-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Using GVC with Unique User Certificate



Description
With the WAN Group policy (GVC) configured in the SonicWall appliance, some users want to use unique certificate for each user, however that is not possible if the policy is configured with the “Peer Id Type” as a “Distinguished Name”. The reason is the “Distinguished Name” may not be same for all the users as it contains different fields may not be same for all the users. And this configuration will not allow the certificate configured with any other “Distinguished Name”.
Resolution
This limitation can be overcome by choosing an “Email ID” or “Domain name” in place of “Distinguished Name”. When the either of these is chosen then the exact or partial match of these should be present in the “Subject Alternative Name” field of the user certificate. If
For example:
1. If you select “Email ID” as Peer Id and Peer ID filter as *@example.com then the
“Subject Alternative Name” filed in the certificate could be admin@example.com or user1@example.com or any email id from example.com could be used.
2. If you select “Domain name” as Peer Id and Peer ID filter as *.example.com then the
“Subject Alternative Name” filed in the certificate could be web.example.com or vpn.example.com or any sub domain from example.com could be used.
The SonicWall appliance provides an opportunity to fill in “Subject Alternative Name” in the CSR (Certificate Signing Request) then can be used to create certificates for the appliance itself. We can only import the Local/3rd party certificates in the GVC software, but can not create a CSR and thus can not provide the “Subject Alternative Name” in it.
