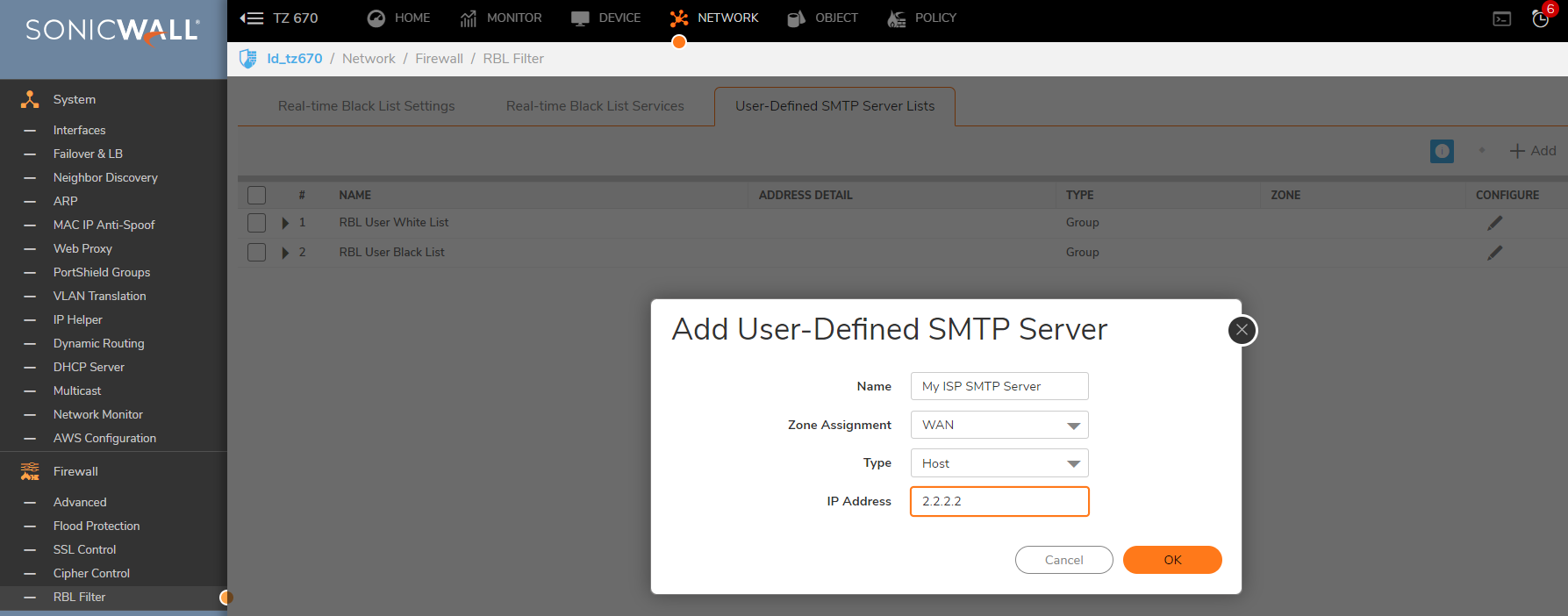
- Click the edit icon in the Configure column of the RBL User White List row, and add the Address Object. The table will be updated, and that server will always be allowed to make SMTP exchanges.
The Monitor | Dashboard page also provides a Real-time Black List Lookup feature that allows for SMTP IP addresses (or RBL services, or DNS servers) to be specifically tested.
For a list of known spam sources to use in testing, refer to http://www.spamhaus.org/sbl/latest.lasso
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Configuring Real Time Blacklist (RBL) Filter
- Login to the SonicWall Management Interface
- Go to Manage | security services | RBL Filter
- Select the checkbox Enable Real-time Black List Blocking
- The RBL DNS Servers menu allows you to specify the DNS servers. You can choose Inherit Settings from WAN Zone or Specify DNS Servers Manually. If you select Specify DNS Servers Manually, enter the DNS server addresses in the DNS Server fields.
When Enable Real-time Black List Blocking in enabled inbound connections from hosts on the WAN, or outbound connections to hosts on the WAN are checked against each enabled RBL service with a DNS request to the DNS servers configured under RBL DNS Servers.
