Microsoft Security Bulletin Coverage for December 2024

Overview
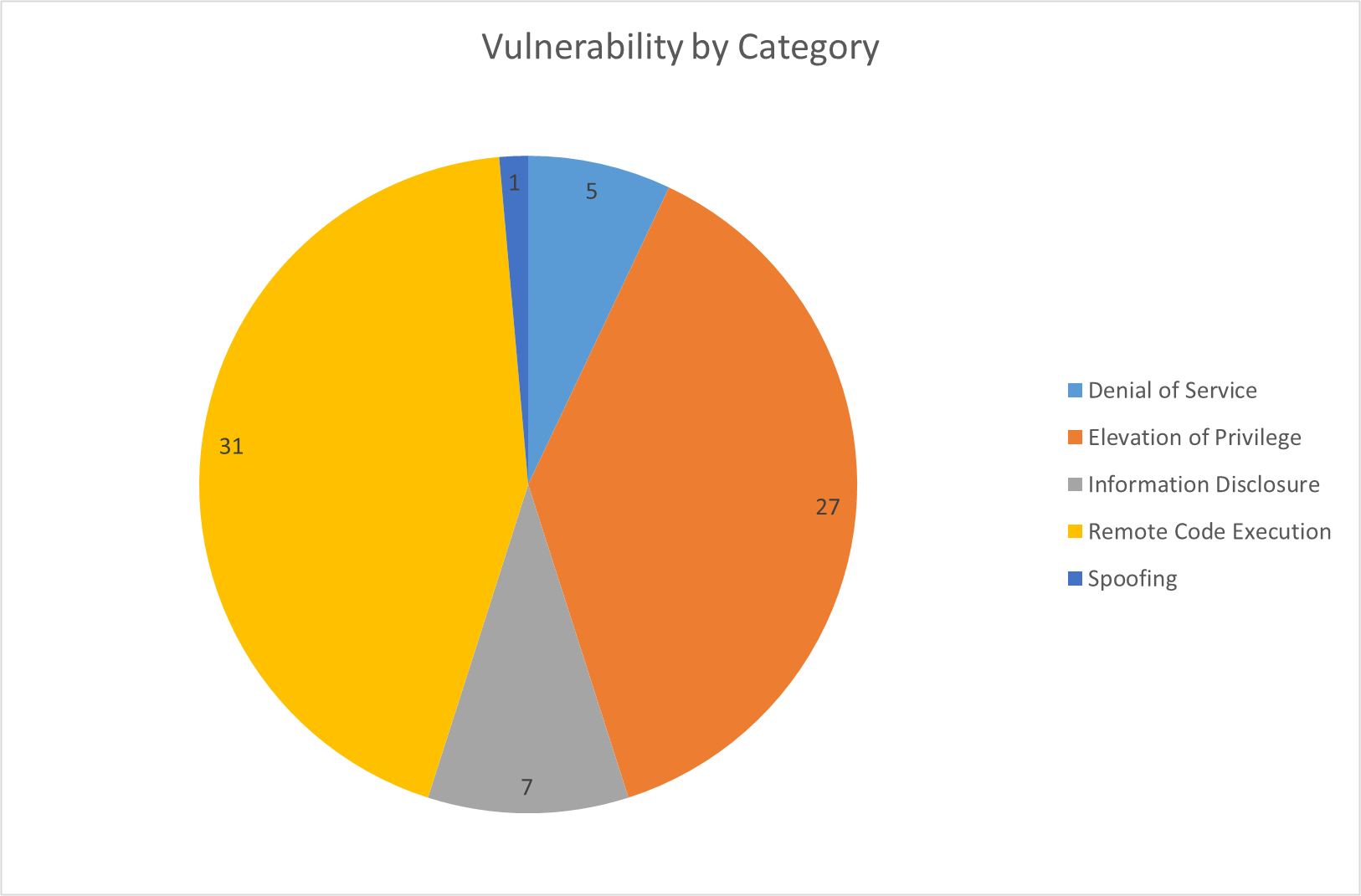
Microsoft’s December 2024 Patch Tuesday has 71 vulnerabilities, of which 31 are Remote Code Execution. SonicWall Capture Labs' threat research team has analyzed and addressed Microsoft’s security advisories for the month of December 2024 and has produced coverage for 6 of the reported vulnerabilities.
