HTML Phishing On the Rise: Analyzing New Threat Vectors

Spike in HTML-Driven Phishing Threats
This week, the SonicWall Capture Labs Threat Research Team observed a significant increase in HTML phishing threats. The prevalence of phishing campaigns targeting Microsoft Office and Adobe Cloud users is rising, with attackers focusing on stealing individual account passwords within various organizations. Many of these campaigns primarily targeted Chinese-speaking users.
Case 1: Office Phishing with the Title Confirm Identity
In this campaign, phishing pages mimicking Microsoft Office login screens were used to target corporate users. The pages prompted users to log in, claiming it was necessary to verify they were not robots.
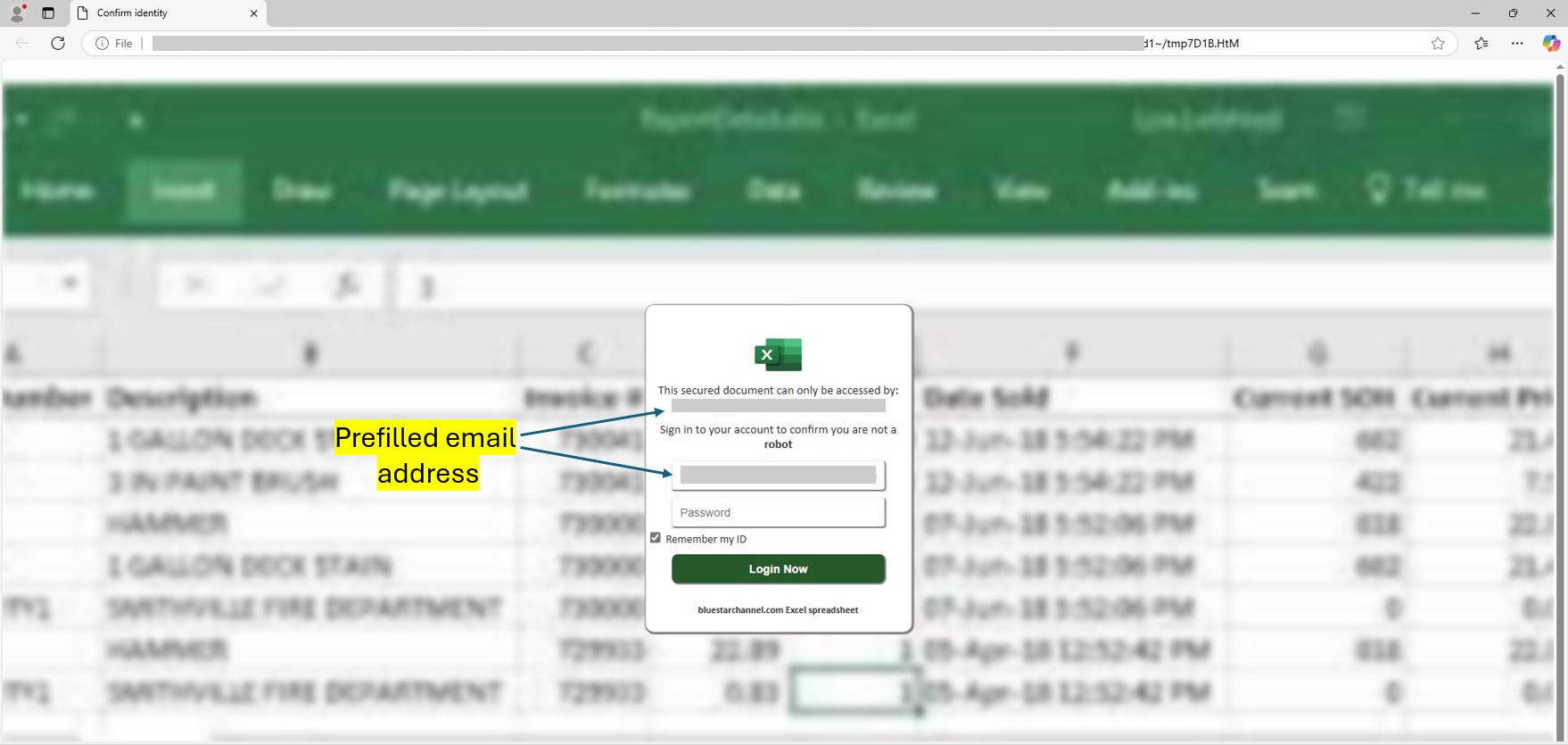
Figure 1: Login Page
These phishing pages featured a blurred image of an Excel sheet as the background, with a login box in the foreground. The login box often contained a prefilled email address of the targeted user.