 NOTE: By default sbl-xbl.spamhaus.org and dnsbl.sorbs.net RBL Services are pre-configured; SonicWall will query these providers to determine the source of spam.
NOTE: By default sbl-xbl.spamhaus.org and dnsbl.sorbs.net RBL Services are pre-configured; SonicWall will query these providers to determine the source of spam.
 TIP: Statistics are maintained for each RBL Service in the RBL Service table, and can be viewed with a mouseover of the (statistics) icon to the right on the service entry.
TIP: Statistics are maintained for each RBL Service in the RBL Service table, and can be viewed with a mouseover of the (statistics) icon to the right on the service entry.
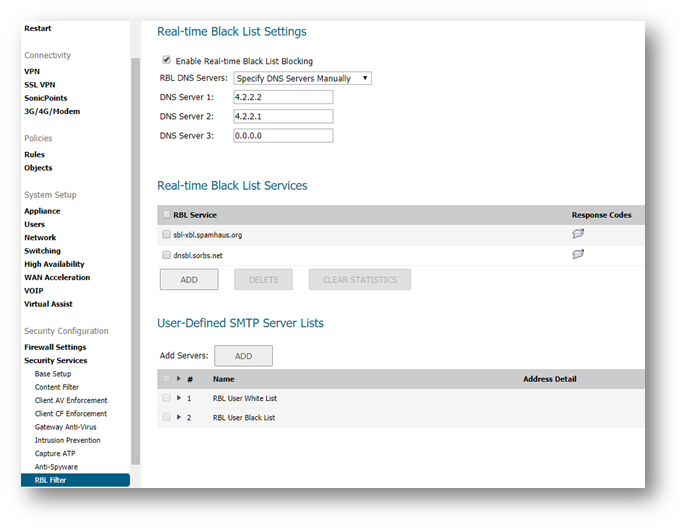
Add additional RBL Services
You can add additional RBL services to the Real-time Black List Services section by clicking the Add button.
In the Add RBL Domain window, you specify the RBL domain to be queried, enable it for use, and specify its expected response codes. Most RBL services list the responses they provide on their Web site, although selecting Block All Responses is generally acceptable.
User-Defined SMTP Server Lists
The User Defined SMTP Server Lists section allows for Address Objects to be used to construct a white-list (explicit allow) or black-list (explicit deny) of SMTP servers. Entries in this list will bypass the RBL querying procedure.
For example, to ensure that you always receive SMTP connections from a partner site's SMTP server:
- Create an Address Object for the server you added using the Add button
 |  |
- Click the edit icon in the Configure column of the RBL User White List row, and add the Address Object. The table will be updated, and that server will always be allowed to make SMTP exchanges.
The Monitor | Dashboard page also provides a Real-time Black List Lookup feature that allows for SMTP IP addresses (or RBL services, or DNS servers) to be specifically tested.
For a list of known spam sources to use in testing, refer to http://www.spamhaus.org/sbl/latest.lasso
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
Configuring Real Time Blacklist (RBL) Filter
- Login to the SonicWall Management Interface
- Go to Anti-Spam | RBL Filter
- Select the checkbox Enable Real-time Black List Blocking
- The RBL DNS Servers menu allows you to specify the DNS servers. You can choose Inherit Settings from WAN Zone or Specify DNS Servers Manually. If you select Specify DNS Servers Manually, enter the DNS server addresses in the DNS Server fields.
When Enable Real-time Black List Blocking in enabled inbound connections from hosts on the WAN, or outbound connections to hosts on the WAN are checked against each enabled RBL service with a DNS request to the DNS servers configured under RBL DNS Servers.
 NOTE: By default sbl-xbl.spamhaus.org and dnsbl.sorbs.net RBL Services are pre-configured; SonicWall will query these providers to determine the source of spam.
NOTE: By default sbl-xbl.spamhaus.org and dnsbl.sorbs.net RBL Services are pre-configured; SonicWall will query these providers to determine the source of spam.
 TIP: Statistics are maintained for each RBL Service in the RBL Service table, and can be viewed with a mouseover of the (statistics) icon to the right on the service entry.