Vulnerabilities with Detections
CVE | CVE Title | Signature |
CVE-2024-49088 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | ASPY 7026 Exploit-exe exe.MP_420 |
CVE-2024-49090 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | ASPY 7027 Exploit-exe exe.MP_421 |
CVE-2024-49093 | Windows Resilient File System (ReFS) Elevation of Privilege Vulnerability | ASPY 7028 Exploit-exe exe.MP_422 |
CVE-2024-49114 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | ASPY 614 Exploit-exe exe.MP_423 |
CVE-2024-49122 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability | IPS 4535 Microsoft Message Queuing RCE (CVE-2024-49122) |
CVE-2024-49138 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | ASPY 615 Exploit-exe exe.MP_424 |
Release Breakdown
The vulnerabilities can be classified into the following categories:
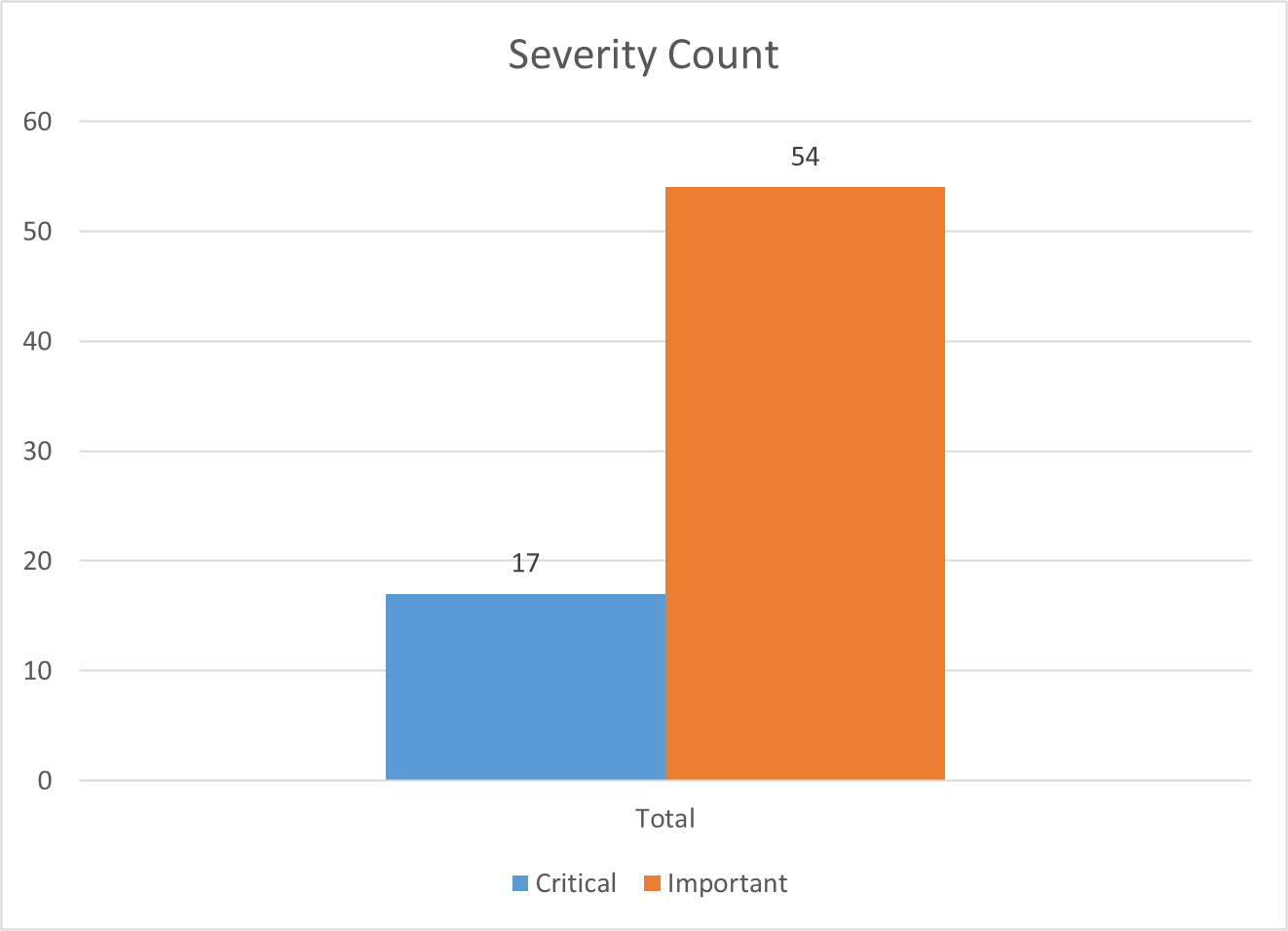
For December, there are 17 Critical and 54 Important vulnerabilities.