Interestingly, the "Remember my ID" checkbox was ticked by default. Upon entering their password and clicking the "Login Here" button, users were redirected to an image displaying a mock PDF page.
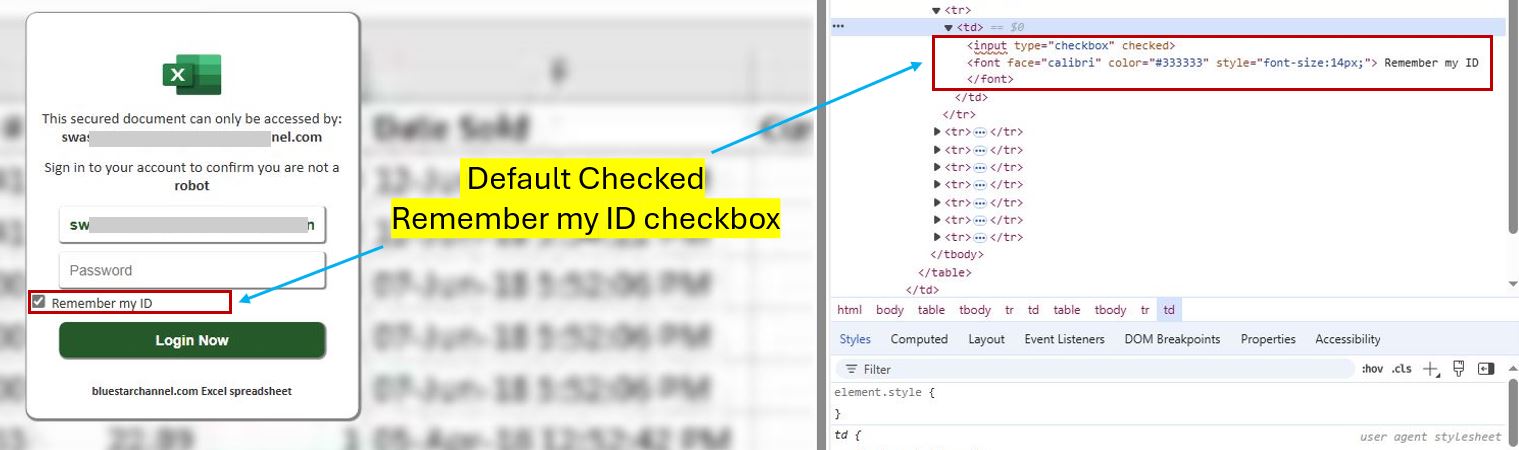
Figure 2: “My ID” Checkbox
Figure 3: PDF Page
The phishing domain no.pjaser9.sa[.]com is already flagged as malicious and has been linked to other phishing campaigns targeting Chinese-speaking users.
Case 2: Adobe Cloud Phishing with the Title Protected File Sign-In
In this scenario, victims were tricked into entering their passwords to access files—usually invoices—allegedly stored on Adobe Cloud. The phishing page was carefully designed, including copyright details, to appear legitimate.