By default some software vendors do not provide the opportunity to fill in the “Subject Alternative Name” in the CSR. Below are some steps that helps filling in the same in the CSR.
Note: The below methods are provided for local OpenSSL and Microsoft CA and if you are using the 3rd party certificates then you need to contact you CA as to how to get a “Subject Alternative Name” in the user certificates.
Using local Microsoft Windows 2003 Server CA for the user certificate for GVC software:
Make sure that the Root CA certificate is already present in the GVC software before importing the user certificate as it can validate the user certificate from that CA
Note: If (by default) the Microsoft Windows 2003 Server CA is not configured to provide the “Subject Alternative Name” in the certificate then please follow the procedure in the section “Preparing the CA server to provide “Subject Alternative Name” in the certificate”
Access the CA web page of you local CA and click on “Request a certificate link”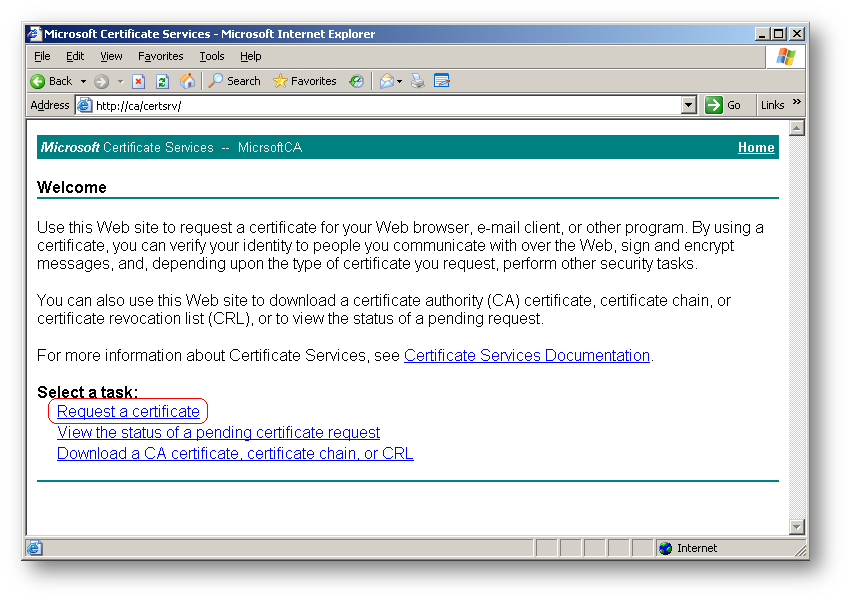
Click on “advanced certificate request” on the next screen
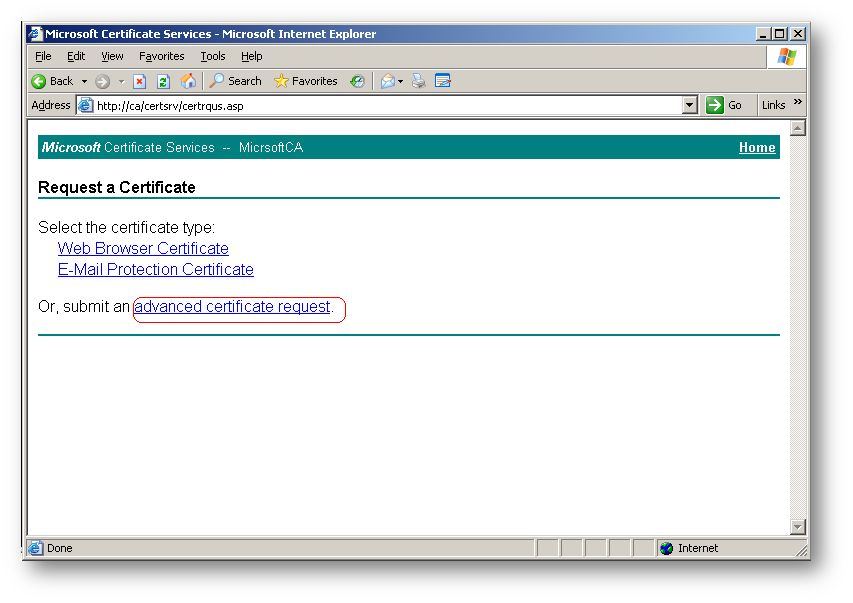
Make sure that the “Mark keys as exportable” option is selected and put in the SAN:email=”user@domainname.com” for email as SubjectAltName or SAN: dns=”domain name” for domain name of the user in Attributes filed.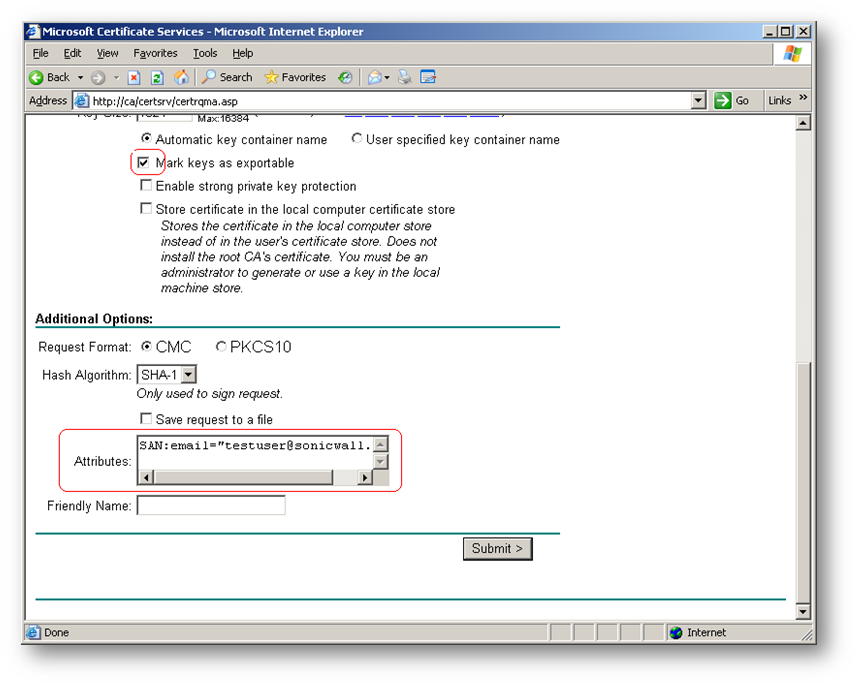
Click on ‘Install the certificate link’ so it’ll install the certificate in the user certificate store.