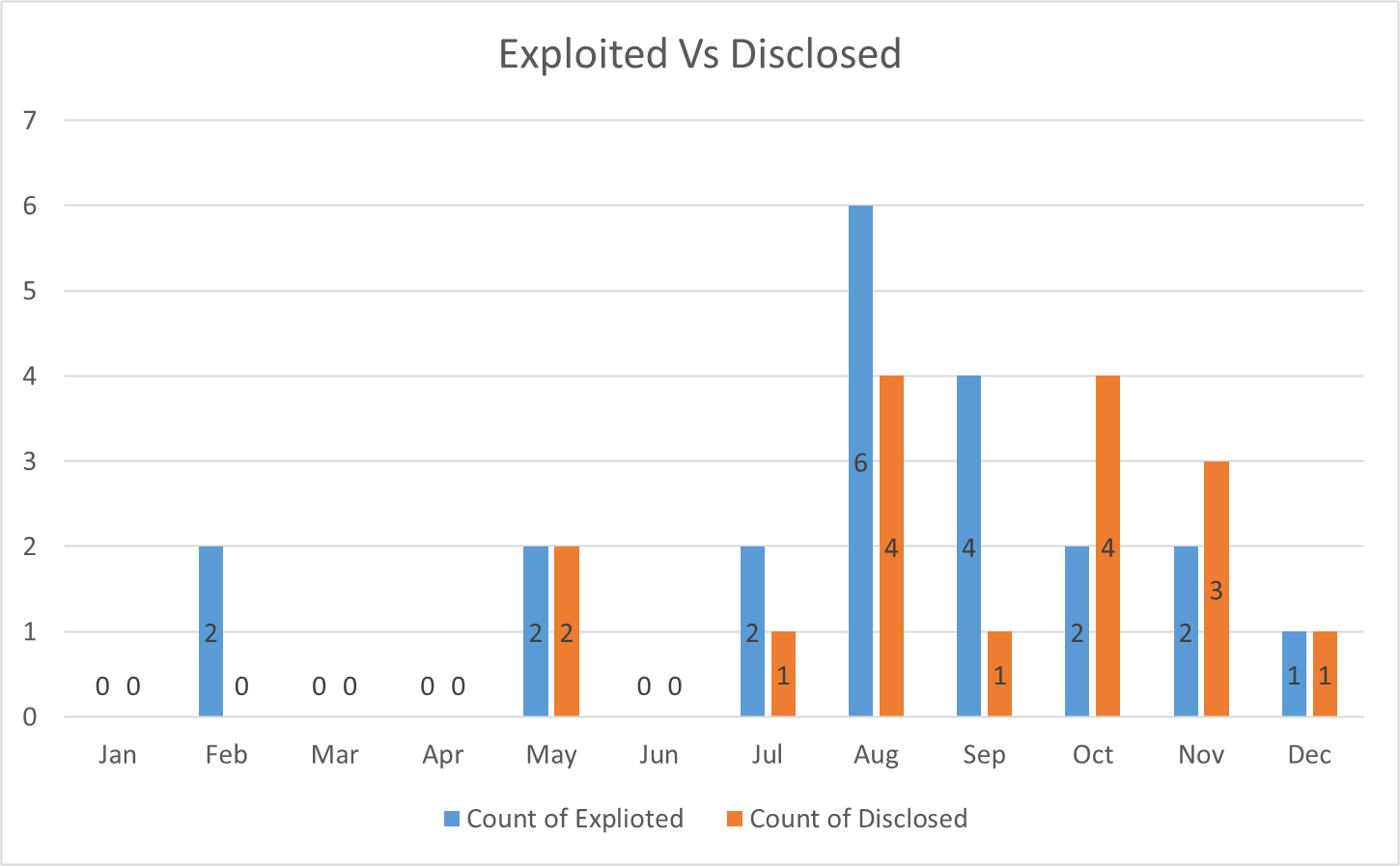
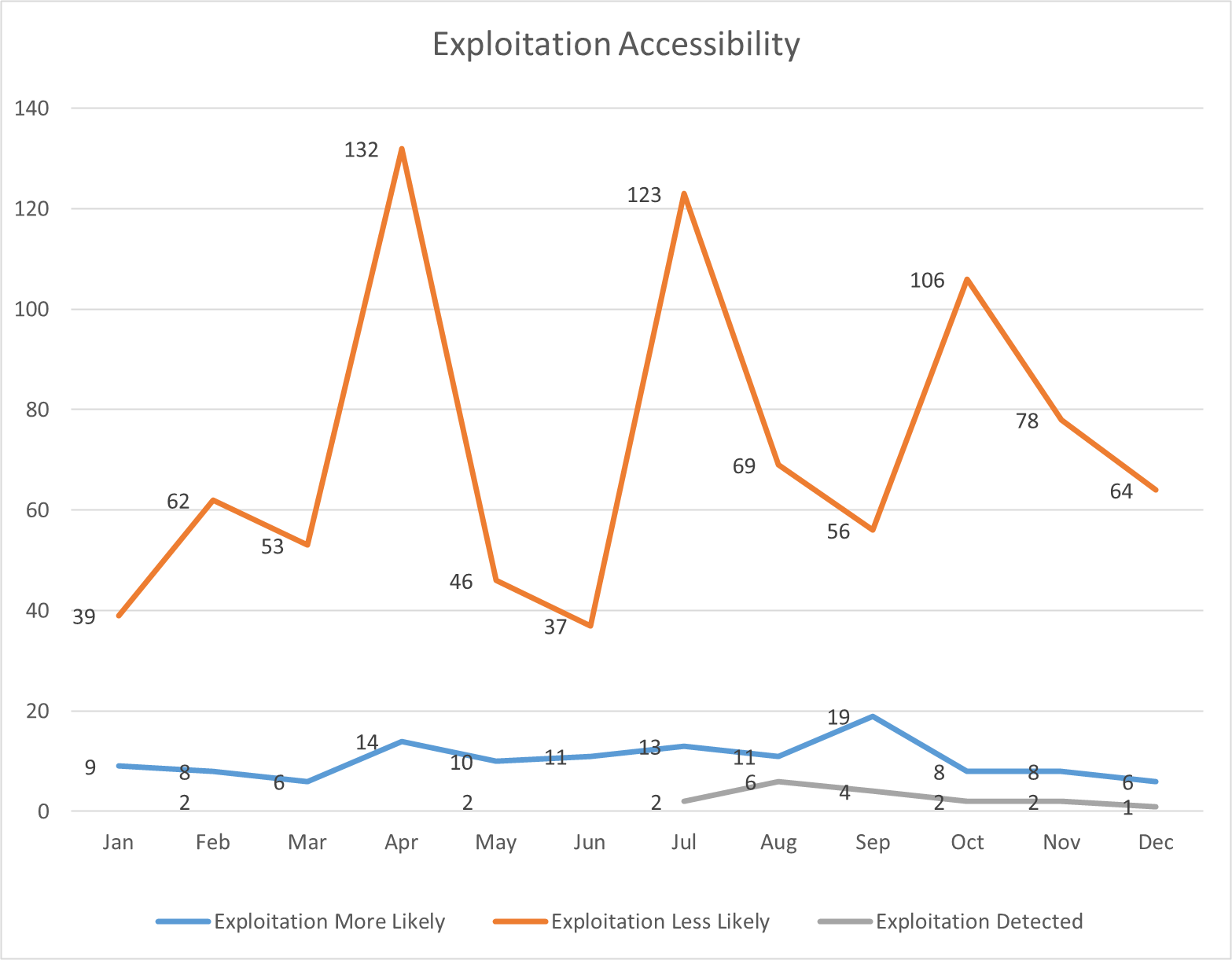
Microsoft tracks vulnerabilities that are being actively exploited at the time of discovery and those that have been disclosed publicly before the Patch Tuesday release for each month. The above chart displays these metrics as seen each month.