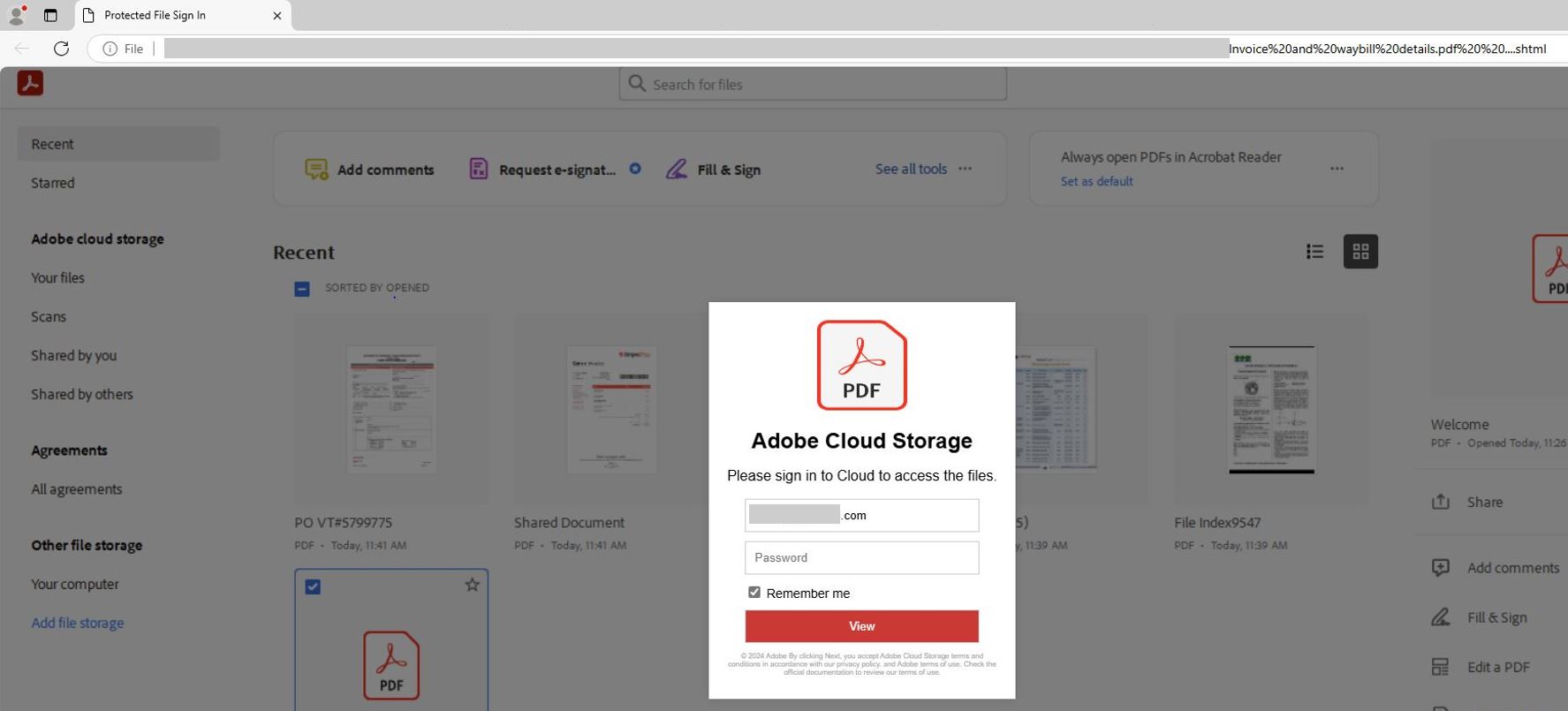
Figure 4: Adobe Cloud Page
The page's background mimicked the Adobe Cloud interface, while the foreground featured a credential input box. Upon entering their passwords, victims’ data was submitted to submit-form[.]com powered by formspark[.]io.
Case 3: Office Phishing Targeting Chinese Users (m.s - 163bj.com)
This campaign targeted Chinese-speaking users, prompting them to enter their email credentials to access documents.
