Critical Exploit in ProjectSend (CVE-2024-11680): Insights, Impact and Remediation

Overview
The SonicWall Capture Labs threat research team became aware of an improper authentication vulnerability affecting ProjectSend versions prior to r1720. ProjectSend is a free, open-source platform designed for sharing files and data with clients. It prioritizes ease of use, privacy and comprehensive management features, including client groups, user roles, statistics, multiple languages and detailed logs.
The vulnerability in question is CVE-2024-11680, which carries a critical CVSSv3 score of 9.8. As of December 2024, it has been added to the CISA Known Exploited Vulnerabilities Catalog (KEV). Classified as an Improper Authentication issue under CWE-287, this flaw allows unauthenticated attackers to exploit the application by sending specially crafted HTTP requests to options.php, thereby enabling unauthorized configuration changes. Multiple proofs of concept (PoCs) are publicly available, and there is evidence of active exploitation in the wild. Users are strongly encouraged to update their ProjectSend instances to the latest patched versions.
Technical Overview
CVE-2024-11680 is a critical Improper Authorization vulnerability found in ProjectSend. This flaw enables an unauthenticated attacker to modify the application’s configurations and lead to code execution. This issue can be exploited remotely and could lead to unauthorized access to sensitive data. It can also allow unauthenticated actors to gain post-authentication privileges, indicating that they are not confined to scanning for vulnerable instances. This occurs in the user registration feature and can be enabled via the attacker using a specially crafted HTTP POST request along with a malicious CSRF token to “options.php”
Triggering the Vulnerability
Attackers can exploit the improper authentication flaw in ProjectSend by issuing a series of specially crafted requests to the vulnerable options.php endpoint. Since the application does not adequately verify the authenticity of these requests, the attacker can update critical configuration settings without being logged in. By toggling security-related parameters—such as enabling user registrations, auto-approving new accounts and removing file upload restrictions—the attacker transforms a normally secure environment into one where they can freely create new users, upload arbitrary PHP files and ultimately achieve remote code execution.
The process involves obtaining and using a CSRF token, even though the authorization checks are flawed, to bypass any superficial validation steps. Once the attacker has escalated control, they can upload a malicious PHP payload disguised as a normal file. By manipulating configuration settings and executing the uploaded payload through carefully crafted requests, an unauthenticated attacker can subvert ProjectSend’s security model and gain full control due to the missing authorization logic on configuration endpoints.
- Initial Check & CSRF Token Extraction: The attacker retrieves a CSRF token and checks if it can alter the site’s title via options.php, confirming vulnerability.
- Configuration Manipulation: By sending crafted parameters through POST requests (Figure 1) to options.php, the attacker enables user registration, auto-approval, and unrestricted file uploads—no authentication is required.
- Account Creation & Upload: With security controls disabled, the attacker creates a new account, logs in, and uploads a malicious PHP file.
- Payload Execution: The attacker then triggers the malicious file by calculating possible filenames and making requests to execute the payload, ultimately achieving remote code execution on the server.
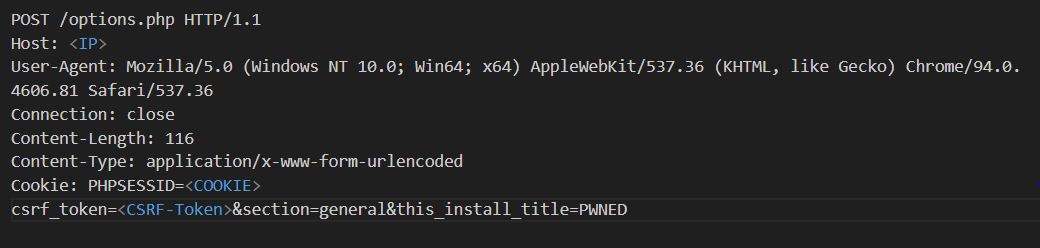
Figure 1: POST Request w/CSRF Token
Exploitation
Successful exploitation of this vulnerability could allow attackers to manipulate or delete critical data and escalate privileges. The potential impact includes:
- Full Compromise of Database Integrity: Attackers could modify, delete, or exfiltrate database records, affecting both data integrity and confidentiality.
- Privilege Escalation: By exploiting this vulnerability, attackers could gain higher-level permissions, granting broader access across the system. In the case of CVE-2024-11680, options.php is responsible for updating the application’s configuration. Due to an authorization check being performed only after the rest of the application code executes, unauthenticated users can carry out high-privilege actions without proper verification.
- Remote Code Execution (RCE): Exploiting the flaw allows the attacker to execute arbitrary PHP code on the host system. This not only compromises the system itself but can also serve as a foothold for deeper network infiltration.
- Unauthorized Access: An attacker could enable user registration, auto-approve new accounts, or add new entries to the whitelist of allowed file extensions, all without proper authorization. Such actions could destabilize the system, potentially leading to service interruptions, crashes, or broader availability issues.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS:20505 – ProjectSend Improper Authentication
- IPS:20506 – ProjectSend Improper Authentication 2
Remediation Recommendations
To deny the execution of any script in the upload/file’s directory, the following line must be added in the upload/files/.htaccess file:
php_flag engine off
According to the advisory, considering the severe consequences of this vulnerability and the trend of nefarious activists trying to leverage the exploit in the wild, users are strongly encouraged to upgrade their ProjectSend instances to the latest patch to address the vulnerability.
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News