TIP: Statistics are maintained for each RBL Service in the RBL Service table, and can be viewed with a mouseover of the (statistics) icon to the right on the service entry.
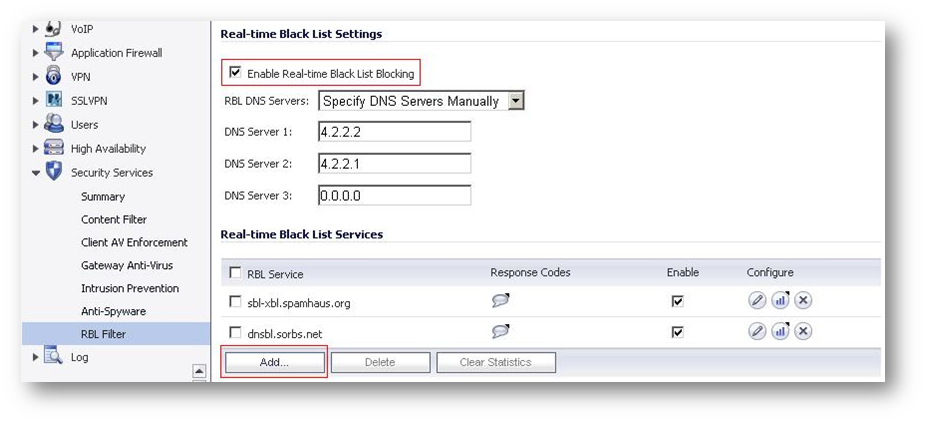
Add additional RBL Services
You can add additional RBL services to the Real-time Black List Services section by clicking the Add button.
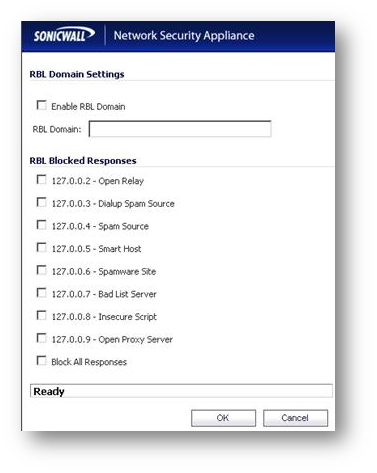 | In the Add RBL Domain window, you specify the RBL domain to be queried, enable it for use, and specify its expected response codes. Most RBL services list the responses they provide on their Web site, although selecting Block All Responses is generally acceptable. |
User-Defined SMTP Server Lists
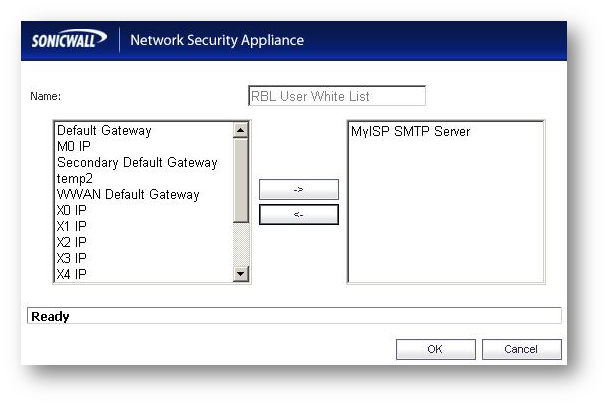
The User Defined SMTP Server Lists section allows for Address Objects to be used to construct a white-list (explicit allow) or black-list (explicit deny) of SMTP servers. Entries in this list will bypass the RBL querying procedure.
For example, to ensure that you always receive SMTP connections from a partner site's SMTP server,
- Create an Address Object for the server you added using the Add button,
 |  |
- Click the edit icon in the Configure column of the RBL User White List row, and add the Address Object. The table will be updated, and that server will always be allowed to make SMTP exchanges.
The System | Diagnostics page also provides a Real-time Black List Lookup feature that allows for SMTP IP addresses (or RBL services, or DNS servers) to be specifically tested.
For a list of known spam sources to use in testing, refer to http://www.spamhaus.org/sbl/latest.lasso
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM








 YES
YES NO
NO