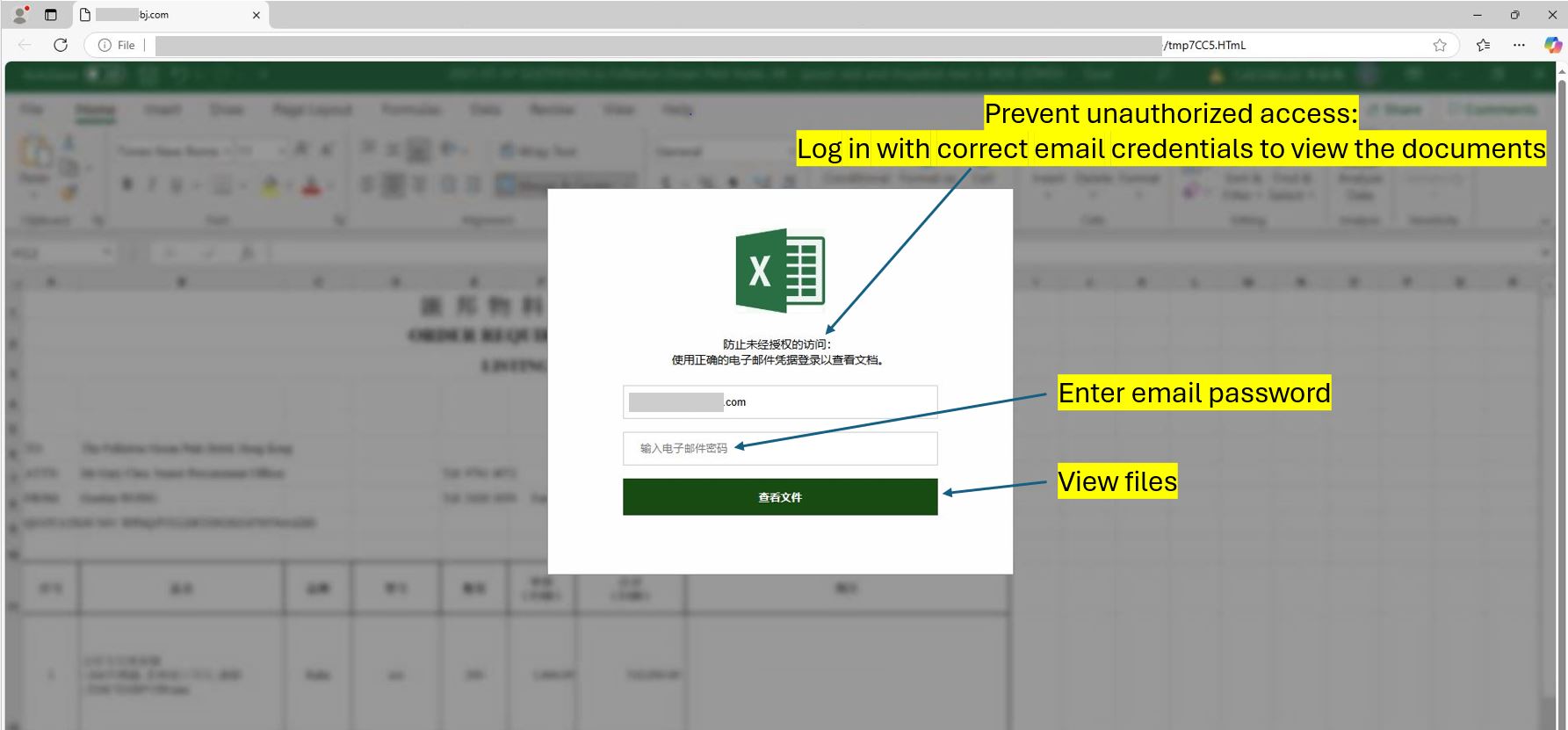
Figure 5: Chinese Excel Sign-In Page
The phishing page featured a blurred Excel sheet as the background with content resembling a quotation document. All text in the sign-in box was in Chinese.
Case 4: Office Phishing with the Title Microsoft Excel | Online
This campaign used another Excel-themed phishing page, requesting users to log in with their passwords to view documents. The email ID of the targeted victim was prefilled in the HTML code.