Release Detailed Breakdown
Denial of Service Vulnerabilities
CVE | CVE Title |
CVE-2024-49075 | Windows Remote Desktop Services Denial of Service Vulnerability |
CVE-2024-49096 | Microsoft Message Queuing (MSMQ) Denial of Service Vulnerability |
CVE-2024-49113 | Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability |
CVE-2024-49121 | Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability |
CVE-2024-49129 | Windows Remote Desktop Gateway (RD Gateway) Denial of Service Vulnerability |
Elevation of Privilege Vulnerabilities
CVE | CVE Title |
CVE-2024-43594 | System Center Operations Manager Elevation of Privilege Vulnerability |
CVE-2024-43600 | Microsoft Office Elevation of Privilege Vulnerability |
CVE-2024-49059 | Microsoft Office Elevation of Privilege Vulnerability |
CVE-2024-49068 | Microsoft SharePoint Elevation of Privilege Vulnerability |
CVE-2024-49072 | Windows Task Scheduler Elevation of Privilege Vulnerability |
CVE-2024-49073 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
CVE-2024-49074 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
CVE-2024-49076 | Windows Virtualization-Based Security (VBS) Enclave Elevation of Privilege Vulnerability |
CVE-2024-49077 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
CVE-2024-49078 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
CVE-2024-49081 | Wireless Wide Area Network Service (WwanSvc) Elevation of Privilege Vulnerability |
CVE-2024-49083 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
CVE-2024-49084 | Windows Kernel Elevation of Privilege Vulnerability |
CVE-2024-49088 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
CVE-2024-49090 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
CVE-2024-49092 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
CVE-2024-49093 | Windows Resilient File System (ReFS) Elevation of Privilege Vulnerability |
CVE-2024-49094 | Wireless Wide Area Network Service (WwanSvc) Elevation of Privilege Vulnerability |
CVE-2024-49095 | Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability |
CVE-2024-49097 | Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability |
CVE-2024-49101 | Wireless Wide Area Network Service (WwanSvc) Elevation of Privilege Vulnerability |
CVE-2024-49107 | WmsRepair Service Elevation of Privilege Vulnerability |
CVE-2024-49109 | Wireless Wide Area Network Service (WwanSvc) Elevation of Privilege Vulnerability |
CVE-2024-49110 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
CVE-2024-49111 | Wireless Wide Area Network Service (WwanSvc) Elevation of Privilege Vulnerability |
CVE-2024-49114 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
CVE-2024-49138 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
Information Disclosure Vulnerabilities
CVE | CVE Title |
CVE-2024-49062 | Microsoft SharePoint Information Disclosure Vulnerability |
CVE-2024-49064 | Microsoft SharePoint Information Disclosure Vulnerability |
CVE-2024-49082 | Windows File Explorer Information Disclosure Vulnerability |
CVE-2024-49087 | Windows Mobile Broadband Driver Information Disclosure Vulnerability |
CVE-2024-49098 | Windows Wireless Wide Area Network Service (WwanSvc) Information Disclosure Vulnerability |
CVE-2024-49099 | Windows Wireless Wide Area Network Service (WwanSvc) Information Disclosure Vulnerability |
CVE-2024-49103 | Windows Wireless Wide Area Network Service (WwanSvc) Information Disclosure Vulnerability |
Remote Code Execution Vulnerabilities
CVE | CVE Title |
CVE-2024-49063 | Microsoft/Muzic Remote Code Execution Vulnerability |
CVE-2024-49065 | Microsoft Office Remote Code Execution Vulnerability |
CVE-2024-49069 | Microsoft Excel Remote Code Execution Vulnerability |
CVE-2024-49070 | Microsoft SharePoint Remote Code Execution Vulnerability |
CVE-2024-49079 | Input Method Editor (IME) Remote Code Execution Vulnerability |
CVE-2024-49080 | Windows IP Routing Management Snapin Remote Code Execution Vulnerability |
CVE-2024-49085 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
CVE-2024-49086 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
CVE-2024-49089 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
CVE-2024-49091 | Windows Domain Name Service Remote Code Execution Vulnerability |
CVE-2024-49102 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
CVE-2024-49104 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
CVE-2024-49105 | Remote Desktop Client Remote Code Execution Vulnerability |
CVE-2024-49106 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
CVE-2024-49108 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
CVE-2024-49112 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
CVE-2024-49115 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
CVE-2024-49116 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
CVE-2024-49117 | Windows Hyper-V Remote Code Execution Vulnerability |
CVE-2024-49118 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability |
CVE-2024-49119 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
CVE-2024-49120 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
CVE-2024-49122 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability |
CVE-2024-49123 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
CVE-2024-49124 | Lightweight Directory Access Protocol (LDAP) Client Remote Code Execution Vulnerability |
CVE-2024-49125 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
CVE-2024-49126 | Windows Local Security Authority Subsystem Service (LSASS) Remote Code Execution Vulnerability |
CVE-2024-49127 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
CVE-2024-49128 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
CVE-2024-49132 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
CVE-2024-49142 | Microsoft Access Remote Code Execution Vulnerability |
Spoofing Vulnerabilities
CVE | CVE Title |
CVE-2024-49057 | Microsoft Defender for Endpoint on Android Spoofing Vulnerability |
Share This Article

An Article By
An Article By
Security News
Security News
.jpg%3Fwith%3D384%26height%3D170&w=828&q=75)