Now, we need to export the certificate from the browser to a file so you can import in the GVC software.
On the browser, click on Tool menu > Content Tab > Certificates button > select the certificate that you have requested form the CA server and click on Export button.

Select ‘Yes, export the private key’ so you can save the certificate in p12 (.pfx) format

Provide the password to protect the certificate. (And remember the password, this is needed to import the certificate in the GVC software)

It will show the confirmation that the certificate export was successful.


Now the GVC software is ready to establish a connection with sonicwall with a user certificate. Installing the CA certificate
Installing the CA certificate
Access the CA server in the browser and click on ‘Download a CA certificate…’
Preparing the CA server to provide “Subject Alternative Name” in the certificate
Caution: The below steps involve the change in registry of the server so make sure that you have the backup of registry before doing this. And you may do this at your own risk; SonicWall is not responsible for any damage, outage, data loss or any kind of loss. Or you may contact Microsoft to assist you for the same.
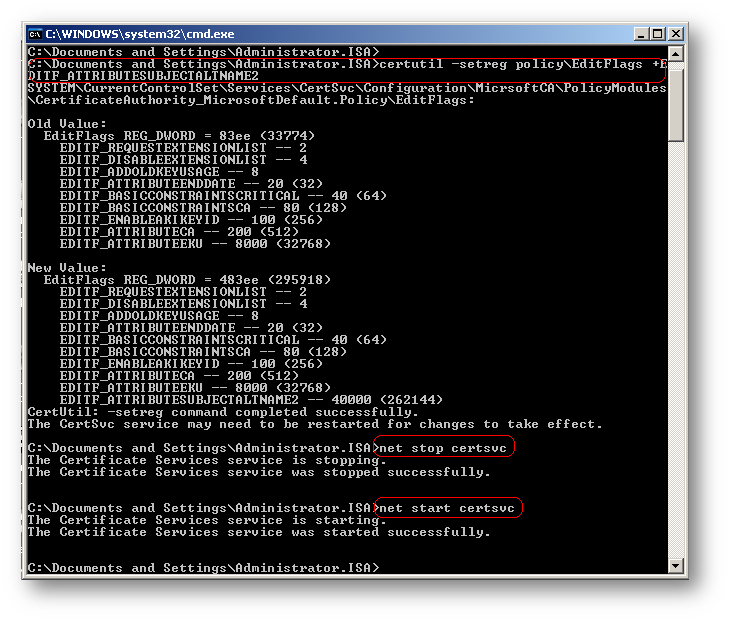
All you need to do is login as administrator on the CA server, open a command prompt window and type:
certutil –setreg policyEditFlags +EDITF_ATTRIBUTESUBJECTALTNAME2
The response will be something like below in the screen shot.
Then stop and start the CA service.
Now the CA server is ready to provide the “Subject Alternative Name” in the certificate
 Generating CSR thru OpenSSL you need to create an ‘extension’ file with the following attributes and use it with the command to create a CSR (details are not provided here):
Generating CSR thru OpenSSL you need to create an ‘extension’ file with the following attributes and use it with the command to create a CSR (details are not provided here): subjectAltName = email:[ ] or subjectAltName = DNS:[ ]
basicConstraints = critical,CA:FALSE
nsCertType = client,email
nsComment = "GVC user certificate"
For more details on OpenSSL with SonicWall, please search for “Using OpenSSL to Create a Private Certificate Authority” tech note on sonicwall web site.
Verifying the Subjective Alternative Name in the Certificate
On the certificate details you should be able to see the Subjective Alternative Name as shown in the screen shots below:

Related Articles
- How to migrate settings from GEN6 to GEN7 firewall?
- Supported SonicWall and 3rd party SFP and SFP+ modules that can be used with SonicWall TZ series
- How to Block Google QUIC Protocol on SonicOSX 7.0?
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall NSA Series






 YES
YES NO
NO