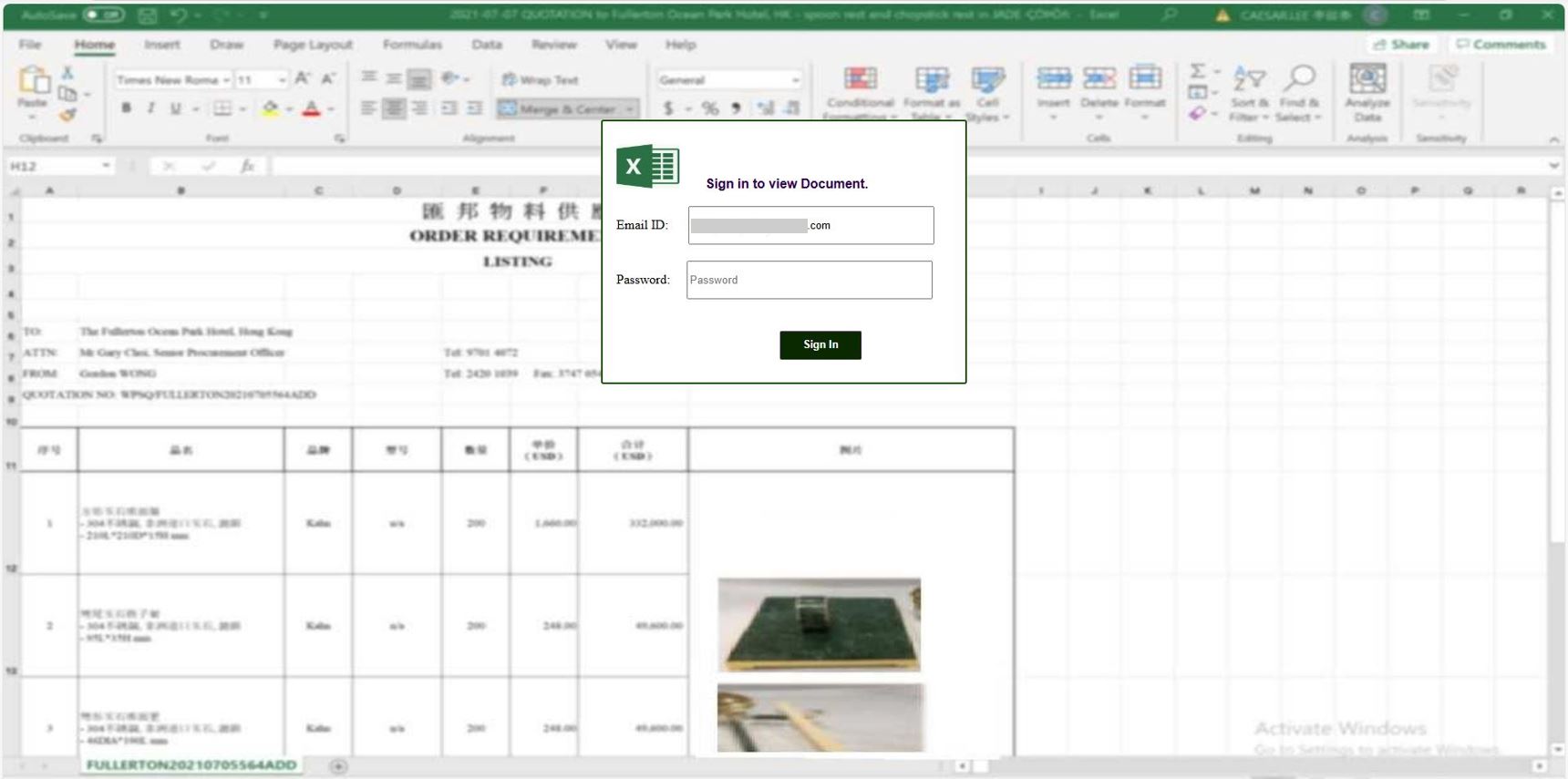
Figure 6: Excel Sign-In Page
To evade detection by antivirus software, malware authors obfuscated strings such as "Email ID:" and "Password" in the HTML file.
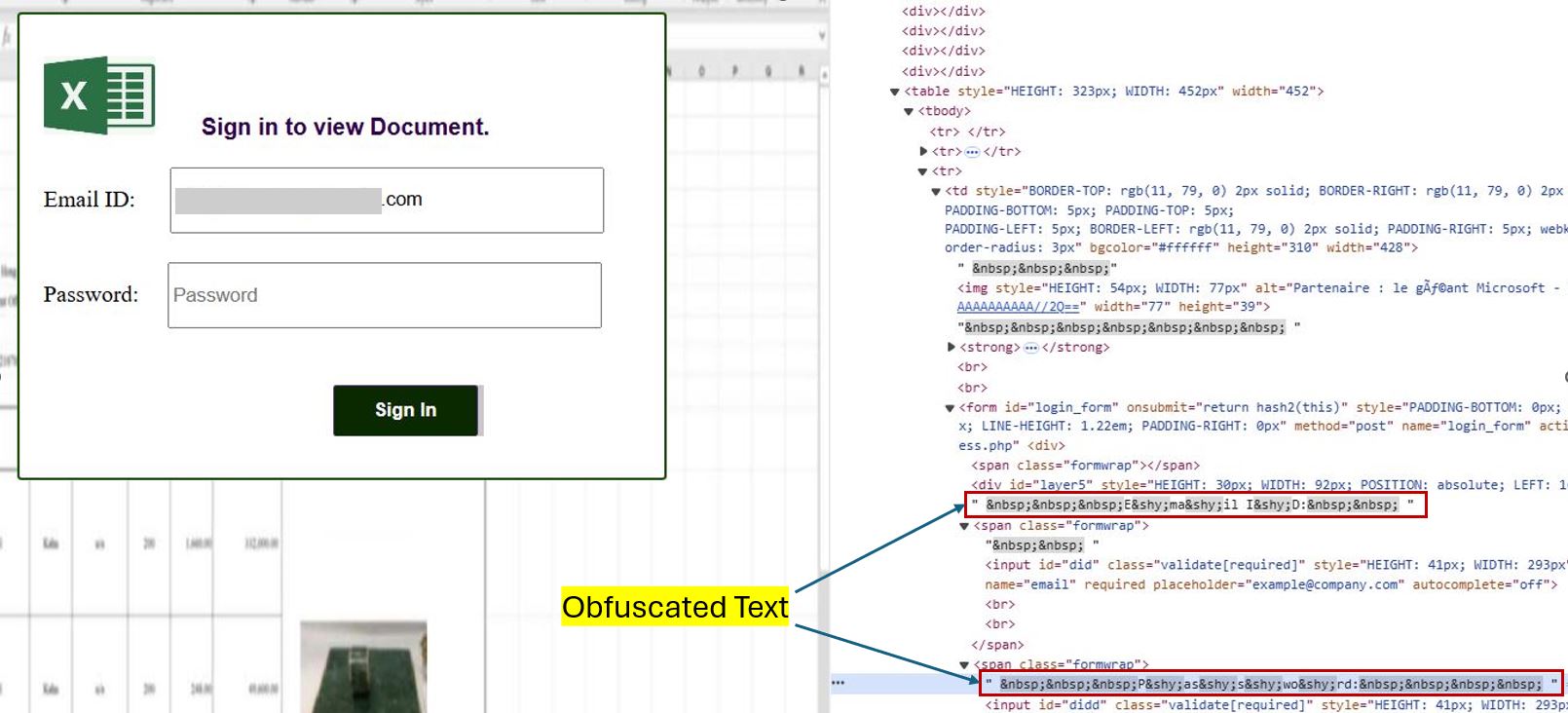
Figure 7: Obfuscation
Case 5: SF Express Phishing with the title SF Express | Tracking
This phishing campaign targeted Chinese-speaking users with a multilayered approach.
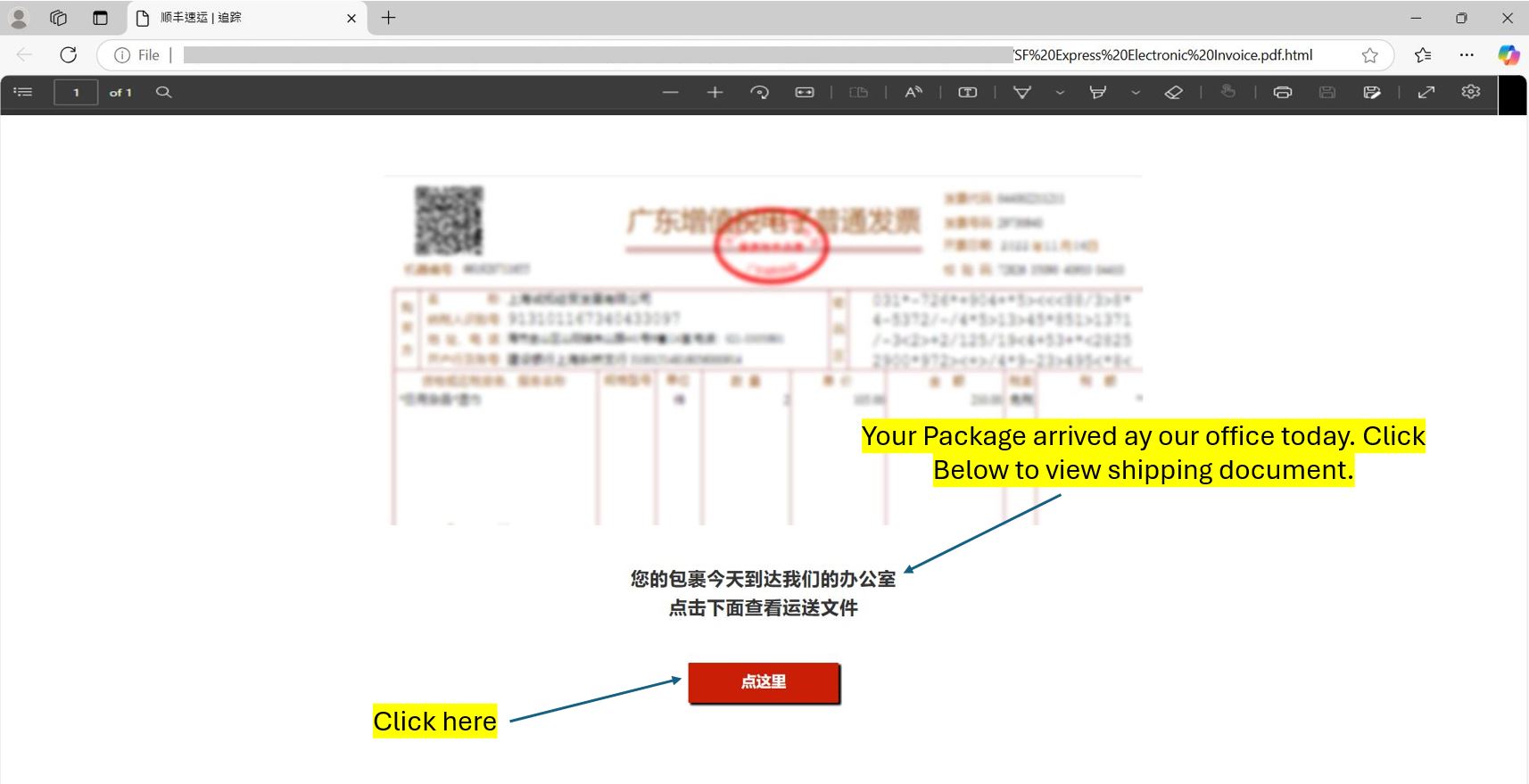
Figure 8: Click Button
The page content, written in Chinese, prompted users to click a button to open a shipping document.
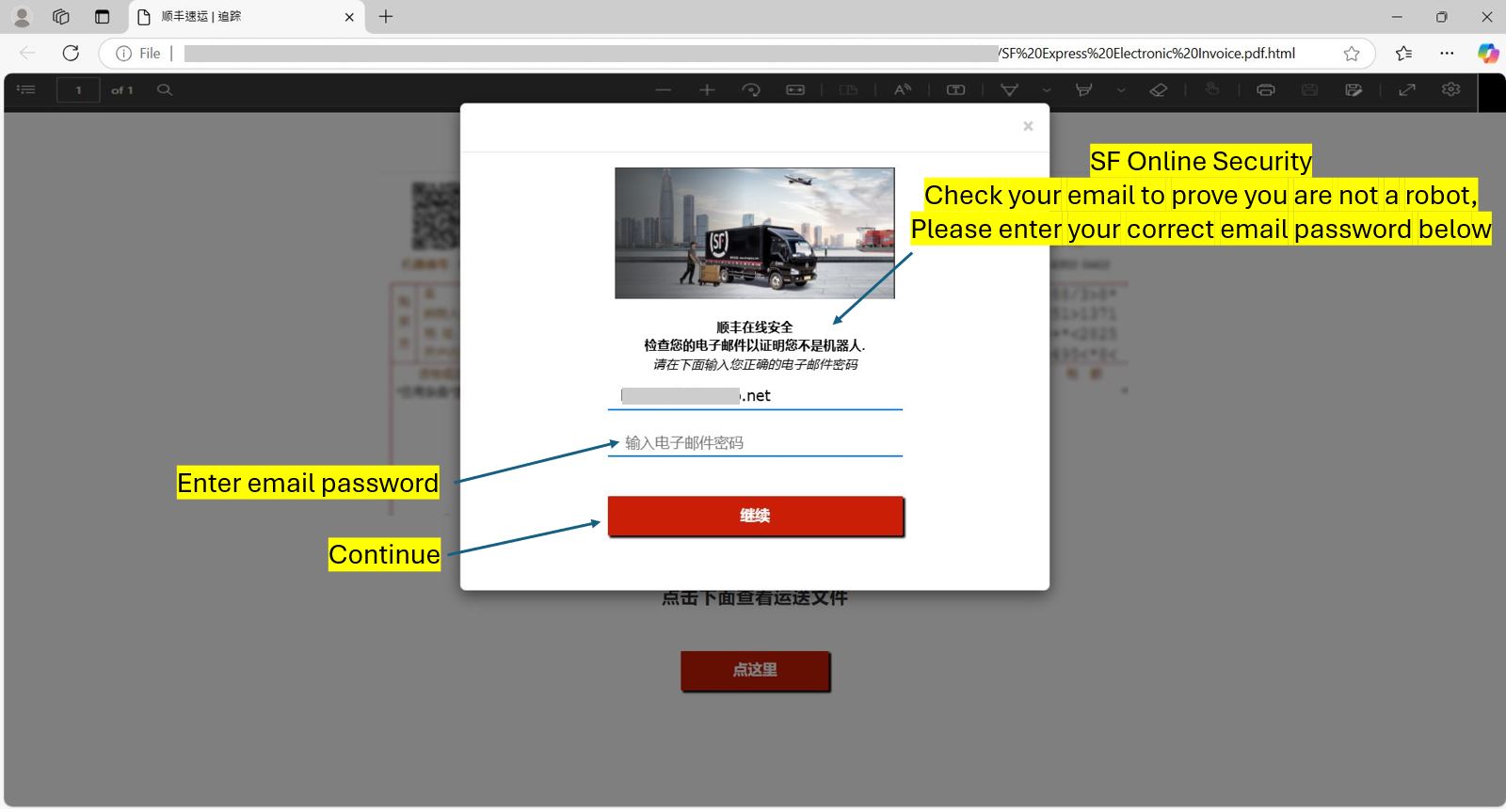
Figure 9: SF Express Phishing Page
After clicking the button, a pop-up appeared with a prefilled email address. The page then requested the user’s email password, allegedly to verify their authenticity.
Conclusion
These examples highlight the surge in phishing activity using HTML-based tactics. While some campaigns have been observed in the wild before, others are new. All the phishing threats mentioned in this blog are already being detected and mitigated by SonicWall’s security solutions. Organizations and users must remain vigilant, especially when encountering login prompts or credential requests from unknown sources.
IOCs
a5fbfec494c30006186aac27919a61cad459a56a7dcc2c7b670e6628a2cc2bff
f76d9827e41a7488be40fffee73e156f4246d4bfdebd296913db974e63f64c2d
9dba0d2b4f54fb7588814556eccf07324a06fc71023ca97d6ac7f3245715f259
7bffcefa296c9224fc7a9088b9524f5b297b83ebf728a9978985d5bc455b6802
4a424b3efb1681fbed52f92b199806fb32861d14d3216805684cdac33233aa99
URLs
hxxps://europeanautocare.com[.]au/ggh/excelaccess.php
hxxps://submit-form[.]com/aa0pVuDBf
hxxps://amigasdacasadocroche.com[.]br/ad/excelaccess.php
hxxps://submit-form[.]com/aa0pVuDBf
hxxps://no.pjaser9.sa[.]com/.ll/notice/exc.php
Share This Article

An Article By
An Article By
Security News
Security News
